[noob question] pfSense as a OpenVPN client for selected devices
-
@draghmar
"Don't pull routes" prevents that the default route is changed to the vpn provider, when the client connection is established.
If you leave this unchecked and the provider pushes the default route to you (what I assume) the whole upstream traffic from you local network is directed over the vpn, which is not that, what you want as you stated above. -
@viragomann Hm...I get it but I didn't see that behavior. I mean, only the two devices I was testing with, had their traffic pushed through VPN. Other devices did not. Anyway, I have the whole setup disabled currently and will check that option tomorrow. Thanks for suggestions and explanation. :)
-
Another report from VPN battlefield. ;)
So it works for me but I've notice that some detection tools still know that I'm using VPN even though I tested on different servers and at least one knew my own IP for some reason. I didn't do anything to DNS settings. Should I change something? My brother suggested that services may detect VPN by checking DNS somehow, so maybe I should do something...But is there a way to make it work in a way that everything goes as usual except for VPN traffic? Maybe I should set DNS Resolver'sOutgoing Network Interfacesto everything except VPN interface? -
@draghmar
Yes, that might be detected by leaking DNS.You can setup the resolver to send request out to the VPN interface only. However, this setting is applied also to DNS requests from other devices, which possibly isn't desired.
To affect only these certain devices you're directing out to the VPN, you can simply forward DNS traffic from the concerned devices to a public DNS server and policy route this traffic to the VPN gateway.
-
@viragomann I have one rule that directs all requests that would go outside of LAN on port 53 to local. If I would put rule above that one, where specific IPs would be directed to DNS IP from VPN provider, would that work I think it should?
-
@draghmar
Should work that way. -
Because I'm a little bit afraid I'm going to break something with DNS I'll ask if what I want to do is ok. :P
I have Port Forward set using this recipe. My idea is to create alias with DNS from NordVPN and then create new Port Forward, above previous one. Choosing LAN as a interace I will add specific devices in the source field for port 53, destination will beset to
anyfor port 53 and redirect IP to VPN DNS alias.
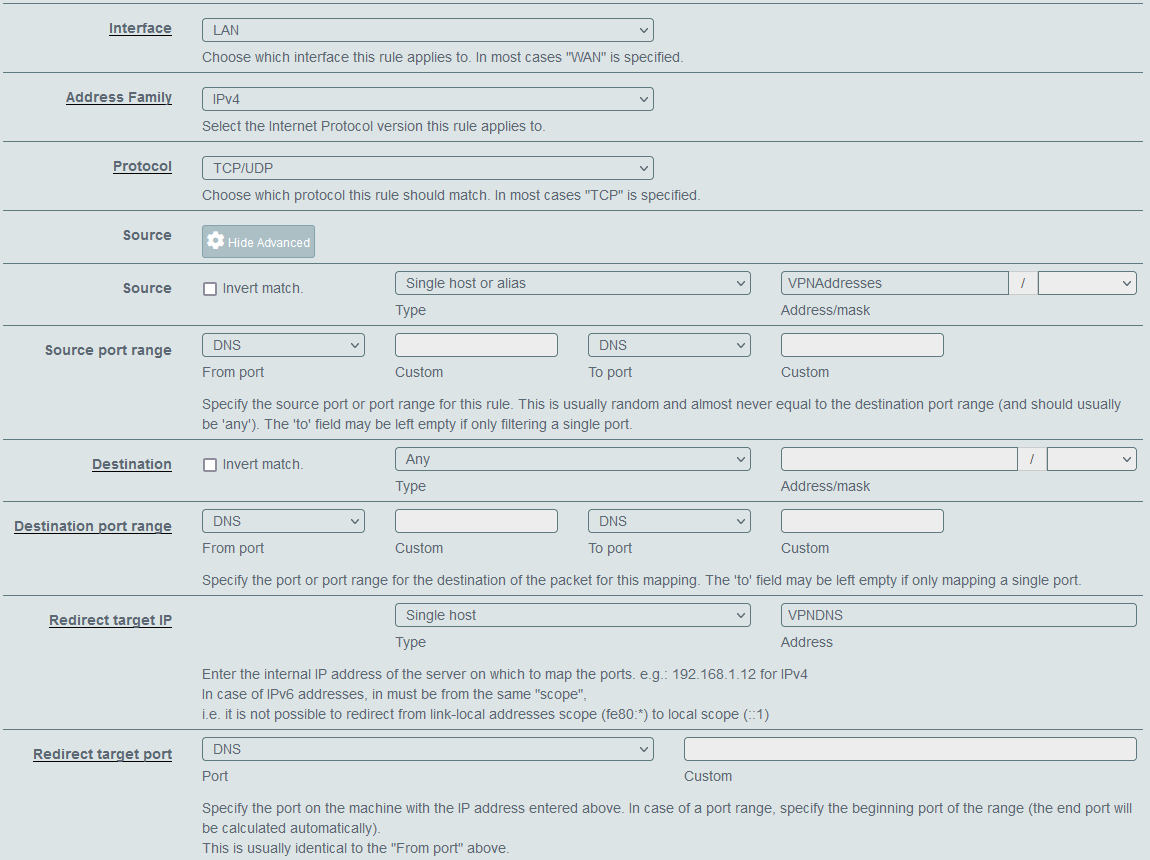
Will that be enough?
