Multiple untagged VLAN's on single switch port
-
Hi,
I've just purchased an SG-1100 Netgate firewall. My ideal setup is -
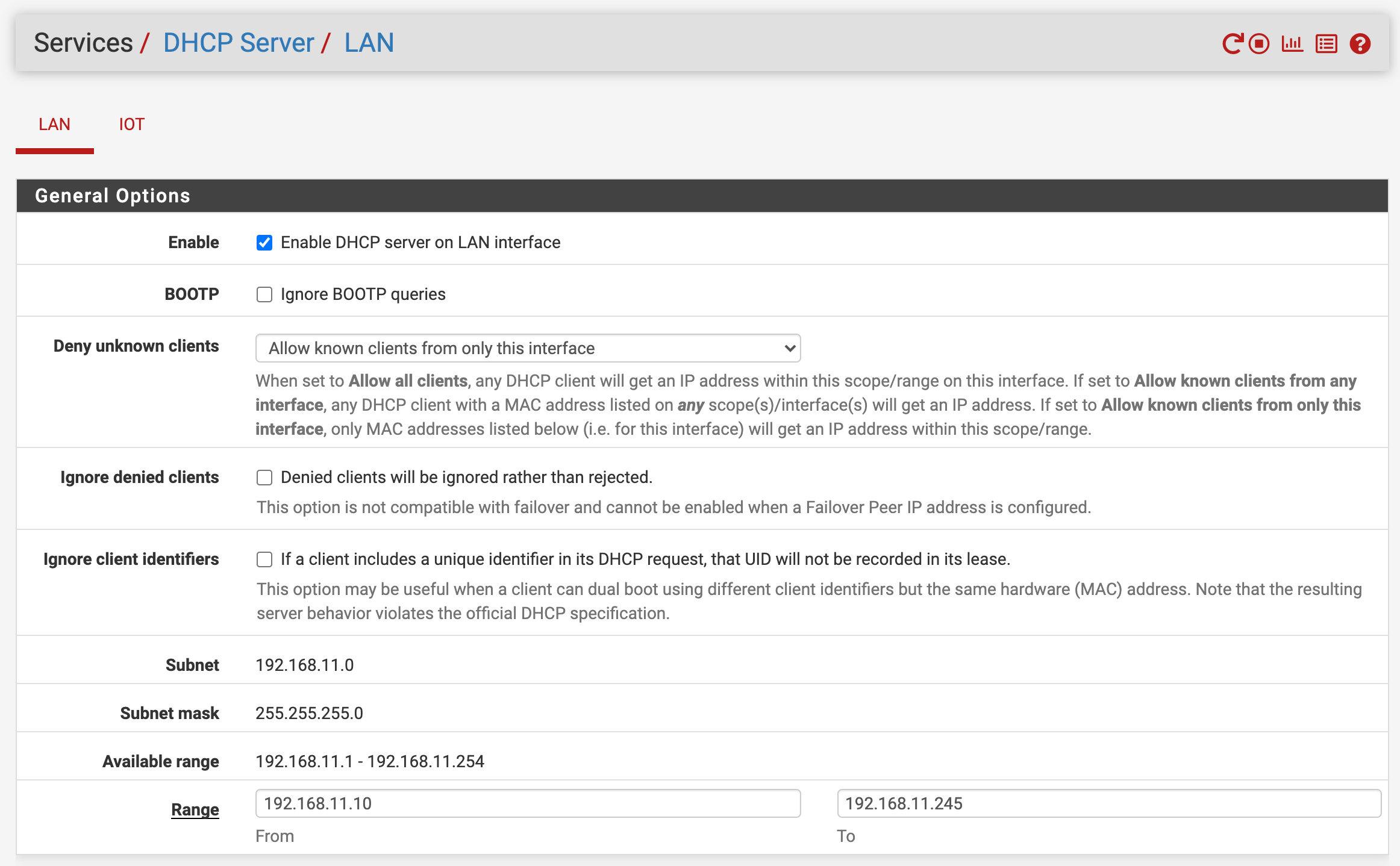
VLAN 4091 - LAN. 192.168.11.0/24 used as management network. DHCP configured to allow only specific mac addresses.
