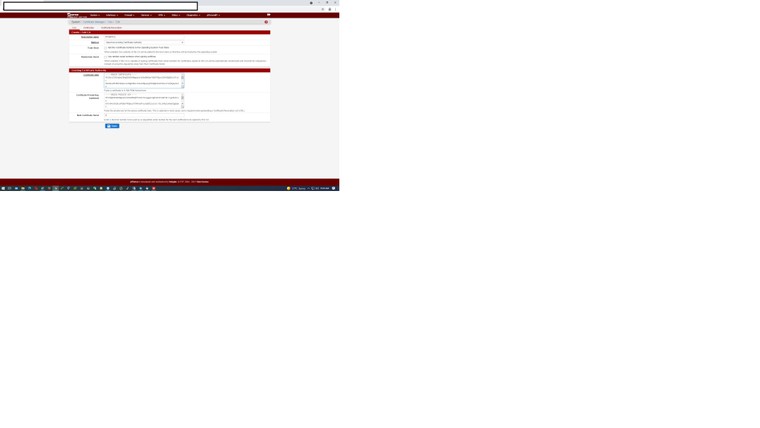
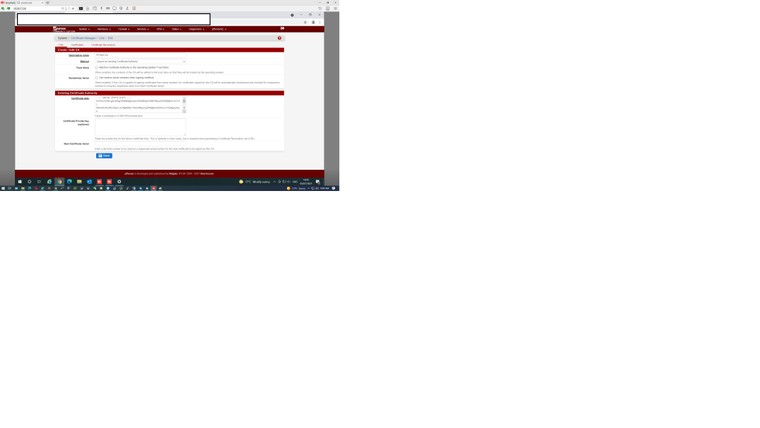
Error: TLS key negotiation failed
-
And in client in pfsense i recived this messages:
Jun 30 14:33:12 openvpn 77371 SIGUSR1[soft,ping-restart] received, process restarting
Jun 30 14:33:12 openvpn 77371 [UNDEF] Inactivity timeout (--ping-restart), restarting
Jun 30 14:32:12 openvpn 77371 UDPv4 link remote: [AF_INET]81.........:44441
Jun 30 14:32:12 openvpn 77371 UDPv4 link local (bound): [AF_INET]92............:0
Jun 30 14:32:12 openvpn 77371 TCP/UDP: Preserving recently used remote address: [AF_INET]...............:44441
Jun 30 14:32:12 openvpn 77371 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jun 30 14:32:12 openvpn 77371 WARNING: No server certificate verification method has been enabled. -
i use 3 servers with pfsense
1 is server-vpn
2 is client-vpn
3 client-vpn
all have installed pfsense and use Mode: Peer to Peer ( SSL/TLS ) and after update VPN disconected and no connect again ... all have TUN option enabled.Jul 2 12:51:36 openvpn 20529 .....:59685 TLS Error: TLS handshake failed
Jul 2 12:51:36 openvpn 20529 ......:59685 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Jul 2 12:49:29 openvpn 20529 Initialization Sequence Completed
Jul 2 12:49:29 openvpn 20529 UDPv4 link remote: [AF_UNSPEC]
Jul 2 12:49:29 openvpn 20529 UDPv4 link local (bound): [AF_INET]127.0.0.1:44441
Jul 2 12:49:29 openvpn 20529 /usr/local/sbin/ovpn-linkup ovpns3 1500 1622 10.1.1.1 255.255.255.0 init
Jul 2 12:49:29 openvpn 20529 /sbin/ifconfig ovpns3 10.1.1.1 10.1.1.2 mtu 1500 netmask 255.255.255.0 up
Jul 2 12:49:29 openvpn 20529 TUN/TAP device /dev/tun3 opened
Jul 2 12:49:29 openvpn 20529 TUN/TAP device ovpns3 exists previously, keep at program end
Jul 2 12:49:29 openvpn 20529 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Jul 2 12:49:29 openvpn 20529 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Jul 2 12:49:29 openvpn 20529 WARNING: experimental option --capath /var/etc/openvpn/server3/ca
Jul 2 12:49:29 openvpn 20529 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jul 2 12:49:29 openvpn 20366 library versions: OpenSSL 1.1.1k-freebsd 25 Mar 2021, LZO 2.10
Jul 2 12:49:29 openvpn 20366 OpenVPN 2.5.1 amd64-portbld-freebsd12.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Apr 5 2021
Jul 2 12:49:29 openvpn 20366 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.In dashboard i see this in VON category: UNDEF IP:30965
-
On the server side you have :
@vinceent said in Error: TLS key negotiation failed:
Jul 2 12:51:36 openvpn 20529 .....:59685 TLS Error: TLS handshake failed
Jul 2 12:51:36 openvpn 20529 ......:59685 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)On the client side, you have :
@vinceent said in Error: TLS key negotiation failed:
Jun 30 14:32:12 openvpn 77371 WARNING: No server certificate verification method has been enabled.
