VPN Breaks Vlan to Lan
-
Have 1 Vlan (30) that is bound to the Lan Interface. Both can talk to each other and go out to the internet. Once I enable VPN back to the Office they can no longer talk to each other. They both can talk to the Main Office network and Internet. Here are the Firewall rules for the Lan and the Vlan (EmployeeWireless)
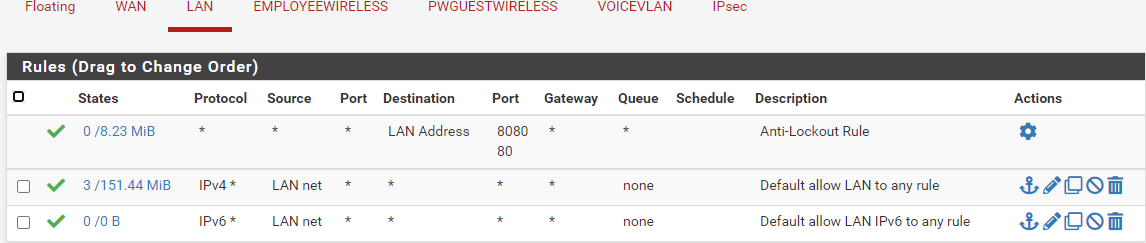
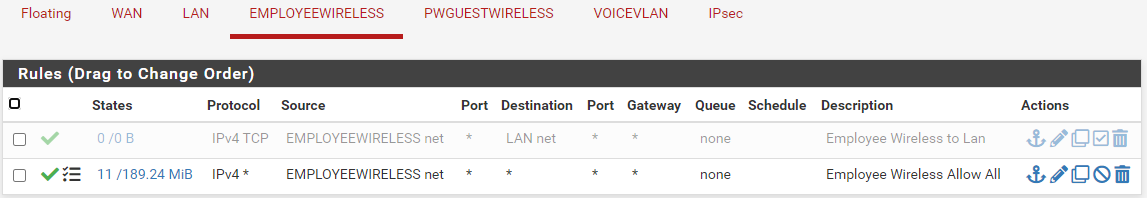
Seems to be a routing issue. The system logs show a ping being allowed through the rule but does not work.
-
@kevcar2021 Why would it be a routing issue, both VLANS are directly attached.
What are you using as an AP ?
-
@kevcar2021 said in VPN Breaks Vlan to Lan:
Once I enable VPN back to the Office they can no longer talk to each other.
Where are enabling vpn? On the client directly or via pfsense and policy routing out some gateway?
-
Under VPN->IPSec. I disable it.
-
That shouldn't break anything - what are the remote networks involved and your local networks? Did you setup routed ipsec and doing policy routing?
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/routed-vti.html
Your going to have to give some pieces of the puzzle if you want help solving it ;)
-
Here is the Phase 2 of one of the networks. Currently I have 3. They are all configured the same.
Just tell me what you wan to see I will show it. Thanks for the quick responses.
