Cannot connect from tun_wg0 to LAN
-
Hi Guys!
Apologies, if this has been asked previously, however, I could not find a solution here.
I have the following scenario.
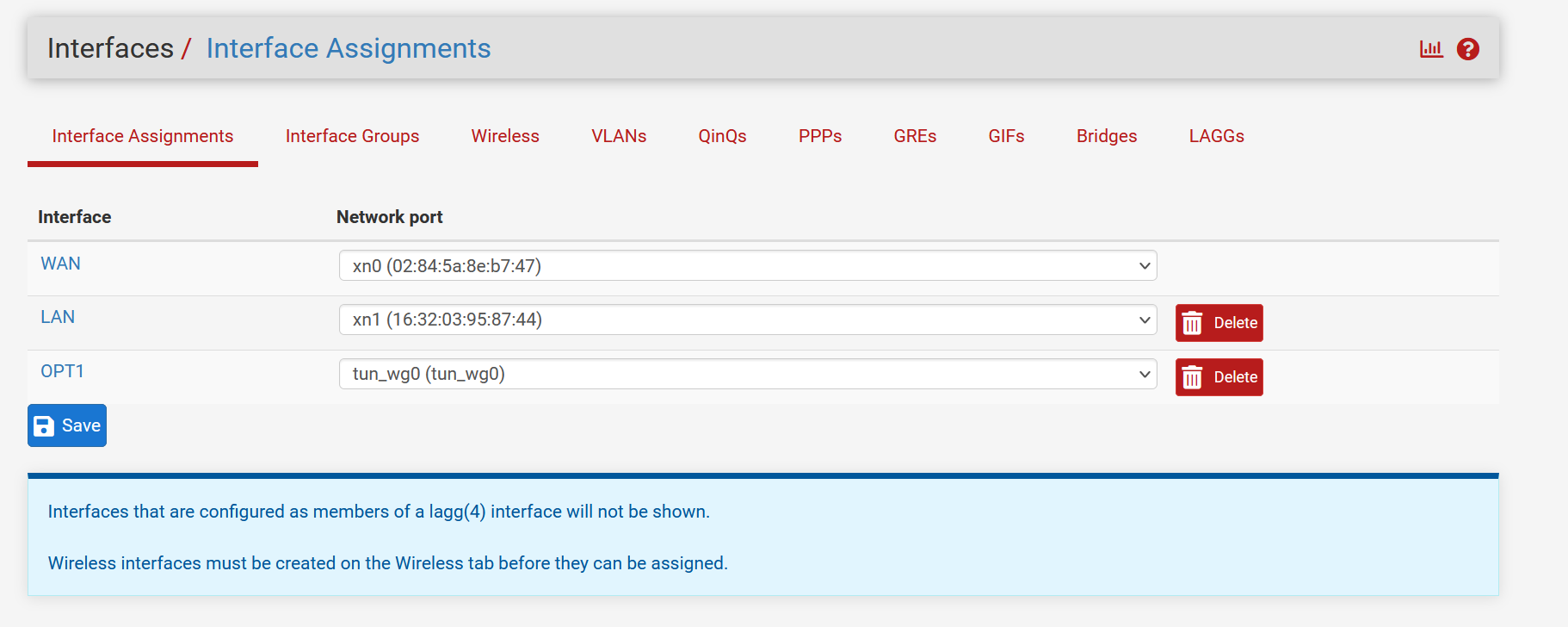
PFsense server with 2 NICs
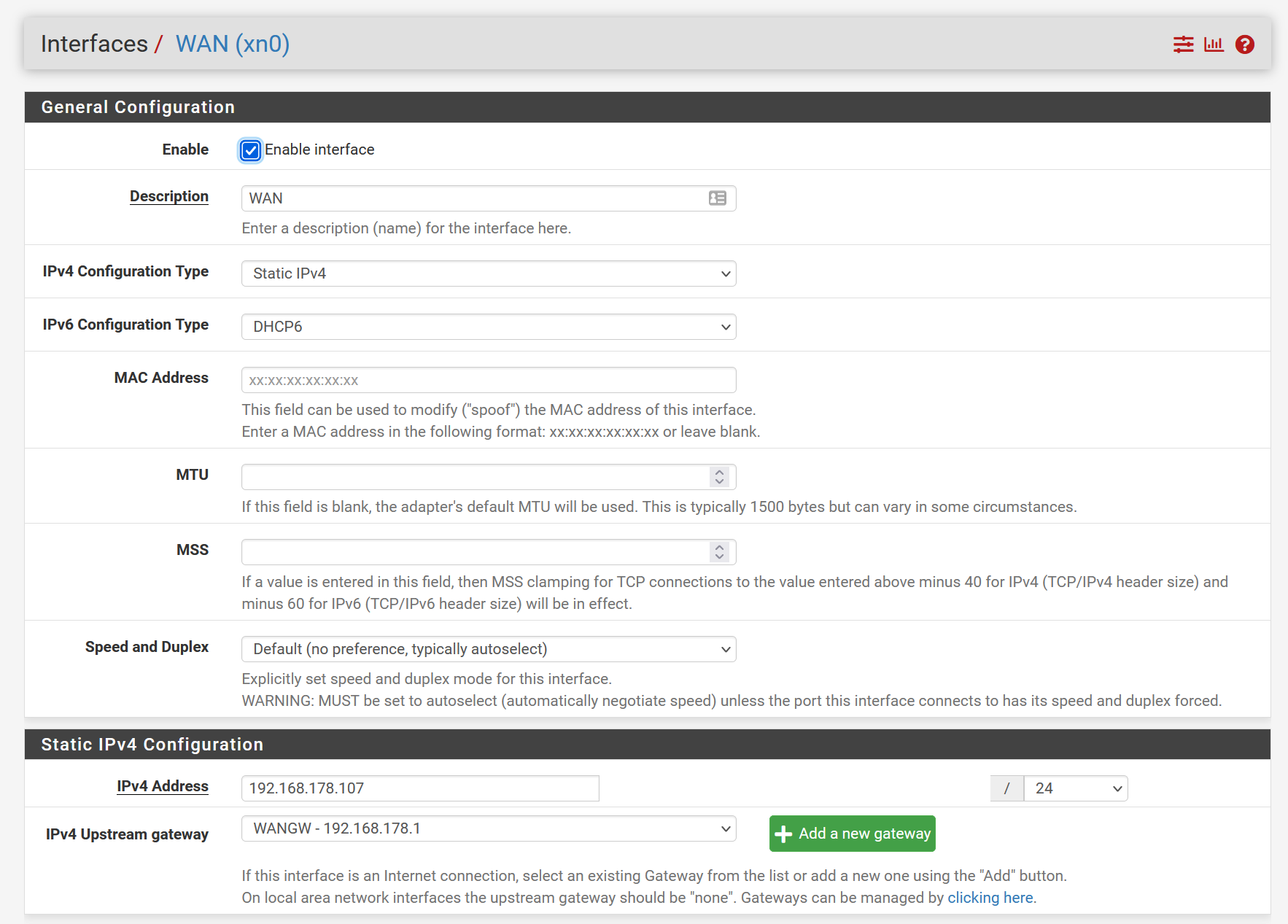
