Right config with HMA openVpn config
-
@viragomann
Well, in the tutorial, it says to put this option as HMA use the replace gateway .
I have create a rule, in Lan which saysSRC : 1 IP address
port all
Dest ALL
and in advanced, I changed the GW , to the GW created by VPN.
If I reboot the PFsense, it works for ping, then .. if I do anything else, everythins stops working ( including ping ) -
@smalldragoon
Yeah, route-nopull is the correct setting to avoid get pushed the default route and do policy routing instead.Consider that the policy routing rule does not allow any internal traffic from the source IP, cause it directs any packet to the VPN gateway. This also applies for DNS.
Hence you have either use a public DNS on the concerned device or maybe redirect DNS on pfSense to a public server and direct this one over the VPN (both helps to avoide DNS leaking), or you add an additional firewall rule above of the policy to allow internal access (without the gateway stated).
-
@viragomann
Well, maybe I'm missing something
I did this anyway, with the hidden IP being my LAN computer IP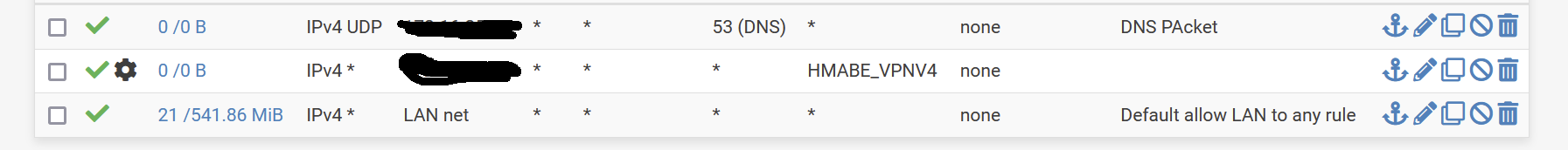
Resolution works ( as per the rules created using normal GW ) , but nothing else ....
-
@smalldragoon
Interestingly both rules don't show any traffic.
Could it be that there is another rule matching the traffic from the client before? Maybe a floating rule or one on an interface group which LAN is belonging to.To analyze I'd enable logging in the rule and add a proper description. So you can see in the firewall log, if the rules are applied.
-
@viragomann
Well, no groups of rules, my setup is pretty basic :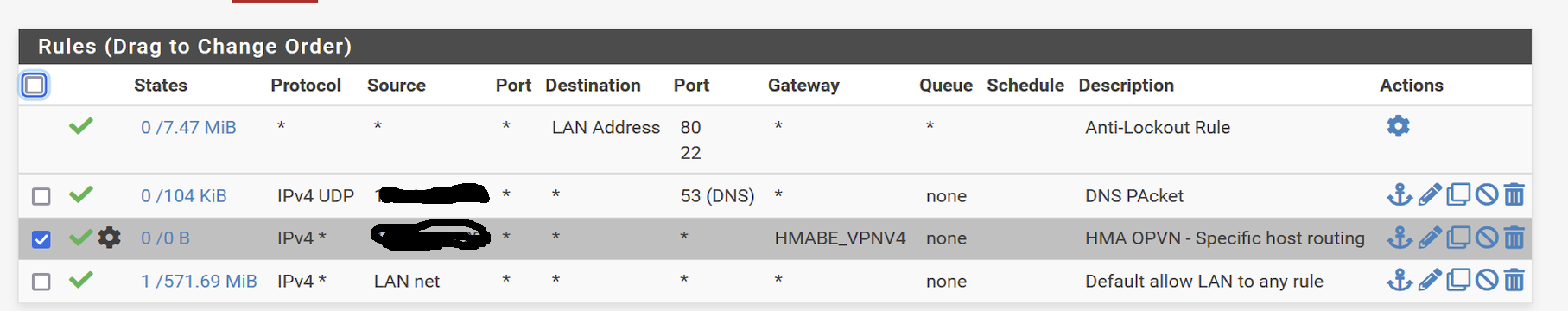
I have this setup for the HMA interface ?
