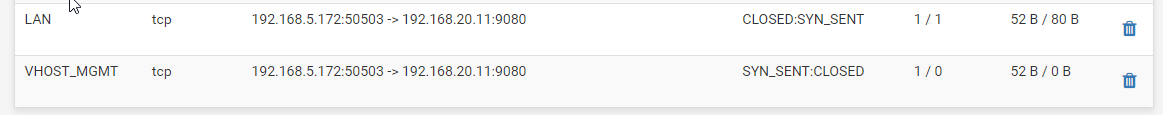
VLAN can't ping pfSense address
-
@johnpoz said in VLAN can't ping pfSense address:
I thought you couldn't ping the pfsense 20.x address from something on the 20 vlan..
That's true too.
-
-
@johnpoz thanks. I solve routing issue using your the link you share.
Unfortunatelly I can't solve the traffic issue inside VLAN 20.
But Iam gonna give some try to switch config.I guess the problem is there right now.
Thanks.
-
Also configured the servers (ESXi) with vlan ID 20.
How is pfsense connected to the network - via a switch? If vlan 20 is tagged in pfsense, then it needs to be tagged on your switch port its connected to.
When it comes to the connection into esxi. What vswitch and port group is connected to? If you want esxi to pass the tags then your vswitch/port group needs to have vlan ID 4095 set to pass the tags.
Or you can just let esxi handle the tags and set them on your vswitch/port group and the VM interface connected to this would not have any tags set.
-
@johnpoz said in VLAN can't ping pfSense address:
How is pfsense connected to the network - via a switch? If vlan 20 is tagged in pfsense, then it needs to be tagged on your switch port its connected to.
Yes. pfsense connects via switch. Vlan is tagged in pfsense:

And it's tagged on switch to ( as trunk port)
When it comes to the connection into esxi. What vswitch and port group is connected to? If you want esxi to pass the tags then your vswitch/port group needs to have vlan ID 4095 set to pass the tags.
The switch ports where ESXi is connected are trunked to. and VLAN 20 is configured at ESXi management NIC.
Iam reading this:
https://docs.netgate.com/pfsense/en/latest/recipes/switch-vlan-configuration.html
To try to understand a little bit more about the correct config.
I have change the switch without success. Iam gonna set servers ports to access and remove all vlans config from switch and ESXi to try to setting this up from bottom to top.If setting ESXi without vlan config and switch ports as access, then I guess if the problem still persist I will have to take a look at pfsense, but if the problem dissapear then I have to take a look at switch config.
Unfortunatelly I am not a pfSense neither networking expert. So I can't tell yet where the error is.
Thanks for your time.
Or you can just let esxi handle the tags and set them on your vswitch/port group and the VM interface connected to this would not have any tags set.
-
@daniel1972 said in VLAN can't ping pfSense address:
VLAN 20 is configured at ESXi management NIC.
So your trying to get to esxi managment? Or a vm?
I would suggest just connect a normal PC to the port - would just be access port in vlan 20.. does that work?
esxi and vlan with tagging can be bit much for someone new to it.. Are you doing VST or VGT, or do you have multiple interfaces in your esxi host and going to do EST?
This might help
https://kb.vmware.com/s/article/1003806But I would get your switch and pfsense working with just a PC ending up in the vlan you want first before playing with esxi and vlans.
-
@johnpoz Thanks for your help. Iam gonna try with a PC as you said in a access port.
Well I really don't know wich virtual tagging method are gonna be finally used. That's an integrator VMWare consultant matter.
Iam trying to figure it out why is this enviroment not working (it's someway similar to another ones we alredy had)
But following your tip Iam gonna start from simplest config as I can.
Thanks again.
