Suricata-6.0.0_11 auto-enable by SID Mgmt conf files don't work properly
-
@bmeeks
Auto-enable by SID Mgmt conf files "Feodo Tracker Botnet C2 IP Rules" and "ABUSE.ch SSL Blacklist Rules" don't work properly, auto-enabled checks are missing.Added "feodotracker" and "sslblacklist_tls_cert" to enablesid.conf, Interface SID Management List Assignments LAN Rebuild checked, save.
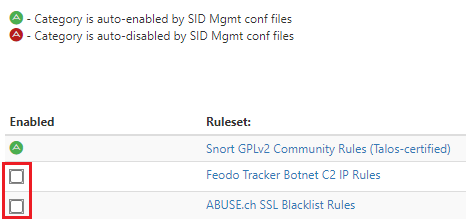
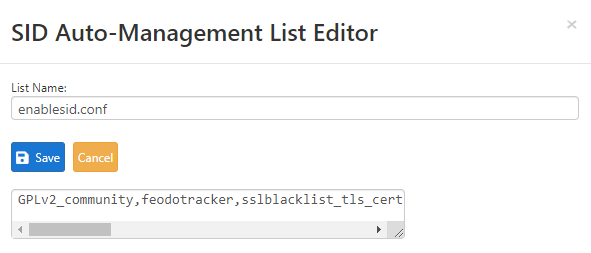
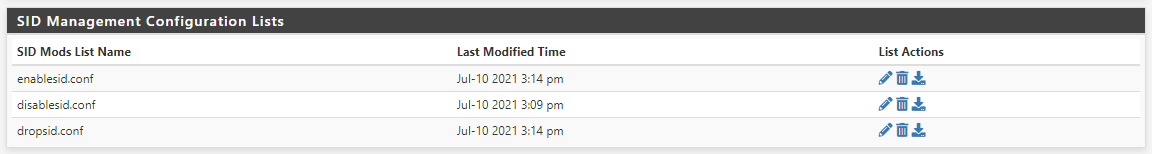
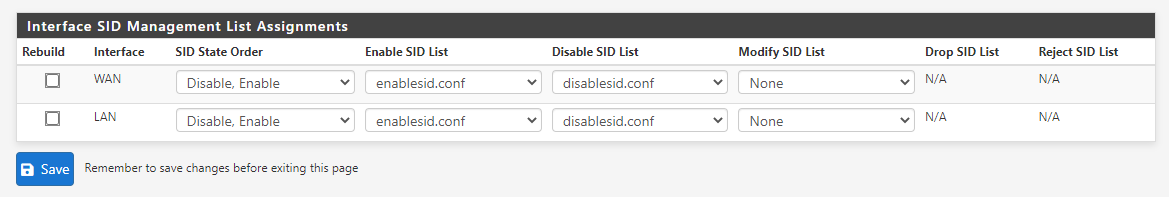
-
I've verified this issue. I will get it fixed in the next package update. In the meantime, you can simply go to the CATEGORIES tab and enable those categories if you want to use them.
-
Same thing with others categorys, for exemple : dns-event or something elses.
enablesid.conf by sid auto-management doesn't work properly but
disablesid.conf and dropsid.conf working good.Thank you bmeeks for the next package update.
-
@jm1384 said in Suricata-6.0.0_11 auto-enable by SID Mgmt conf files don't work properly:
Same thing with others categorys, for exemple : dns-event or something elses.
enablesid.conf by sid auto-management doesn't work properly but
disablesid.conf and dropsid.conf working good.Thank you bmeeks for the next package update.
Yes, I found that issue as well. It was due to only looking for rules filenames with the prefixes "emerging-" or "snort-" instead of all rules rules. It will be fixed in an upcoming release. Snort suffered from the same issue, and I will fix that as well.
The new Suricata package is ready, but I am waiting a bit while working with the upstream Suricata binary team to see if we can identify and fix an issue in the 6.0.3 binary. I would love to update the pfSense package to use 6.0.3, but at the moment netmap under any 6.x version will work for a short period of time and then freeze - halting all traffic on the interface.
-
@bmeeks said in Suricata-6.0.0_11 auto-enable by SID Mgmt conf files don't work properly:
e new Suricata package is ready, but I am waiting a bit while working with the upstream Suricata binary team to see if we can identify and fix an issue in the 6.0.3
If you are referring to this defect https://redmine.openinfosecfoundation.org/issues/4478 raised by you...I would like to thank you for taking care of Suricata, by documenting this issues.
I don't know what happened with Suricata team during 6.0 version.
I'm speaking about this defect https://redmine.openinfosecfoundation.org/issues/4443 alsoI'm starting to think that FreeBSD is a 3rd class citizen compared to Linux, by the means of implementation, integration and testing
Also please note that the defect was moved to be fixed in 6.0.4 https://redmine.openinfosecfoundation.org/versions/169
Thank you again
-
@NRgia:
Yes, I was primarily speaking of the defect I raised about Netmap hanging. Another user chimed in with a similar hanging issue, but he is not using Netmap. So perhaps something else is wrong within Suricata's threading logic. There were lots of changes there in the move from 5.x to 6.x.I am working via email with the developer assigned to the Redmine issue I submitted. He can reproduce it, but only randomly. Same on my end now. It takes longer for the "hang" to happen. I can reliably reproduce it if I let my test machines run overnight. So this is a very puzzling defect.
One good outcome from this problem is that I've learned an awful lot about the internals of netmap. And I believe I have found some subtle bugs in the current Suricata implementation of netmap. I am proposing some fixes for these as I work with the Suricata developer. Hopefully this all winds up producing a better performing Suricata package on pfSense in the future.
-
The fix for this issue has been posted in the latest Suricata package update under review by the pfSense developer team. I've asked them to update the package in all pfSense CE and pfSense+ branches. It may take a couple of days for the update to post.
Here is the Pull Request containing the fixes: https://github.com/pfsense/FreeBSD-ports/pull/1085.
-
@bmeeks
thanx, it's working fine now...