VPN not passing traffic to client specific override, but can get to pfsense
-
I have an active VPN connection with OpenVPN created to the wizard, and the client specific override is set to allow access to a specific IP on a specific VLAN. The VPN gives an IP in a different subnet (VPN gives an ip in 192.168.1.120, the device I use client specific overrides to live at 192.168.200.200/32 in the .200 vlan. There are no firewall rules aside from letting the .200 vlan out to the internet - but I thought the client specific override should allow that traffic out without explicit firewall rule.
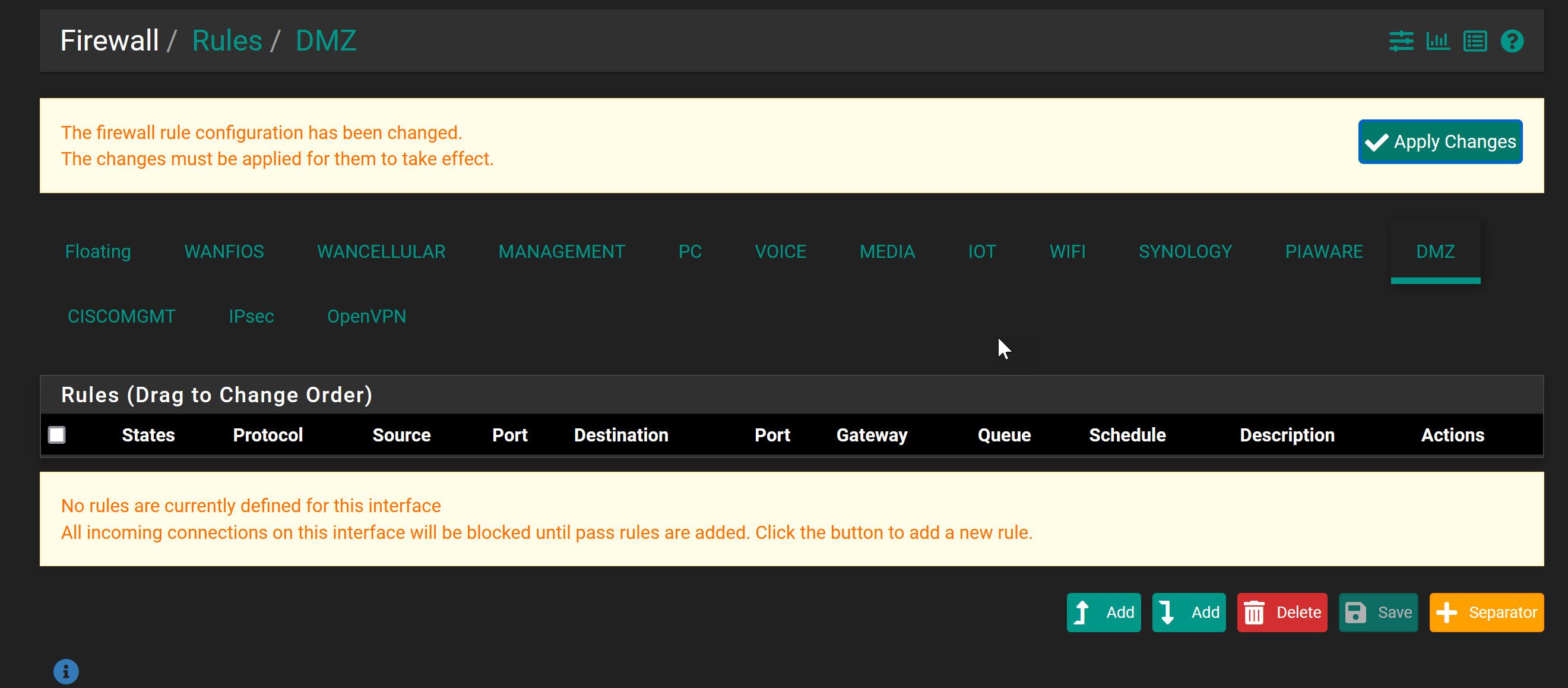
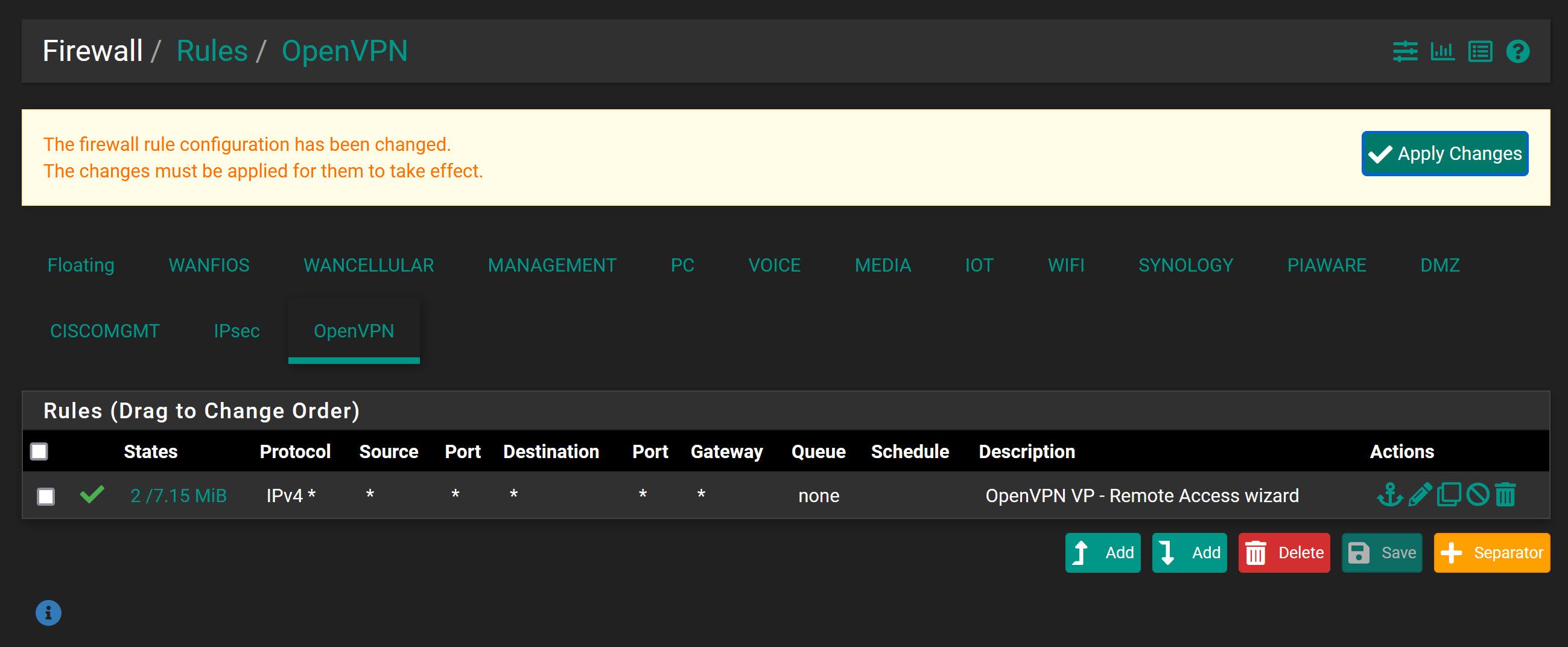
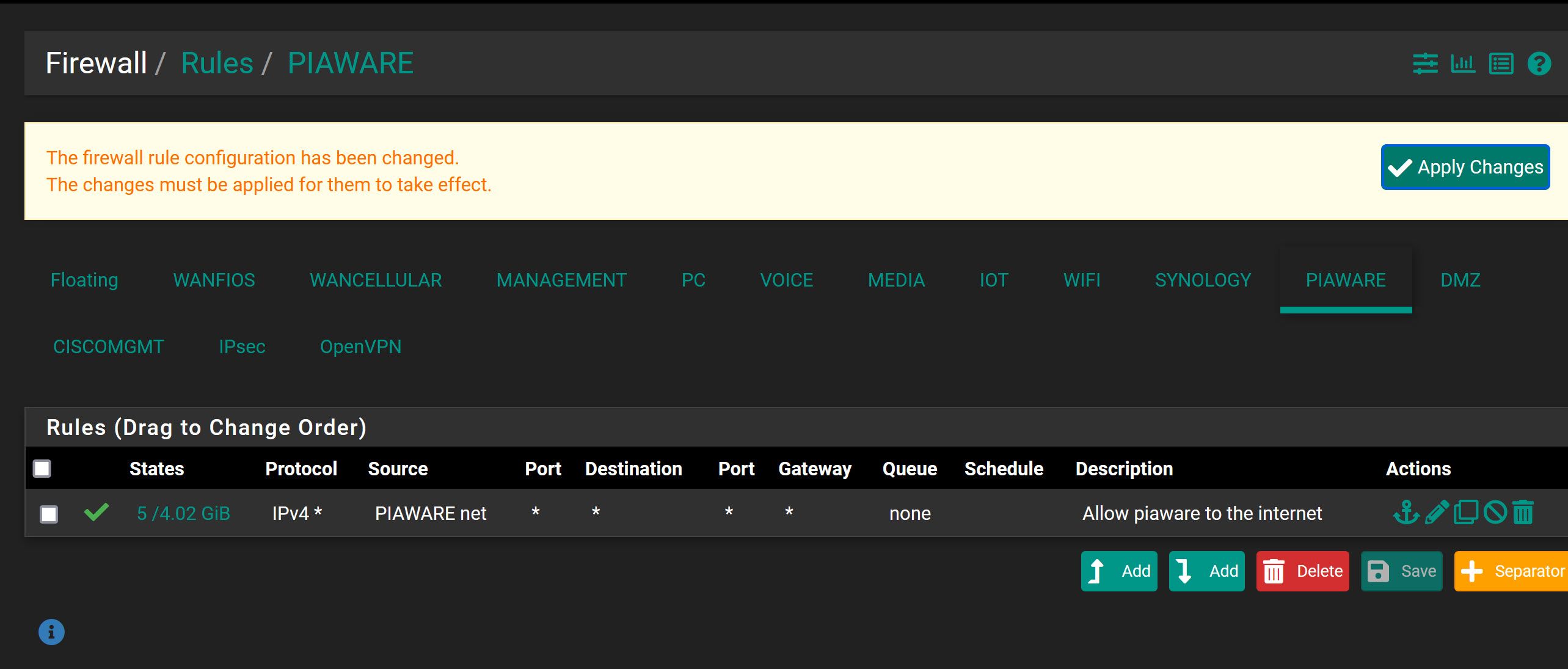
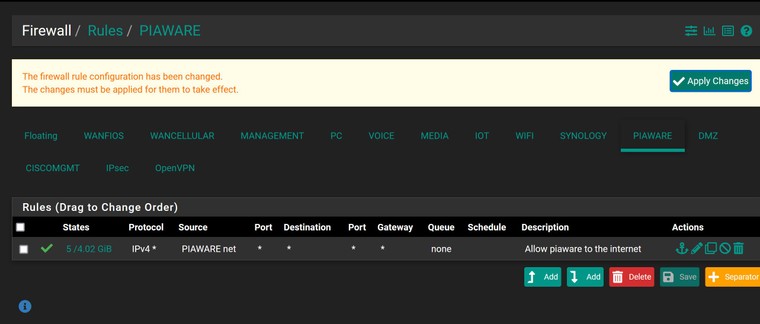
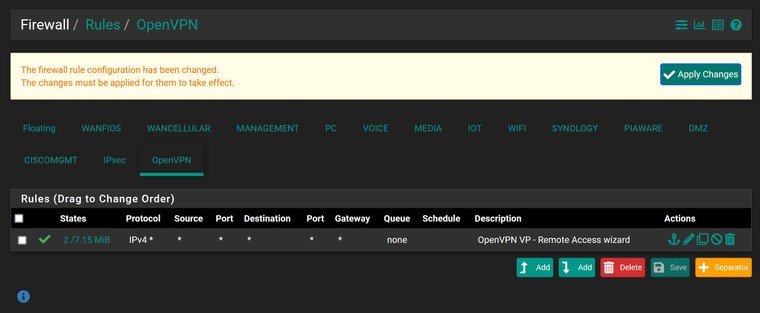
Screenshots of the client specific overrides and the firewall rules for the .200 vlan, the openvpn, and the DMZ (DMZ=.120 where the VPN provides an IP successfully into) Active VPN connections do show healthy in the status on pfsense, and I can get to the pfsense console from there. Anywhere else I should look here?
-
@jmoore
A client specific override allows nothing. It only configures the VPN clients virtual interface and routes.For allowing anything you have to add firewall rules.