-
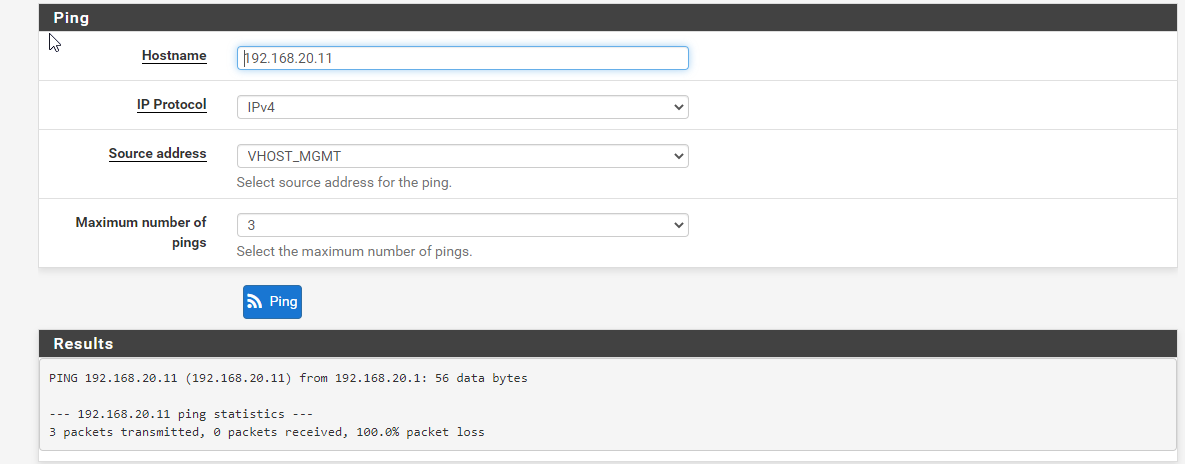
I had setup a Notebook in an access port with an IP in VLAN 20 range (192.168.20.64) and can't ping it at all.
I just get Destination Host Unreachable from this notebook and from one ESXi server (removed vlan config and set switch port to access).
Iam planning to restart pfSense. Not more changes for today.
Thanks.
-
@daniel1972 said in VLAN can't ping pfSense address:
Iam planning to restart pfSense.
That not going to fix anything.. The only time you would ever have to reboot pfsense is on an upgrade..
What switch are you setting vlans on? Is this a netgate appliance - and you are using the switchports on it?
Setting up vlans is literally 30 seconds.. If you working with netgate appliance and you wanting to put port in a vlan - your going to have to show your switch config from your appliance.
If this is some other switch?
-
@johnpoz thanks for your kind help.
well, at least I learnt something (when to restart pfsense).
I have found this in my arp table:
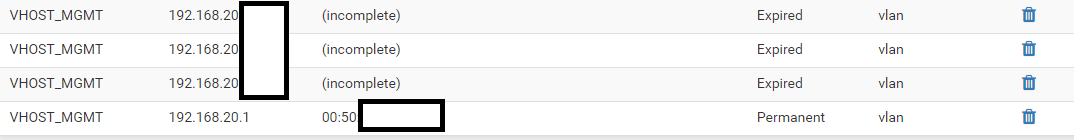
Still can't figure it out what is happening here (pfsense or switch config).
Iam gonna try a couple of things and then upload switch config. It's a CISCO SG-250. Very simple switch.
Iam using it to test this environment and then move to production one. -
Well lets see the config from your 250, I have 350s
Yeah your right simple config.. Like I said this is 30 seconds.. Did you actually create vlan 20 in your cisco switch?
pfsense -- trunk 20T -- cisco -- Acess 20U --- PC
incomplete in the arp table - just means nothing answered for the IP you arp for
here
[21.05-RELEASE][admin@sg4860.local.lan]/root: ping 192.168.9.44 PING 192.168.9.44 (192.168.9.44): 56 data bytes ^C --- 192.168.9.44 ping statistics --- 3 packets transmitted, 0 packets received, 100.0% packet loss [21.05-RELEASE][admin@sg4860.local.lan]/root: arp -a | grep 192.168.9.44 ? (192.168.9.44) at (incomplete) on igb0 expired [ethernet] [21.05-RELEASE][admin@sg4860.local.lan]/root:Because there is no 9.44 - You have a problem with just layer 2 connectivity if you can not arp the mac
I create a new VLAN (ID 20) in an OPT Interface.
So is there a native network on this opt interface? Do you have the interface enabled?
