OpenVPN performance tuning in OCI
-
Hi there,
Last couple days I was struggling with openvpn performance on a pfsense instance running in OCI.
Starting from 40Mbit/s on a gigabit OCI virtual network, I ended up with ~550Mbit/s. Unfortunately, it's still not the best: similar OEL 7.9 instance (VM.Standard.E3.Flex, 1 OCPU, 4GB) gave me almost 1Gbit/s with the same openvpn configuration.I would really appreciate if anybody told me how to improve things to get the same performance like on the linux instance!
Here are details of my stage:
-
Layout:
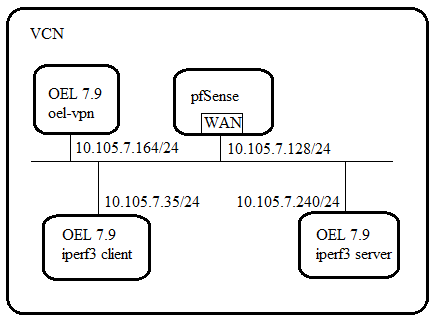
Openvpn server injects a route to iperf3 server to iperf3 client.
pfSense version is 2.5.2-RELEASE (amd64)
Openvpn on OEL is openvpn-2.4.11-1.el7.x86_64 -
iperf3:
iperf -s- on the server
iperf -c 10.105.7.240- on the client -
OpenVPN server and client configs (pfSense, meaningless lines reducted):
dev ovpns3 verb 3 dev-type tun dev-node /dev/tun3 script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 local 10.105.7.128 tls-server server 10.100.253.0 255.255.255.0 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'sslvpn' 1" lport 1194 duplicate-cn tls-auth /var/etc/openvpn/server3/tls-auth 0 ncp-disable cipher AES-256-GCM allow-compression no persist-remote-ip float topology subnet fast-io push "route 10.105.7.240 255.255.255.255" sndbuf 0 rcvbuf 0 push "sndbuf 0" push "rcvbuf 0" tun-mtu 8000 fragment 0 mssfix 0 explicit-exit-notify 3dev tun persist-tun persist-key ncp-disable cipher AES-256-GCM auth SHA256 tls-client client resolv-retry infinite remote 10.105.7.128 1194 udp4 lport 0 verify-x509-name "sslvpn" name remote-cert-tls server explicit-exit-notify 3 verb 3 fast-io tun-mtu 8000 fragment 0 mssfix 0 txqueuelen 2000 ...- OpenVPN server and client config (oel-vpn)
dev tun proto udp lport 1194 daemon keepalive 10 60 ping-timer-rem cipher AES-256-GCM ncp-ciphers AES-256-GCM auth SHA256 persist-remote-ip float topology subnet server 10.8.1.0 255.255.255.0 passtos keepalive 10 60 remote-cert-tls client tls-version-min 1.2 tls-auth /etc/openvpn/server/ta.key 0 persist-key persist-tun duplicate-cn verb 3 comp-lzo no script-security 3 explicit-exit-notify 3 push "route 10.105.7.240 255.255.255.255" tun-mtu 8000 fragment 0 mssfix 0 sndbuf 0 rcvbuf 0 ...dev tun persist-tun persist-key cipher AES-256-GCM ncp-ciphers AES-256-GCM auth SHA256 tls-client client resolv-retry infinite remote 10.105.7.164 1194 udp float remote-cert-tls server comp-lzo no explicit-exit-notify 3 verb 3 sndbuf 0 rcvbuf 0 txqueuelen 2000 tun-mtu 8000 fragment 0 mssfix 0 ...Most important things:
- pfsense should use virtio nic (vtnetX)
- tun-mtu, fragment and mssfix settings are crucial to reach high performance
-