Cannot Block VLAN Traffic
-
I apologize if this has been answered before but I really am stumped why this is not working. Im trying to block traffic coming in on VLAN 35 from LIVINGROOM. I can block traffic to LIVINGROOM. I created a rule for this in the photo its currently off but I confirmed this with some pings. It does not work in the opposite direction. I created another rule blocking all traffic from LIVINGROOM to VLAN 35 net and pings are still able to go through. What could be wrong?
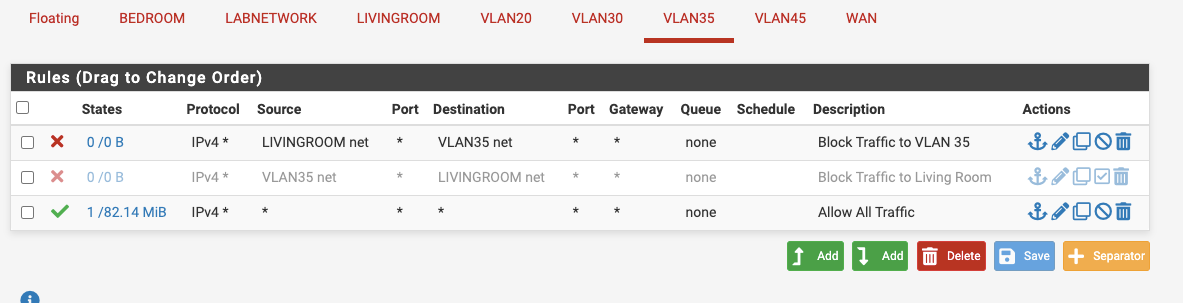
These are my interfaces and my rules for VLAN 35.
The Bedroom interface is a point to point connection to a Ruckus switch (192.168.44.0/30)
I have a port assigned on this switch for VLAN 35. Here is the show vlan output:
SSH@BH-SW-ICX7150#show vlan
Total PORT-VLAN entries: 5
Maximum PORT-VLAN entries: 1024Legend: [Stk=Stack-Id, S=Slot]
PORT-VLAN 1, Name [None], Priority level0, On
Untagged Ports: None
Tagged Ports: None
Mac-Vlan Ports: None
Monitoring: Disabled
PORT-VLAN 25, Name Management, Priority level0, On
Untagged Ports: None
Tagged Ports: (U1/M2) 1
Mac-Vlan Ports: None
Monitoring: Disabled
PORT-VLAN 35, Name DATA, Priority level0, On
Untagged Ports: (U1/M1) 1 2 3 4 5 6 7 8
Tagged Ports: (U1/M2) 1
Mac-Vlan Ports: None
Monitoring: Disabled
PORT-VLAN 45, Name VOICE, Priority level0, On
Untagged Ports: (U1/M1) 9 10 11 12
Tagged Ports: (U1/M2) 1
Mac-Vlan Ports: None
Monitoring: Disabled
PORT-VLAN 77, Name DEFAULT-VLAN, Priority level0, On
Untagged Ports: (U1/M2) 1 2
Untagged Ports: (U1/M3) 1 2
Tagged Ports: None
Mac-Vlan Ports: None
Monitoring: DisabledHere is also a show run:
SSH@BH-SW-ICX7150#show run
Current configuration:
!
ver 08.0.90dT211
!
stack unit 1
module 1 icx7150-c12-poe-port-management-module
module 2 icx7150-2-copper-port-2g-module
module 3 icx7150-2-sfp-plus-port-20g-module
stack-port 1/3/1
stack-port 1/3/2
!
!
!
!
!
default-vlan-id 77
!
vlan 1 by port
!
vlan 25 name Management by port
tagged ethe 1/2/1
!
vlan 35 name DATA by port
tagged ethe 1/2/1
untagged ethe 1/1/1 to 1/1/8
!
vlan 45 name VOICE by port
tagged ethe 1/2/1
untagged ethe 1/1/9 to 1/1/12
!
vlan 77 name DEFAULT-VLAN by port
!
!
!
!
!
!
!
!
!
!
!
!
!
aaa authentication web-server default local
aaa authentication login default local
console timeout 30
enable super-user-password .....
enable aaa console
enable acl-per-port-per-vlan
hostname BH-SW-ICX7150
ip address 192.168.44.2 255.255.255.252
ip dns server-address 8.8.8.8 8.8.4.4
ip default-gateway 192.168.44.1
!
no telnet server
username super password .....
username nicholas password .....
!
password-change any
!
!
clock timezone us Eastern
web-management https
!
!
sz registrar
!
!
interface ethernet 1/3/1
speed-duplex 1000-full
!
interface ethernet 1/3/2
speed-duplex 1000-full
!
!
!
!
!
!
ip ssh timeout 30
ip ssh idle-time 20
!
!
!
!
!
end -
If you want to block living room from going to vlan 35 the rule would be on living room interface, not vlan35.
Rules are evaluated as traffic enters an interface.
Top down, first rule to trigger wins, no other rules are evaluated.
Think of this way if you want to stop someone from going into your back yard (vlan35) from your front yard (living room). Do you stop them before they even inter the house (pfsense), or do you stop them before they exit the back door.
-
@johnpoz Ah ok. Yea I just tried copying the rule to LIVINGROOM and that worked. Im used to Watchguard where all the rules are on one page. That metaphor was useful for how to think about this. Thanks!
-
Other thing to keep in mind, that even though you create a block rule. If there are any existing states that allowed the traffic you have to wait til those states clear, or you kill them.
So say you tested accessing http on some box in vlan35 from livingroom. Then put in a block rule on living room interface to stop http to vlan 35.
If the state is there, the traffic would still be allowed since states are evaluated before interface rules. Simple solution is to just look states table under diagnostics and see if any traffic matches what your wanting to now block and kill those states.
-
After saving a rule, you have to click on Apply changes. Does that do anything about those states?
-
No states could still be there. It doesn't really come up that often... But states have bitten new users a few times wondering why their block rules are not working.. Normally because they just did a test before they did the rule.. And that state is there, on the exact thing they were trying to block ;)