pfSense no reporting IPs behind Switch
-
Ahh ...
Could be one dumb switch per pfsense ethernet interface.
These are prob. untagged , so no vlans defined , but still multiple "def-gw's"/Bingo
-
While the function of a switch, which diverse in many aspects from a Hub, and by the way, hubs are hardly used any longer, Switches frames between the same switch does not leave the switch since the frames are all forward base on the MAC in MAC table. This would be inter LAN communication. By the way, there is not way to configured gateways in unmanaged switches.
Contrary to clients, please does not mistake with network nodes, sending Internet request, leaving the network are not being logged. For install a client connecting to https://yahoo.com, it is not log into the FW logs as pass packet, or a client connecting to a site that is blocked, it is not logging a block packet. All that is being logged are the gateways.
For instance packets send by 172.16.7.1 gateway passing traffic on port 53 to the FW. But the actual client, let's say 172.16.7.100 is not being logged even the switch it directly connected to port OPT1. Almost like it is filtering the local clients.
Figured a pic worth 1K words:
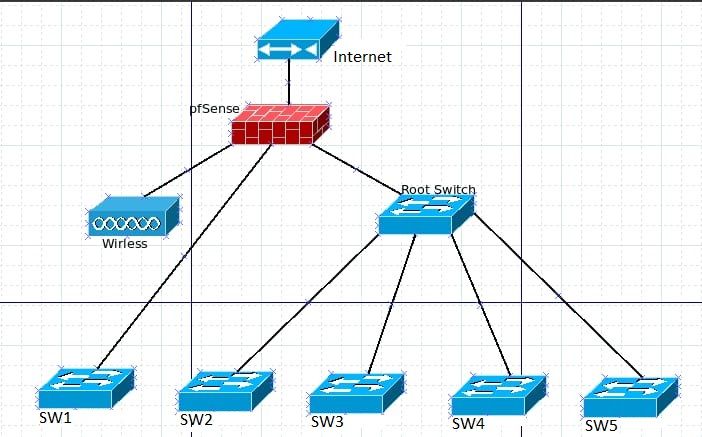
Hopping that makes sense.
-
VLANs are not that complex, actually they are very simple even a subvlaning is being used. Let's use the KISS method in the scenario. No need to go on tangents or adding more complexity that is actually needed.
Let's eliminate, hubs since they are extremely scarce at this point in the 21st Century. No VLANs since they are unmanaged SW. Of course the will be the default VLAN as define by the OS in the SW, otherwise noting will communicate, right? Just common sense.
Instead of guessing here is a kind of a network diag:
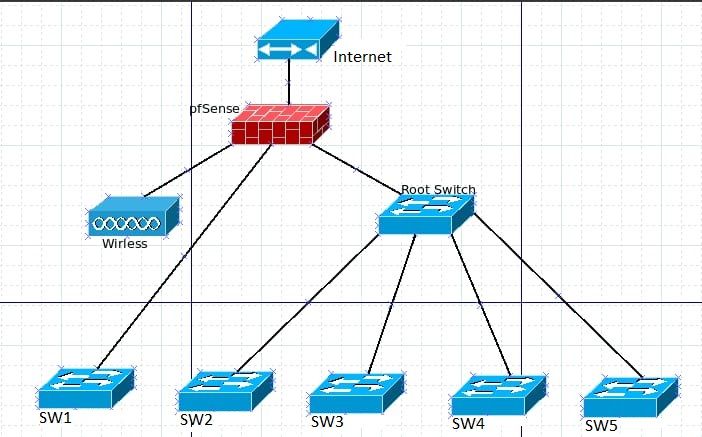
Hopes this help a bit.
-
@g405tsh311 If something is masquerading the inside IP addresses into one address, then you have a router doing NAT or something along those lines. Switches, managed or not, do not alter IP addresses (Unless it is a layer 3 switch which is really a router in that role).
-
Hi there, thank you for your input.
Just to clarified a bit more beside the diagram. The device is just a simple L2 device. I looked a the datasheet and specs and it is very clear it is not a multilayer dev.
Since the device is unmanaged, the is not NAT, specially at L2 where again, are frames being used. But now I am wondering what is in the SW that might be affecting packets passing to the FW????
Let me get back with you in a bit!!!
-
The way I am reading the diagram, is that the PFSense device has 4 NICs. One is WAN, one is the wireless, and there are two other NICs connecting to two 'dumb' switches, one of which connects to more switches. Therefore, there are 4 networks here, assuming these are dumb switches and there are no vlans. So traffic passing between any device connected to the 'root switch' that has all the switches below it, and its port on the PFSense, can all 'talk' to each other provided those devices don't have a firewall on them that blocks ports or IP ranges. By default, they would NOT be able to communicate with the wireless devices or the other dumb switch connected to another port on PFSense, by default. This is also assuming that all the switches are functioning properly, and all the cabling is good. They would NOT, for example be able to see wireless devices, or the items on the other switch that isn't connected to 'root switch' with all the switches below it. It would not see that PFSense port either, but their own default gateway port. If using PFSense for DHCP, for example, it would need to be configured for each of those LAN/OPT ports. If only one of those ports is configured on PFSense, only that port will have visibility into the network. So provided this drawing is correct, make sure that you have configured/enabled all the LAN ports, and any DHCP per PORT.
I hope I haven't misread the diagram, but that is what it looks like to me. -
@tzvia
I am so confused on what you are talking about, that it is not even funny.I think you are confusing your terminologies and definitions giving the devices totally the wrong function within a network. Unamanged and dumb switch are two, totally, different devices. "Dumb" usually refers to hubs contrary to switches. Unamanged switches are not "dumb" they are unamanaged, meaning the configuration cannot be modify without altering the current OS. Switches have some logic programmed within to make decision base on the frames received contrary to hub that just duplicate the packets on all ports.
Your definition on the diagram is totally incorrect. Pure L2 switches, such the ones I am using, does not have ACL or rules for blocking or filtering. You can have multiple switches interconnected and as long as the switches are on the same subnet, they will be able to communicate. I would recommend to learn a bit more about switching technologies.
-
@g405tsh311 said in pfSense no reporting IPs behind Switch:
"Dumb" usually refers to hubs contrary to switches.
I've never heard that before. In my book a dumb or unmanaged switch is one that you can't configure to do anything. It just passes traffic. A managed switch can be configured for a variety of things, such as VLANs. locking port speed/duplex etc..
-
@g405tsh311 I am only looking at the diagram. Still see 4 NICS on the PFSENSE. Each of these PFSENSE ports are a separate network with their own network addressing as they connect to different ports on the PFSENSE router. No one is talking about hubs, which are ancient technology that operate in the physical layer of the OSI model, while switches operate in the Data Link Layer. The single collision domain, being a broadcast device; switch is unicast, multicast as well as broadcast, half vs full dupe and I don't know why you mention them as they are not present in your diagram. I get switch vs hub, I learned that 17 years ago in a Cisco class. Yea VLANS are simple to setup I have several and don't use unmanaged dumb switchess. Now back to the diagram. The 'rules and filtering', again if your diagram is correct and there are 3 LAN side ports on your router that are in use by various WAPs/switches, are being done by PFSENSE itself. I didn't think I had to spell that out. So provided these interfaces other than LAN on the PFSENSE are configured with network ports associated and you see them on the interfaces tab and devices connected to the wireless and to these switches which are attached to those additional ports in PFSENSE are getting valid IPs or are set static and can get to the internet, any blocking going on, based on firewall rules on these interfaces, should be logged in the firewall log for all these interfaces. I am assuming that you have created firewall rules, not just a blanket allow all type of rule on these interfaces.
-
I don't know who wrote what you are reading. In network devices "dumb" meaning, have no logic to analyze the content passing through it.
I think the right terminology you are looking for is "transparent" or "passthrough" meaning they pass all traffic using basic configuration. Usually hubs are "dumb" devices that all they do, is repeat what they received. -
All I can say about your post, is that you are way on the left field.
For a simple network, unmanaged devices are fine to use. If you want to use managed devices for simple operation in a residential environment an expend the extra money, well be my guess. You are looking way beyond the simplicity of the question.
Duplicity, speed, unicast or broadcast are totally irrelevant on this question since, all that I was wondering is why
pfSense was not registering the packets leaving the ER.Once again, dumb vs smart, managed vs unmanaged. Switches, regardless they can be controlled by a CLI or GUI, they are smart devices since they have to monitor, build, add, remove or updates MAC table which requires some logic to be built into the device.
You are correct, hubs are ancient technology and yet many people still think hubs are switches and switches can act like hubs, this is a misconception.
Regardless how your network is built, if there a monitoring systems and all packets are passing through that point, the monitoring engine should be able to capture the information that is required by the configuration.
While you are using VLANs, my network is using physical LANs by pfSense, just because that is the way I wanted configured. Each interface have their own set of FW rules that allows specific traffic between interfaces. The only interface I can see logging-on a single IP address for all the dev. is the Wireless, since the wireless is actually a router/switching dev that hasn't been replaced but, once is RPL with an AP, then I should be able to see all the dev on that interface.
BYTW, the network is fully interconnected, every subnet is able to reach each other. Otherwise it will defeat to have a network.
-
@g405tsh311 said in pfSense no reporting IPs behind Switch:
f you want to use managed devices for simple operation in a residential environment an expend the extra money, well be my guess
Its not that much extra.. You can pick up a "smart/managed" switch for like $40.. And now have the ability to do vlans vs having to do physical isolation and multiple switches, etc.
Dumb in terms of switch means it is not managed, doesn't support vlans - and more than likely has no gui or cli to glean any info from it other than the lights.. While yes as a switch it would learn and build mac address table, etc. its "DUMB" in the sense you have no way to view any of this info, nor can you configure any vlans..
He sure doesn't have to drop any real money to get a "smart" switch that will allow him to view info like error on interfaces, the mac address table, set interface speeds.. Maybe he wants something to run at 100 or 10 vs gig, etc. None of that stuff is available in a "dumb" switch..
Now these entry level "smart" switches are not going to have all the bells and whistles that a fully managed switch would be able to do.. But its going to well worth the few extra bucks to have a switch he can glean info from, run vlans on, etc..
-
I will agree to disagree on the "dumb" term. That is totally & improperly used. Just because it is unmanaged does not mean it has not features. As a matter of fact, the NetGear GS308 SW cost about $90 bucks and it is unmanaged. The same SW can be upgraded via a third party software just adding a GUI making it fully managed. Yet all the features are there and are the same as the managed one.
I have hardly seeing any one configuring a port for a specific speed, sensing or duplexity other than auto/auto. Sure I can go to my closet and add my HPE 2530-48G PoE+ and start creating VLANs and subVLANs and aggregate ports and create failover and virtual channels and CARP to another dev. Just to use a high price level switch in a residential env.....Way to excessive. I do that at work!!
The extra bucks you are paying for a manage dev, it is just for CO. to enable the GUI, all other features are still there. I had that going on with a nameless company to add a GUI to a dev at work, the charged the dif for adding the web GUI since one of the VPs preferred the candy-eye contrary to CLI.
-
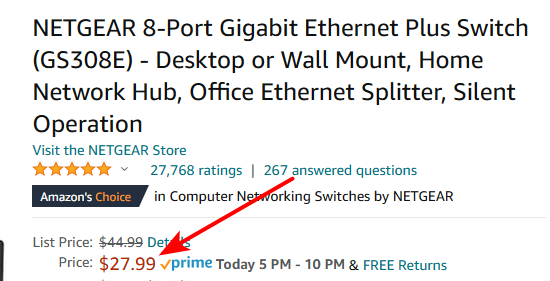
@g405tsh311 said in pfSense no reporting IPs behind Switch:
NetGear GS308 SW cost about $90 bucks
Not sure where your buying your switches?
This one is "smart" and can do vlans
This one is dumb
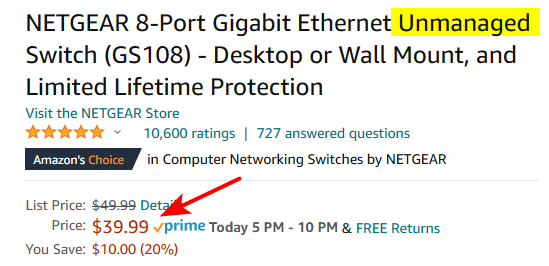
Why would someone not get the "plus" or smart version? As to downgrading speed - it was an example.
Be it the hardware the same or not - if you can load 3rd party on it to enable vlans and give yourself a gui/cli to get access to "smart" features - than that is great. Get a dumb one and add the gui/cli
But when someone calls it a "dumb" switch - means to me it has no gui or cli, and has no way to glean info from it or set anything at all, lack of vlans being the big thing. its DUMB!!
I run a 28 port sg300 as my main switch, and then have a 10 port sg300 in my AV cab.. I do multicast acls on mine, so no these entry level "smart" switches don't have such features.
Its not excessive - and it wasn't all that expensive, under 200 new! And uses low amount of power.. I have way too many devices to use anything else than a 24 port switch anyway.. Good luck finding a dumb version of those anyway.. And it would be pointless, because the devices are not in the same vlans. Sure not going to isolate them all physical with different switches.
Nobody is saying he has to drop $$ on a switch, and hey if you have a way for him to save a few bucks and get "dumb" model and put 3rd party on it and get vlan support, etc. etc.. Then you should really link to those details..