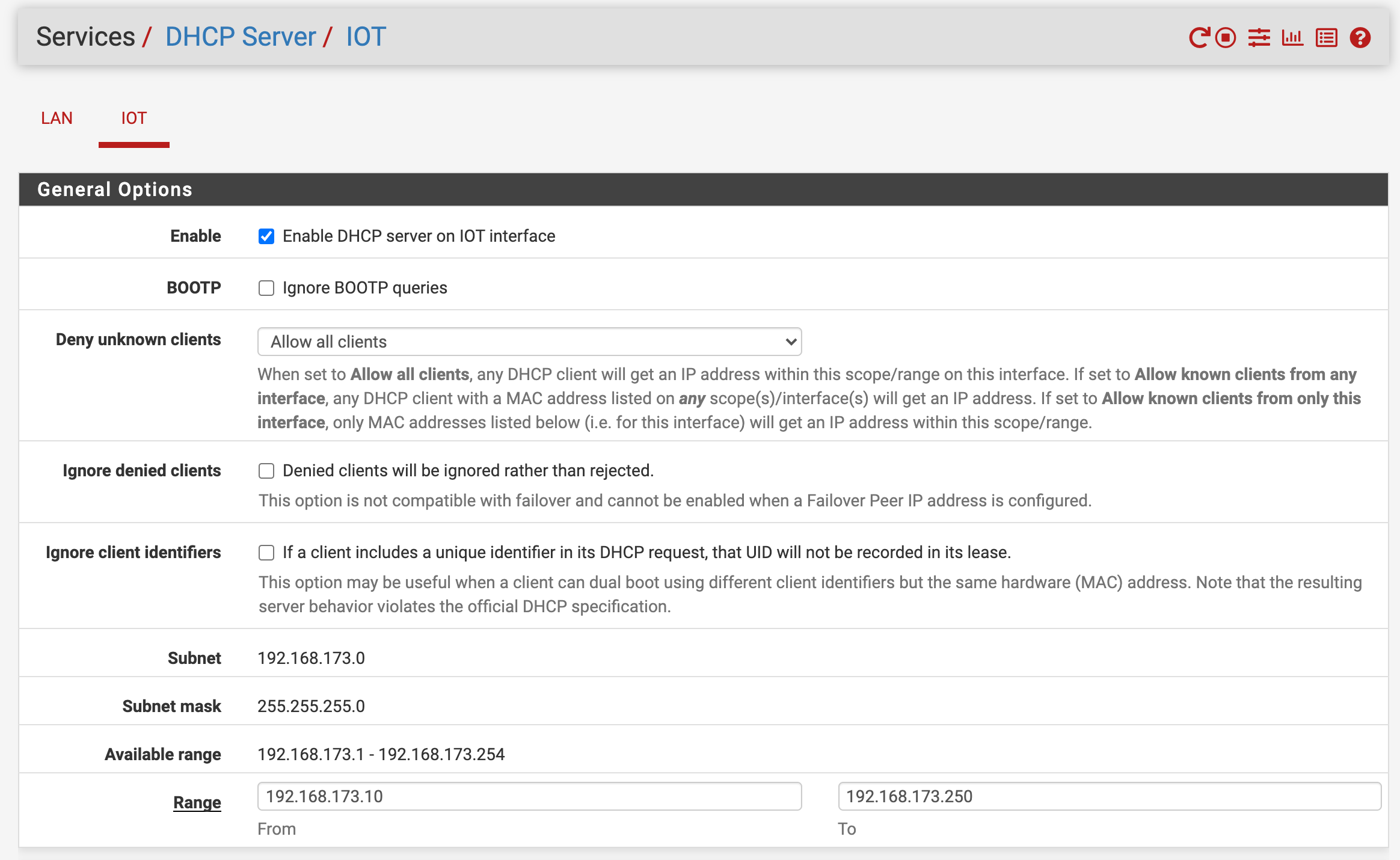
VLAN 4093 - IOT. 192.168.173.0/24 used as internet of things with no access to LAN (via firewall rules). DHCP configured to allow all clients.