Or, when you want to use TLS/SSL this implies the usage of certificates.
Your logs lines, both side, basically say : "no connection".
@vinceent said in Error: TLS key negotiation failed:
Jul 2 12:49:29 openvpn 20529 UDPv4 link local (bound): [AF_INET]127.0.0.1:44441
Normally, the OpenVPN server listens on the WAN interface ...
-
@gertjan
This i see in server
Jul 5 07:57:27 openvpn 23661 ip:14492 TLS Error: TLS handshake failed
Jul 5 07:57:27 openvpn 23661 ip:14492 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)Common Name
UNDEF ip:39772 -
See this one : Configuring OpenVPN Remote Access in pfSense Software
This is the one and only pfSense OpenVPN server setup guide.
See also the 2 (3) older OpenVPN videos present on the Youtube Netgate channel : you'll be needing them afterwards.
When set up, also test if your UDP port can be reached from the Internet :
https://www.ipvoid.com/udp-port-scan/
Enter your IP and the " Scan a custom port " which is 1194.You should get a
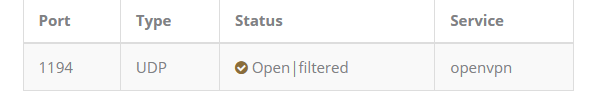
-
@gertjan i use port 44442
And in firewall rules is added to allow !!! -
@gertjan 44442 UDP Open|filtered unknown
-
@vinceent said in Error: TLS key negotiation failed:
44442 UDP Open|filtered unknown
Most probably ok.
But I advise you use the set by set setup of an OpenVPN server using exactly the same settings a the example video.
That will work.Only when you have a working setup, you can start changing things.
Btw :
No "help me" PM's please. Use the forum.means :
No "help me" PM's please. Use the forum. -
@gertjan
this is in server:
Jul 10:18:17 openvpn 23661 ip:14492 TLS Error: TLS handshake failed
Jul 10:18:17 openvpn 23661 ip:14492 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Jul 5 10:11:17 openvpn 67094 Initialization Sequence Completed
Jul 5 10:11:17 openvpn 67094 UDPv4 link remote: [AF_UNSPEC]
Jul 5 10:11:17 openvpn 67094 UDPv4 link local (bound): [AF_INET]ip:44442
Jul 5 10:11:17 openvpn 67094 /usr/local/sbin/ovpn-linkup ovpns4 1500 1622 ip 255.255.255.0 init
Jul 5 10:11:17 openvpn 67094 /sbin/ifconfig ovpns4 ip ip mtu 1500 netmask 255.255.255.0 up
Jul 5 10:11:17 openvpn 67094 TUN/TAP device /dev/tun4 opened
Jul 5 10:11:17 openvpn 67094 TUN/TAP device ovpns4 exists previously, keep at program end
Jul 5 10:11:17 openvpn 67094 WARNING: experimental option --capath /var/etc/openvpn/server4/ca
Jul 5 10:11:17 openvpn 67094 Initializing OpenSSL support for engine 'devcrypto'
Jul 5 10:11:17 openvpn 67094 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jul 5 10:11:17 openvpn 67050 library versions: OpenSSL 1.1.1k-freebsd 25 Mar 2021, LZO 2.10
Jul 5 10:11:17 openvpn 67050 OpenVPN 2.5.1 amd64-portbld-freebsd12.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Apr 5 2021
Jul 5 10:11:17 openvpn 67050 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
This is in client
Jul 5 10:13:38 openvpn 33001 UDPv4 link remote: [AF_INET]ip:44442
Jul 5 10:13:38 openvpn 33001 UDPv4 link local (bound): [AF_INET]ip:0
Jul 5 10:13:38 openvpn 33001 TCP/UDP: Preserving recently used remote address: [AF_INET]ip:44442
Jul 5 10:13:38 openvpn 33001 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jul 5 10:13:38 openvpn 33001 WARNING: No server certificate verification method has been enabled.