-
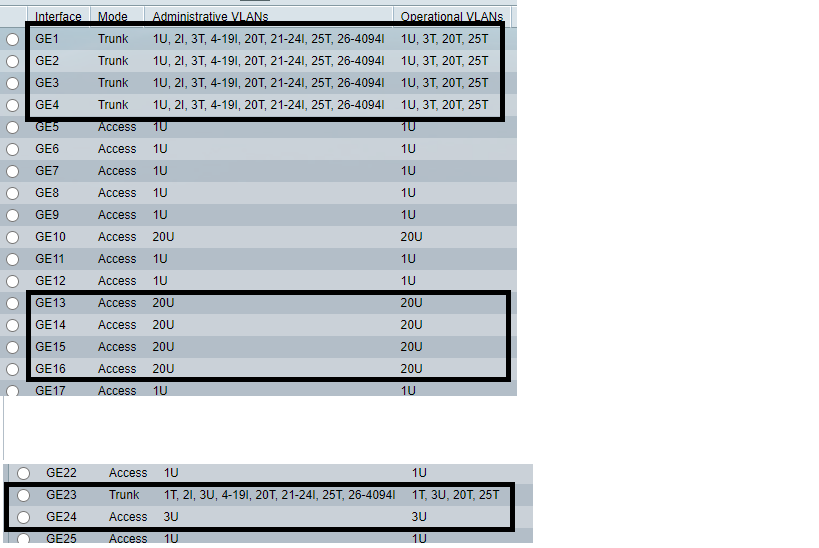
@johnpoz here it is, switch config:
VLANs:
1 - Not used at all
3 - traffic alredy passing across pfsense (its working)
20 and 25 - My New VLANs.Iam just only talking about VLAN 20 because I assume that if a fix one, fix both.
Switch:
ports: 1-4 trunk ports (1st. attempt)
port: 10 - VLAN 20 Untagged port for my laptop
ports: 13-16 untagged ports on VLAN 20 (where my hosts are right now)
port 23: where pfsense is connected to.
port 24: VLAN 3 traffic (working Ok)That's all.
-
Why all the I vlans (internal used)?
You don't have a PVID set? Your access 20U port should really show 20UP, Without the pvid being set for the vlan, it would default to 1..
Why are you tagging vlan 1 on port 23?
Here - so 5 is going to pfsense that has native network (vlan2) and vlans on it tagged.
Port 16 goes to a rasberry pi in my vlan 3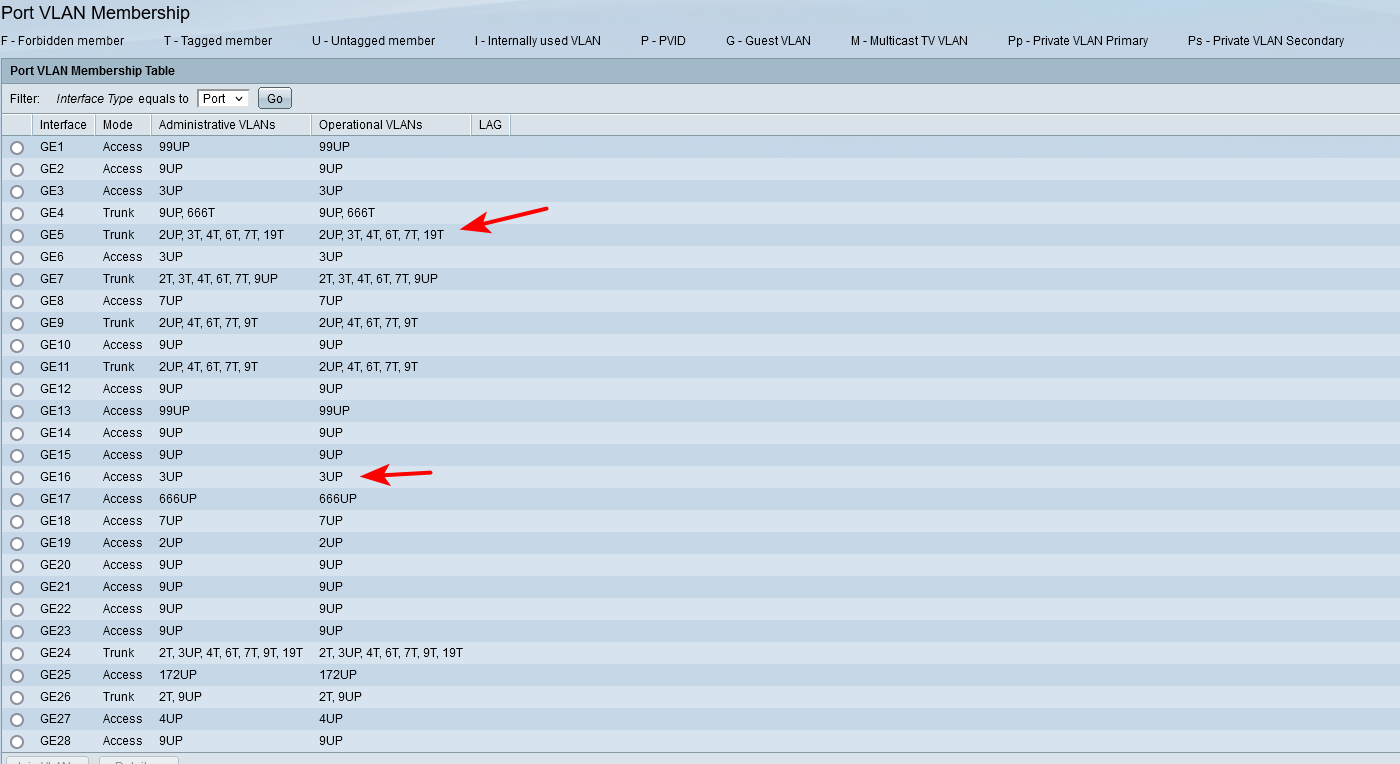
Notice the P - you need that set on access port or even trunk port where there is going to be untagged traffic so switch knows what vlan any ingress traffic it sees into that port what vlan its on.
-
@johnpoz Yes I is Internal.
Well, that image is from a similar switch. But as you can see in my switch there is any port with P, even those ones that haven't been configured (like 5,6, or 7).
Iam gonna trying to force it.
Thanks.
-
@daniel1972 said in VLAN can't ping pfSense address:
Iam gonna trying to force it.
On the top of your listing of where you show - does it show P for PVID.. A port has to have a vlan that it puts untagged traffic too.. It not like something only unique to a specific cisco switch ;)
Any managed/smart switch that understands them has to be able to set the pvid... Maybe your switch auto changes it to be what the Access vlan is - but I doubt that to be honest.
Out of the box switch would be vlan 1 would be native, and all ports would have PVID of 1.. If you changed yoru default native vlan.. Then the default of all ports would be that vlan.. There has to be a place to set the pvid of port you put in either trunk mode with native vlan or on your access ports.. Even cheap $40 smart switches allow this.
-
@johnpoz Yes. I agree. It's just that I alredy changed, but it's not reflected in the administrative console.
There is a Join VLAN button, where you can setup this. Iam gonna send a pic. Pheraps Iam missing an step somewhere....
Thanks-.