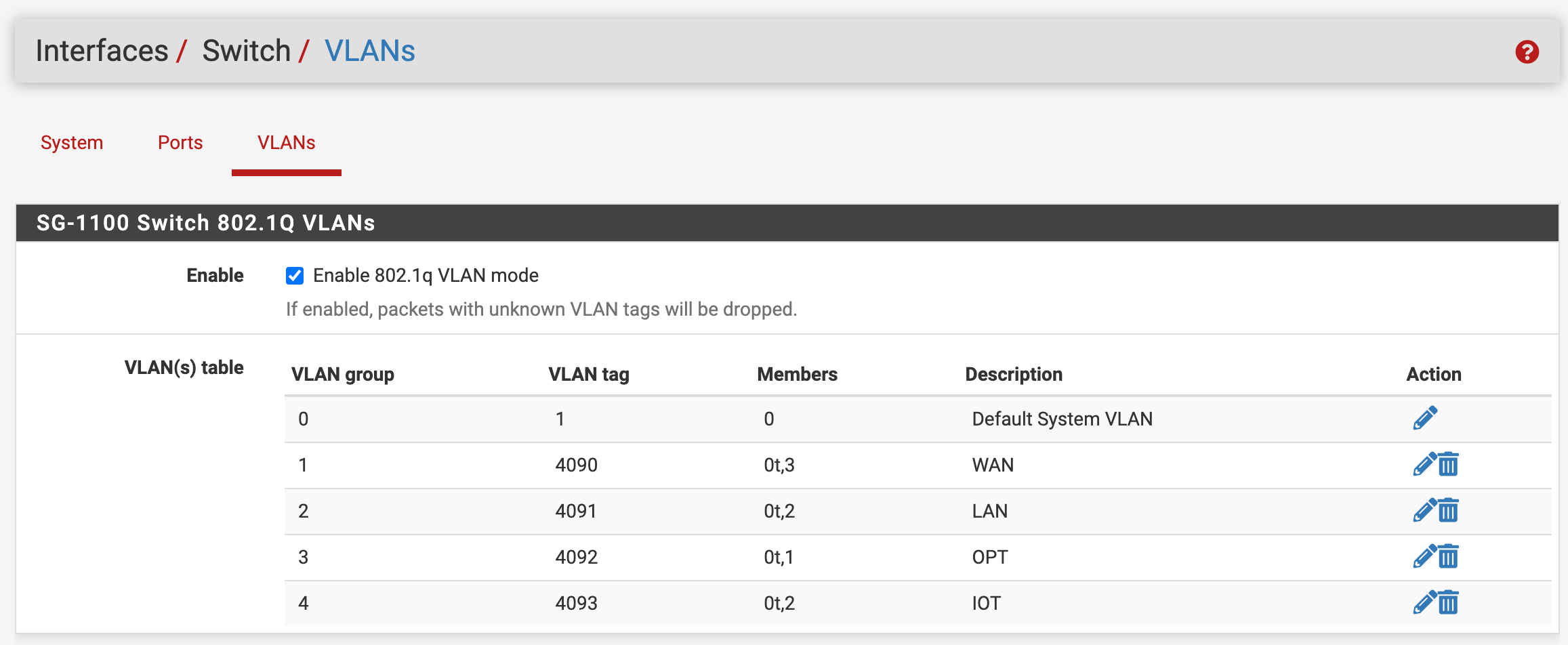
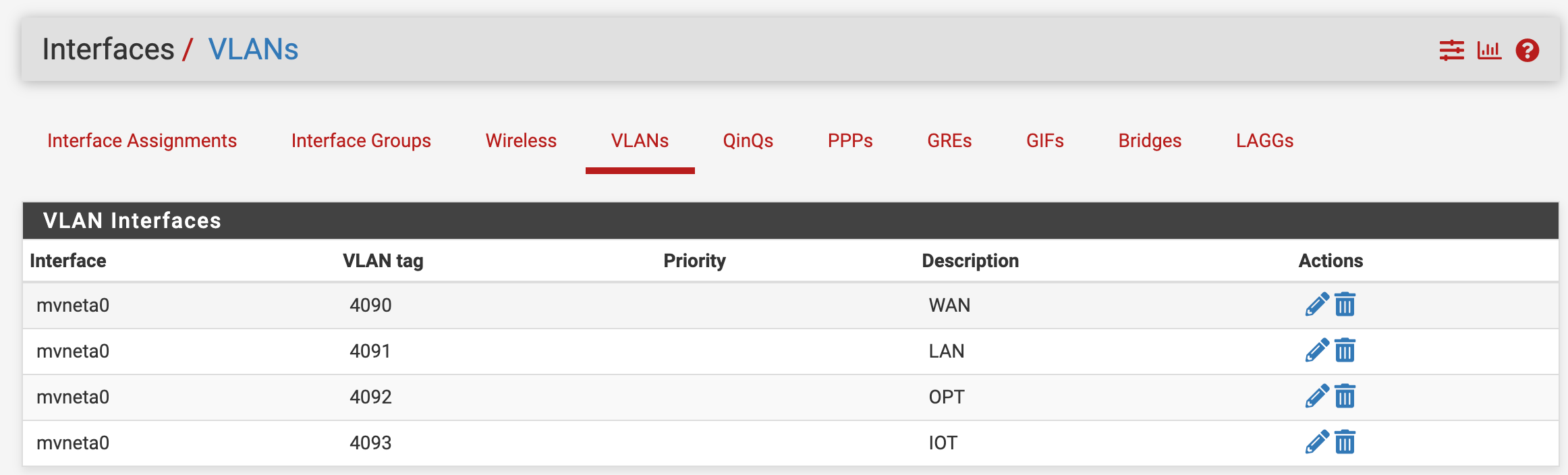
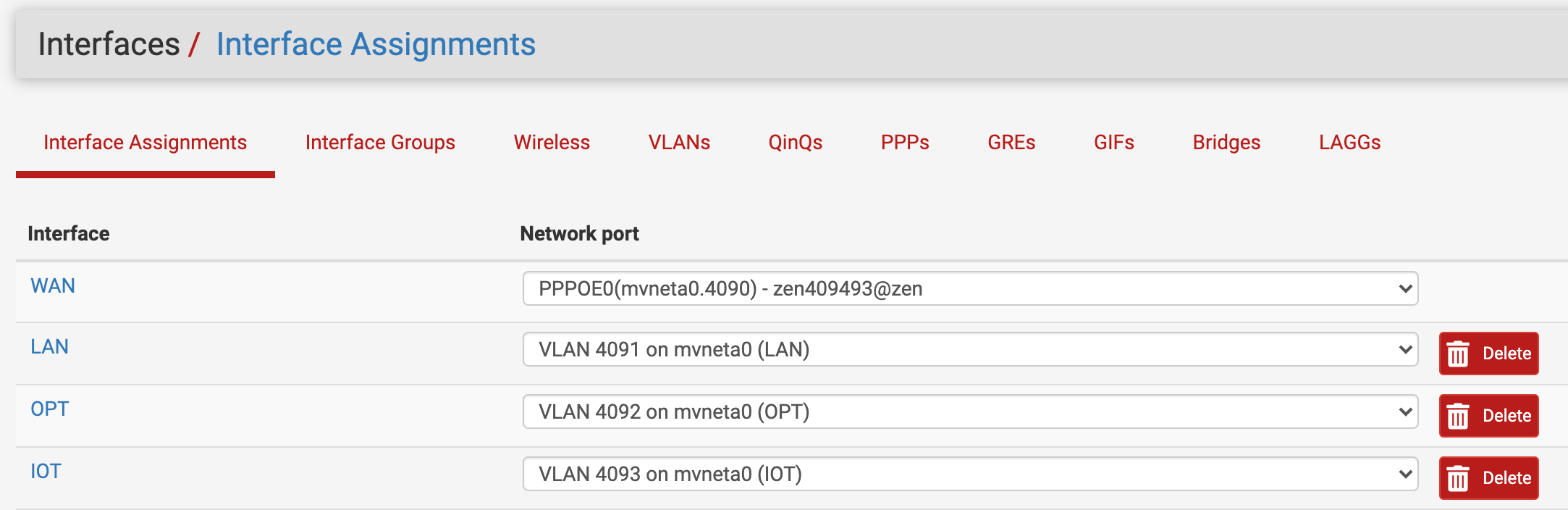
I've setup both VLAN's as interfaces named LAN & IOT, and configured DHCP. I've