When you want to pass internet upstream traffic from the client through the VPN, check "Redirect gateway" in the CSO and add an outbound NAT rule to WAN for its source IP. -
@viragomann Thanks Virago. I turned on the redirect gateway but I'm having trouble with the rule and where to put it. My goal here was to only allow VPN traffic for this single host on this specific vlan, but not to put the VPN users into that VLAN so they couldn't access anything else. Given that they have an IP in this DMZ (.120) - would I still need a firewall rule on the man WAN rule table? Below is the rule I added but still no effect.
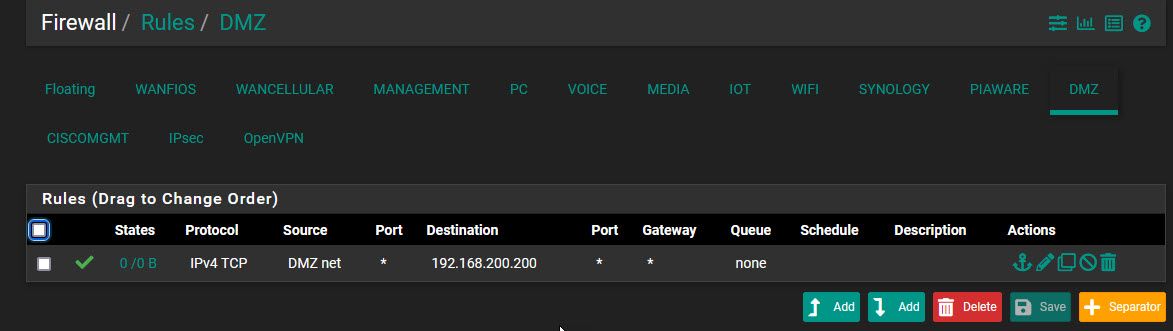
-
@jmoore
Not sure if I understood your setup correctly.
192.168.200.200 is the device which the vpn client should be able to access to and 192.168.1.120 is the virtual vpn IP of the client, correct?If so you have to put the rule on OpenVPN tab and you have to change the source to the clients IP. Rules always have to be added to the interface where the traffic is coming into pfSense.
On the OpenVPN tab the wizard might have added an allow-any rule. So if you want one client with the IP 192.168.1.120 give access to that single IP only, but other clients should still have access to any, you have to put this rule to the top, followed by a block rule for 192.168.1.120 next underneath.
-
@viragomann So that rule looks like it's already in place on the OpenVPN tab.
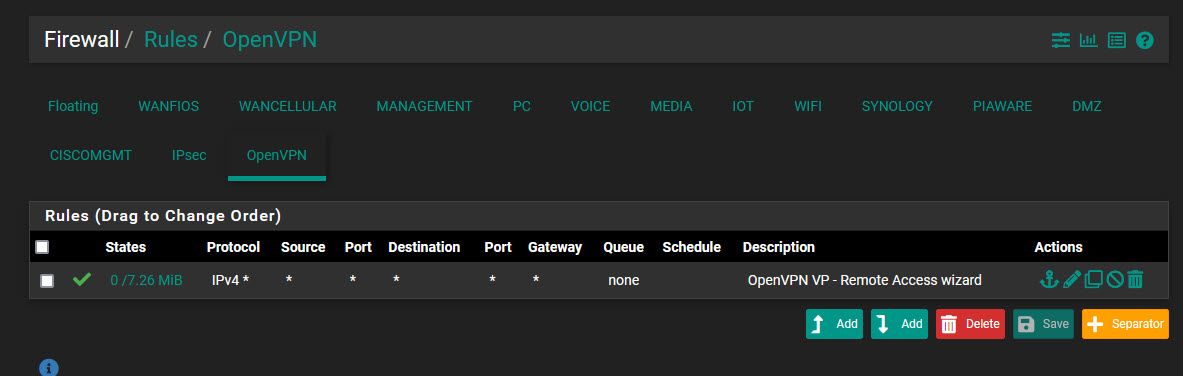
OpenVPN gives out IPs in the .120 subnet (called DMZ in the screenshot) - so a device that connects to the VPN would come in as 192.168.120.2 etc.
The goal is that those devices that connect through OpenVPN would be able to access a device that sits in the .200 VLAN (piaware) - specifically 192.168.200.200. There's nothing else in the DMZ aside from other VPN users, and in the .200 vlan just the single device.
So I open the laptop, connect to OpenVPN - get an IP like 192.168.120.2 - and I should be able to make a connection to 192.168.200.200. Since there could be multiple VPNs connected - I don't know which IP specifically to put in the rule - but if you're getting an IP from OpenVPN in that 192.168.120.x (only used for openvpn) - then it's safe to say I want you to get access to that 192.168.200.200 (which I thought was in client specific overrides).