1x WAN: 192.168.178.0/24
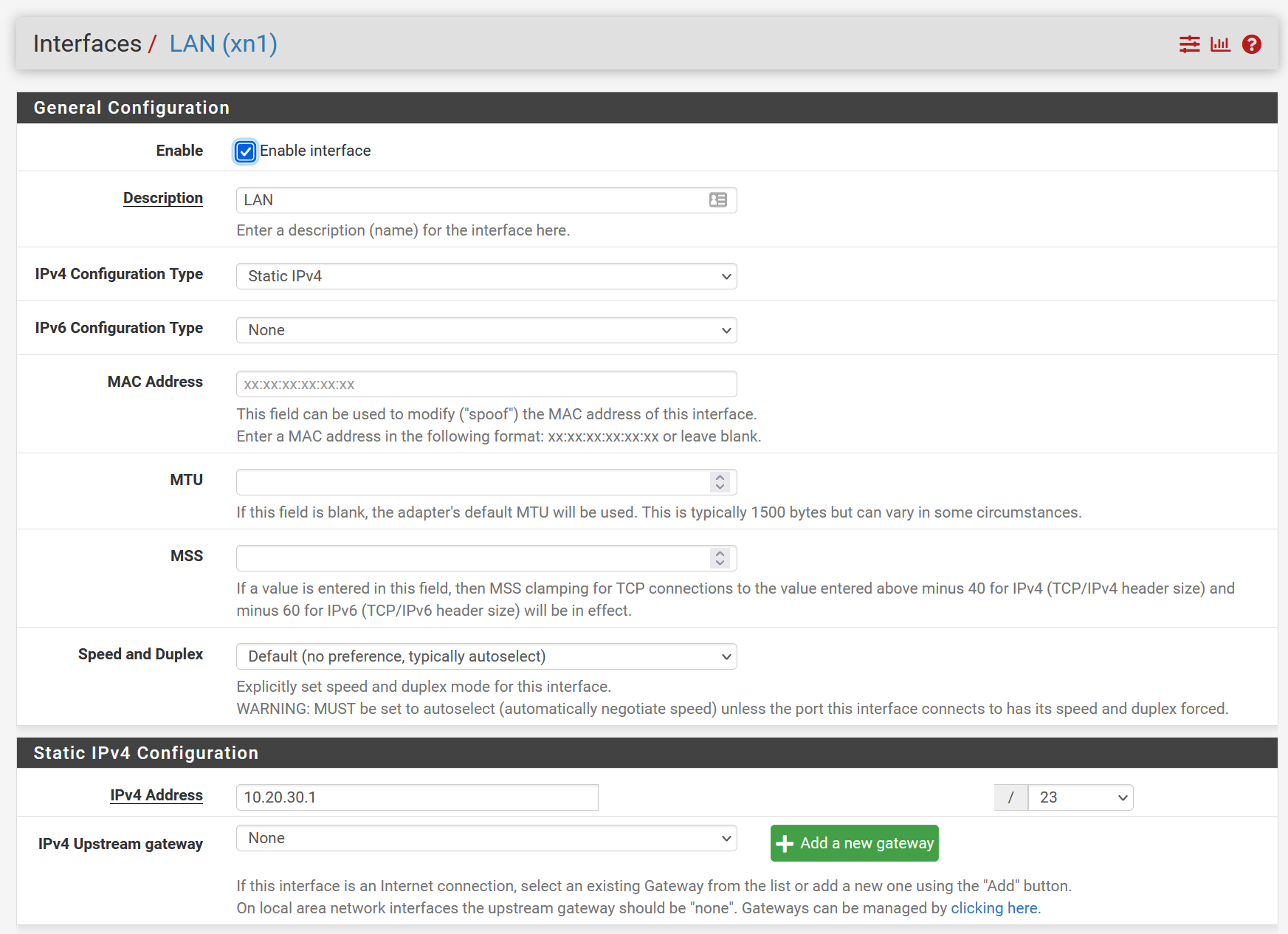
1x LAN: 10.20.30.0/23
an HP ProCurve 2524 switch some more clients connected to it, that are all coming in via the LAN connection to pfSenseOn pfSense I set up a Wireguard tunnel with one peer.
