Routing pfsense openvpn users to another router with vpn access to intranet.
-
I need help in setting up correct routing.
I have a "old cisco router" I use for vpn access. This is to be replaced with my new pfsense router.
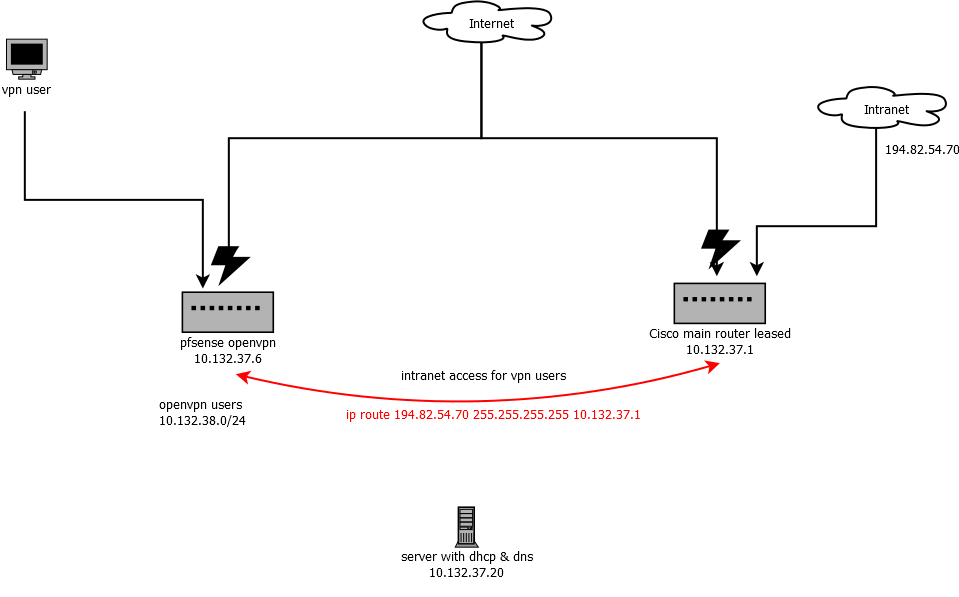
And I have almost got it all working except routing intranet requests from pfsense vpnusers to my "main cisco router" which I have no control over.Pictures speak better than words so have made a diagram (ip's have been obfuscated).
The text string in red was what worked in the "old cisco vpn router".
you want more information on how openvpn is configured?
-
bonus info:
openvpn
Devicemode: tun layer3
interface: WAN
IPv4 Tunnel Network: 10.132.38.0/24
IPv4 Local network(s): 10.132.37.0/24
DNS list: 10.132.37.20I have Hybrid outbound Nat rules to give vpnusers access to LAN devices on 10.132.37.0/24
interface: LAN
Source: any
source port: *
Destination: 10.132.37.0/24
Dest port: *
NAT address: LAN adress
NAT port: * -
changed to:
interface: LAN
Source: 10.132.38.0/24
source port: *
Destination: 10.132.37.0/24
Dest port: *
NAT address: LAN adress
NAT port: * -
how do I add a fixed route for a specific ip to another gateway?
like 194.82.54.70 255.255.255.255 to gateway 10.132.37.1 which is a gateway on another router in the lan?
-
@tjohansen
Not clear, why you are routing intranet traffic to the public IP.
Does the Cisco work that way, when accessing from the LAN?Anyway, since you direct the traffic to the public IP, the destination in the outbound NAT rule has even to be this public IP, not the LAN network.
-
@viragomann Its because we have access to some corporate "intranet" through "cisco main router" but need to give my vpnusers access to this as well.
I have no access to "the cisco main router".All I know is that our old secondary cisco router could do this by this:
ip route 194.82.54.70 255.255.255.255 10.132.37.1 -
@tjohansen said in Routing pfsense openvpn users to another router with vpn access to intranet.:
All I know is that our old secondary cisco router could do this by this:
ip route 194.82.54.70 255.255.255.255 10.132.37.1That's a simple static route.
To add it to pfSense, add 10.132.37.1 as gateway in System > Routing > Gateways, then go to the static routes tab and add a route for 194.82.54.70/32 and select the gateway you've added before.
You have also to add 194.82.54.70/32 to the "Local Networks" in the OpenVPN server settings to push the route to the vpn clients.
-
@viragomann Thx, done this but somehow part of dont work.
I have added it as gateway.
I have added a static route.
I can ping 194.82.54.70 through the diagnostic -> ping
So conclusion must be that static route works.I have added 194.82.54.70/32 in openvpn server localnetworks so it says:
"10.132.37.0/24,194.82.54.70/32"
but cant ping 194.82.54.70 from my vpn user.
10.132.37.0/24 is required to be able to ping my server etc. -
@tjohansen
Does the Cisco accept accessing its public IP from inside the LAN? I already asked this, but you didn't respond.Did you update the outbound NAT rule as I suggested?
-
The cisco router has a fixed "vpn" connection the corporate "intranet" (194.82.54.70), thats why I can only access it within the LAN through the gw 10.132.37.1.
I missed that about the outbound rule.
I have added it as an extra outbound rule with dest.194.82.54.70/32 .
I can now ping it from my vpn user.Awesome.
Thank you for your great help, I really appreciate it.