Does that make sense?
-
@jmoore said in VPN not passing traffic to client specific override, but can get to pfsense:
OpenVPN gives out IPs in the .120 subnet (called DMZ in the screenshot)
I'm wondering, why your OpenVPN clients get IPs out of a so called DMZ subnet. Did you assign this interface to the OpenVPN server and call it DMZ?
Also not clear from your description if only a specific VPN client should get access to 192.168.200.200 or any.
A client specif override is used to assign a specific virtual IP to a VPN client. You can use this IP in filter rules for permitting or blocking access then.
Additionally you can provide specific routes and DNS settings to this client, but this is second-rank and doesn't provide any security benefit. -
@viragomann I don't really have a good answer to why I called it that. I just configured OpenVPN to put the IPs into 192.168.120.x which is the VLAN called DMZ. I think my thinking was that there may be a few folks coming in here, and that they shouldn't be able to really talk to anything else aside from this one device. I had experimented with putting another device in there that I would want the VPN folks to have access to - but didn't move forward with that.
As it stands - any VPN client should be able to access 192.168.200.200. I did create a config with a CSO to another IP - but I didn't use it. Really what I'm trying to get working is just access to that specific device. When I was setting it up, my understanding was the best way in pfsense to get that working with OpenVPN was with the CSO option since the needs for the specific CSO and Cert would be for that specific thing.
So to summerize - a VPN client should connect to the pfsense box, get an IP in 192.168.120.x (I'm willing to change this part) - and be able to send and receive traffic ONLY to 192.168.200.200 - understanding it will need to talk to 192.168.120.1 for DHCP/routing purposes. I did have this working some time ago, but I must have modified a rule and I just can't figure out where I made that change/mistake.
-