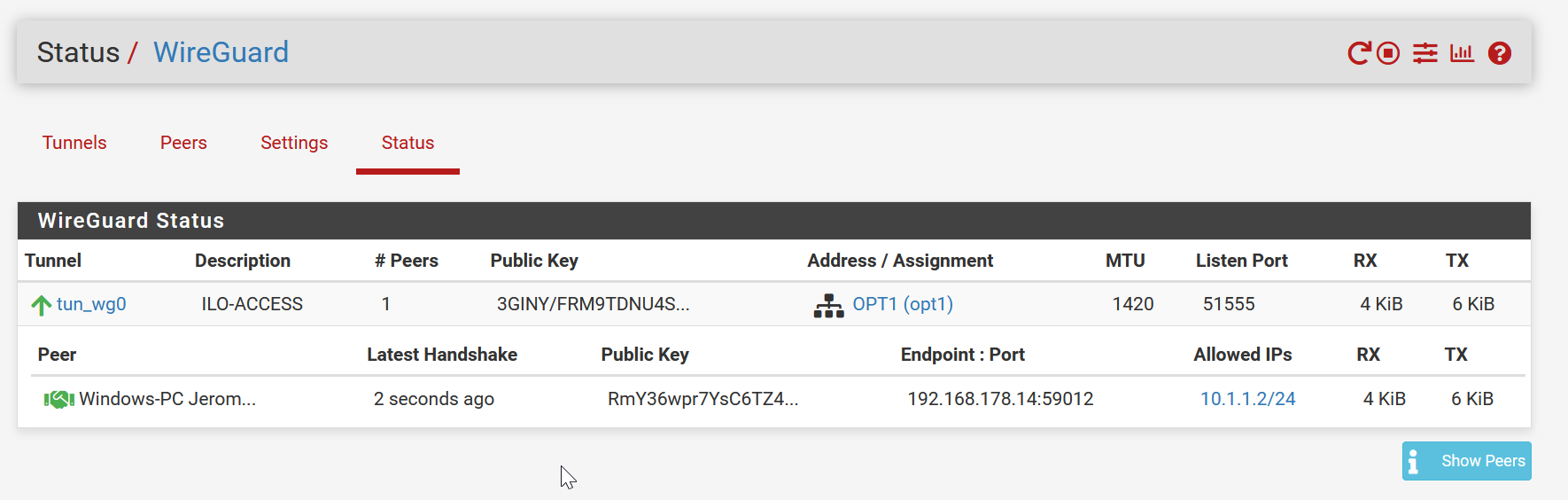
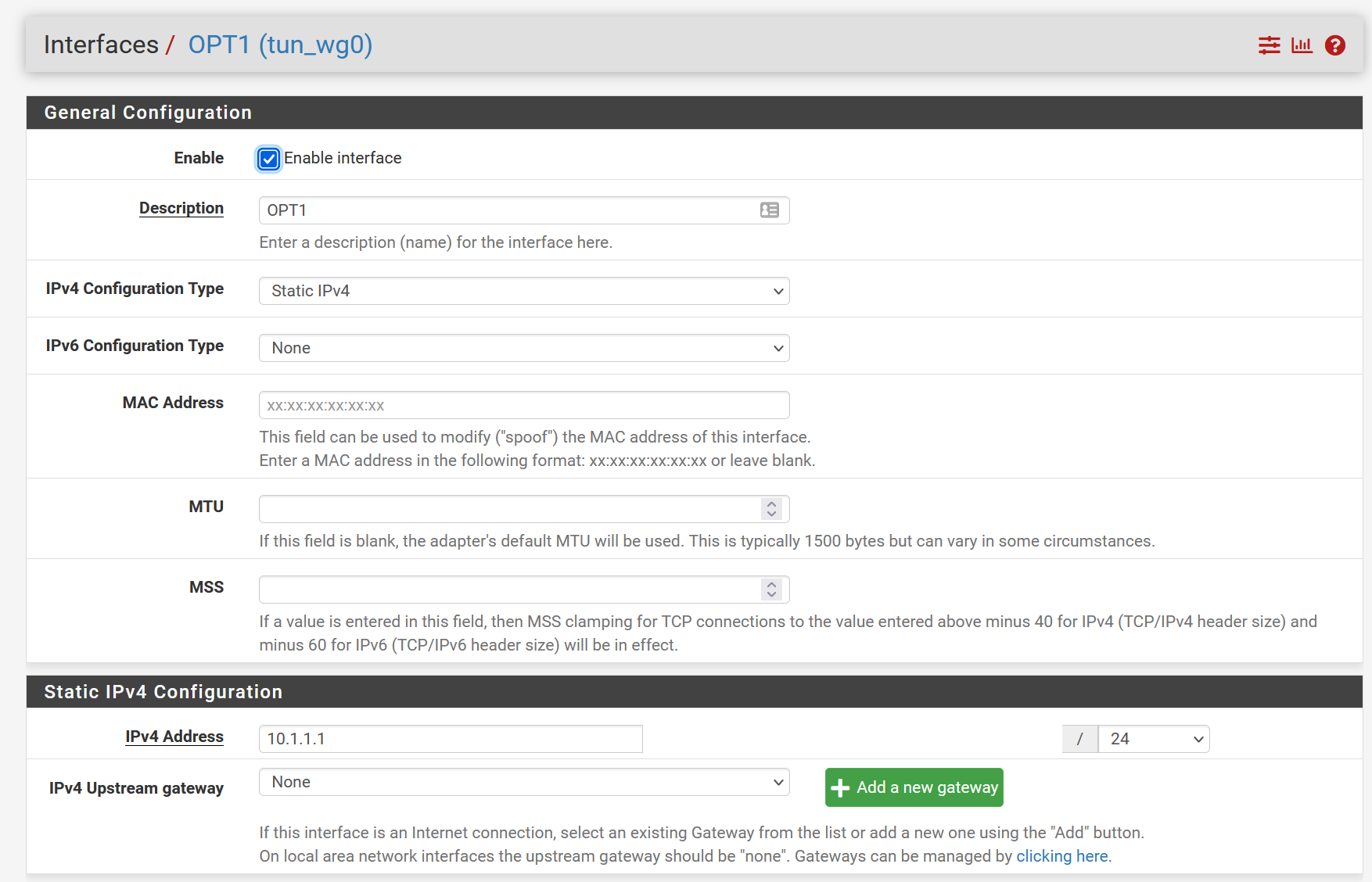
The Wireguard network is 10.1.1.0/24Connecting to that tunnel works fine, as well as being able to ping (once connected) the following:
10.1.1.1 (pfsense server, tun_wg0 device)
10.1.1.2 (my client)
10.20.30.1 (pfsense server on the LAN interface).However, I cannot access other LAN clients, that are coming in via the LAN network.
