Broadcast packets duplicated across VLAN
-
If you had a TP-Link switch, I'd say toss it. However, I suspect it may be a configuration issue with the switch. I don't have a Netgear switch, so I can't help you with the details.
BTW, please attach files to your post instead of using a link. Who knows where that link leads to.
-
@jknott Apologies, I have now added the screenshots.
-
I didn't say screenshot. I said files. For example, you can attach the capture file, which contains a lot more info than a screen capture. Also, one thing you can do in Wireshark to make things a bit easier is add a column for VLAN ID. That way, you can tell it at a glance, rather than hunt for it in the data. That column, like the others, can be enabled or disabled as needed. Another thing which I do, is change the layout, so the 2nd and 3rd panels are across the bottom part of the screen. This results in what I find to be the best display. I adjust the width of the 3rd panel so that has just enough space to hold the hex data, leaving maximum space for panel 2.
Here's how my Wireshark display looks:
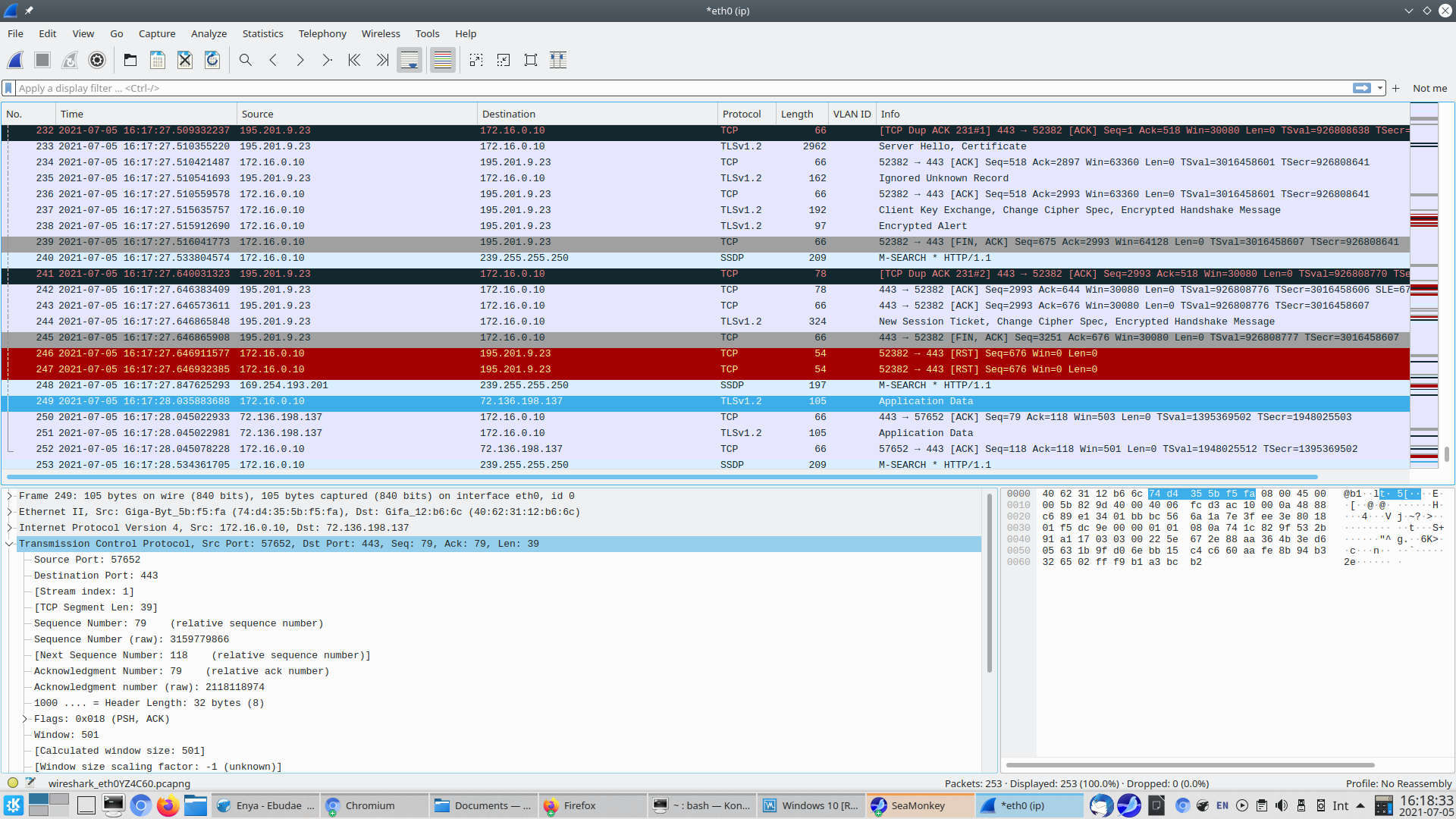
Also, why are you using a VLAN for the main LAN? Normally, that would be native LAN.
