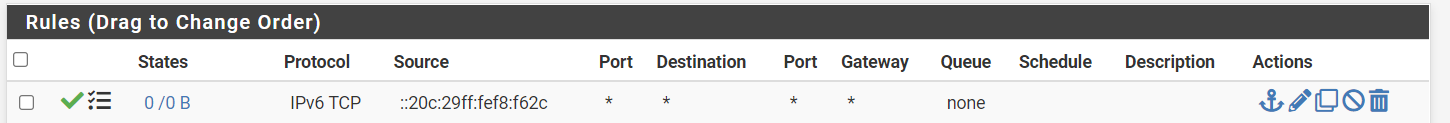
Support for IPv6 firewall entries with dynamic delegated prefix and static host address
-
@bob-dig darg my bad... I had changed from PD to static temporarely, because i sometimes lost the whole PD from the ISP, due to an error in their end. I'll revert and test it again :)
Tested and it works! Thanks a bunch. (Now I just have to figure out how to make pfsense not throw away my PD when the ISP has problems, as that removes all communication on ipv6 between my zones)
-
@kalledk said in Support for IPv6 firewall entries with dynamic delegated prefix and static host address:
(Now I just have to figure out how to make pfsense not throw away my PD when the ISP has problems, as that removes all communication on ipv6 between my zones)
Is this primarily for your LAN?
-
The problem here is that it's ambiguous. The firewall doesn't know any more than the interface the rule is on, it can't know where a target is without being told that somehow. Thus, you'd also need a way to specify the interface to which the suffix should be appended, which doesn't yet exist. That's similar to, but not the same as, the feature that was implemented. That would be a separate feature request since the first part has already been implemented.
-
@bob-dig said in Support for IPv6 firewall entries with dynamic delegated prefix and static host address:
Is this primarily for your LAN?
No and yes. I have multiple zones at home, but also multiple VPN tunnels (they are also trouble when the PD changes), and also servers that is reached via their ipv6 from the internet.
I simply try to move my stuff to ipv6 only (for the experience and for learning the problems our customers will face)
And as this is a personal line, I can't really justify the cost of a static ipv6 prefix as that requires a business line here.
But thanks again @bob-dig that is my headache, and I might solve it by finding a provider that doesn't have a messed up DHCPv6 system :D
-
@jimp said in Support for IPv6 firewall entries with dynamic delegated prefix and static host address:
The problem here is that it's ambiguous. The firewall doesn't know any more than the interface the rule is on, it can't know where a target is without being told that somehow. Thus, you'd also need a way to specify the interface to which the suffix should be appended, which doesn't yet exist. That's similar to, but not the same as, the feature that was implemented. That would be a separate feature request since the first part has already been implemented.
I understand why it doesn't work, but I try to point out, that the solution implemented doesn't "really" work in most usecases. As in rules are matched on the interface the traffic arrives on, which almost never is the interface with the host you are trying to protect. Therefore all rules that has the host as destination won't be able to use this. This is more or less only useable for rules that deny traffic from the host (which people rarely use in my experience), and also is what is talked about in the issue
One possible way to do this would be to add an item to the Destination drop-down (i.e. LAN Prefix) and allow the host portion of the address to be entered into the text box.
Another possible way would be to have a token that could be entered into the Address box, that is replaced with the prefix during rule generation.( As in this is feedback - I'm happy that this was added !!! )
-
@kalledk said in Support for IPv6 firewall entries with dynamic delegated prefix and static host address:
I simply try to move my stuff to ipv6 only (for the experience and for learning the problems our customers will face)
Yeah, that is asking for trouble.

In reality, at least around here, you always will have some sort of IPv4 via DS-Lite and CG-NAT (but not for incoming connections). But if your IPv6 Internet is unstable, then it absolutely makes no sense to go for IPv6 only.If it would be primiraly for LAN, you could use ULAs and later NAT them with the pfSense WAN-IPv6 address to the internet...
-
Granted what you are trying to do would be nice to support, but while that may be your use case it is not "most" use cases from what we've seen.
Most of the things we see are passing/blocking from specific sources to more general destinations (e.g. specific ports, but not specific destination hosts or networks).
-
@jimp said in Support for IPv6 firewall entries with dynamic delegated prefix and static host address:
Granted what you are trying to do would be nice to support, but while that may be your use case it is not "most" use cases from what we've seen.
Most of the things we see are passing/blocking from specific sources to more general destinations (e.g. specific ports, but not specific destination hosts or networks).
That I can't argue with, if that's your experience. Then my only "card" is the WAN interface, where I would normally put hosts in destination.
Just out of curiosity would a rule that you normally see be something like APP_HOST -> DB_NET port 3306 on the interface that houses APP_HOST?
-
@bob-dig said in Support for IPv6 firewall entries with dynamic delegated prefix and static host address:
If it would be primiraly for LAN, you could use ULAs and later NAT them with the pfSense WAN-IPv6 address to the internet...
I know, but then I would have to go back to split dns, one of the nightmares I try to get away from

-
@kalledk said in Support for IPv6 firewall entries with dynamic delegated prefix and static host address:
Just out of curiosity would a rule that you normally see be something like APP_HOST -> DB_NET port 3306 on the interface that houses APP_HOST?
It depends on the implementation/user/whatever they want. Normally there would be block rules preventing communicating with the DB Net entirely and then above that some pass rules from specific hosts.
While some people choose to only allow specific source hosts to specific destination hosts in a DB net, usually people don't get that fine-grained, either because the sources need to reach most if not all the resources in the target network, or because there aren't that many to bother with being that specific. Either way if someone has to get that complex with rules it's highly unusual for them to be using any kind of dynamic addressing like prefix delegation.
-
@jimp said in Support for IPv6 firewall entries with dynamic delegated prefix and static host address:
While some people choose to only allow specific source hosts to specific destination hosts in a DB net, usually people don't get that fine-grained, either because the sources need to reach most if not all the resources in the target network, or because there aren't that many to bother with being that specific. Either way if someone has to get that complex with rules it's highly unusual for them to be using any kind of dynamic addressing like prefix delegation.
Now that I can completely agree with! But may I suggest that you name the feature in another way? As this works with and without prefix delegation, and is more concerned about using a shortform (host part only) on interfaces.
This is based on that I only understood the limit, when I read the sourcefile, and realized it did not use my PD, but the network the interface was assigned even if it was static.
-
 M mlohr referenced this topic on
M mlohr referenced this topic on
-
 M mlohr referenced this topic on
M mlohr referenced this topic on
-
M marcg referenced this topic on
-
M marcg referenced this topic on
-
M marcg referenced this topic on
-
M marcg referenced this topic on