Jul 5 10:13:33 openvpn 33001 SIGUSR1[soft,ping-restart] received, process restarting
Jul 5 10:13:33 openvpn 33001 [UNDEF] Inactivity timeout (--ping-restart), restarting
Jul 5 10:12:33 openvpn 33001 UDPv4 link remote: [AF_INET]ip:44442
Jul 5 10:12:33 openvpn 33001 UDPv4 link local (bound): [AF_INET]ip:0
Jul 5 10:12:33 openvpn 33001 TCP/UDP: Preserving recently used remote address: [AF_INET]ip:44442
Jul 5 10:12:33 openvpn 33001 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jul 5 10:12:33 openvpn 33001 WARNING: No server certificate verification method has been enabled.down (pending) (pending)
and after past a few minutes
VL/MT UDP4 reconnecting; ping-restart Mon Jul 5 10:26:59 2021 (pending) (pending) -
The server looks fine.
Go for '@vinceent said in Error: TLS key negotiation failed:
Jul 5 10:11:17 openvpn 67050 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
Use :

and make sure the config on the client side is using the same setting(s).
This is what the client side says :
WARNING: No server certificate verification method has been enabled.
so compare cert info in the config file of the client.
It should correspond with the server side.Example : If the server needs a "certificate verification method" and the client has no (or wrong certs) then it will fail.
Check and compare the config files on both side.