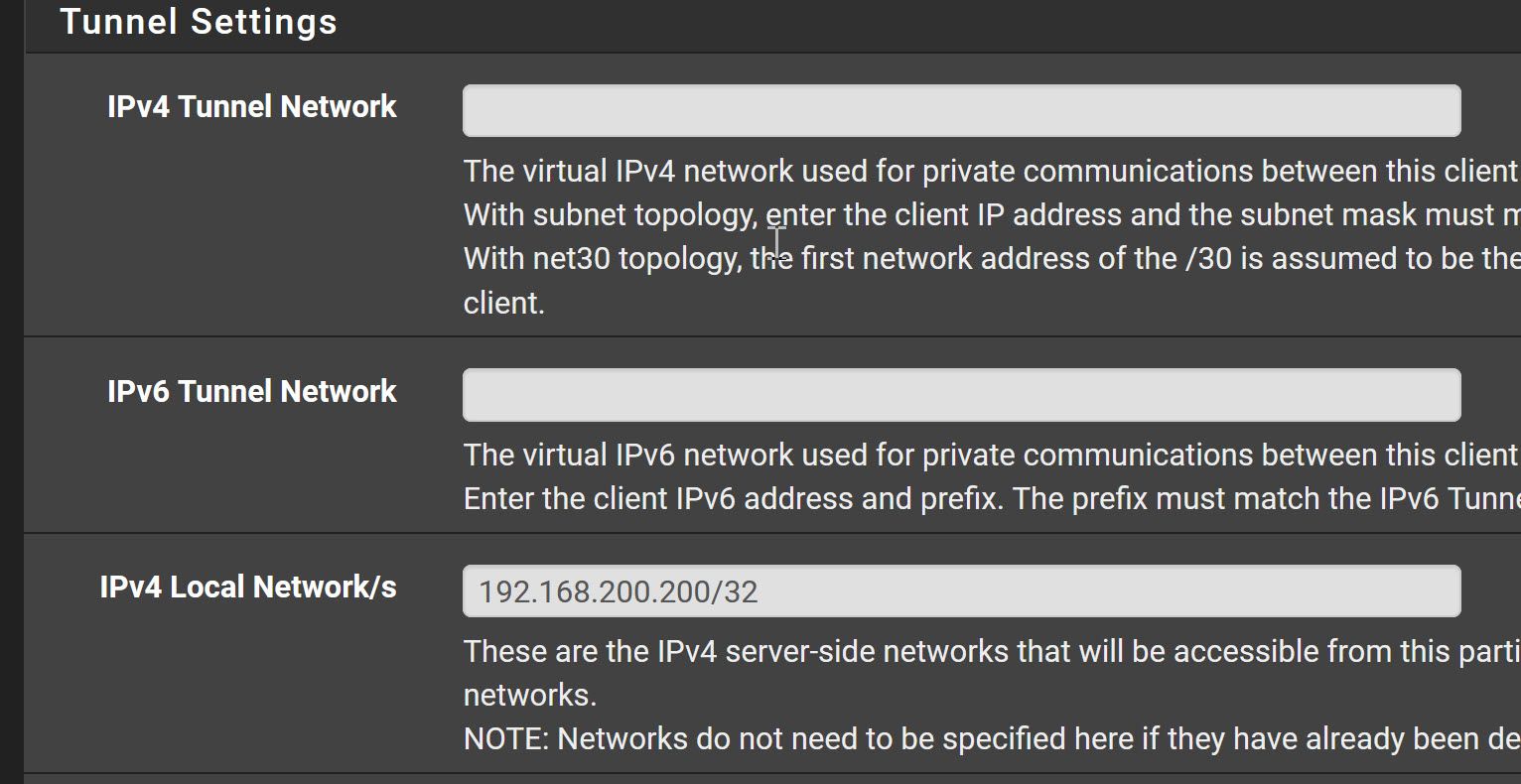
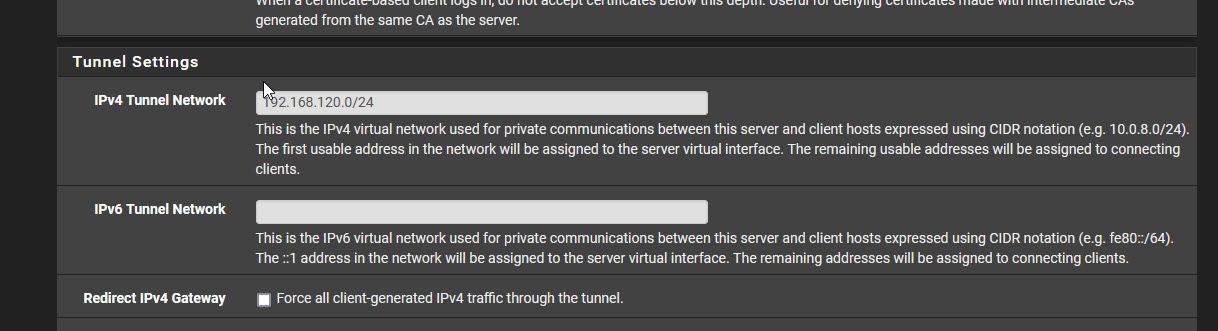
@jmoore I thought it may be helpful to indicate where in the VPN config the tunnel is setup to put the IPs there. There is only one OpenVPN server, with multiple CSOs. Those CSOs are nearly all the same, but using certificate auth for simplicity so that creates multiple CSOs instead of user accounts.
-
@jmoore said in VPN not passing traffic to client specific override, but can get to pfsense:
I don't really have a good answer to why I called it that. I just configured OpenVPN to put the IPs into 192.168.120.x which is the VLAN called DMZ. I think my thinking was that there may be a few folks coming in here, and that they shouldn't be able to really talk to anything else aside from this one device.
For clarification, I'm talking about an OpenVPN server in tun mode, not tap. In tun it makes no sense to use an tunnel subnet, that is already defined on any interface. You will run into routing issues, no matter if there are devices in DMZ using this IP or not.
So to summerize - a VPN client should connect to the pfsense box, get an IP in 192.168.120.x (I'm willing to change this part) - and be able to send and receive traffic ONLY to 192.168.200.200 - understanding it will need to talk to 192.168.120.1 for DHCP/routing purposes. I did have this working some time ago, but I must have modified a rule and I just can't figure out where I made that change/mistake.
So you simply have to enter 192.168.200.200 into the "Local Networks" box in the OpenVPN server settings. There is no need for a CSO here.
Then edit the firewall rule on the OpenVPN tab and change the destination to single IP: 192.168.200.200. -
@viragomann Makes sense - I put that into the Local Networks box and now it's all set. I kept the CSO setup because it makes for easier export of the installers or config files with the certificates embedded for the specific 'user' or cert - but since this was my use case - it's working perfectly now.
Thank you for all your help today - I learned a lot.