Can't ping anything on the internet through LAN
-
Hello there,
I'm guessing someone could help me there. I'm front of a annoying problem. I'll explain you my situation.I have two PPPoE WANs:
WAN_FTTH_1
WAN_FTTH_2
Both of us are setting up with a Load Balancer and a Fail Over. I made a gateway group to permute to the more stable one.Then, I have 3 LANs:
LAN_MGMT(pfsense is in that LAN):192.168.50.x - DNS: 192.168.50.52.
LAN_ADMIN - 192.168.40.x
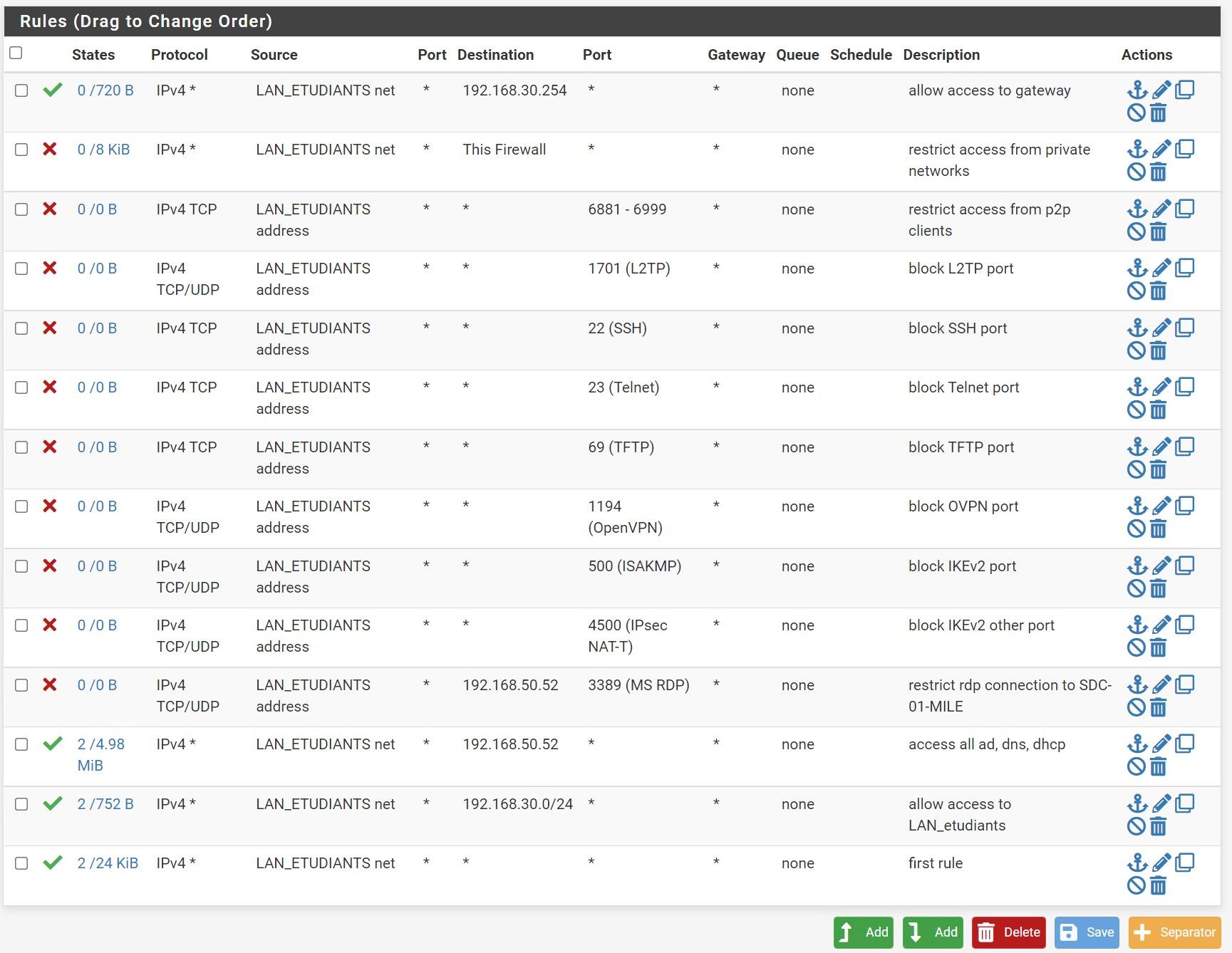
LAN_ETU - 192.168.30.xI need to set up some rules in the firewall for the LAN_ETU. I need to prevent them from accessing the other LANs. The only thing they can do is to access internet, and the whole LAN_ETU addresses. Which now, I probably messed up something. After days of research, and fails, I can't let this LAN accessing internet. The problem is 100% from the firewall rules but don't know which rule to create in order to let the whole LAN accessing internet. I allowed accessing 192.168.50.52 which is the DNS server.