-
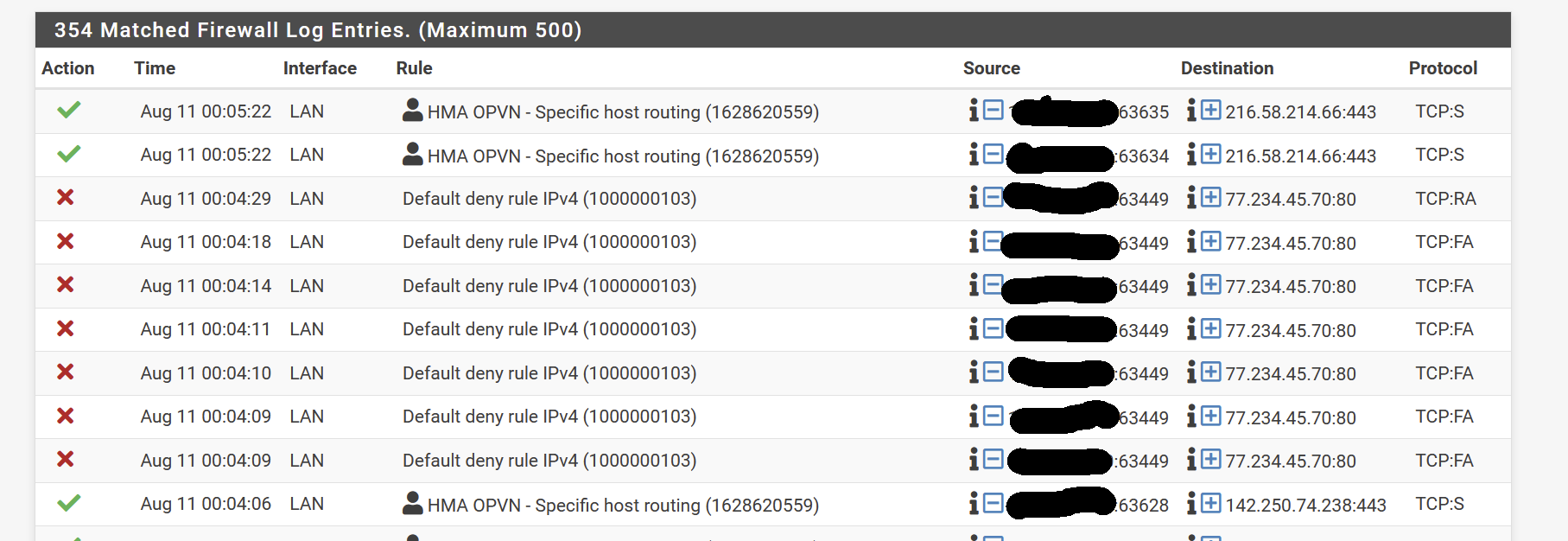
@viragomann seems that the rules a default rule is triggered ? I don't have one ...
-
@smalldragoon said in Right config with HMA openVpn config:
I have this setup for the HMA interface ?
This rule only allows incoming traffic on the VPN. You do not need any rule here for outgoing connections.
The same is true for the OpenVPN tab.No idea why you traffic doesn't flow. Could be due to wrong settings in the OpenVPN client.
The tutorials you quoted are very old. The shown Advanced settings are deprecated and shouldn't be use anymore. Most of them can be set in the GUI nowadays or are default values.
You shouldn't use the showed settings. Simply follow the specifications of the provider and set it in the GUI. Only set / change options which are mentioned in the guidelines. -
@smalldragoon
One thought came up: Did you add an outbound NAT rule for the VPN? -
@viragomann
Well no, was not mentionned in the Tutorial and I assume it is the HMA server wich is doing the NAT at the end ?