I have two other clients (10.20.30.5 and 10.20.30.10) but cannot reach any of them.
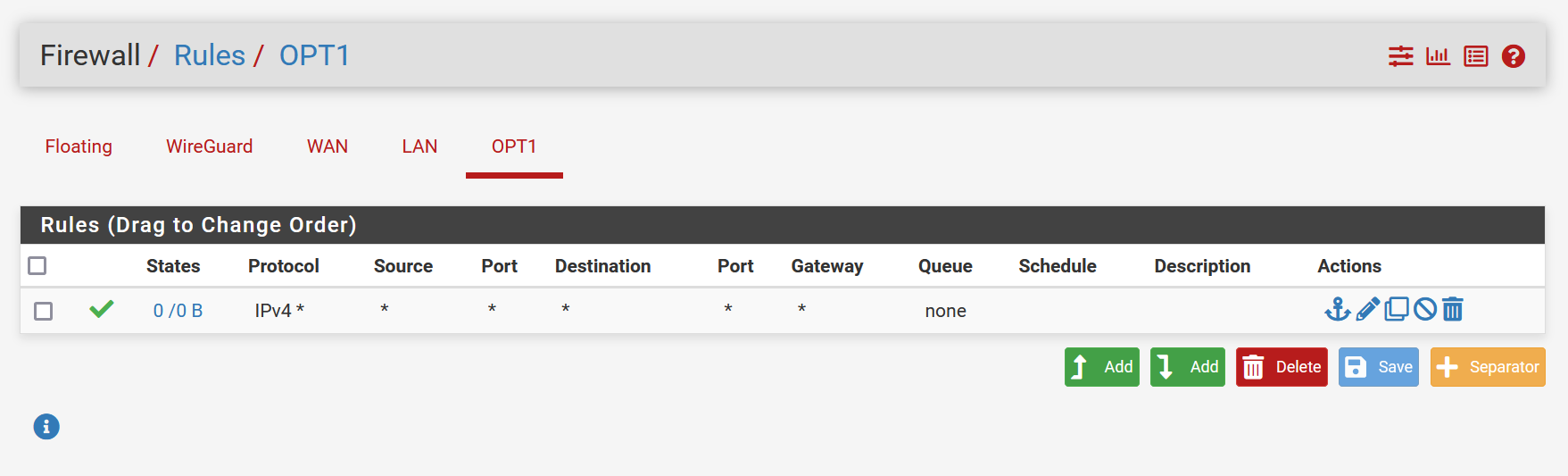
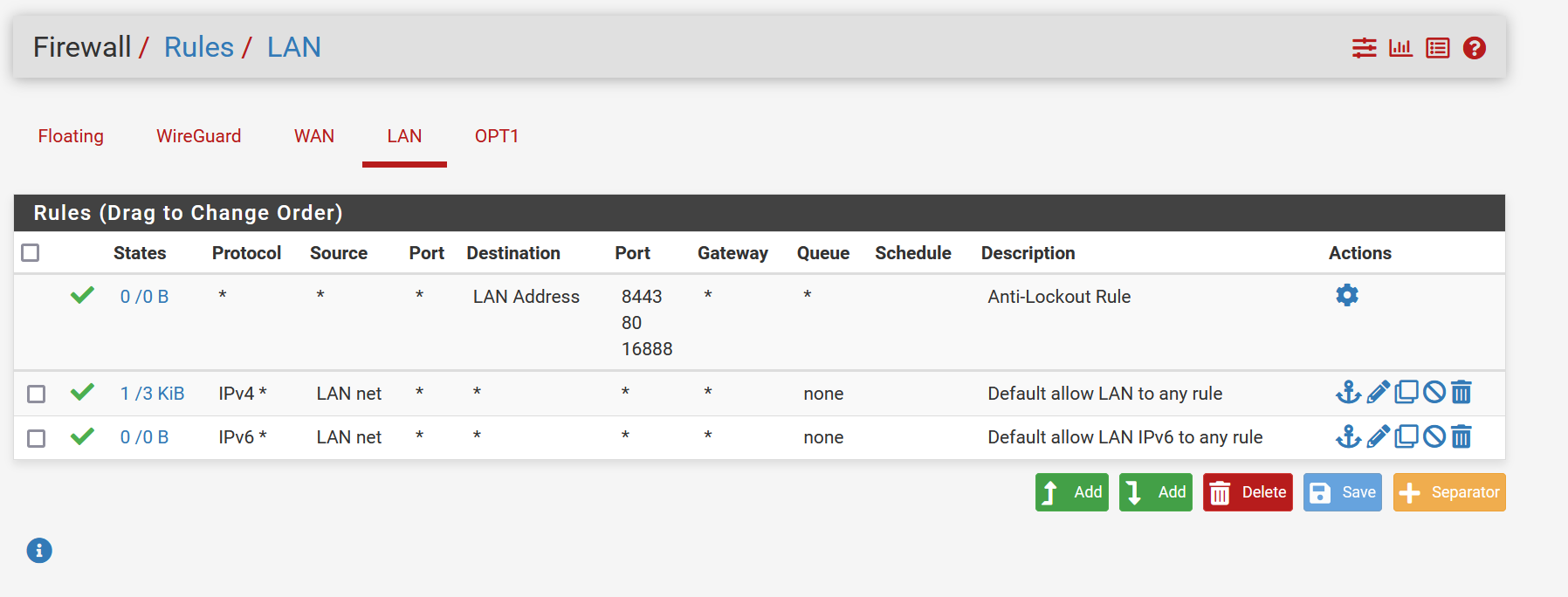
To be sure, it'S not a firewall related issue, I created an "accept all rule" on LAN and OPT1 (which is the tun_wg0 device)When trying to ping these clients (10.20.30.5 and 10.20.30.10) from either the ping-tool in pfSense or from SSH directly, both clients respond fine).
What did I miss to be able to reach my clients, when being connected via WireGuard?
If necessary I attached a bunch of screenshots of my relevant config, if necessary.
