Remote Access VPN connects but unable to access LAN IPs
-
I configured Remote Access OpenVPN on one network and all works well.
I then set up a new site with same model firewall but while the VPN establishes connection fine, I am unable to access any of the remote hosts. I imagine it's something to do with the IP addressing?The working site has 192.168.1.0/24 LAN which I entered into the "local network" field and 192.168.2.0/24 into the "tunnel network". All works well here.
On the one that doesn't work, 192.168.123.0/24 in "tunnel network" and 10.1.0.0/16 in "local network". VPN established, client gets 192.168.123.2 IP but is not able to ping 10.1.1.8 which is pingable from the Diag tab on the firewall.
The VPN was created by the Wizard which added the firewall rules as well.
Tracert hits 123.1 and then times out the rest.What am I missing?
-
maybe try this, it worked for me last night:
Hybrid outbound Nat rules to give vpnusers access to LAN
interface: LAN
Source: any
source port: *
Destination: 10.1.0.0/16
Dest port: *
NAT address: LAN adress
NAT port: * -
@peterlecki said in Remote Access VPN connects but unable to access LAN IPs:
but is not able to ping 10.1.1.8 which is pingable from the Diag tab on the firewall.
Does the host respond as well if you change the soure to OpenVPN?
@tjohansen said in Remote Access VPN connects but unable to access LAN IPs:
maybe try this, it worked for me last night:
Hybrid outbound Nat rules to give vpnusers access to LAN
interface: LAN
Source: any
source port: *
Destination: 10.1.0.0/16
Dest port: *
NAT address: LAN adress
NAT port: *Your suggestion could be dangerous! It might be okay in certain circumstances like for VPN access with several trusted clients. But to restrict it to VPN clients, you have to limit the source to the VPN tunnel network.
However, when using source = any this rule is applied to any internal traffic as well as incoming from the internet, which could result in uncontrolled and undesired access. -
Is it also dangerous when its only in the "outbound" NAT rules?
just tried to limit it to the vpn tunnel network and that works too :-)
thx -
@tjohansen
Such rules let the LAN devices think, the access would be coming from inside their own subnet and hence trust it and let the traffic pass.If you set the source to any this rule applies to any source address naturally. However, you can additionally control the traffic on the incoming interface and restrict it there. But if you have sloppy inbound rules you will open more as you want with that.
And with such rule there is no possibility to determine the real source IP on the destination device. Hence this is a no-go if you have servers inside which are accessible from the internet. Instead you should configure the servers firewalls to pass the desired access.
The bottom line is, if you know what it does, you can use it. But I wouldn't suggest it to a newbie.
-
@viragomann said in Remote Access VPN connects but unable to access LAN IPs:
Does the host respond as well if you change the soure to OpenVPN?
I didn't try it before but did now and it does NOT respond, 100% packet loss.
-
@peterlecki said in Remote Access VPN connects but unable to access LAN IPs:
I didn't try it before but did now and it does NOT respond, 100% packet loss.
So the destination device will block access, when it's coming from outside.
You can either set its firewall to allow access from the VPN network or do masquerading on pfSense concerning the discussion above.
-
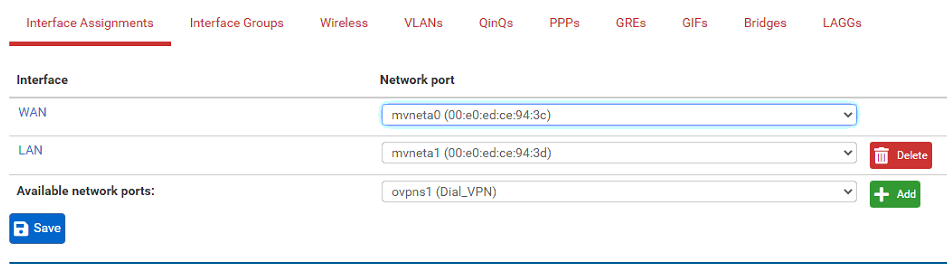
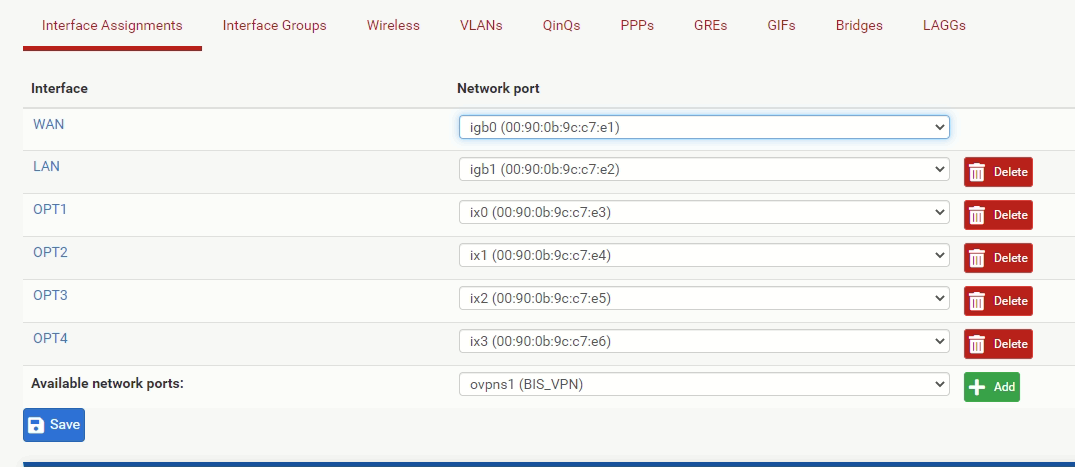
My mistake saying they were the same model devices. That one that works is SG-2100 while the one that doesn't is SG-5100. I don't know if it makes a difference in this case but their interface assignments looks different.
SG-2100
SG-5100
-
@viragomann said in Remote Access VPN connects but unable to access LAN IPs:
@peterlecki said in Remote Access VPN connects but unable to access LAN IPs:
I didn't try it before but did now and it does NOT respond, 100% packet loss.
So the destination device will block access, when it's coming from outside.
You can either set its firewall to allow access from the VPN network or do masquerading on pfSense concerning the discussion above.
Software firewalls on the internal hosts are NOT on.
-
@peterlecki
Is pfSense the default gateway on the destination device? -
@viragomann said in Remote Access VPN connects but unable to access LAN IPs:
@peterlecki
Is pfSense the default gateway on the destination device?It was not. I added this new firewall in addition to the primary that is still in service. I wanted to make sure it works before I swapped them. I just changed the default gateway on that device now and it started responding to pings from firewall Diag but still not from VPN clients. That is a damn good find, man. I wouldn't have thought of that. Big step forward.
-
@peterlecki said in Remote Access VPN connects but unable to access LAN IPs:
@peterlecki
Is pfSense the default gateway on the destination device?It was not.
That would be worth to mention.
When request traffic is from outside its subnet the destination device send respond packets to its default gateway.To get the packets back to pfSense you can remove pfSense from the LAN and put it into a transit network. Then add routes to pfSense for the LANs pointing to the gateway and add a route to the gateway for the VPN tunnel network pointing to pfSense.