If anyone has any ideas to help me resolving this issue. I'm glad to hear your help.
Here is a screenshot of my firewall conf. Note that if I make a rule with no restrictions it works. The other LANs are accessing internet too.
-
@louisleg The rules you present will not allow LAN_ETUDIANTS access to Internet.
The rule From LAN_ETUDIANTS net to WAN_FTTH_1 only allows the users on LAN_ETUDIANTS to access the IP of WAN_FTTH_1... I don't think that's what you want.
You can fix the problem in one of two ways:My preference: Create an alias called PRIVATE_IP, and put the networks 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16 in it. Next, insert 2 rules at the bottom:
From LAN_ETUDIANTS net to PRIVATE_IP - block
From LAN_ETUDIANTS net to Any - allow
This will allow access to All Internet, but prevent access to everything internal.
If you need to allow access to other internal resources, you need to place rules above the 2 rules.The second way to make this work is similar, but instead of using aliases
You would put block rules to each of the other LANs. These 3 rules need to go at the bottom:
From LAN_ETUDIANTS net to LAN_ADMIN net - block
From LAN_ETUDIANTS net to LAN_MGMT net - block
From LAN_ETUDIANTS net to Any - allow -
As mentioned already about your top rules to FTTH don't allow access to internet.
Also the bottom rules were your blocking would never be evaluated if your top rules did allow access to internet.
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated. So you need to make sure your block rules are above open allow rules (like internet access)..
Also if your wanting to block access to access to firewall IPs, ie your mgmt rules - the built in alias "this firewall" comes in handy because it includes all pfsense interface IPs.
Also Your allow rule for ad,dns,dhcp? Is that pfsense IP on Lan_ETUDIANTS net? dhcp doesn't make any sense there since if you enable dhcp on pfsense interface hidden rules are created that make sure dhcp is reachable. if that IP some other network that rule for dhcp doesn't make any sense at all.
If your wanting to create rules to specific pfsense interface IPs - its better to use the alias for them, which would be the interface name with Address vs Net.
-
Thank you both of your for your help. I don't know very much about firewall rules. I'm a beginner. Now everything works, here is the configuration that worked for me. I tried the aliases but in fact the "This firewall" is better I think. Then I allow only things I want. But, last question is it necessary to allow access to the gateway of the LAN I think yes but I'm not plenty sure. Because I ping 8.8.8.8 even if 192.168.30.254 is not reachable by a ping. This is the rule I made to the top. To answer you, all my dhcp, dns services are hosted in a Windows Server 2019 in the MGMT lan.
-
@louisleg said in Can't ping anything on the internet through LAN:
is it necessary to allow access to the gateway of the LAN
No you do not need to allow students access to the gateway. They can talk "through" it without that. It is a good idea to block students from accessing This Firewall or they could try to log in. To be clear though This Firewall is the pfSense itself, not any of its networks. So you haven't blocked access to the other networks, above the rule that allows LAN_ETUDIANTS to * (any).