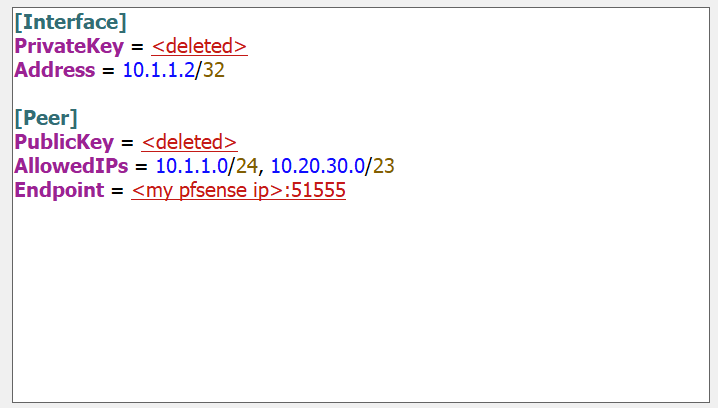
Wireguard App Config
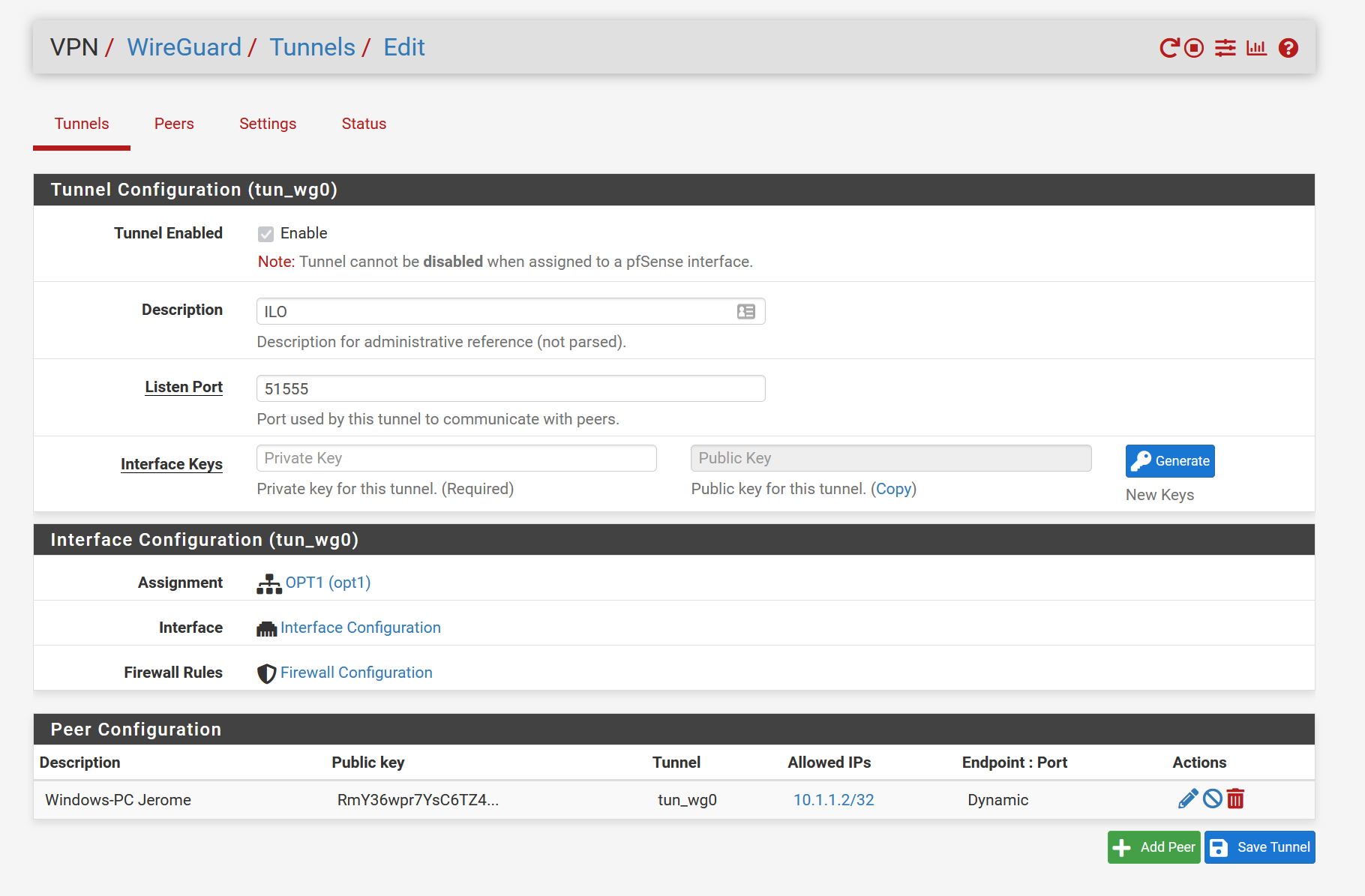
Wireguard Tunnel Configuration
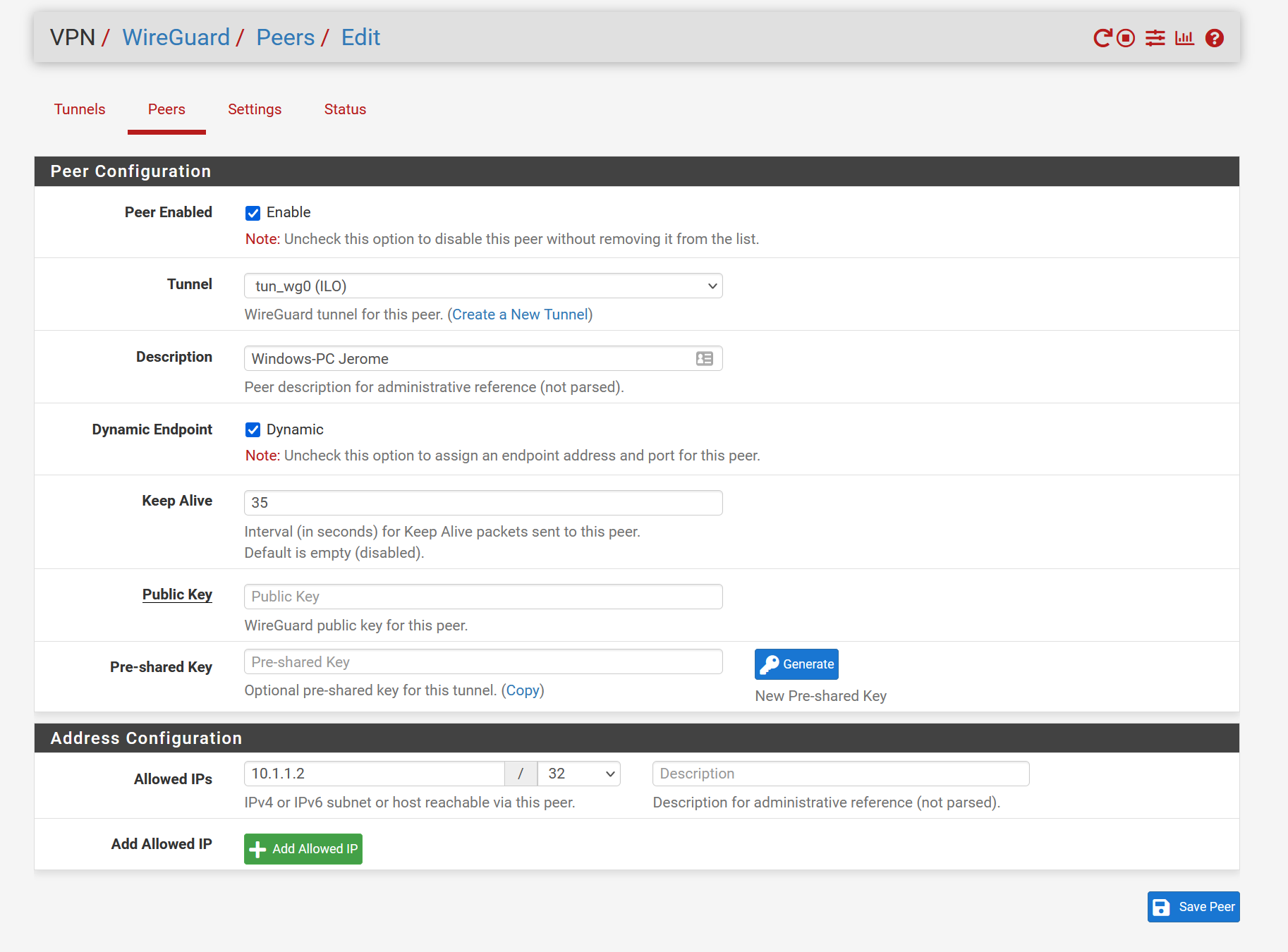
Wireguard Peer Configuration
Firewall Rules OPT1
Firewall Rules LAN
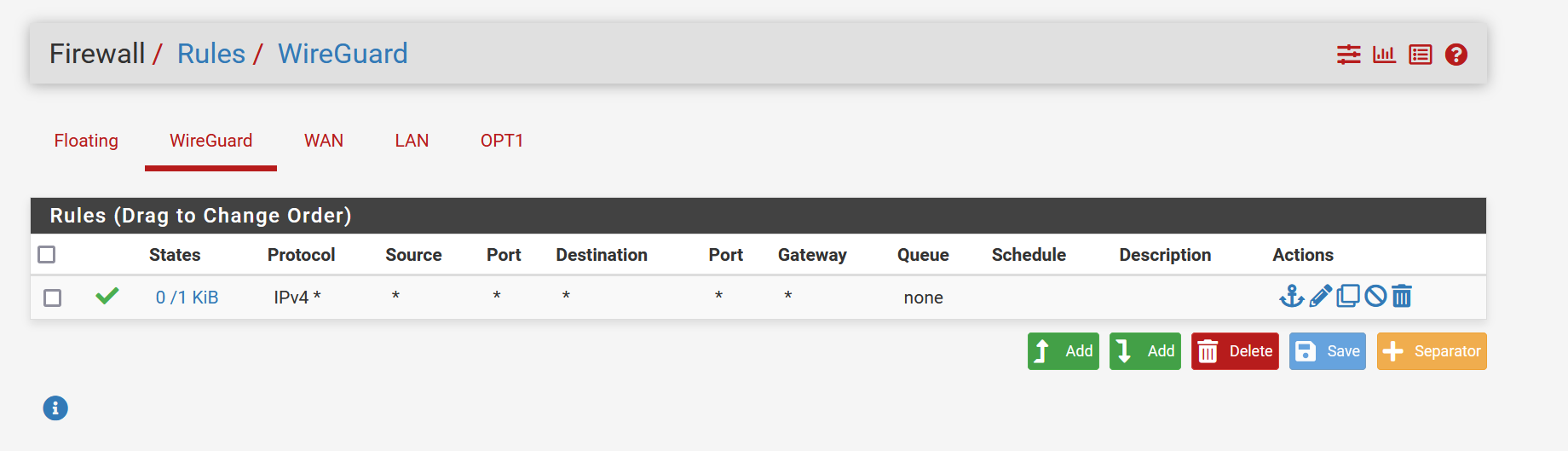
Firewall Rules Wireguard
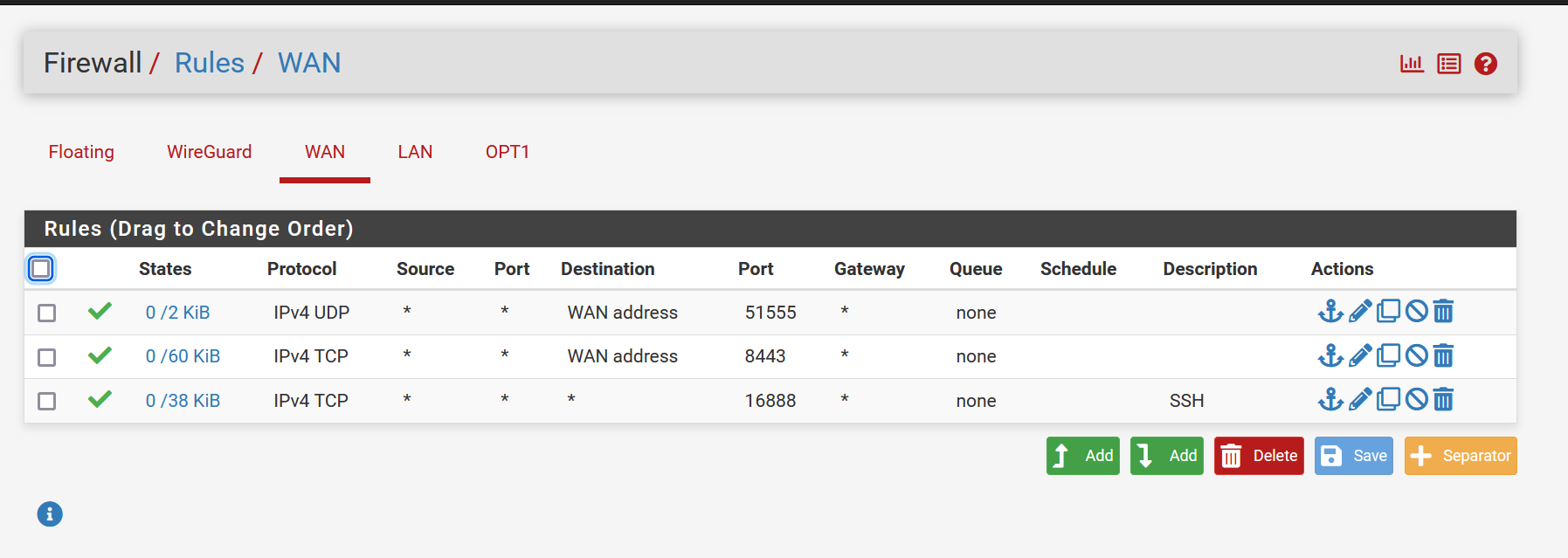
Firewall Rules WAN
Interface-Setup tun_wg0
Interface-Setup LAN
Interface-Setup WAN
Interface Assignments
Any help would be appreciated!
Thanks a lot and best regards,
tanjix
-
@tanjix
Try deleting the rule on Interface OPT1. Its not necessary.
Next enter 1420 in MTU and
1380 in MSS for interface OPT1 (tun_wg0).
Rest should be ok.
Maybe that helps. -
@_igor_ said in Cannot connect from tun_wg0 to LAN:
@tanjix
Try deleting the rule on Interface OPT1. Its not necessary.
Next enter 1420 in MTU and
1380 in MSS for interface OPT1 (tun_wg0).
Rest should be ok.