they say here to change to manual outbound NAT, AON but that's all :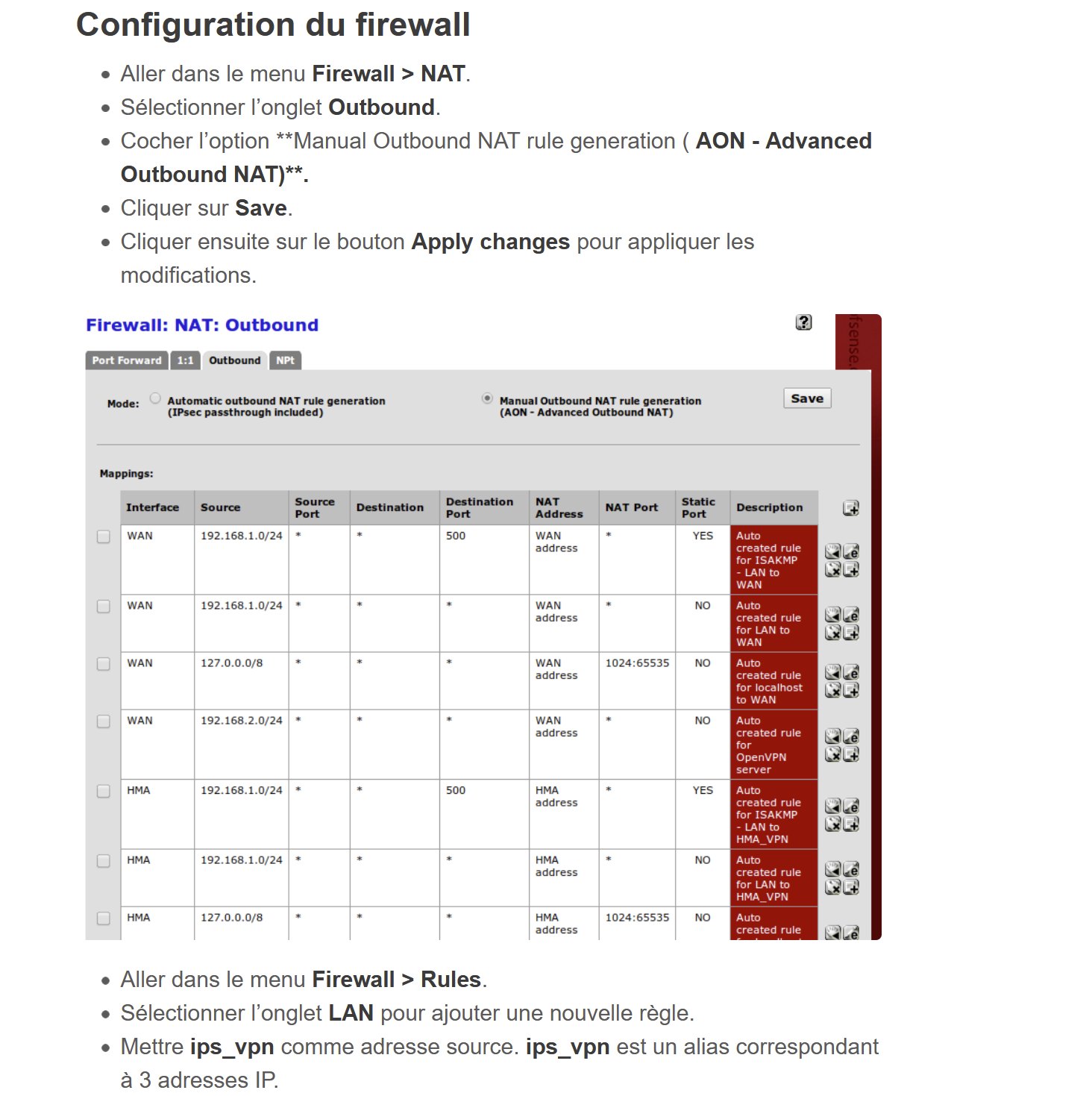
-
@smalldragoon said in Right config with HMA openVpn config:
was not mentionned in the Tutorial and I assume it is the HMA server wich is doing the NAT at the end ?
Might not be the best tutorials.
However, the screen shows two HMA rules.Anyway, it will not work without that.
But switch the Outbound NAT into the hybrid mode and save it.
Then add a rule:
interface: <your VPN interface>
Source: LAN, or only the IPs (alias) you need
dest.: any
translation: interface address -
@viragomann
switch to hybrid , done
Created as 1st rule :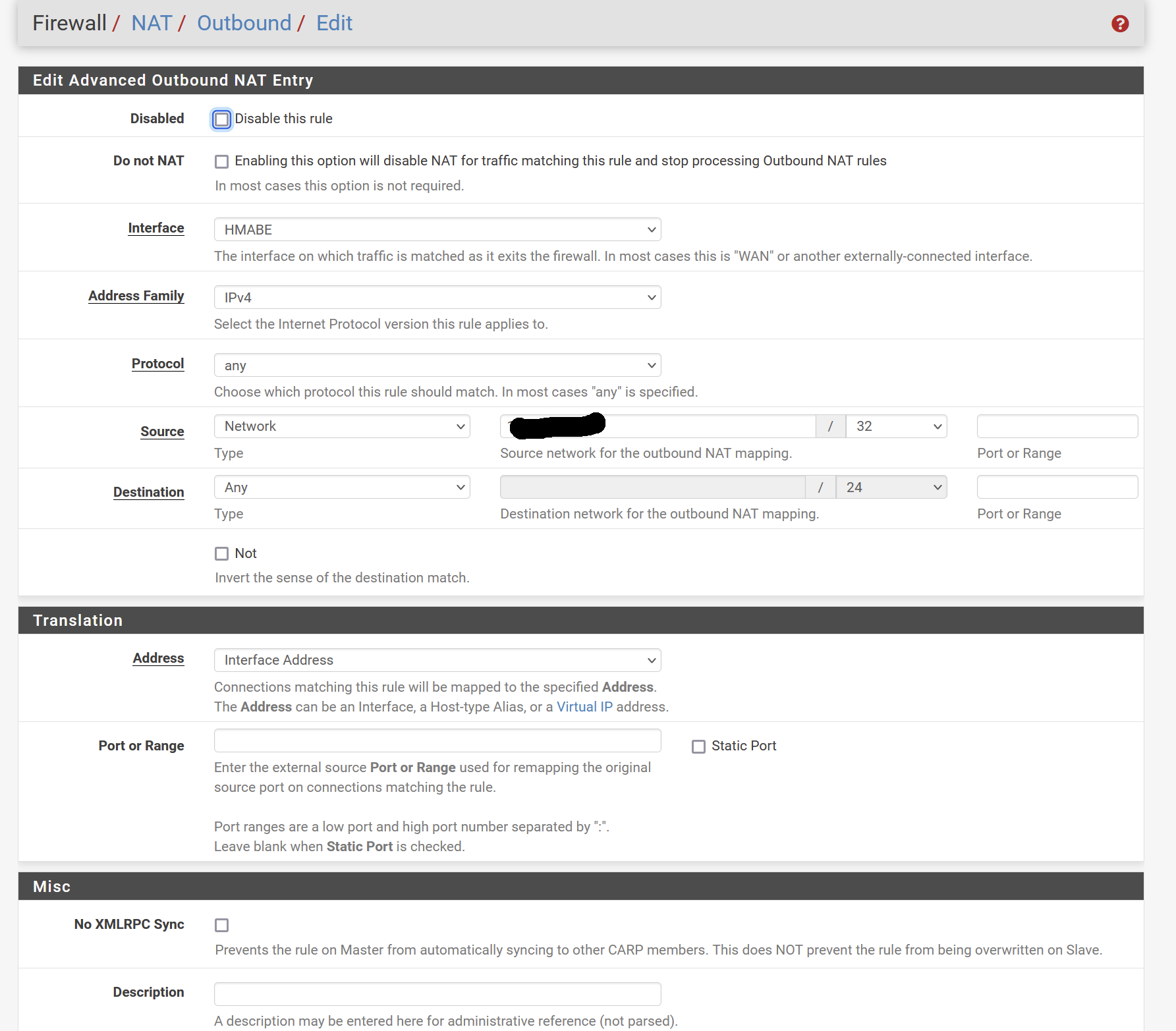
Where the hidden value is my LAN computer for tests
Still nothing :( -
@smalldragoon
Try a simple ping to a public IP like 8.8.8.8 on the client, while taking a packet capture on the VPN interface to see, what's going on. -
@viragomann
Hi, I rechecked evrything and followed one of your advice, to check VPN .. found that ( 2 first line , other to give conext ):Aug 13 14:51:30 openvpn 72184 Authenticate/Decrypt packet error: packet HMAC authentication failed Aug 13 14:51:21 openvpn 72184 Authenticate/Decrypt packet error: packet HMAC authentication failed Aug 13 14:51:18 openvpn 72184 MANAGEMENT: Client disconnected Aug 13 14:51:18 openvpn 72184 MANAGEMENT: CMD 'status 2' Aug 13 14:51:18 openvpn 72184 MANAGEMENT: CMD 'state 1' Aug 13 14:51:18 openvpn 72184 MANAGEMENT: Client connected from /var/etc/openvpn/client2/sock Aug 13 14:51:13 openvpn 72184 Initialization Sequence Completed Aug 13 14:51:13 openvpn 72184 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Aug 13 14:51:13 openvpn 72184 /usr/local/sbin/ovpn-linkup ovpnc2 1500 1624 100.120.41.81 255.255.255.0 init Aug 13 14:51:13 openvpn 72184 /sbin/ifconfig ovpnc2 inet6 -ifdisabled Aug 13 14:51:12 openvpn 72184 /sbin/ifconfig ovpnc2 inet6 2001:db8:123::2/64 mtu 1500 up Aug 13 14:51:12 openvpn 72184 /sbin/route add -net 100.120.41.0 100.120.41.1 255.255.255.0 Aug 13 14:51:12 openvpn 72184 /sbin/ifconfig ovpnc2 100.120.41.81 100.120.41.1 mtu 1500 netmask 255.255.255.0 up Aug 13 14:51:12 openvpn 72184 TUN/TAP device /dev/tun2 opened Aug 13 14:51:12 openvpn 72184 TUN/TAP device ovpnc2 exists previously, keep at program end Aug 13 14:51:12 openvpn 72184 Incoming Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication Aug 13 14:51:12 openvpn 72184 Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key Aug 13 14:51:12 openvpn 72184 Outgoing Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication Aug 13 