-
@nazuro said in Broadcast packets duplicated across VLAN:
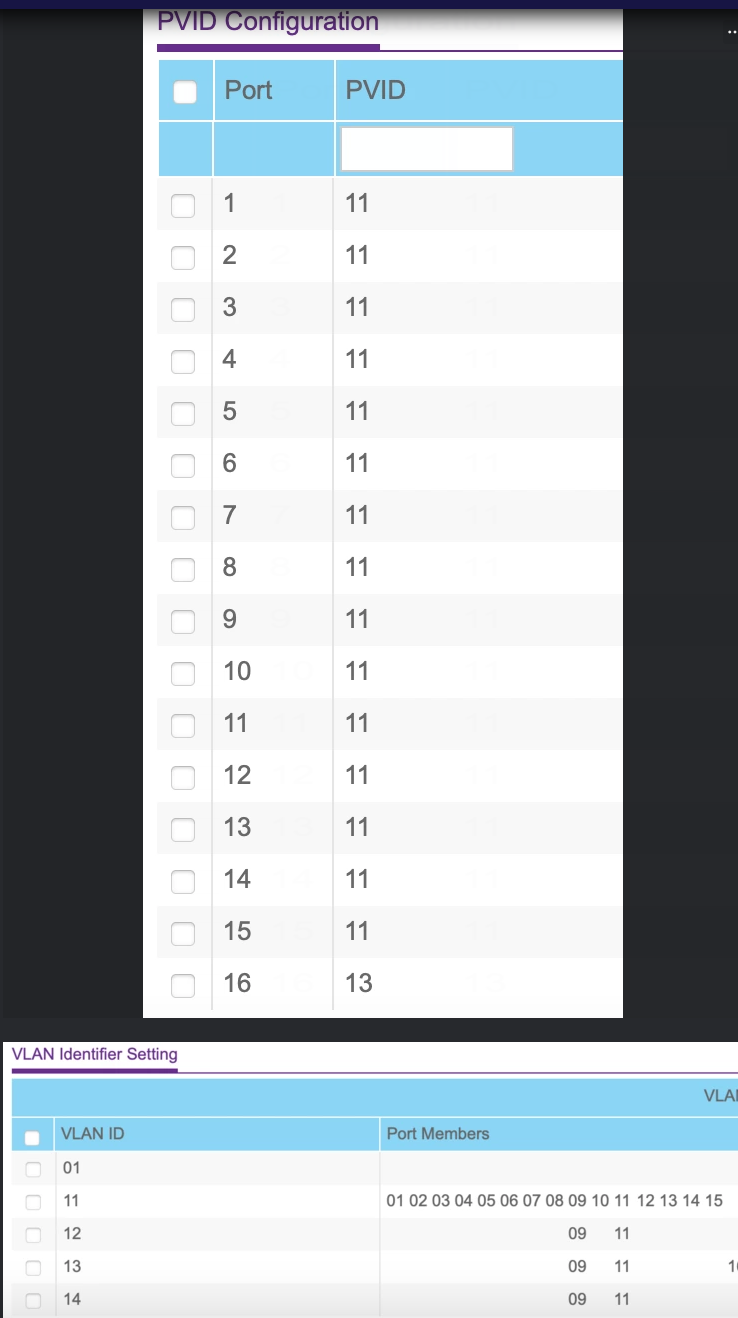
Port 11 is trunk from Unifi AP
So why is this port untagged assigned to VLAN 11?
