Error in legacy mode of snort service.
-
Hello!!! I am testing the snort service in Pfsense and I need an IP to be detected and blocked, but the snort service is not working for me and I don't understand it.
Attached is my configuration, do you see any configuration wrong or do you know about it?

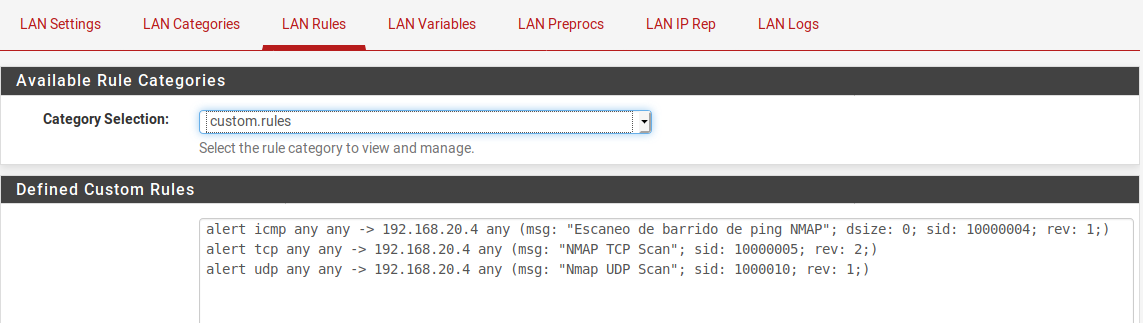
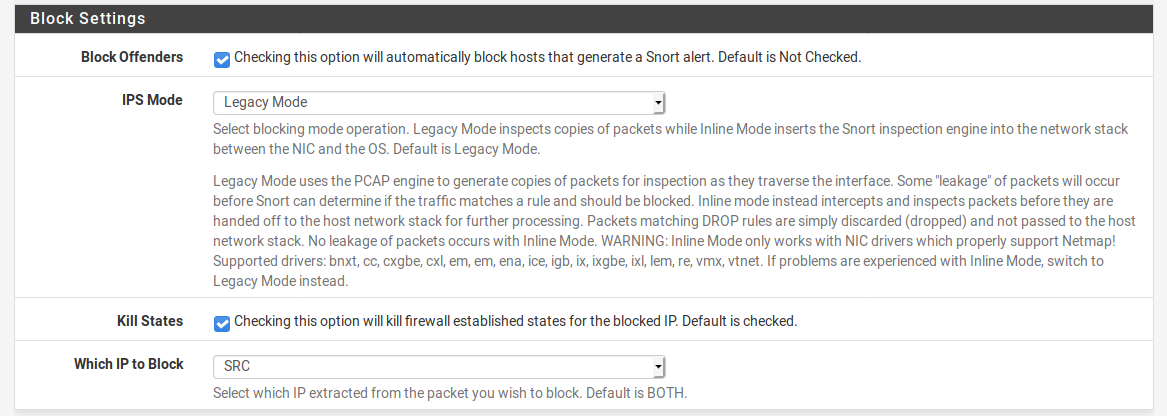
-
I'm going to assume that 192.168.20.x is your LAN subnet. The default setup for Snort is to put the LAN subnet (and all locally-attached networks) in the automatic Pass List. This is so local machines (in HOME_NET) are not blocked, and blocks get applied to external hosts (those in EXTERNAL_NET).
If you actually want to block internal LAN hosts, you will need to create a custom Pass List and assign it to the interface. However, I would advise against that as once a host is blocked, ALL traffic to and from that host through the firewall is blocked. You normally only want that for external hosts out on the Internet, and not your local internal hosts. You want them blocked from talking to the bad guy, but not necessarily blocked from talking to other hosts in your LAN such as the DNS server, mail server, etc.
Also, hopefully you know that when it comes to hosts doing things to each other in a switched network (i.e., when both devices are in the same subnet), that the firewall will not even see the traffic.
-
@bmeeks I didn't quite understand why snort IP blocking doesn't work, it's a test lab and I'm playing with the LAN
-
@cris9731 said in Error in legacy mode of snort service.:
@bmeeks I didn't quite understand why snort IP blocking doesn't work, it's a test lab and I'm playing with the LAN
Go to the INTERFACE SETTINGS tab for your LAN interface in Snort. Scroll down and click on the View List button beside the Pass List drop-down selector. The IP addresses and networks you see in that list will not be blocked by Snort. These are the automatically-added addresses in a default configuration. And 90% or more of the time, you want your Pass List to look like this. In the rare instance you don't, and you want to actually block LAN hosts, then you will need to create a custom list under the PASS LIST tab, and then come back and assign the custom list to the interface, save the change, and restart Snort.
Just be aware that if you monkey with the Pass List and are not keenly aware of the potential consequences of your modificatoins, you can lock yourself out of the firewall from a LAN workstation.
-
@bmeeks Thanks, now I understand everything, I have made several tests, I want to block the IP inside my Lan 192.168.20.3, but this appears in the default list of "PASS LIST", I have played with the list but what I want is to suppress that it takes me all the addresses 192.168.20.0/24 to be able to check the snort blocking. Is there any way to modify this list?
Sorry for my lack of experience in this but I am doing this to learn.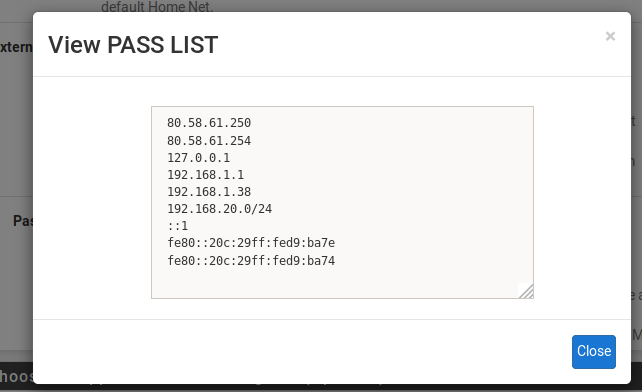
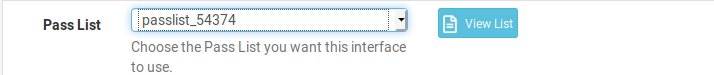