Assuming LAN_ETUDIANTS is the 192.168.30.0/24 subnet, those devices don't need a rule as the devices would talk to each other through the switch and not go through the router.
-
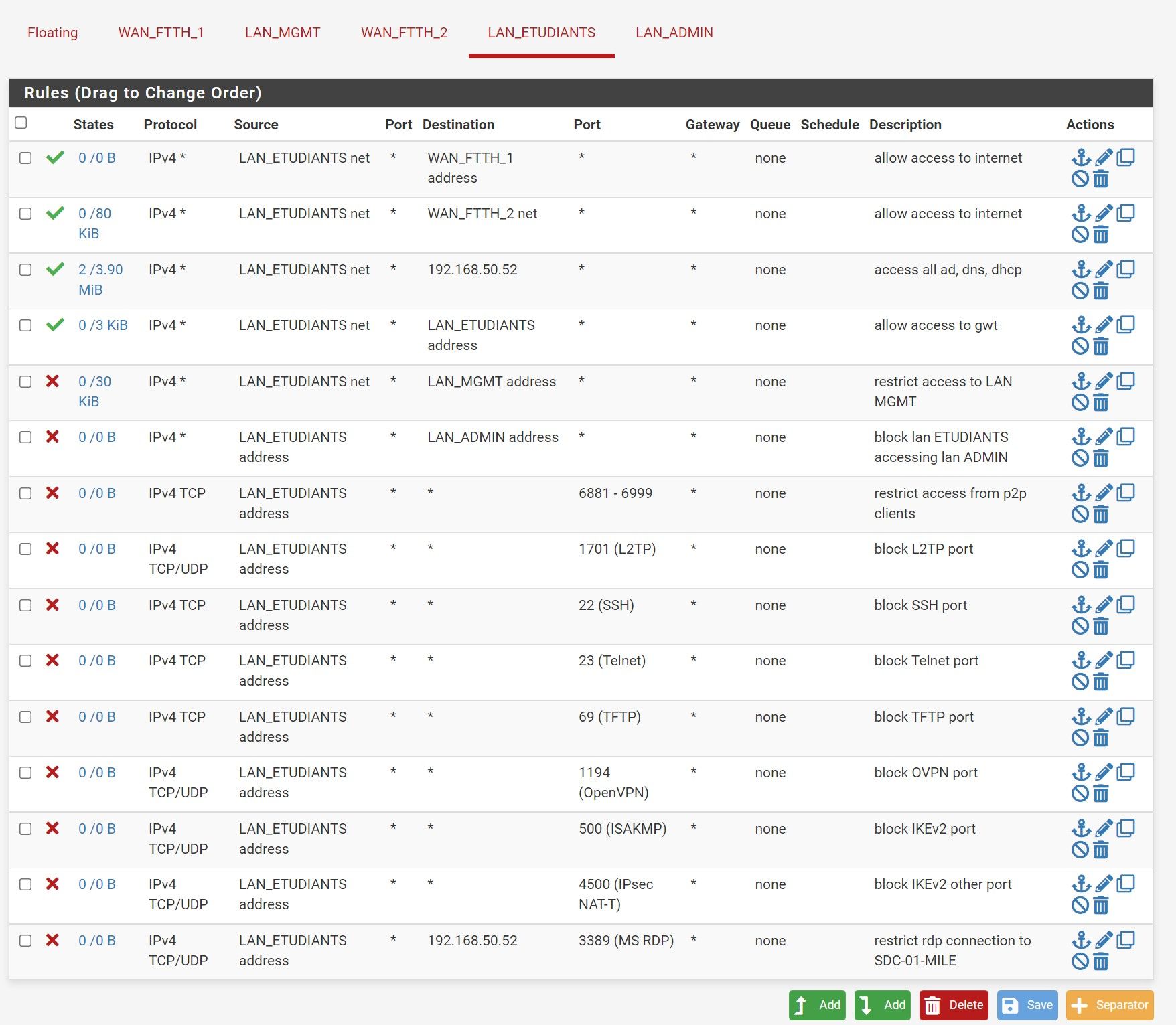
@steveits Ok, thanks for your helpful informations. I made all the modifications now they can ping each other on the same network but can't ping 192.168.30.254 and access the internet and the dns/dhcp server. Hope it'll be ok now!