-
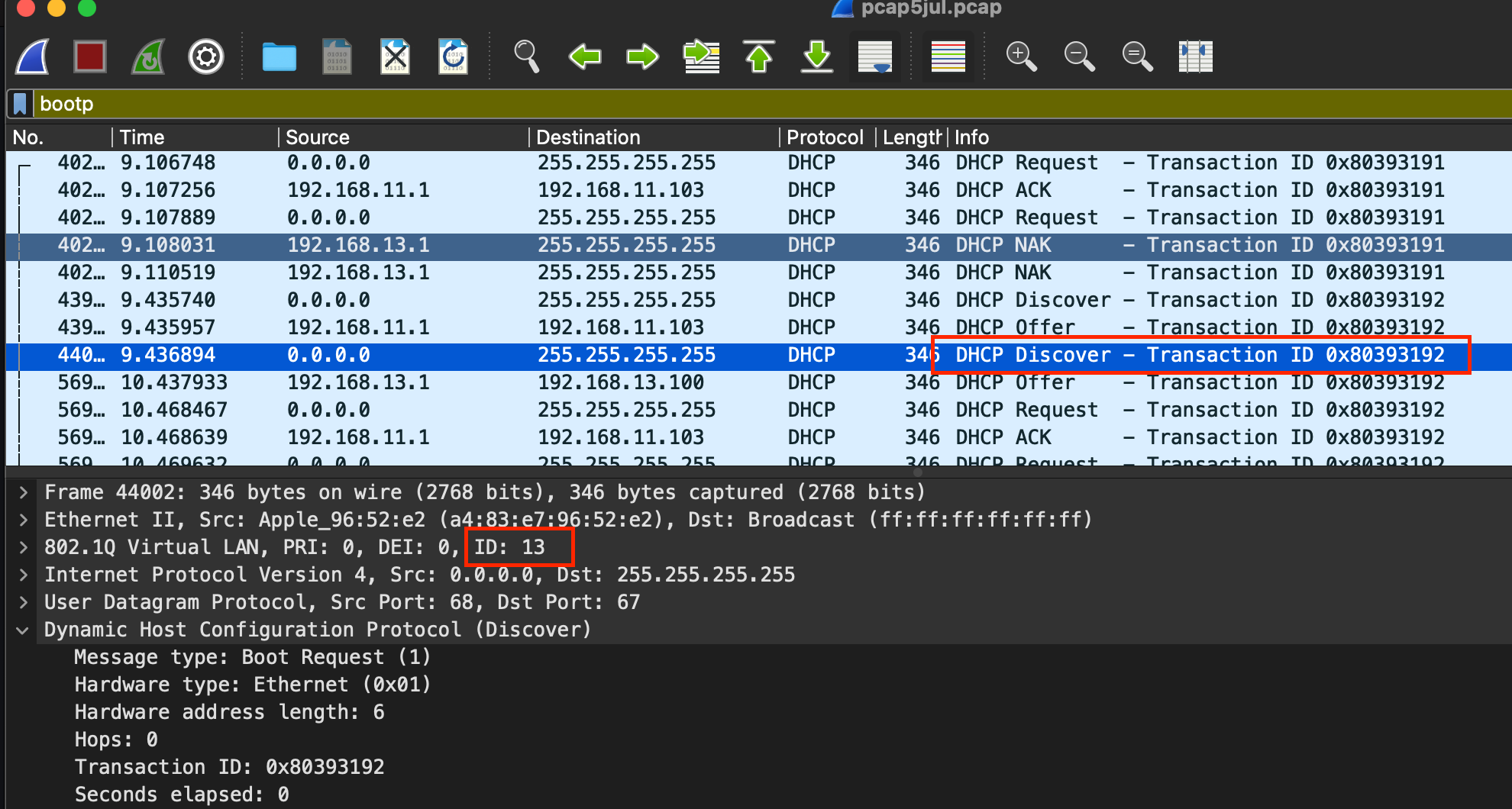
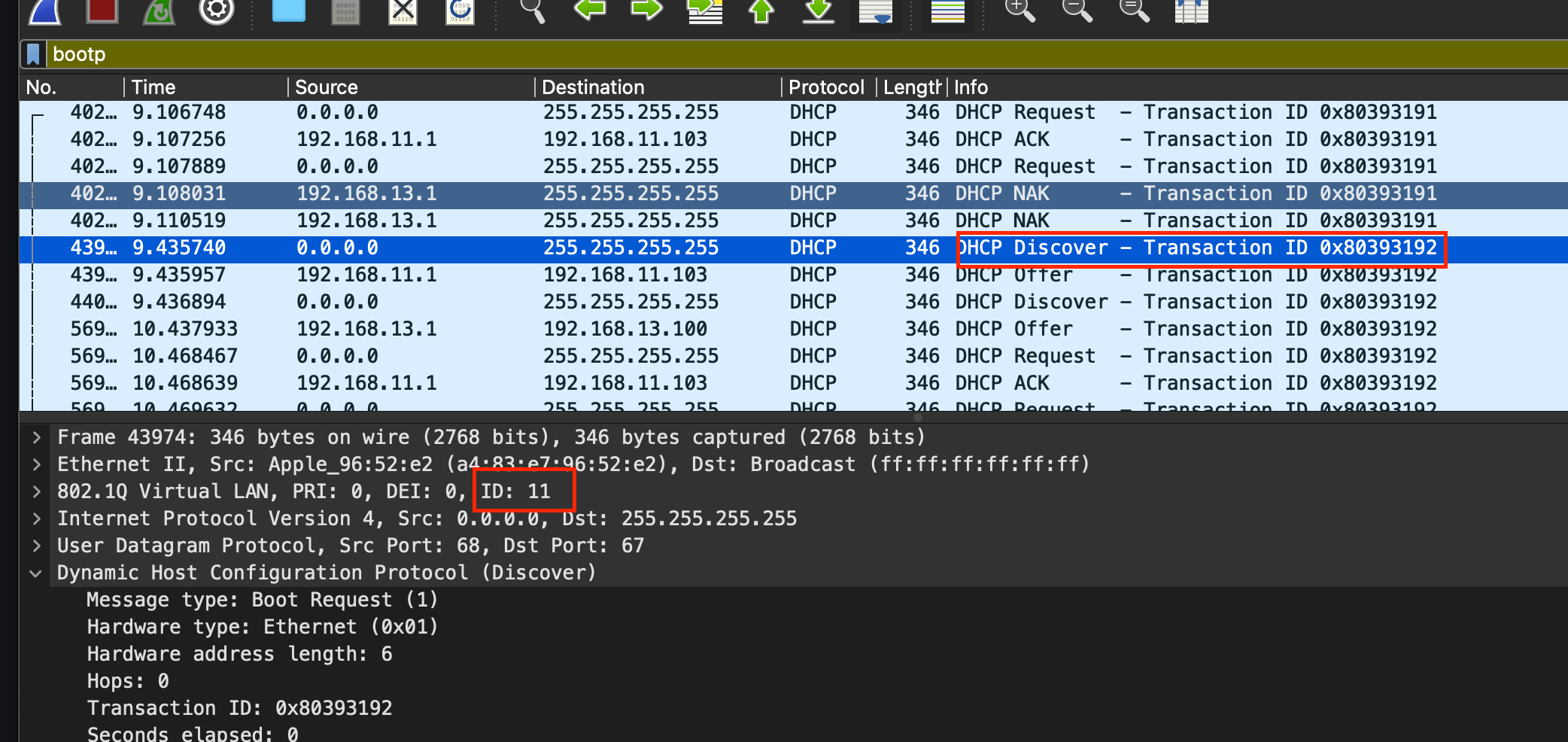
@jknott Thanks for the tips! I have made those adjustments and it's indeed much easier to follow. Here are the DHCP packets I captured pcap1.pcap
If it's best practice to use a native LAN for the main network instead of a VLAN then I can certainly give that a go. Kinda makes sense actually.
@viragomann This is the configuration I was advised as the default network on Unifi cannot be VLAN tagged.