I saw in OpenVPN'sClient Specific Overridesthat I can set there DNS. Should I do that? I'd guess not but who knows. ;) -
@draghmar said in [noob question] pfSense as a OpenVPN client for selected devices:
Will that be enough?
The forwarding looks well, but you have also to direct that traffic to the VPN provider. This isn't done by NAT.
You have to add a policy routing rule with the VPNDNS alias as destination and set the gateway to the VPN.I saw in OpenVPN's Client Specific Overrides that I can set there DNS.
This is used by VPN access servers to set certain directives for specific clients. It cannot be used in your case.
Consider that the your "VPNAdresse"s may possibly use DoH for name resolution. To cover this, you have to direct their HTTPS upstream traffic to the VPN server by poilcy routing.
-
@viragomann said in [noob question] pfSense as a OpenVPN client for selected devices:
The forwarding looks well, but you have also to direct that traffic to the VPN provider. This isn't done by NAT.
You have to add a policy routing rule with the VPNDNS alias as destination and set the gateway to the VPN.Isn't that added automatically? I have a rule like that from creating Port Forward from the recipe. I guess I'd have to edit this new one then to set VPN Gateway in advanced settings, right?
-
@draghmar
Depends on the rule creation option:
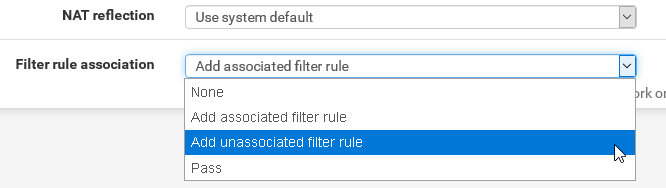
However, pfSenes cannot create a policy rule from a NAT, since there is no gateway info.
So at best you can let it create an unassociated filter rule and edit it after to set the gateway.
-
@viragomann I think I did everything but https://dnsleaktest.com still is able to detect my IP. :( I have Port Forward set as above and in the created rule I changed gateway to VPN one. What else am I missing?
-
@draghmar
Maybe there is an other rule matching the DNS traffic before. Floating rule?Enable logging in the rule to investigate.
-
@viragomann Hm...I checked
Log packets that are handled by this rulebut I don't see anything inSystem logs->Firewallpoping up when browsing websites from device I'm testing from. And I don't have any other rule DNS related, just those two. I have fairly simple network here. No floating or anything fancy like that ;) -
@draghmar
Do you consider the possibility that the client may use DoH?
So what's about its HTTPS traffic? -
@viragomann I'm testing from FireFox on Win 10 with DoH disabled and DNS servers set to router IP.
What about HTTPS traffic? -
@draghmar
When using DoH the DNS traffic goes over HTTPS protocol.Never seen you rule set, so I cannot say if they are ok.
But for testing, direct the whole upstream traffic from the 'VPN clients' to the VPN server.