then setup the SG-1100 switch to route VLAN 4091 & 4093 via port 2, untagged.
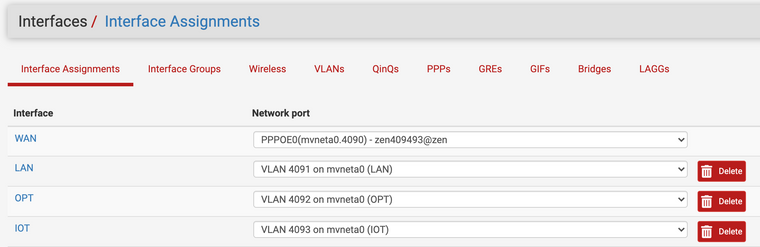
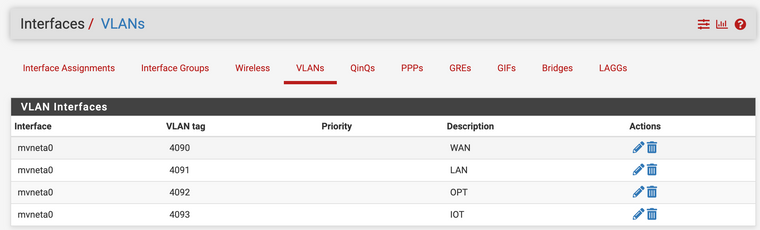
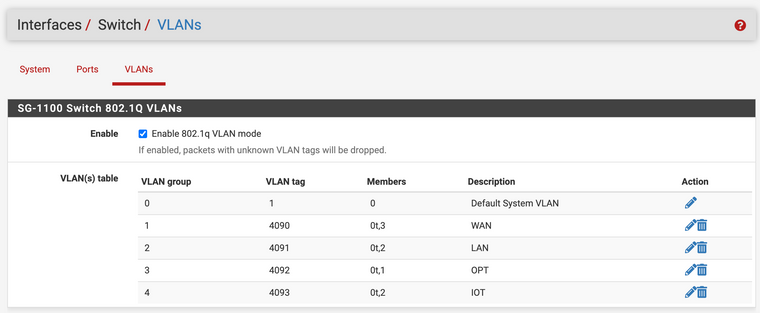
Port 2 then goes off to an unmanaged switch. In my mind, devices with mac addresses registered on the LAN DHCP server should get a 192.168.11.0/24 IP address, and anyone else assigned a 192.168.173.0/24 address.
