My Rules to block certain IPs from the internet is not working
-
@derekmarch You put rules on the interface that the traffic ENTERS, not exits. Put your rules on LAN, not WAN. Also, each interface has an implicit block rule that you can imagine being at the bottom of the list, so you don't need to put a specific block rule. If you don't allow it explicitly, it will be blocked.
-
@kom Sorry I should have labeled those screen shots better. The top 2 screen shots are a WAN rule and the next 2 screen shots are a LAN rule. This is what the walkthrough I followed told me to do.
Am I supposed to setup both of these things up as LAN rules?
The last LAN rule (not in the screen shot) is the allow everything rule.
If you know what changes I need to make are you able to tell me specifically by chance? I don't have a ton of experience working without help in the pfsense.
Thanks
-
@derekmarch Ah I didn't notice with that big wall of white.
Get rid of that rule on WAN. It's not needed. One thing with firewall rules that trips up new people is that a new rule or modified rule will not affect established traffic. For the rule to take effect, you must clear the states of the clients that the rule will apply to.
For your LAN rules, you have told it to block access from LAN to destination Block_from_Internet. That isn't valid. You want to block from SOURCE, not destination. The source is your LAN clients, destination would be where they're trying to go. Change your rule so that the Source is Block_from_Internet and Destination is Any. Then go to Diagnostics - States and clear the states of those two LAN client.
-
@kom I have tried clearing the states a number of times during my hours of troubleshooting. But I will keep that in mind. After my current meeting I'll give this rule change a try. Thanks for the suggestion
-
@derekmarch Take the time to quickly read up on the two links I gave you. It's hard to play the game when you don't know the rules.
-
Also what else did you do to that rule, you have the advanced gear showing.. But your not showing your advanced settings...
-
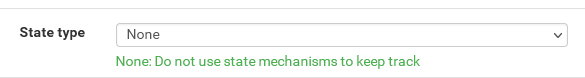
The only thing I did in advanced as part of my troubleshooting was set state from Keep to None.
Should i revert that back to Keep?
-
@kom Thank you for those links, I will give them a read.
-
yeah your going to want to keep states ;)
The way your rule was written it would never triggered as you can see by the 0/0 - your destination was what you want your source to be if you want to block those 2 IPs from going to the internet.
-
-
BTW something is missing from this puzzle - because with the way those rules are. Nothing would be able to go to the internet.. Since you have no allow other than going to the gui of pfsense.
Do you have rules in floating or something?
-
@johnpoz Sorry for the confusion with my screen shots, there are plenty more rules below my screen shot, i just cut it off at the relevant line I had added for this purpose.
-
OK,
I disabled the WAN rule and flipped the LAN rule I had. and it now appears my laptop has no access to the internet.
It appears my laptop can still access other items on the LAN.
How do I set this up so that the IPs in this alias can't access the WAN or the LAN?
Thanks for all the help so far
-
@derekmarch ah - if you look close you can see the difference in color that would be the next row.. But yeah its always best to show all rules on an interface when troubleshooting..
It appears my laptop can still access other items on the LAN.
Well yeah.. pfsense has nothing to do with devices on the same network talking to each other.
If you don't want them accessing other stuff - move them to their own vlan would be the easy simple best solution.. Filtering devices on the same network from talking to each other would have to be done via your switch infrastructure, ie like a private vlan setup. Or via host firewalls. Pfsense has nothing to do with devices talking amongst themselves on a network - only to get off said network is where pfsense comes into play routing and firewalling.
-
@johnpoz I will be sure to keep that in mind next time I need help.
I guess i'll have to research what other options I might have if I want to block random devices from my LAN.
Thanks again, everyone, for all the help
-
See my edit to your question about devices on the same network.
Vlans are very handing for keeping device X from talking to Y - because you just put them in different vlans. Grouping like devices together that you want to talk to each other, etc and other devices that you don't want talking to other devices in their own vlan - but they would be able to talk amongst them selves on that vlan.
To keep devices on the same network from talking to each other - wired this is normally called a private vlan. In wireless its called client or ap isolation.
-
Hm, I do have a managed switch that I'll be configuring soon. I guess I'll setup a rule at that time to move this alias to its own VLAN.
Thanks
-
Yeah any smart switch should be able to do vlans - not all entry level smart switches would support stuff like private vlans though..