Maybe that helps.Thanks for your input; I applied the changes you suggested, but I still do not have success in reaching clients on the 10.20.30.0/23 network through WireGuard, once I am connected. :-(
-
@tanjix
I built my tunnel with help from here: Look at the Client part with the pub-key, which has to be entered at pfsense peer.
Pub-key from pfsense has to be entered at client-side.
Does your client appear at the status-page from Wireguard on pfsense? is it shown green?
Your second screenshot shows missing Interface-keys... -
@_igor_ said in Cannot connect from tun_wg0 to LAN:
@tanjix
I built my tunnel with help from here: Look at the Client part with the pub-key, which has to be entered at pfsense peer.
Pub-key from pfsense has to be entered at client-side.
Does your client appear at the status-page from Wireguard on pfsense? is it shown green?
Your second screenshot shows missing Interface-keys...Hi igor,
yes, on the status page I am shown as green.
Correct, the keys aren't on the screenshot as I removed them before screenshotting, but they are there.
Like I said, once I am connected, I can ping the devices itself:10.1.1.1 (pfsense server, tun_wg0 device)
10.1.1.2 (my client)
10.20.30.1 (pfsense server on the LAN interface).However, I cannot reach clients behind the LAN interface, like 10.20.30.5, 10.20.30.10 or 10.20.30.20.
Thanks, tanjix
-
-
Sorry, forgot the link: https://itigic.com/how-to-configure-wireguard-vpn-server-in-pfsense/
One other thing: I miss a rule from LAN, which allows traffic from the WG to LAN.
Try an any to any rule for LAN. Change Source LAN-NET to any. -
@_igor_ said in Cannot connect from tun_wg0 to LAN:
Sorry, forgot the link: https://itigic.com/how-to-configure-wireguard-vpn-server-in-pfsense/
One other thing: I miss a rule from LAN, which allows traffic from the WG to LAN.
Try an any to any rule for LAN. Change Source LAN-NET to any.Hi,
do you mean a rule like that?