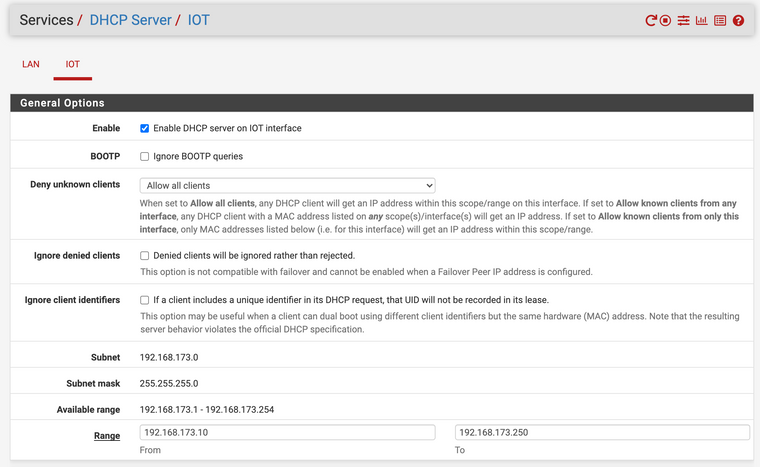
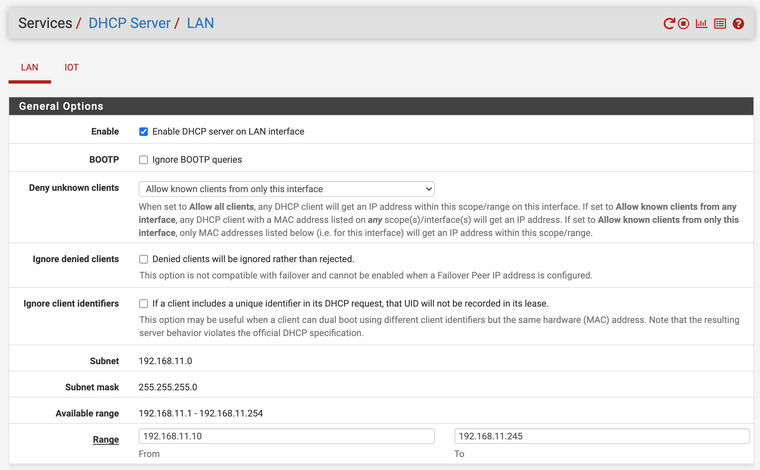
When plugging in a device registered with LAN DHCP, I get a .11.0/24 IP address no problem. But when plugging in anything else it doesn't get an IP at all.
Am I doing something wrong, is this setup not even possible? Hope someone can help... Thanks, Chris.
-
@chrispage said in Multiple untagged VLAN's on single switch port:
In my mind, devices with mac addresses registered on the LAN DHCP server should get a 192.168.11.0/24 IP address, and anyone else assigned a 192.168.173.0/24 address.
Why should that work this way?
Get a managed switch if you have to share the pfSense NICs and configure both to send packets in/out tagged.
-
@viragomann it was more that I was hoping it'd work this way. I have a mesh WiFi which I'd like both the LAN & IOT interfaces available on.
The hardware doesn't support VLAN tagging so that's not an option.
-
@chrispage
So there is no way to separate the networks on the wifi, I guess.Setting up 2 subnets on a single interface does not separate networks. You can do this for having a better view on your network, give one devices group static IPs and let the others pull IPs from DHCP. But that gives no security benefit.
Only thing you can do for enhance security with this hardware might be station separation on the wifi AP, so that it blocks direct traffic between the connected devices. But if you set this it is applied to all wifi devices.
-
@viragomann thank you for the information. So when you say two subnets on one interface, how could I configure that?
I'm not particularly looking for complete network isolation, I just want to prevent crosstalk using firewall rules.
Thanks,
Chris -
@chrispage
As I stated, assigning multiple subnets to a single interface is not a convenient way to separate network segments. Therefor I suggested to do this on the wifi.
However, filtering should be possible.Configure the subnet you want to run DHCP on as the primary in the interface settings. Then add the additional as IP alias in Firewall > Aliases. Remind to set a proper mask for the subnet. This IP can be used as gateway on the devices.
Then configure your firewall rules on that interface advisedly.