-
@nazuro said in Broadcast packets duplicated across VLAN:
This is the configuration I was advised as the default network on Unifi cannot be VLAN tagged.
Really? The management IP cannot be on a VLAN?
So I'm wondering why so many people are using these crappy Unify parts.Anyway, I'd remove this port from VLAN 11 for testing to rule out the AP is the backdoor into VLAN 13.
-
I have a Unifi AC-LITE AP with the main network on native and guest WiFi on VLAN3. I configured pfsense, the AP and appropriate switch ports to pass VLAN3 as well as native. AP management is on the native LAN.
Sometimes, when you have weird problems, the best thing to do is start from scratch and do things one step at a time.
You seem to be having trouble between VLAN11 & VLAN13. VLAN11 is your main system, but VLAN 13 is your VPN. Why is that on a VLAN? That would normally be native traffic on the WAN port. Also, what on 13 is responding to DHCP requests? VPNs normally use TUN, which means they are routed. But DHCP uses broadcasts, which should not be routed.
-
One other Wireshark tip. Some columns appear to run out of space, losing the rightmost info. To fix that, right click on the column title and select Resize Column to Width. This will cause the column to include all the info. This is really handy with IPv6, where the addresses can be really long.
-
@jknott Yes really not sure why the issue is only between VLAN 11 & 13. VPN is not natively on the WAN port as I do not want all my traffic going through the VPN. The DHCP server running on the VPN virtual interface is responding to the DHCP requests.
I've pretty much based my setup around this guide which I found to be quite comprehensive: https://nguvu.org/pfsense/pfsense-baseline-setup/
I'm thinking about adjusting my configuration such that I am using the native LAN for management, however realised that Unifi for some reason only allows me to have four (total) networks. I'd in effect want to have MAIN,IOT,VPN,GUEST,native_management which would be five.
Alternatively I could use the native LAN for my "Main" traffic but I can't quite get my head around how this will work in pfSense, given that I have several firewall rules configured between VLANs at the moment and it's quite easy to do as each VLAN is on it's own virtual interface. Not sure how I would enforce rules on the "Main" traffic as I'd have to apply these on the LAN interface which could potentially get in the way of VLAN traffic coming in on LAN. Admittedly I am a bit out of my depth here and potentially talking complete nonsense so am happy to be corrected.
Alternatively I do have three spare NIC ports on pfSense so in theory could have a physical interface for each VLAN.
Thanks and appreciate your help
-
@nazuro said in Broadcast packets duplicated across VLAN:
for some reason only allows me to have four (total) networks. I'd in effect want to have MAIN,IOT,VPN,GUEST,native_management which would be five.
If you want more than 4, disable link monitoring.. Then you can have up to 8 per radio.. And you can not use wireless uplink.
Another option for more than 4 networks is dynamic assigned vlans.
-
@nazuro said in Broadcast packets duplicated across VLAN:
VPN is not natively on the WAN port as I do not want all my traffic going through the VPN.
That depends on how you configure the VPN, not by using VLANs. The setting in OpenVPN server config is Redirect IPv4 Gateway, which can force all traffic through the VPN. This might be used for those using the Wifi in a coffee shop, etc..
I'm thinking more you should start over from scratch.
-
@johnpoz Thanks for that, news to me! I made a change and gave myself four VLANs on Unifi and one native LAN. I could then update the switch so all four VLANs were tagged on port 11. However, same issue persists and I also noticed the issue persists on wired connection to the switch (ruling out Unifi issue).
@JKnott
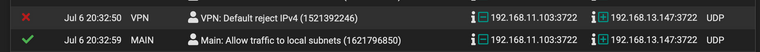
I am dreading the thought of starting again if I'm honest. Am seemingly so close with the perfect setup for me it's just these damn broadcast packets that seem to get duplicated. Perhaps I have a dodgy switch or NIC on my pfSense box. I just can't think what else could cause these duplicated broadcast packets.Looking in the traffic logs, I also see the odd occasion where the interface is "VLAN" when it should be "MAIN" (as 192.168.11.103 is a device on the MAIN network). So confusing! And throwing off the hypothesis that it's just broadcast traffic being duplicated

-
@nazuro said in Broadcast packets duplicated across VLAN:
I am dreading the thought of starting again if I'm honest. Am seemingly so close with the perfect setup for me it's just these damn broadcast packets that seem to get duplicated. Perhaps I have a dodgy switch or NIC on my pfSense box. I just can't think what else could cause these duplicated broadcast packets.
