Why do I need 2 Firwall rules to access the Internet from a VLan
-
Hello,
I am rather new with pfSense. I read a lot of books and did a lot of internet research. With that I achieved to setup my home network infrastructure in a way that it works how I expect. Here my setup:
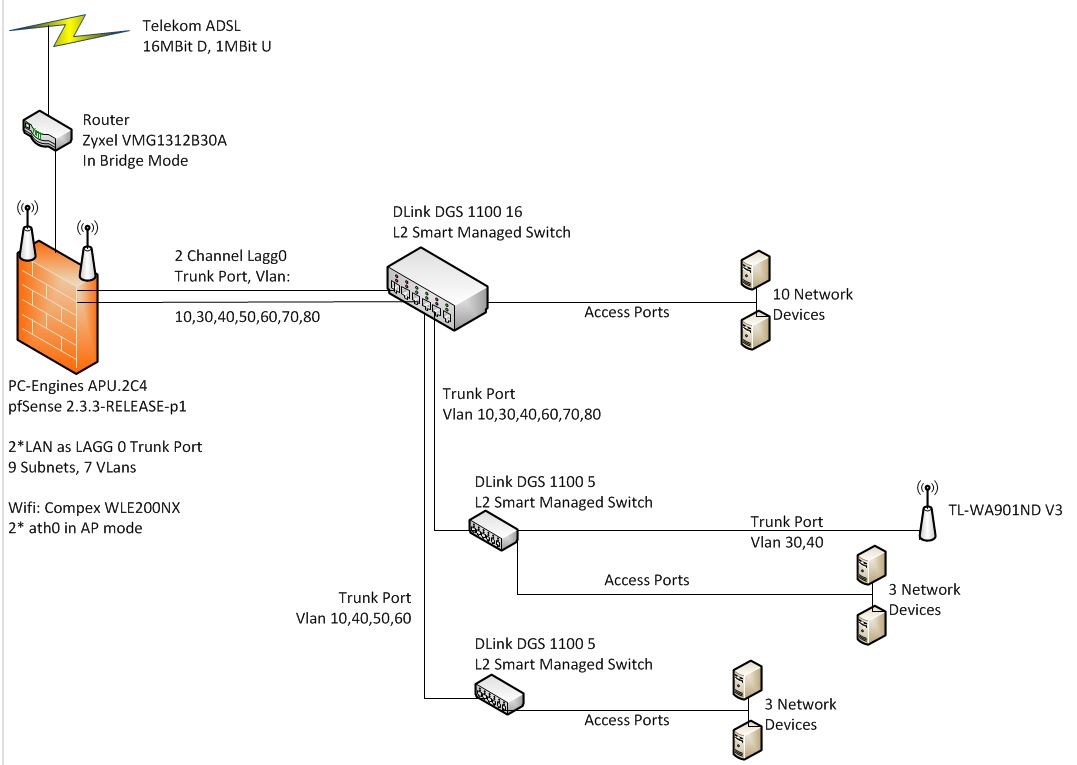
I want to block inter vlan communication in general. But allow specific hosts to talk to other VLan members. So I created a blocking rule for Subnet_All (192.168.1.1/16). Above this rule I allow the traffic for special hosts. VLANDATA is defined as 192.168.40.1/24. Here my questions:
1. Why do I need 2 rules to access the internet: The "pass any" rule at the bottom and the "VLANDATA net" to "VLANDATA address" pass rule? If I delete either one of them, I cannot access the internet.
2. How is "VLANDATA net" and "VLANDATA address" resolved. To which IP addresses?I do want that the devices within the VLans can communicate. But this is handled by the switch. And it works, so far as I could test it. OK.
I expected that, if an IP address outside of the VLans subnet is accessed, the default gateway (192.168.40.1) is accessed and this handles the internet access. My guess would be that the rule "net –> address" allows that. But why do I need the "pass any" rule at then end?
Any help appreciated.
Thanks
Armin

-
" "VLANDATA net" to "VLANDATA address" pass rule? "
And how exactly would your clients ask for dns for example if you remove that rule.. Since your rule of block all would block them from asking pfsense for dns..
-
Hi johnpoz
Thank you for the quick answer. Generally I can understand this.
But in the the top rule there is a "pass any" rule from my "AdminPCs" to "This firewall". So I expected that this rule will take care (at least for the "AdminPCs"). I just checked and disabled the bottom "pass any" rule. Then I could not access the internet. This I do not understand. After reenabling, it immediately worked.
So, I do not understand the logic fully. Maybe I am still to new to all the details.
Can you perhaps please clarify this last topic?
Thank you for your help.
Armin
-
"This Firewall" does exactly that: access the IP of the firewall. Why should that be "the internet" as well?
The rest of the world would be a different address so this rule just doesn't catch it. -
Your first rule would allow your admin pc to access the firewall, for say dns - but it wouldn't allow them to go to the internet..
Your first rule says that whatever is in your admin pc alias can talk to any IP on the firewall on any port via IPv4 via any protocol. But lets say the admin pc wants to go to 208.123.73.69 (ip of www.pfsense.org) – what rule allows that?
if you want to block all access to your other subnets, while still allowing access to the internet you could use a NOT (!) rule.. See attached. Some people don't like this method and like to be more direct with specific blocks and allow vs not rules. But I like the ease of using a ! rule.. There are always many ways to skin the cat.. Understand the process order of the rules is all that is required and then you can come up with many ways to do the same thing.
1st rule: I let dmz segment ping pfsense dmz IP.
2nd rule: I let dmz segment talk to pfsense IP for dns
3rd rule: I let dmz network talk to ntp servers in my alias (ntp) only on udp 123.. These are ntp that run on my lan segment.
4th rule: I block any access to any other firewall IP, be lan, be it wan, be it wlan, dmz on any protocol or port on the firewall that is not allowed via say a hidden rule.. Like dhcp when you enable dhcp server.
5th rule: I then allow any traffic from dmz net on the dmz interface that is not going to a rfc1918 address. This the !, this means NOT.. My alias contains all the rfc1918 space. 192.168/16, 10/8, 172.16/12 -- so in the future if I bring up another vlan or segment I know for sure that the dmz segment will not be able to go there. But it can talk to the internet - which is going to be for sure some other IP other than rfc1918 space.The default rule (not shown) would then block ipv6 since I do not have any rules that allow ipv6, etc. Or anything that is not allowed for above via ipv4 would hit the default deny rule..

-
Dear All
Got it. I think I first need to read some book about basic networking, before working on firewalls . . . ;)
Sorry for beginner questions and thank you very much!
Armin
-
"I think I first need to read some book about basic networking,"
hehheeh - yeah that would be a fantastic idea!!! Come on back if you have questions about any of it - here to help.. But yes a basic understanding of tcp/ip is kind of requirement to understanding how to firewall it..
You don't attempt to tune up your car without knowing how the engine works right ;) Sure you can get it painted, you could hang a dream catcher off the rear view.. You could put on some chrome parts.. You can fill it with gas, and maybe even change the oil.. But do you mess with the fuel mixture or the bore or stroke length – ie replace the cam or modify it without understanding the basics of how that works ;)