-
@johnpoz here is what Iam talking about:
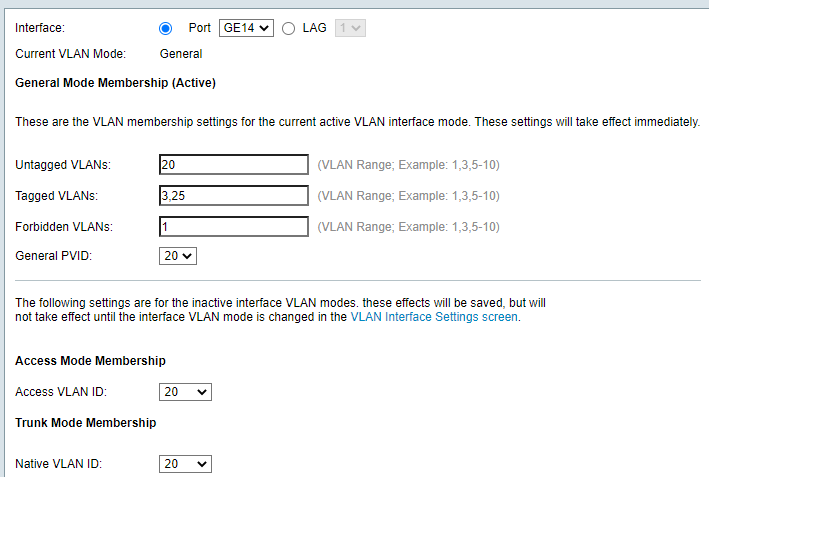
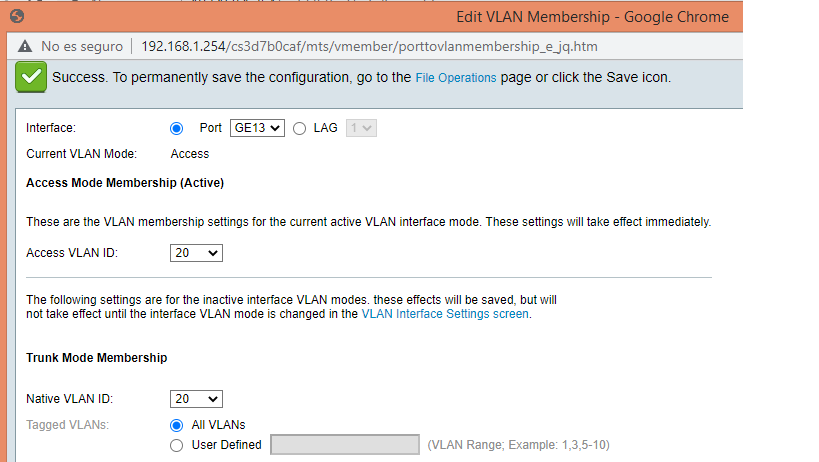
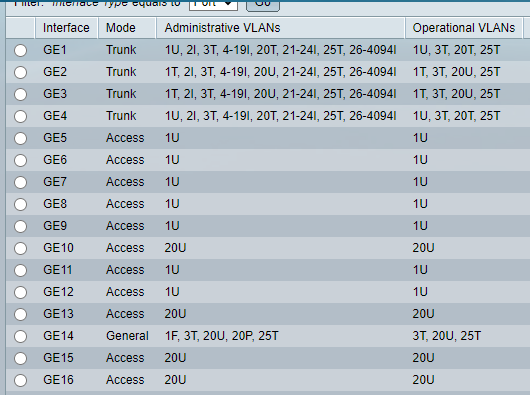
-
Ok - not how I would do it at all ;)
There is really zero use case for "general" ports - seems like your just kind of clicking random shit hoping something works to be honest..
General allows for multiple untagged - which is really a big NO NO!!
Again going to ask why you have vlan 1 tagged on the port that is connected to pfsense? ge23.. What is this actual interface setup on pfsense? That is showing 3U and 1T just makes
What is the physical configuration of this interface on pfsense. So it has a native network whatever your vlan 3 is, and then 2 vlans setup on it 20 and 25?
-
@johnpoz said in VLAN can't ping pfSense address:
Ok - not how I would do it at all ;)
There is really zero use case for "general" ports - seems like your just kind of clicking random shit hoping something works to be honest..You are 110% right. :-)
Iam just trying things. Iam on my own on this. No fellas to ask at my side.General allows for multiple untagged - which is really a big NO NO!!
Second thing learnt.
Again going to ask why you have vlan 1 tagged on the port that is connected to pfsense? ge23.. What is this actual interface setup on pfsense? That is showing 3U and 1T just makes
Vlan 1 is here just because is default config switch. I just use a spare switch to test things in order to not touch production one. Just want to make this work here and then move to production one. Do you believe is messing things up?
I did this to trying to understand where problem is. I belived that if a change switch and the problem still persist then I needed to focus on pfsense. But honestly I do not where else to look at inside pfsense.
Pheraps I need some professional help here.
What is the physical configuration of this interface on pfsense. So it has a native network whatever your vlan 3 is, and then 2 vlans setup on it 20 and 25?
Pfsense have physical Interface (em4) where VLANs 20 and 25 was created. I set native network traffic to vlan 3, thats right (it's the em4 nic traffic alredy exists before I create this VLANs). And vlan 20 and 25 are the new VLANs.
I could try some other things like add a new NIC. But that's not the way I wan't to go.