The thing is I don't think you really have it configured correctly. I can see only 2 things that should be VLANs, guest WiFi and IoT. I still have absolutely no idea why your VPN is on a VLAN, when it shouldn't even be on the LAN side at all. A VPN is used to connect computers or networks securely over the Internet and normally terminate on the firewall/router.
-
So yeah that doesn't make any sense.. What is this 13.147 address?
And this 11.103 is no way its multihomed? And or could tag traffic? Is it a wired device or wireless?
Pfsense shouldn't ever see that traffic unless sent to its mac (its the gateway).. Unless it was broadcast..
can you get a sniff of this traffic? On pfsense interface and post the pcap..
Those firewall entries are 9 seconds apart, so its not like a duplication of traffic.. It would have to be sent separately. I can't see how something duplicating traffic, or any sort of loop, etc. showing the hits 9 seconds apart..
So to me - these were actually sent by the .103 device to 2 different gateway. Too the vpn pfsense IP, and the main pfsense IP.. How these device could talk to these different pfsense IPs when they are in different vlans makes no sense - if the vlans are correctly isolated and being tagged correctly..
edit: To his vpn vlan, I take it that is just what he is calling this vlan, because he wants to route this out his vpn connection.. That is my take on that name.
edit2: If its a wireless device this 103 device - could it be switching wifi ssids? That could explain sending traffic to vpn vlan gateway on vlan X, and then few seconds latter sending same traffic to vlan Y gateway.
-
Further on this. Several years ago, I had one job that had 3 VLANs. It was a senior citizens residence, occupying 3 towers. In addition to the main native LAN for the office, there were VLANs for VoIP, network management and Internet to the resident's rooms. That is the only time I've had that many VLANs and I don't understand why you need 4.
-
@jknott said in Broadcast packets duplicated across VLAN:
why you need 4.
You don't understand why someone might want to isolate wifi to more than 4 vlans? Come on!
I have 4, and really could use more.. My main trusted vlan, my psk vlan, my roku vlan, and then a guest vlan.
I could see busting out a few more.. I have a few different devices sharing my psk vlan.. I could see breaking those out to different vlans for different devices, etc. For example when I setup some camera's I would want those on their own camera vlan. And I should really break out all my lightbulbs to their own vs being on the same vlan as my other iot devices.. Just lazy and let them share the same vlan..
edit: Thinking about this for a few minutes - my "guess" is this 103 device is wireless and its changing the ssid its connected to. Say for example when it cant get to that 13.147 address via the vpn ssid, it jumps to another ssid to try and get there. That would explain the 9 second span between firewall hits.
-
I can understand why there might be a need for more VLANs. What I don't understand is why he needs 4, based on what he's mentioned. For example, what's with the VPN on a VLAN? Where does the VLAN terminate? If other than on pfsense, that complicates routing. As discussed, the main LAN also shouldn't be on a VLAN. That leaves 2. Sure, I could put my TV on it's own VLAN, but the guest WiFi is good enough for that. Even then, the only reason the TV isn't on my main LAN is it chokes on the 63 character password I use on it. I suppose I could put my IPTV boxes on a separate VLAN, but haven't bothered.
-
@jknott said in Broadcast packets duplicated across VLAN:
what's with the VPN on a VLAN?
My take and have seen many users do this.. They create a vlan, that all devices on this vlan are routed out a vpn connection. So for example if he wants to use the vpn on his phone for "something" he just changes the ssid he is connected to. Maybe netflix doesn't work via the vpn, so when he wants to watch netflix on is phone he changes to different ssid that is not routed out the vpn.
-
I suppose I could give my dog & cat their own VLANs.

-
@jknott clearly - they should not be on the same ;) that is for sure - they would just fight ;)