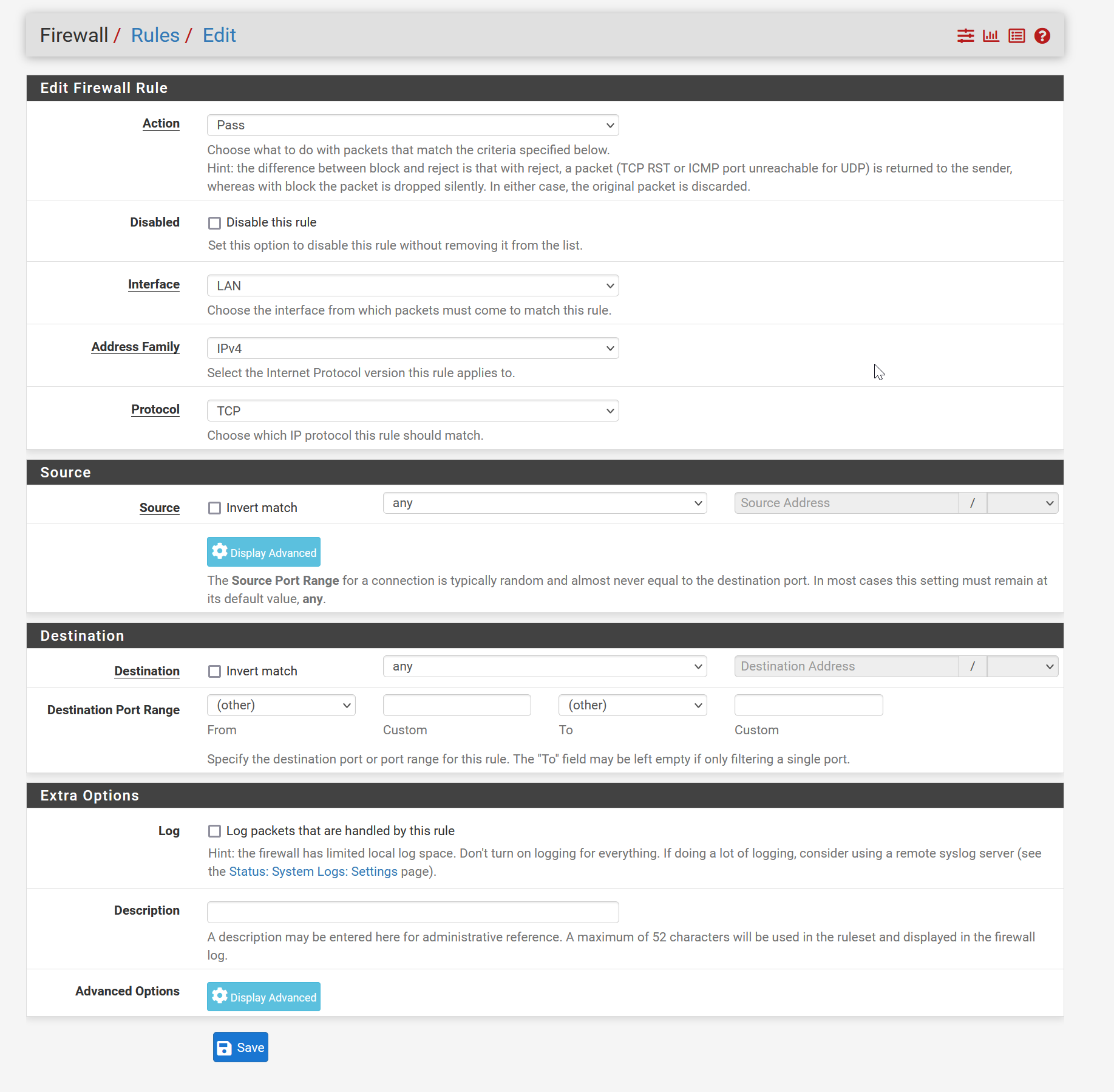
If so, it does not work either, still unable to ping clients behind the LAN interface.
-
@tanjix said in Cannot connect from tun_wg0 to LAN:
@_igor_ said in Cannot connect from tun_wg0 to LAN:
Sorry, forgot the link: https://itigic.com/how-to-configure-wireguard-vpn-server-in-pfsense/
One other thing: I miss a rule from LAN, which allows traffic from the WG to LAN.
Try an any to any rule for LAN. Change Source LAN-NET to any.Hi,
do you mean a rule like that?

If so, it does not work either, still unable to ping clients behind the LAN interface.
Bump! Did you get this working? i am in the same boat tried assigning wireguard to interface and allow that interface to LAN net same issue and also tried with out. Also tried on client peer on phone 0.0.0.0/0 or lan address same issue.
-
@dkeller
The current WG package doesn’t setup any routes.
So for the peers you create in pfsense, the allowed ips need static routes created.
Also you are going to have to check outbound NAT and set to manual and remove any NATing on your WG gateway.Create the tun_wg0 interface
static ipv4
10.1.1.1/24
none for gatewayThen go to system -> routing
create a new gateway
using the assigned opt interface for the tun_wg0 (or whatever you name it)
set gateway to 10.1.1.2Now goto system->routing->static routes
create a new static route
10.1.1.2/32
using the gateway you created aboveThen you need to goto firewall->nat->outbound
set to manual
remove any of the assigned opt interface
remove any NATing of 10.1.1.1/24 on the assigned opt interfacealso if you need to access pfsense dns you have to setup that on your client. you can use the opt interface address and just make sure it’s enabled in dns resolver
give that a try and see if connections work.
for the 0.0.0.0/0 access
you have to do the above but create a second gateway with address the one of client 10.1.1.3
then add static route to that ipthen you need to setup outbound NAT
Use WAN
source 10.1.1.3/32 (or 10.1.1.0/24 if you want all clients to route through wan)
NAT address set to WAN addressagain make sure you have DNS setup on client to resolve things. either point to your pfsense box or some other DNS server
-
@dcgibby said in Cannot connect from tun_wg0 to LAN:
@dkeller
The current WG package doesn’t setup any routes.
So for the peers you create in pfsense, the allowed ips need static routes created.
Also you are going to have to check outbound NAT and set to manual and remove any NATing on your WG gateway.Create the tun_wg0 interface
static ipv4
10.1.1.1/24
none for gatewayThen go to system -> routing
create a new gateway
using the assigned opt interface for the tun_wg0 (or whatever you name it)
set gateway to 10.1.1.2Now goto system->routing->static routes
create a new static route
10.1.1.2/32
using the gateway you created aboveThen you need to goto firewall->nat->outbound
set to manual
remove any of the assigned opt interface
remove any NATing of 10.1.1.1/24 on the assigned opt interfacealso if you need to access pfsense dns you have to setup that on your client. you can use the opt interface address and just make sure it’s enabled in dns resolver
give that a try and see if connections work.
for the 0.0.0.0/0 access
you have to do the above but create a second gateway with address the one of client 10.1.1.3
then add static route to that ipthen you need to setup outbound NAT
Use WAN
source 10.1.1.3/32 (or 10.1.1.0/24 if you want all clients to route through wan)
NAT address set to WAN addressagain make sure you have DNS setup on client to resolve things. either point to your pfsense box or some other DNS server
I'll give it a go and see. Is it me or the primary purpose of vpn is to go from client to server anyway, would you focus on that part first with a package?