14:51:12 openvpn 72184 Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key Aug 13 14:51:12 openvpn 72184 Using peer cipher 'AES-256-CBC' Aug 13 14:51:12 openvpn 72184 OPTIONS IMPORT: adjusting link_mtu to 1624 Aug 13 14:51:12 openvpn 72184 OPTIONS IMPORT: peer-id set Aug 13 14:51:12 openvpn 72184 OPTIONS IMPORT: route-related options modifiedsearched on google, seams related to TLS auth, which is not and must not be activated ... any insight ?
Thx -
@smalldragoon
Possibly something wrong in the client configuration.I already already advised to take the providers requirements for reference and set up all in the GUI instead obeying these age-old tutorials.
Since I whether know these nor your current configuration, I cannot contribute. -
@viragomann
Sorry, I though I would have said.
Provider is not advising really anything.
Ihave the .opvn files , that's all .
That's why I tried other sources -
@smalldragoon said in Right config with HMA openVpn config:
Ihave the .opvn files , that's all .
That may be all you need to configure the OpenVPN client accordingly.
If it uses TLS and there are certs inside, you have to extract them and import it in pfSense. -
@viragomann , first, thanks again for your help and support on this.
for all and benefit of the forum :Took me a long time to figure out , as there was several issues ,
I bypass all tests done going to outcome
1 - my hardware was not strong enough : changes where not applied properly all the time - > this is why I had non consistent behaviors ( I set manually the "Firewall Maximum Table Entries", so apparently no error, but all changes were not applied)
Solution to this 1st point : ordered a new box ( that's why it took some time to get it from china ... )2 - I had duplicate ranges in my IP's ( the one assigned by VPN was another one as well on another link of my FW )
Having solved these 2, I have the VPN connection created, stable with a GW defined.
In the meantime, I have in the new box a wifi connection, that I 'm gonna use as fail-over solution. I will be able to make tests unlink from the VPN, and see if now I encounter the same problemsThanks