-
Lets see your interface config for this em4.. This is not a VM is it? This is a physical box..
example here is my interfaces on my pfsense
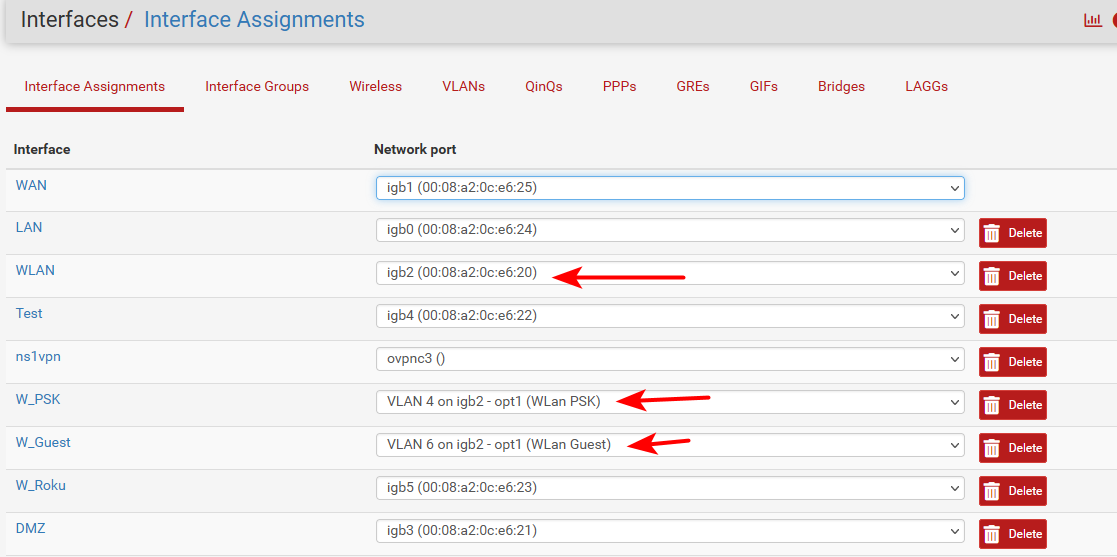
So vlan 4 and 6 are tagged, the native network on this interface is vlan 2 on my switch. That is port ge5 from above. BTW - helping you helped me trim some no longer used vlans from my switch configs ;) So now its config loos like
sg300-28#sho run int ge5 interface gigabitethernet5 description "sg4860 WLan and vlans" switchport trunk allowed vlan add 4,6 switchport trunk native vlan 2 ! sg300-28#Here is device I have on vlan 4, which port ge27..
sg300-28#sho run int ge27 interface gigabitethernet27 description casetahub switchport mode access switchport access vlan 4 ! sg300-28#This is pretty basic stuff.. So we are missing piece of the puzzle here.. If your port on your switch to pfsense for your vlan is tagged, and pfsense has the same tag and setup and enabled. And then you create an access port and put it in that vlan.. Any device you plug into that port would now be on that vlan and pfsense should see its dhcp for example. And that device and pfsense should be able to arp for the each others IP.. Be it firewall or firewall rules blocking all traffic.
My thing on ge27 is just dumb iot device so I can not arp from it. But you can see pfsense sees its mac..
[21.05-RELEASE][admin@sg4860.local.lan]/root: ping 192.168.4.81 PING 192.168.4.81 (192.168.4.81): 56 data bytes 64 bytes from 192.168.4.81: icmp_seq=0 ttl=64 time=0.516 ms 64 bytes from 192.168.4.81: icmp_seq=1 ttl=64 time=0.300 ms 64 bytes from 192.168.4.81: icmp_seq=2 ttl=64 time=0.312 ms ^C --- 192.168.4.81 ping statistics --- 3 packets transmitted, 3 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 0.300/0.376/0.516/0.099 ms [21.05-RELEASE][admin@sg4860.local.lan]/root: arp -a | grep 192.168.4.81 casetahub.local.lan (192.168.4.81) at a8:1b:6a:24:ec:26 on igb2.4 expires in 1151 seconds [vlan] [21.05-RELEASE][admin@sg4860.local.lan]/root: