Why am I seeing Softbank in my DHCP list
-
Hello
I am new to using PFS and have been doing some looking around and came across an entry in the DHCP lease list from softbank (below) which is not a known device but was assigned an IP in my LAN DHCP range. I have seen this in the past when reviewing traffic logs and such but didnt pay it much mind until now. Does anyone know what this is and why since it is not a device known to me it was able to gain an IP on my internal network? Should I be blocking these? Thank you.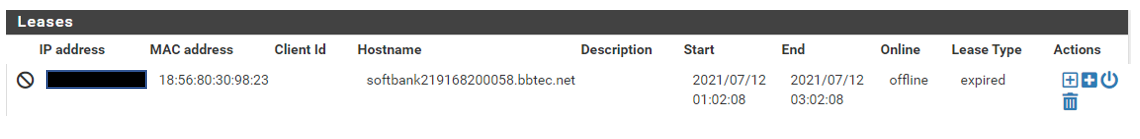
-
It is most likely an Intel NIC. Your call, but my paranoia says block all unknown devices.
-
18:56:80 is intel device..
As to what it actually is? You would only know.. As to how it got a lease from your dhcp - well because it was on your network.
Why are you hiding its IP - if its on your internal network, would have to assume its IP is rfc1918?
As to blocking stuff on your local network from getting dhcp from your dhcp server? Why would you be putting it on your network if you do not want to be on your network?
As to the hostname with bbtec.net - are you using that domain locally. While its a public domain. That could what it registered as its hostname, or it could be what was resolved from the IP.. Again have to assume that IP is rfc1918? Are you running public IP space on your internal network?
I show that name resolving to
;; QUESTION SECTION: ;softbank219168200058.bbtec.net. IN A ;; ANSWER SECTION: softbank219168200058.bbtec.net. 86400 IN A 219.168.200.58Are you running a 219.x.x.x address space on your internal network?
-
@andyrh Yes I did a search on the MAC and it is an Intel card but not any I can verify as belonging to any of my devices. Since I am still getting up to speed can you point me in the right direction on how to block access to the LAN from unknown dvices? Thank you.
-
;; QUESTION SECTION: ;58.200.168.219.in-addr.arpa. IN PTR ;; ANSWER SECTION: 58.200.168.219.in-addr.arpa. 86400 IN PTR softbank219168200058.bbtec.net.If you are running that IP space internally - then yeah that IP would and could resolve to that name.
-
I would block that system at the LAN port with a FW rule to prevent it from going out. Then if you have a managed switch you should be able to locate the MAC and the port should lead you to the device.
If you are in a business environment be careful and do not cause an outage that you cannot explain and justify.
Preventing unknown devices from getting DHCP addresses is a completely different problem.In my home environment the blocking generally brings a kid to me saying the internet is down... No real work on my part. :)
-
@johnpoz Aaaah I can now see, it appears a tad of dyslexia has caused an issue. 219 is a public ip range which is why its visible doing a DNS search, will have to make a change. So if it were the 192 or other private range this issue would not be an issue? Thanks for highlighting that for me, I have made the changes. Still curious what that softbank device was, maybe a scanner of sorts, no info can be found on the web using that name. Now I need to find a way to limit only devices belonging to this network to connect, on my old wifi router I was using WRT and I was able to static assign and lock everything else out, if there a package for pfSense that gives me that granular control? I know someone said using the managed switch which is an option but if can do it centrally from PFS it makes it easier. Thanks for your help and input.
-
huh? So your local network was 219.168.200 vs 192.168.200..
Because of a typo?
So again no device from outside was on your network.. But if some devices had that 219 address because you were handing out that space, then it would and could resolve to that name.. Doesn't mean that was its actual name..
You need to watch your network for that mac address to find out what the actual device was.
If you want to use static arp - you can do that with pfsense.. But then every signal device that is on your network will have to be setup with reservation..
https://docs.netgate.com/pfsense/en/latest/services/dhcp/ipv4.html

Or you could use the deny unknown
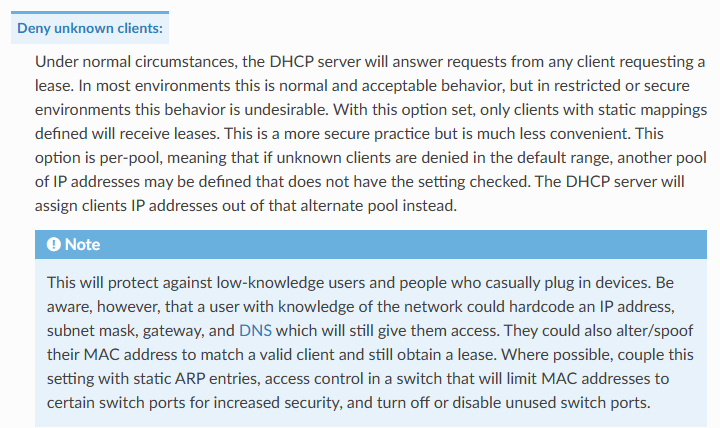
Do you have a scenario where billy could just bring in his device and plug it into some jack - and that is what your looking to stop. Or are you wanting to stop billy from bringing in his own phone and connecting it to your wifi, since he already knows the psk vs using only his work laptop or phone to get on the wifi?
A better option to keeping unwanted devices off your network would prob be to setup 802.1x for both your wired and wireless connections..
-
@andyrh Yes this is for my home and kid control is my main reason for ditching my wifi router and moving up to pfSense a managed PoE switch and an AP. Definitley interested in the details to establish rules to further nail down the environment. I know its an incremental process and appreciate the feedback from other users who know the ins and outs.
-
So at a loss to what could connect to your "home" network that you would want to prevent? Do you have strangers coming into your house and plugging stuff in?
Do you have your wifi psk on sign outside your house?
If what your wanting is to keep your kids phone off the wifi after 10pm say when they are suppose to be in bed, that is a different matter than static arp or deny unknown mac, etc..
-
@johnpoz You never know who is lurking outside or scanning. WiFi passphrases can be cracked, certs can be duplicated, macs spoofed and with everything else going on I think an ounce of prevention is a good thing, besides I hate it when they watch youtube and stupid/silly content, would rather block it all so they decide to go out and play.
-
@rjp1267 said in Why am I seeing Softbank in my DHCP list:
outside or scanning. WiFi passphrases can be cracked,
And you think spoofing a mac can not :) hehehe
Can tell you one thing breaking my psk going to be the harder part then some mac address spoof ;)
Blocking youtube is a bit different than static arp ;)