use pfsense to run wireguard client (mullvad)
-
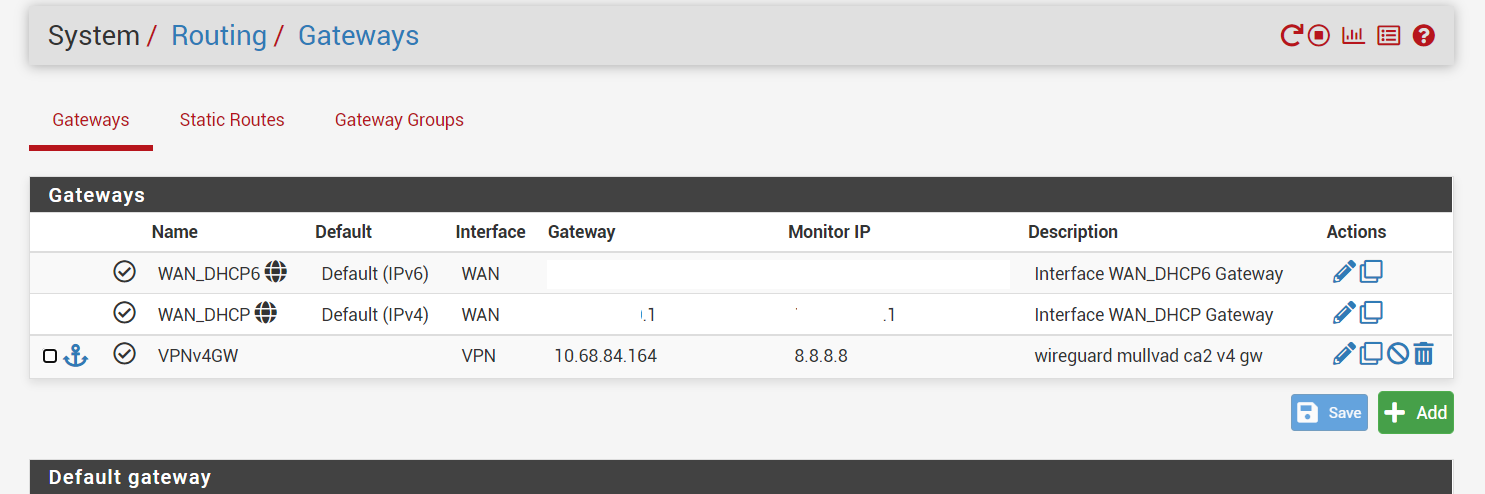
@gabacho4 also, did you set a default IPv4 and IPv6 gateway or did you leave it at automatic? If automatic, you need to set one. In