what is marked here was a test to see how it worked.
-
@cris9731 said in Error in legacy mode of snort service.:
@bmeeks Thanks, now I understand everything, I have made several tests, I want to block the IP inside my Lan 192.168.20.3, but this appears in the default list of "PASS LIST", I have played with the list but what I want is to suppress that it takes me all the addresses 192.168.20.0/24 to be able to check the snort blocking. Is there any way to modify this list?
Sorry for my lack of experience in this but I am doing this to learn.


what is marked here was a test to see how it worked.
When you create a custom Pass List, there are some checkboxes on that page that are checked by default. These add all locally attached networks, the DNS server(s), the default gateway, WAN IP, and any VPN addresses. For your needs, you will want to uncheck the Local Addresses checkbox. For example, in your screenshot I am going to assume the 192.168.10.0/24 and 192.168.20.0/24 networks are locally-attached (meaning defined on a firewall interface). They are getting automatically put there because that checkbox is enabled. Uncheck the box for Local Addresses, and they will not be in the list after you save the change.
You have the option at the bottom of the Pass List edit page to add individual IP addresses, aliases or subnets back to the Pass List, if necessary.
Anytime you make changes to the Pass List, you will need to restart Snort on the interface because the Pass List is only read once during daemon startup. It is NOT dynamic.
-
@bmeeks I have restructured my network, and I got the snort to block an external IP to my LAN when I do a Nmap scan, so far so good, but when I pull the scan it tells me that I have port 80 and 53 open, on port 80 it shows me the following:

This is a normal behaviour in Pfsense? or is it that I have not focused well the network structure?
-
By default, pfSense has zero open ports on the WAN. So anything showing would be one of these two things: (1) you put a rule on the WAN (or a Floating Rule) that allows the access; or (2) some device in front of pfSense that is between it and the external Internet scanner responded to the scan and that device has open ports.
Of course those two ports will likely show open if you scan from the LAN side into the pfSense LAN interface. 53 is DNS, and 80 is, of course, HTTP.
-
@bmeeks Thank you very much for your attention and help, thanks to this I have been able to carry out my laboratory perfectly. Thank you very much !!!!