Verify that the policy routing rule matches. -
@viragomann Those are my NAT and rules:
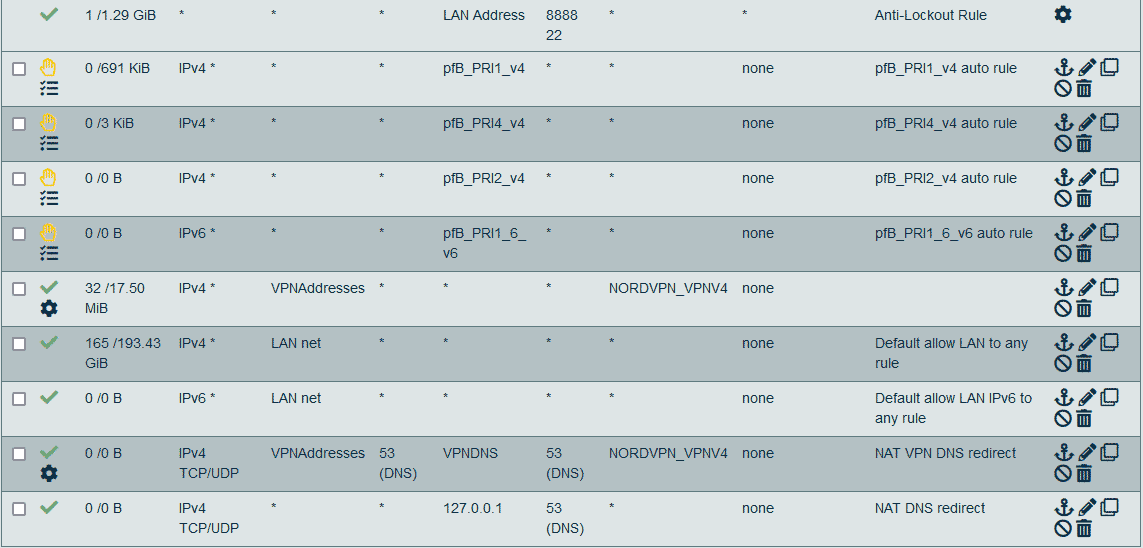
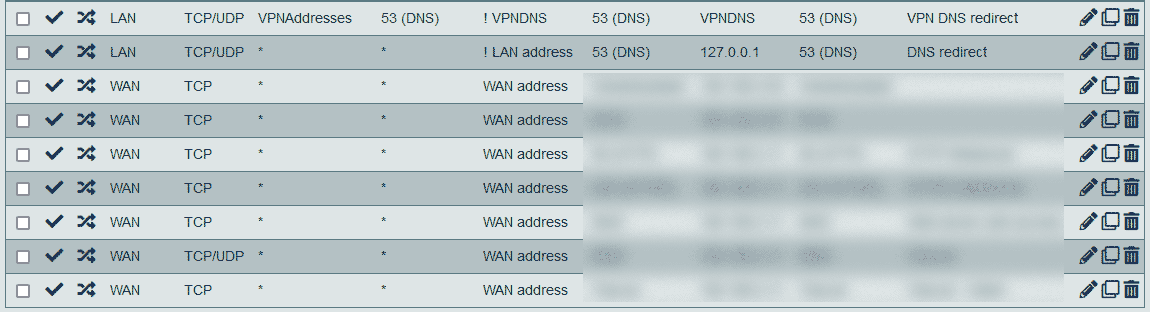
Like I said - nothing complicated. ;) There are some NATs for web server and such. But that's it. The only additional thing are the rules for OpenVPN and for VPN interface. And those are ones we've discussed in this thread.How can I direct like you said? I thought I just did force every device that should go through VPN to VPN server. The rule for that is visible on the list above.
Is there way to make some artificial connection to the DNS server that so could be sure that the flow is correct? I mean something like trying to connect to DNS IP having DNS port. I'm thinking here that I could try connect to router IP this way to check if it's redirected. I'd like to eliminate other factors this way because the only thing I know about testing this is to simply hit some URL from specified device...
-
@draghmar
You must not set a source port in the DNS rule, it has to be any. -
@viragomann Yup, that was it! Thanks! Now everything seems to work as it should. :D