-
@louisleg said in Can't ping anything on the internet through LAN:
and the dns/dhcp server
Again no rule needed for dhcp, if you enable dhcp on an interface in pfsense hidden rules are created that allow access to dhcp, even if you had no other rules on the interface.
These rules are not shown in the gui, but they are there.
You can view them if you cat /tmp/rules.debug
here are mine as example
# allow access to DHCP server on LAN pass in quick on $LAN proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000002641 label "allow access to DHCP server" pass in quick on $LAN proto udp from any port = 68 to 192.168.9.253 port = 67 tracker 1000002642 label "allow access to DHCP server" pass out quick on $LAN proto udp from 192.168.9.253 port = 67 to any port = 68 tracker 1000002643 label "allow access to DHCP server" antispoof for $WLAN tracker 1000003670 # allow access to DHCP server on WLAN pass in quick on $WLAN proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000003691 label "allow access to DHCP server" pass in quick on $WLAN proto udp from any port = 68 to 192.168.2.253 port = 67 tracker 1000003692 label "allow access to DHCP server" pass out quick on $WLAN proto udp from 192.168.2.253 port = 67 to any port = 68 tracker 1000003693 label "allow access to DHCP server" antispoof for $TEST tracker 1000004720 antispoof for $NS1VPN tracker 1000005770 antispoof for $W_PSK tracker 1000006820 # allow access to DHCP server on W_PSK pass in quick on $W_PSK proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000006841 label "allow access to DHCP server" pass in quick on $W_PSK proto udp from any port = 68 to 192.168.4.253 port = 67 tracker 1000006842 label "allow access to DHCP server" pass out quick on $W_PSK proto udp from 192.168.4.253 port = 67 to any port = 68 tracker 1000006843 label "allow access to DHCP server" antispoof for $W_GUEST tracker 1000007870 # allow access to DHCP server on W_GUEST pass in quick on $W_GUEST proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000007891 label "allow access to DHCP server" pass in quick on $W_GUEST proto udp from any port = 68 to 192.168.6.253 port = 67 tracker 1000007892 label "allow access to DHCP server" pass out quick on $W_GUEST proto udp from 192.168.6.253 port = 67 to any port = 68 tracker 1000007893 label "allow access to DHCP server" antispoof for $W_ROKU tracker 1000008920 # allow access to DHCP server on W_ROKU pass in quick on $W_ROKU proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000008941 label "allow access to DHCP server" pass in quick on $W_ROKU proto udp from any port = 68 to 192.168.7.253 port = 67 tracker 1000008942 label "allow access to DHCP server" pass out quick on $W_ROKU proto udp from 192.168.7.253 port = 67 to any port = 68 tracker 1000008943 label "allow access to DHCP server" antispoof for $DMZ tracker 1000009970 # allow access to DHCP server on DMZ pass in quick on $DMZ proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000009991 label "allow access to DHCP server" pass in quick on $DMZ proto udp from any port = 68 to 192.168.3.253 port = 67 tracker 1000009992 label "allow access to DHCP server" pass out quick on $DMZ proto udp from 192.168.3.253 port = 67 to any port = 68 tracker 1000009993 label "allow access to DHCP server" -
@johnpoz Okay I didn't know that. And for DNS I think it's required, because the fact is that DHCP, DNS, AD, NETBIOS, and all the other services are on the host 192.168.50.52. If I do not make a rule they can access to it I'll need to do a rule for each service Netbios, AD, etc. This is kind of annoying.
-
My point was more to that dhcp would not be needed to be listed in that rule description, and if its on another vlan - that rule wouldn't even work for dhcp. Client isn't going to ask some dhcpd on another vlan for an address.