The server config "opvn" file is here : /var/etc/openvpn/server4/ -
@gertjan
Existing Certificate Authority > Certificate data ? in server and in client need to be same ? -
-
@vinceent
Alaways recived this:UNDEF and
Jul 5 11:47:14 openvpn 99092 ip:34508 TLS Error: TLS handshake failed
Jul 5 11:47:14 openvpn 99092 ip:34508 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) -
What should I do with your images ?
You want to see mine ?
( if that might help, ok, why not : )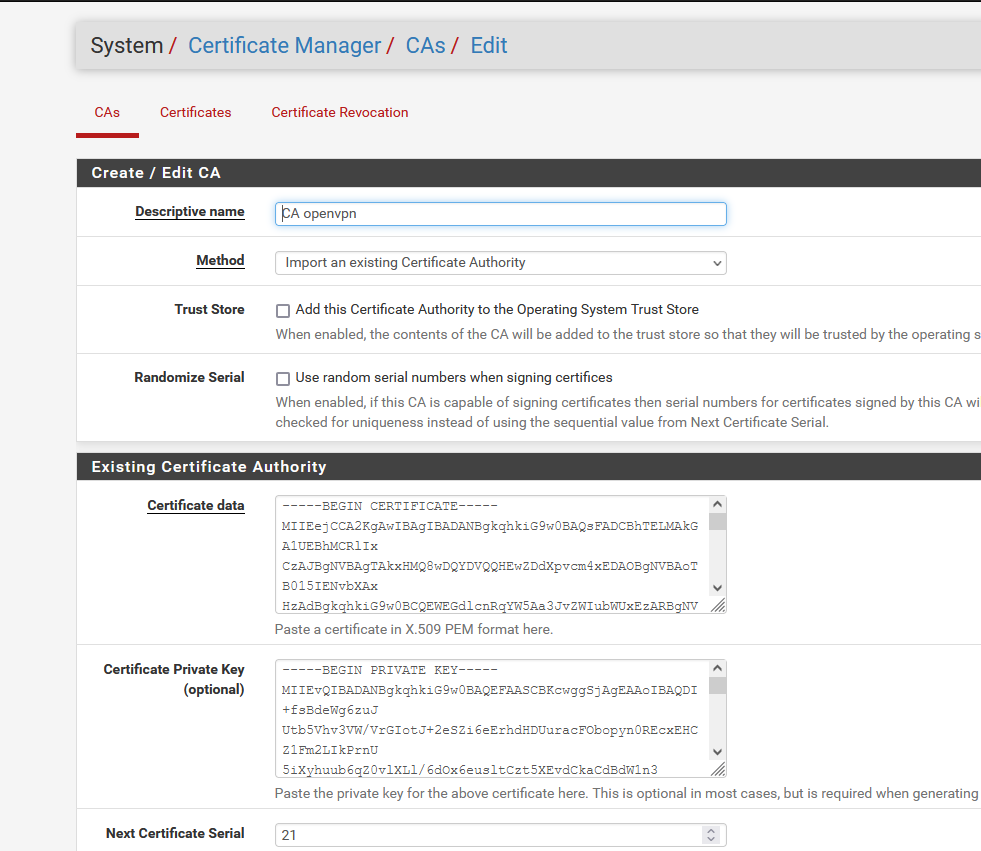
With this "CA openvpn" (I invented this name) I made several certificates :
One for the OpenVPN server :
*
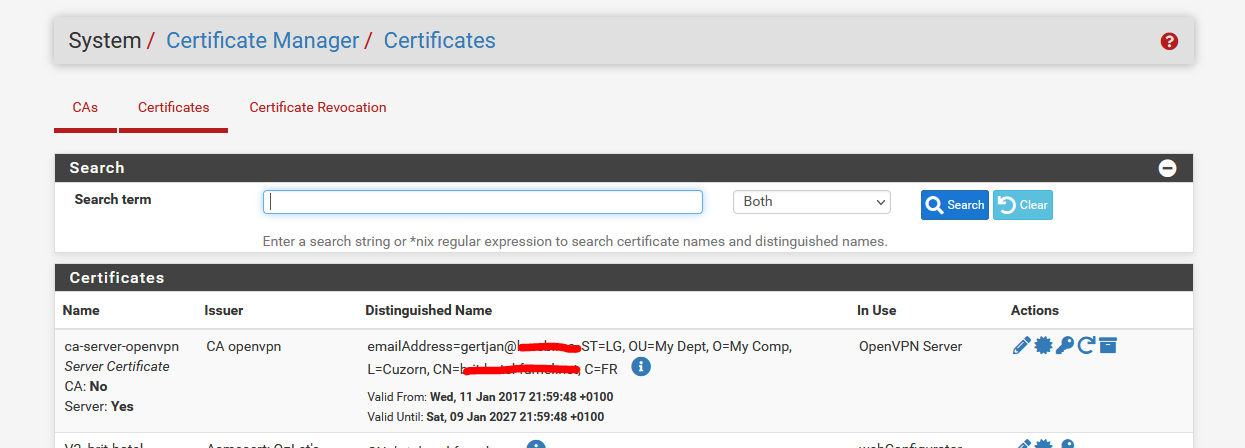
This certificate is used by the OpenVPN server.
And several for the OpenVPN clients certificates, like :
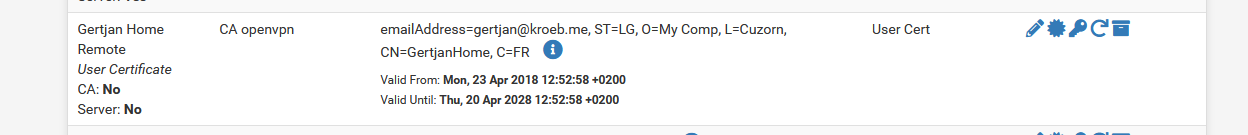
based upon the "CA openvpn".
Again, I advise you to use the Netgate OpenVPN video. Just copy step by step.
-
@gertjan said in Error: TLS key negotiation failed:
Netgate OpenVPN
can to give me please one link to see !!!
i use PEER TO PEER SSL/TLS !!!
tNX VERY MUCH FOR YOUR HELP -
It's a video, so install Youtube.
Then go to the Netgate channel.
You'll find many OpenVPN video's.
Like this one : Configuring OpenVPN Remote Access in pfSense Softwareedit : the video hidden, look :
It's on the first link proposed !!!!!!