your case I’d set the default WAN (IPv4 and IPv6) as them.
-
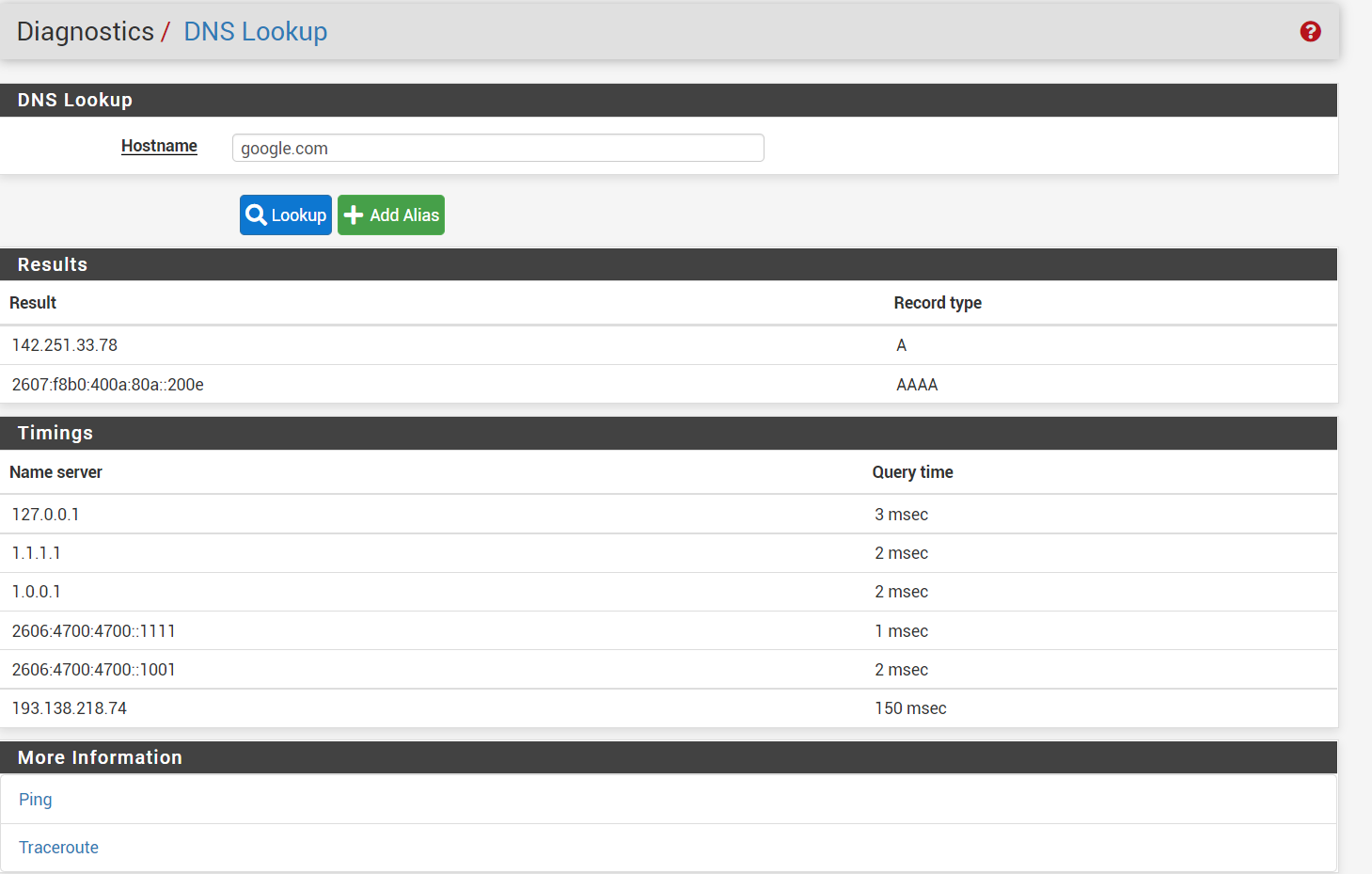
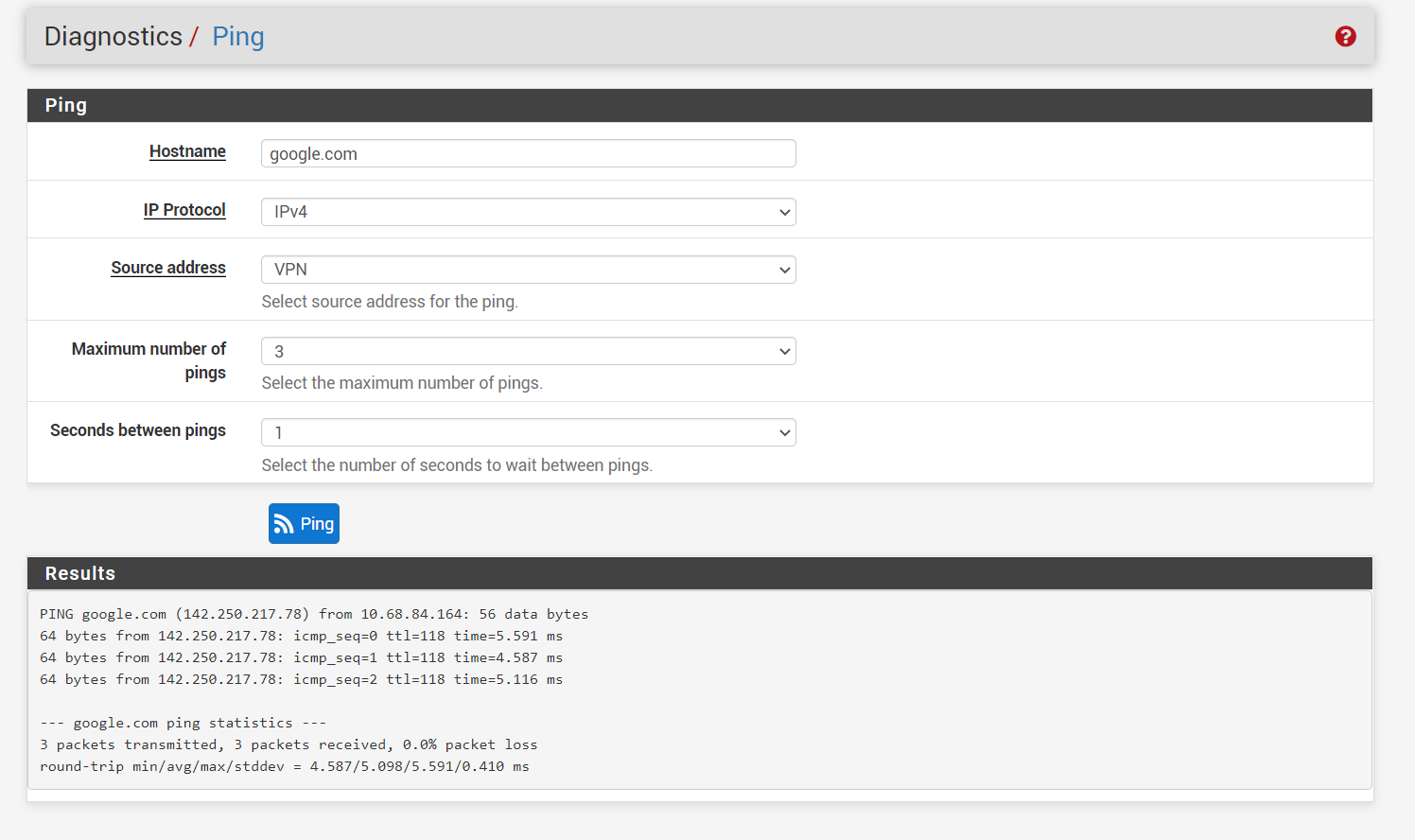
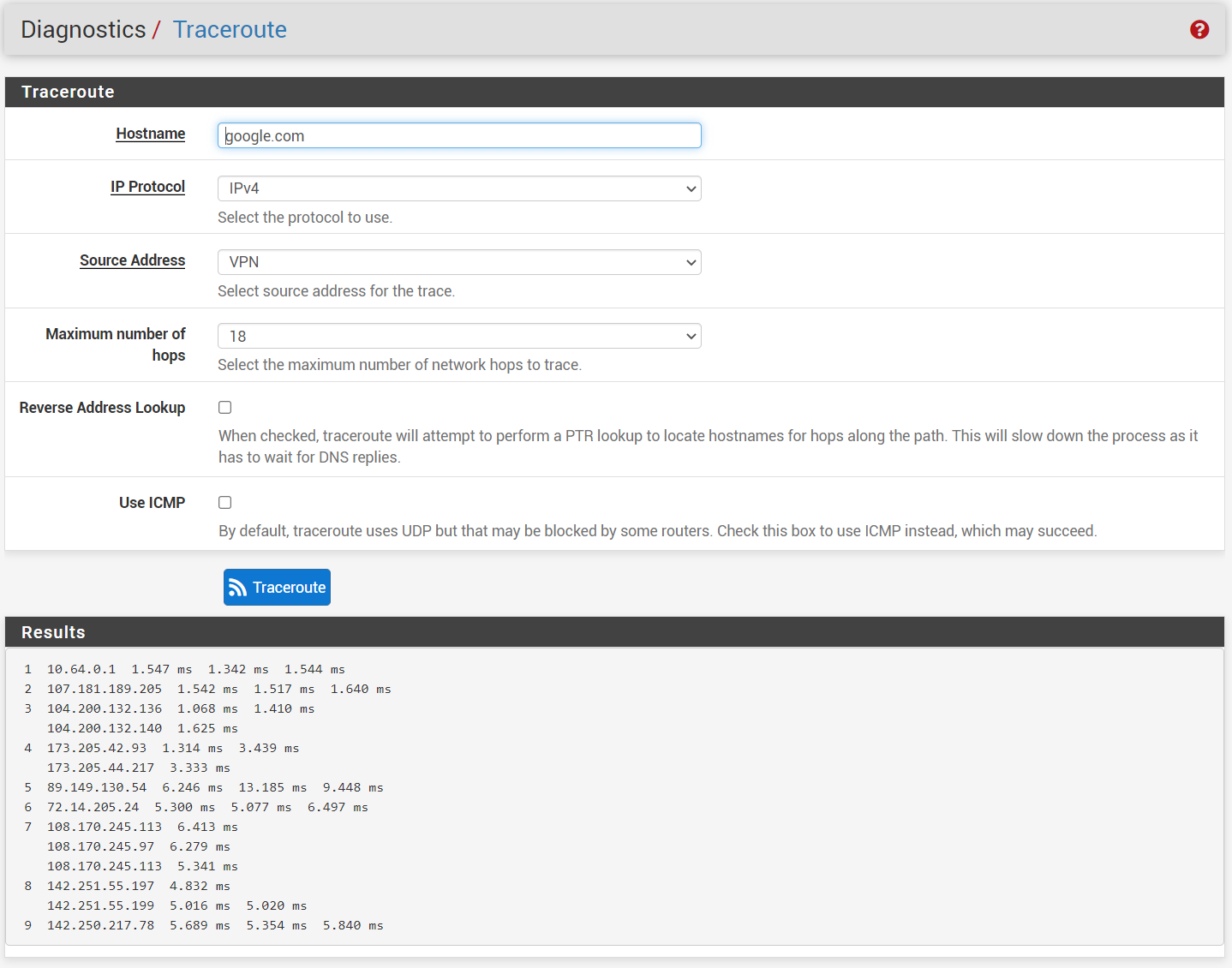
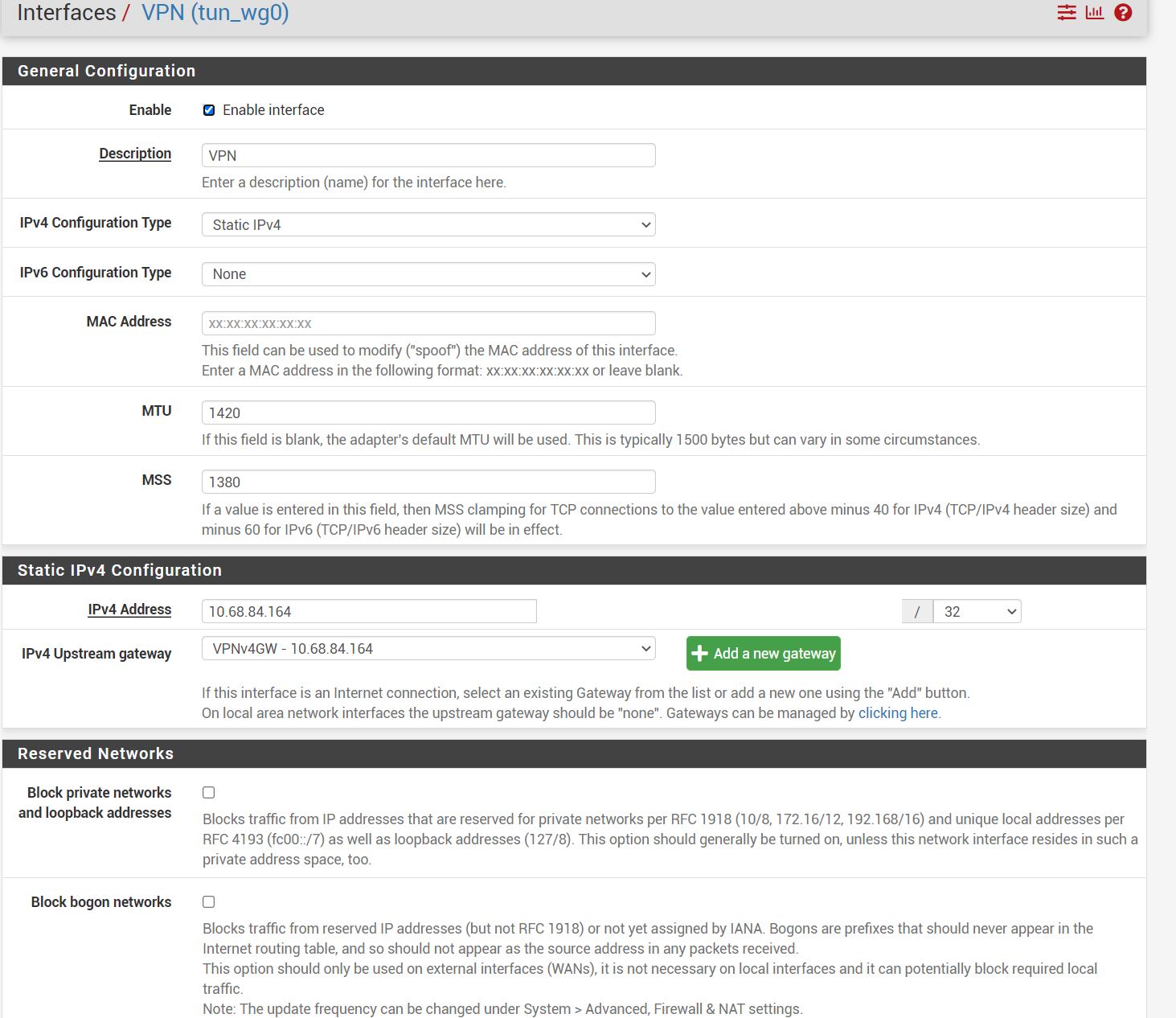
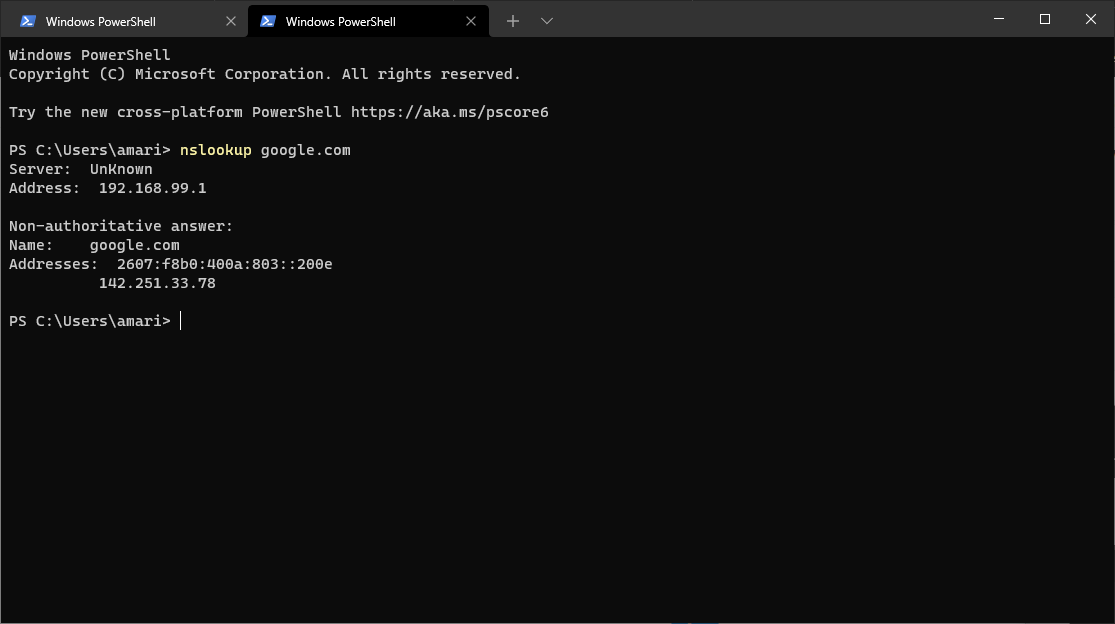
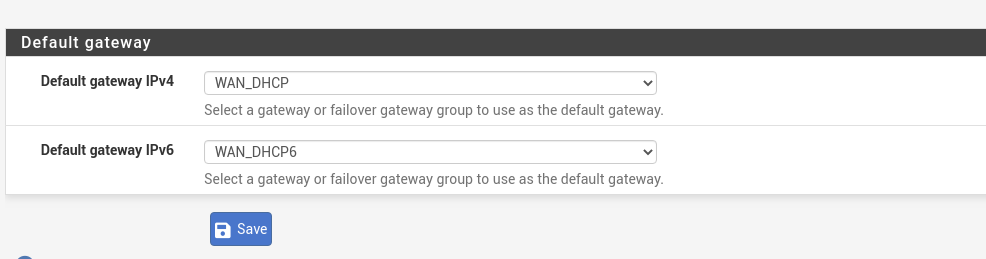
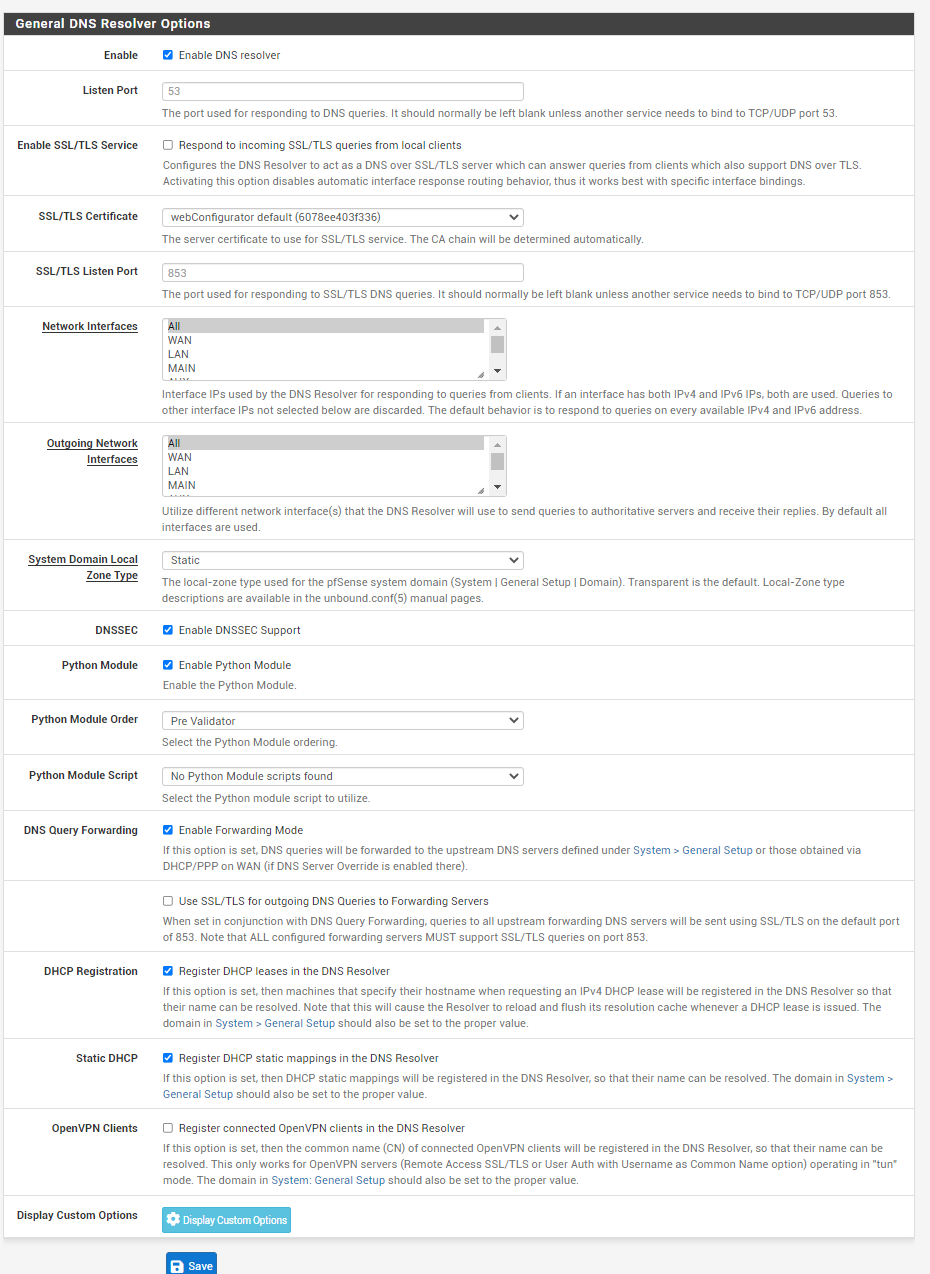
@gabacho4 yes I did set default gateway (attached). ping and nslookup results below as well.
I also tried to redo all the steps based on above screenshots just in case i missed a step. I also reinstalled wireguard (unchecked keep config) just to make sure there was no issue there.
ping 8.8.8.8 from pc (timeout)
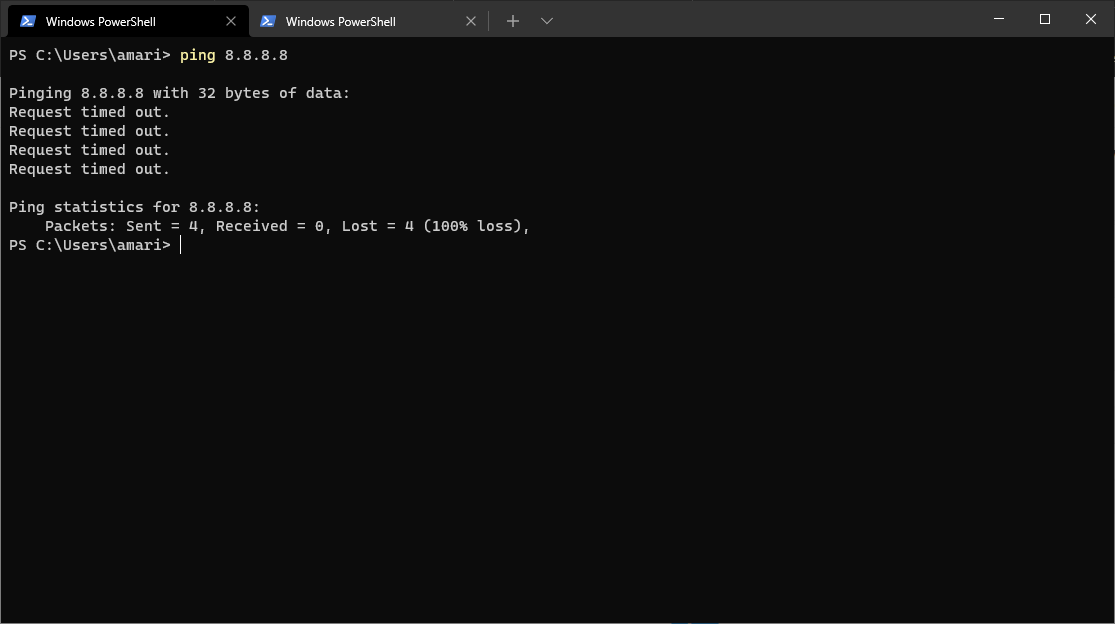
nslookup from pc
default gateway
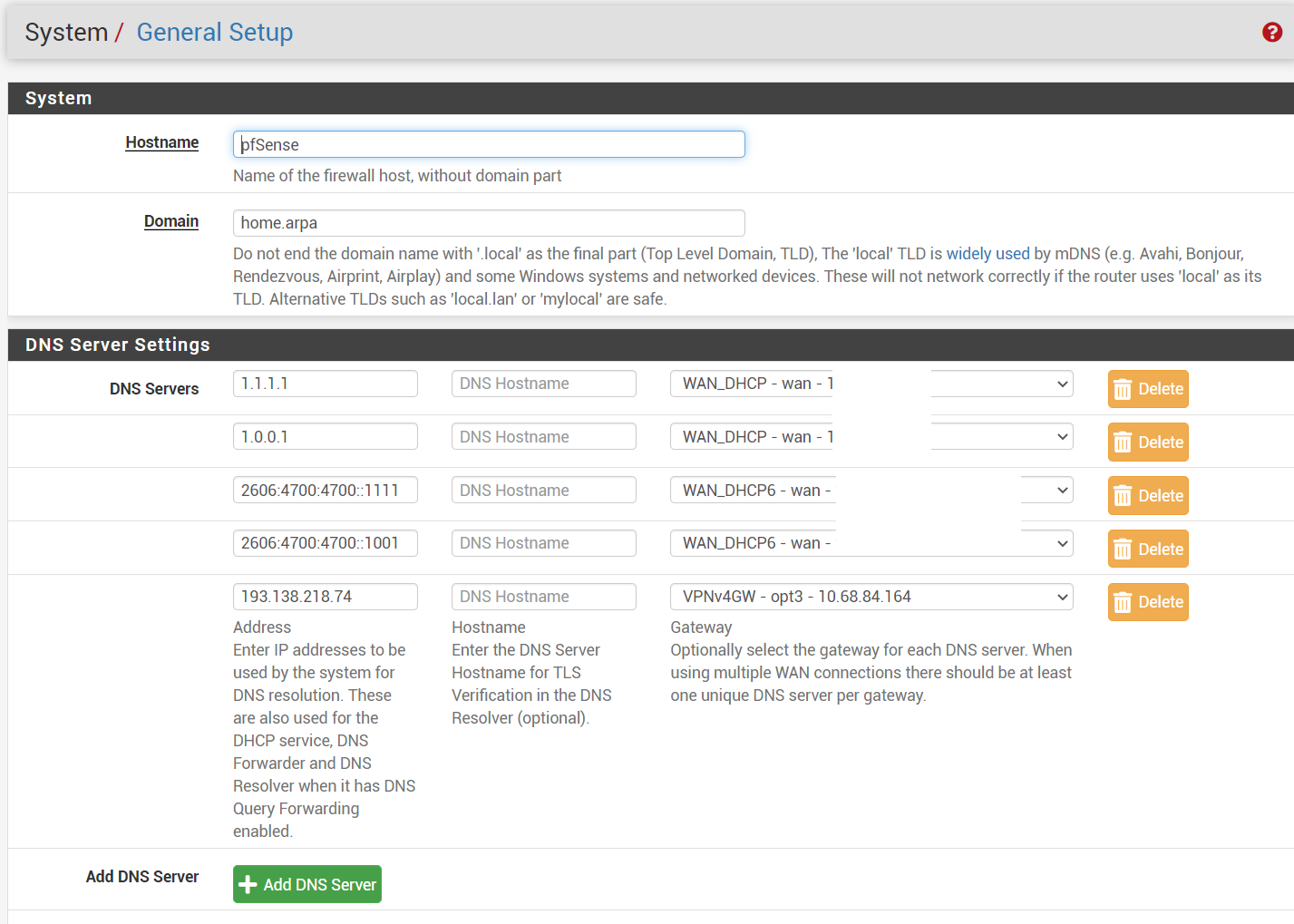
dns settings
-
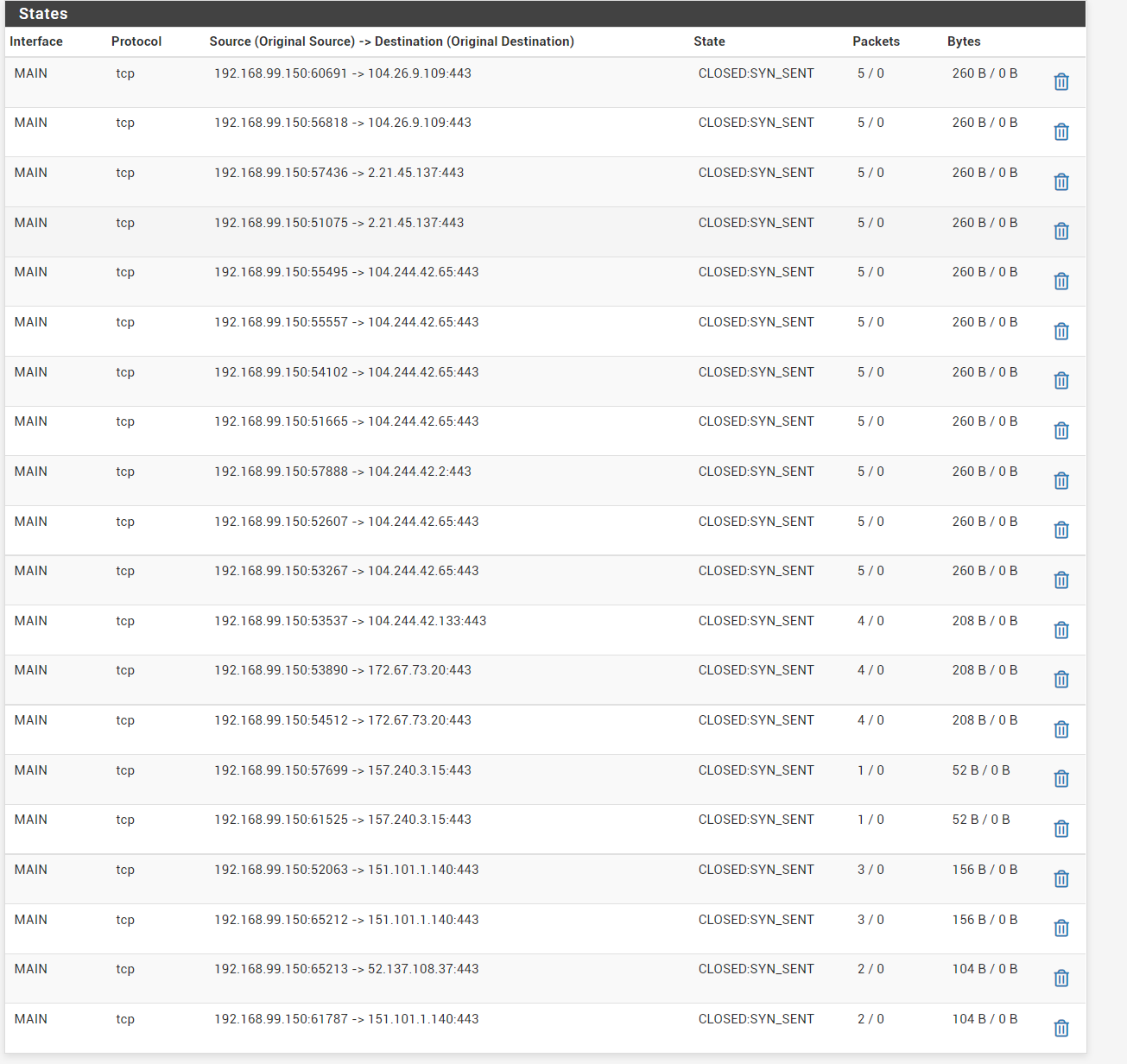
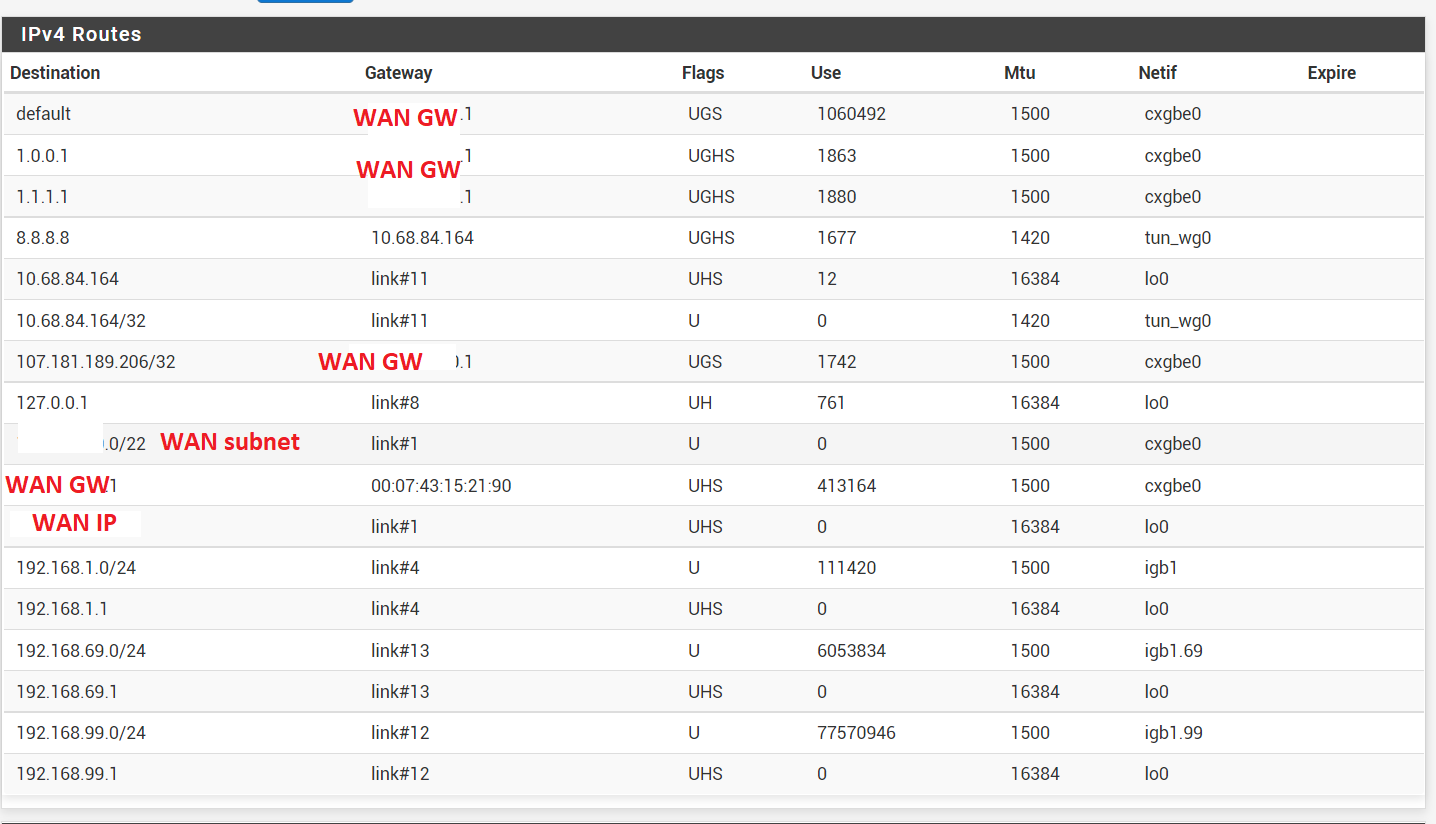
@gabacho4 i also noticed that dns seems to be working for whatever reason in the state table... (and its using wan ip address, not vpn gw address)
I do have ports 443 and 80 forwared on the wan interface to my lan interface reverse proxy on a raspi....
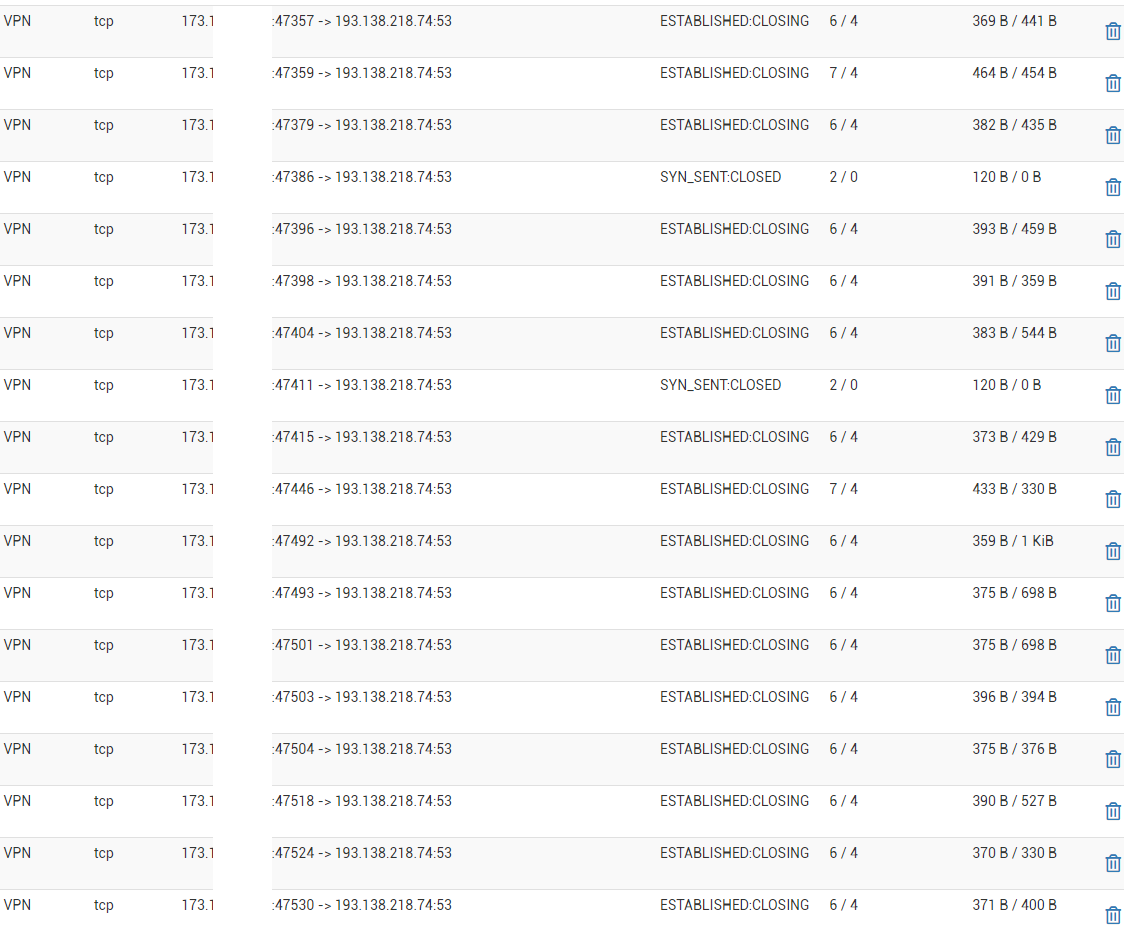
-
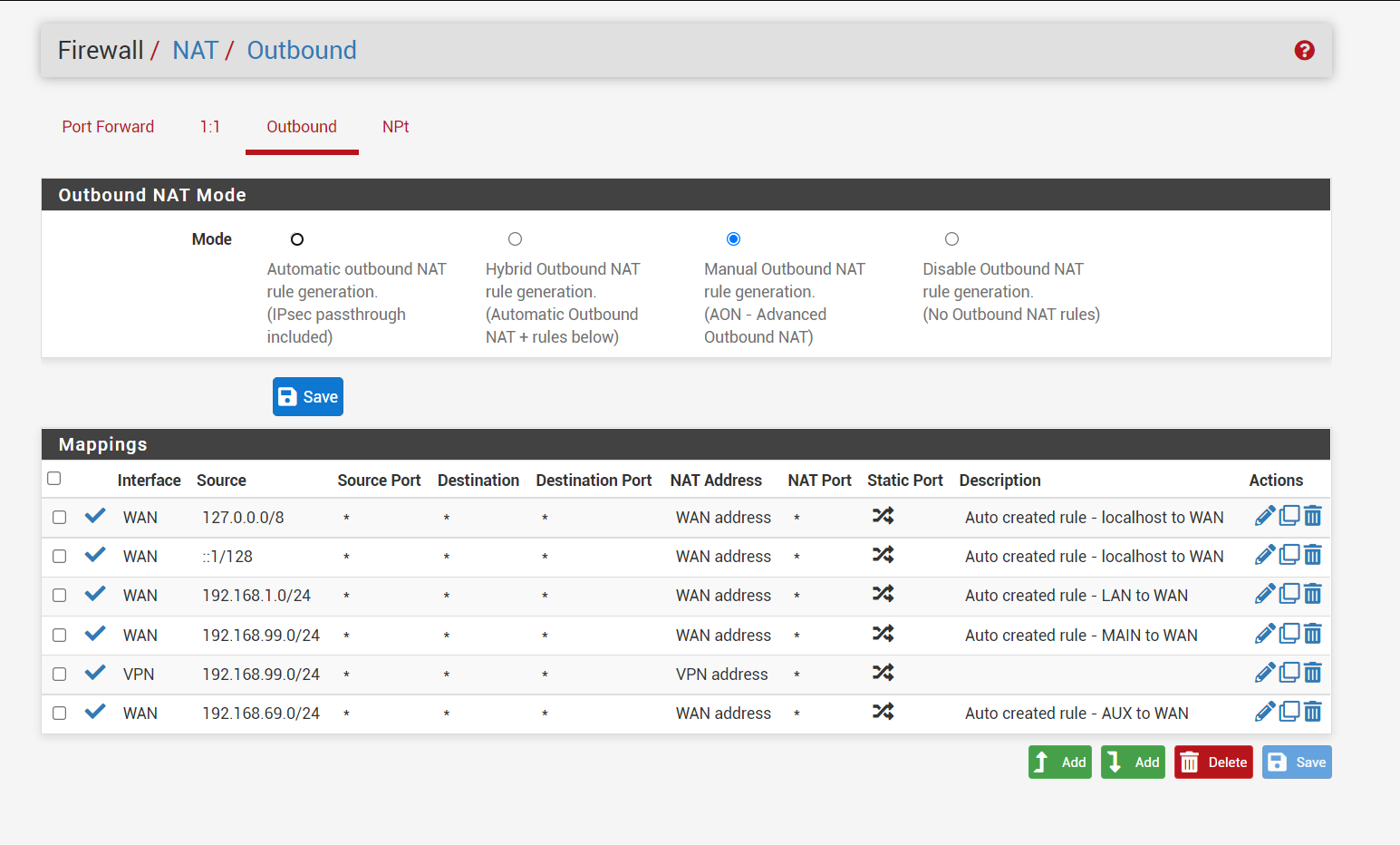
@gabacho4 i changed outgoing interface to vpn and changed settngs in general and dns still seems to work (using vpn interface)
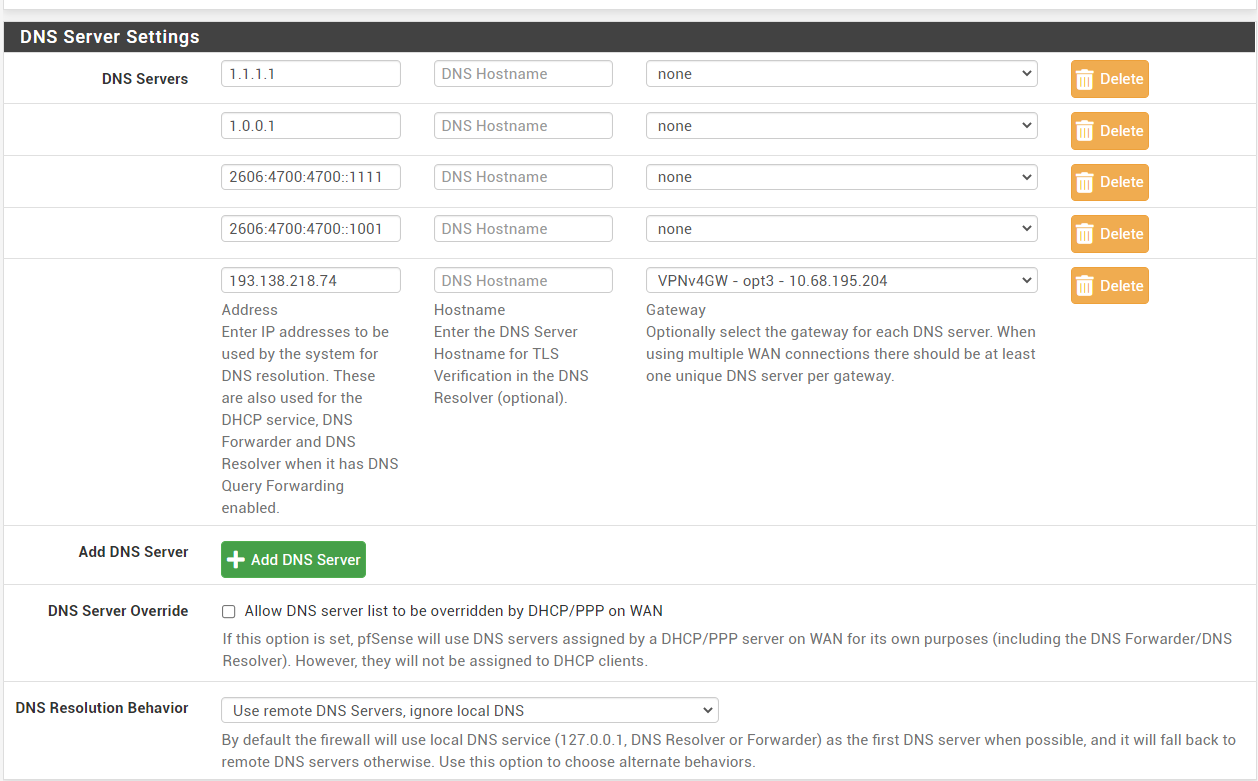
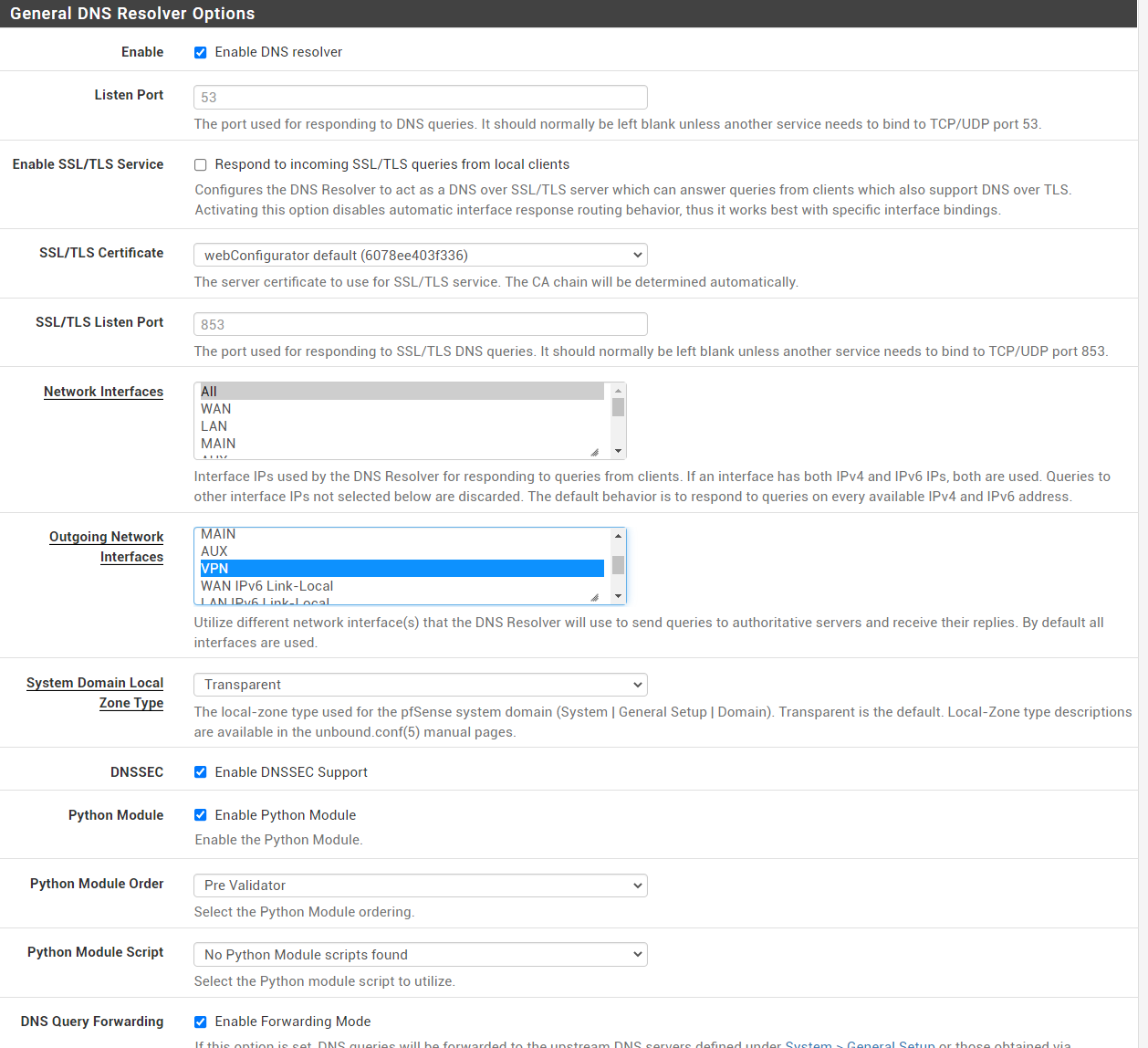
-
@strangegopher you’ve got too many other variables in your setup right now imho. I’d set up a basic router configuration, then get WireGuard working, the add your other configs one at a time so that you can identify when things break. I think you have a problem with your resolver/dns settings. Pfsense can clearly see the world and communicate with it. But your devices, which get their dns resolution from pfsense, seem to have issues. One way to rest this would be to manually specify dns in your computer using maybe 1.1.1.1 and see if your computer magically has internet service through the vpn connection. I do not have a dns address specified for the VPN gateway in the general tab in settings. I just set 8.8.8.8 and 8.8.4.4 and have forwarding in dns resolver turned on. My understanding is that Mullvad intercepts dns requests over a vpn connection and inserts theirs so you don’t have to worry about leaking.
-
@gabacho4 just did a full reset and setup basic config (backed it up).tried wireguard again. exact same issue. restored basic backup i did.
basic config took me 30 mins to get going. i just set password, wan and lan interfaces/ip/dhcp, add 1.1.1.1 and 1.0.0.1 dns in general and set to use remote dns ignore local dns, make vlans, set vlan interface, set vlan dhcp, set static dhcp, dns overrides, dns set to “forwarding mode”, port forward wan ports 443/80 to lan raspi and finally ddns to cloudflare.
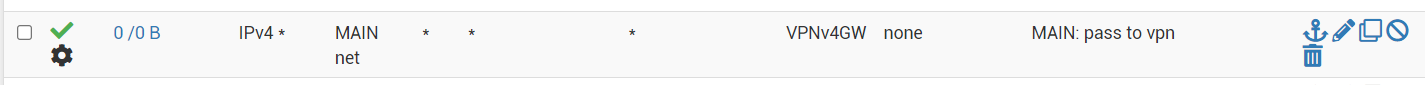
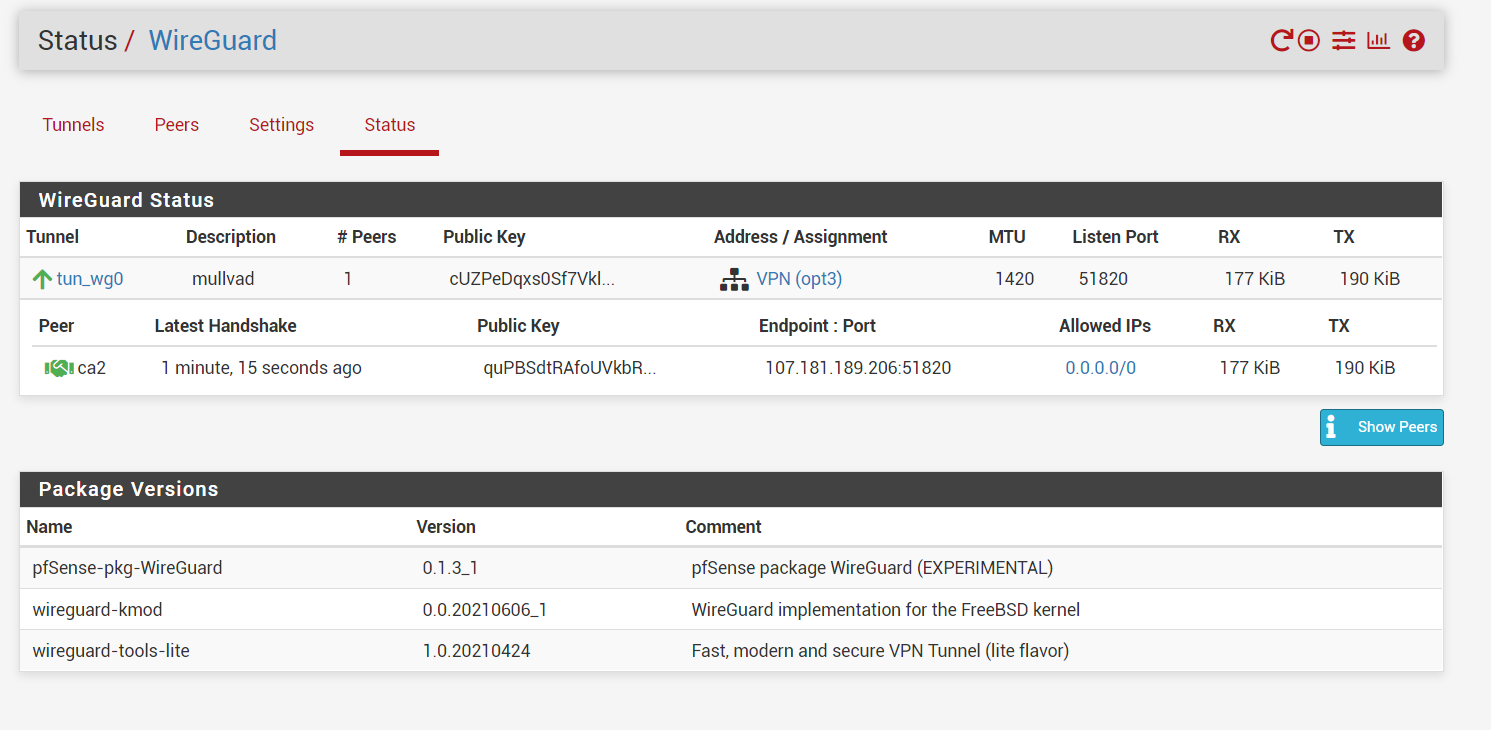
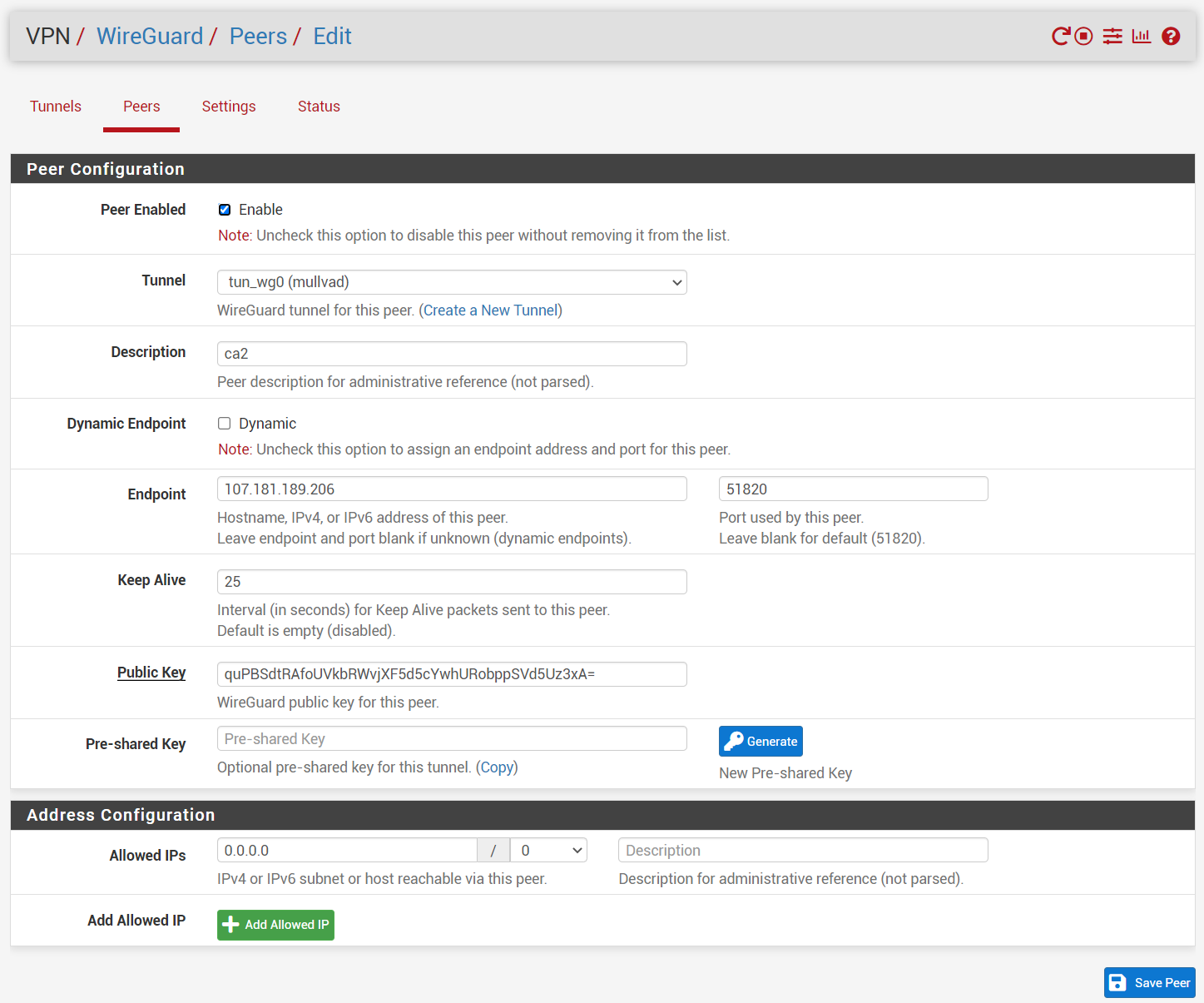
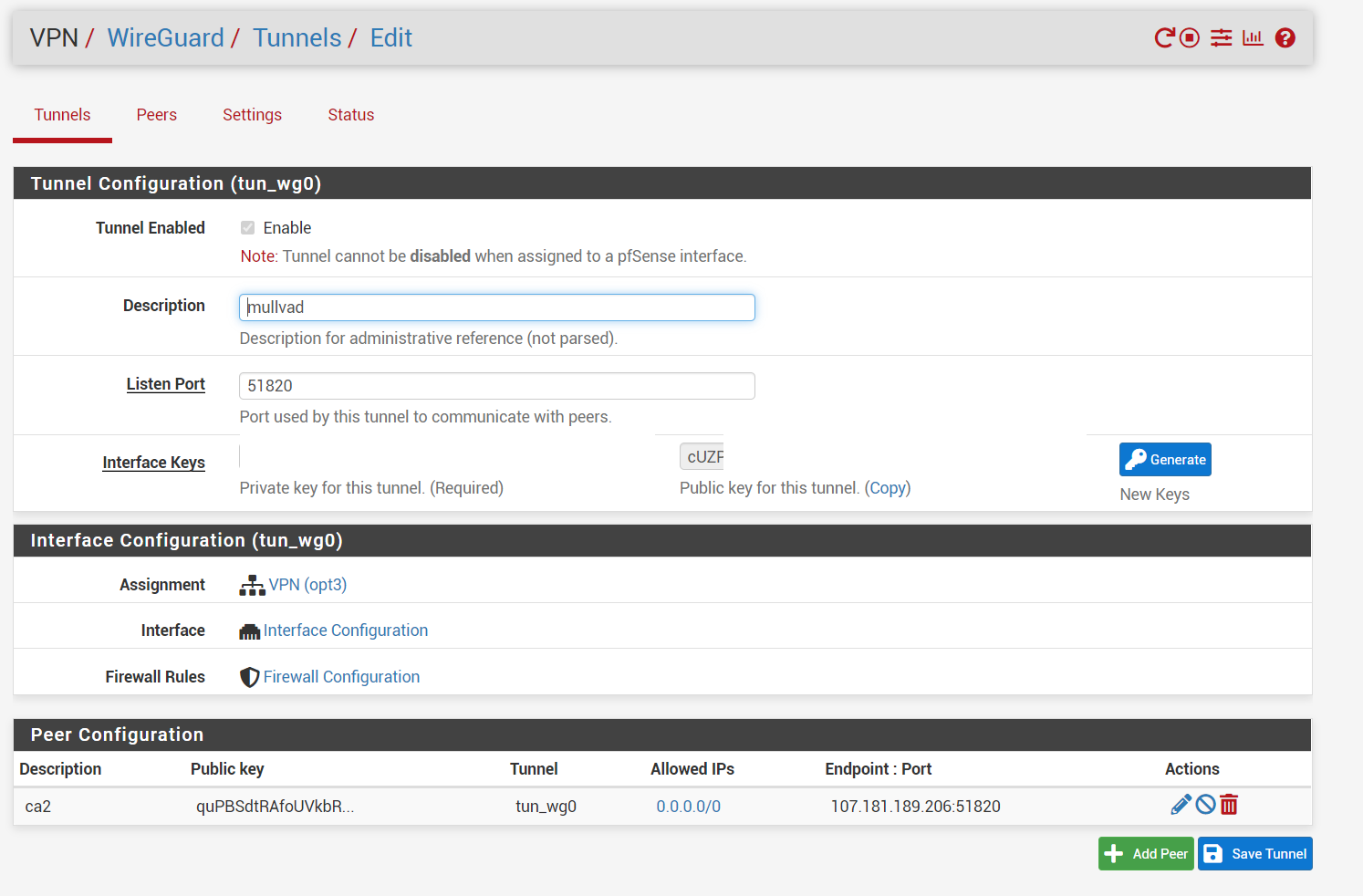
for wireguard i first made a tunnel, used generated key to get mulvad to assign me a ip, added peer, checked successful handshake, make wireguard interface, make gateway for wireguard interface, add NAT entry with wireguard interface just created with my local network subnet, and finally changed interface rule to allow all traffic to use the newly created gateway. i also added allow any to any rules as u suggested for wireguard and vpn tabs.
that’s it.
-
@strangegopher this is really perplexing. I am using Mullvad as we speak and have no issues. My setup is everything you have with exception of the port forwarding. Can you try to disable that really quickly to see if it is causing the issue? I don't remember seeing anything else "custom" that you have set up but would you mind clarifying if there is indeed anything outside of the basic setup that you have or are using? Did you ever set manually set the DNS for your computer to something else other than your pfsense box? Again, maybe using 8.8.8.8 or something like that. Leave the LAN firewall rule as you have it for the Policy Based Routing via the VPN. Manually set the DNS and let's see if you have connectivity. Other than that, I'm at a loss at this point.
-
just to update @gabacho4 and I did a remote desktop session and we were not able to resolve this issue. I am moving on from wireguard for now.
-
i had an issue very similar when i first attempted to use wireguard. i found the key was copy and pasted incorrectly. i REGENERATED a new key and paste the entire key and it started to work
i guess i don't understand why you are forwarding to 1.1.1.1 and you are also using a piehole? -confused look! have you tried just using the unbound resolver out of the box configuration?
-
@bcruze pfsense forwarded 1.1.1.1 by itself. i tired regeneration, no luck.
edit: no pihole... I think it forwarded 1.1.1.1 because I have forward dns servers checked.
-
This post is deleted!