I believe that is not Policy Routing correct?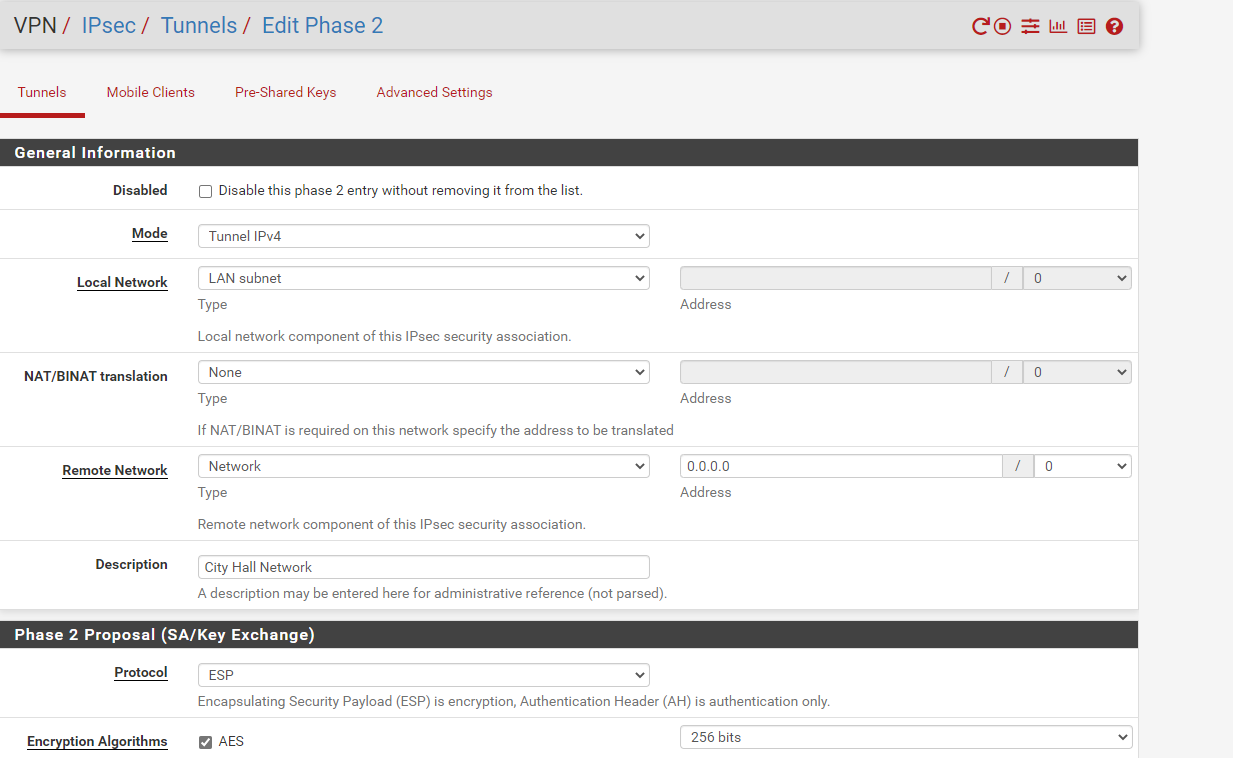
-
I am using Watchguard and Sonicwall Firewalls and have never had an issue like this. I am sure its something I am just missing. I want all Network activity to go through the VPN to the main office and then out their ISP. I am trying to replace an old Sonicwall and when I swap this one out with the Sonicwall everything works except for Vlan->Lan and vise versa. I have not tried the others as of yet.
-
Here is the log of a ping from vlan 30 to the lan
Although it shows it went through the ping returns as Timed Out
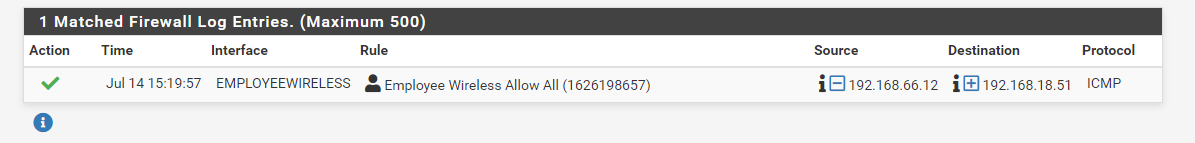
-
@kevcar2021 said in VPN Breaks Vlan to Lan:
ping from vlan 30 to the lan
And what interface did it go out? That just shows it was allow - you don't really know what other interface it left on - did it go out the vpn.. Which would explain why the dest never got it?
-
What is the best way to determine that?
Here is something new. I am also unable to ping the VLAN interface when the vpn is connected. I started a continuous ping from the vlan to the vlan interface and to the device on the Lan. Both were returning time outs. I disabled the VPN and both pings started working. Once I re-enabled the VPN the pings started timing out again. Why would the ping return a timeout to its own interface?