Unofficial E2guardian package for pfSense
-
Hello everyone, this is my first post at the Netgate forums, so please forgive any and all ignorance! I was hoping I could get some assistance with this awesome plugin.
First of all, I'd like to give my sincerest thanks to @marcelloc for all his work in making this available to pfsense. I followed the videos on YouTube best I could-- even turned on subtitles to auto-translate into English, which helped.
I believe I have the majority of my E2G setup configured correctly. After creating a new set of ACLs separate from the defaults, I'm definitely able to block both "sites" and "URL" based on categories and blacklists. Moreover, I can look in the real-time logging and see the ACL getting applied accordingly when I attempt to navigate to various addresses which I know should be getting blocked.
My issues are related to the phrase filtering options, which I cannot seem to get working no matter what I do. For troubleshooting, here's what I've done:
-Completely disabled all of the Site and URL filtering
-Under "General," I ensured:
--"Filter Mode" is set to "Filtered (default)"
--"Weighted phrase mode" is set to "Singular...(default)"
--"Phrase filter mode" is set to "use both (default)"
-The Phrase List ACL I created:
--Is enabled at all times
--Has Banned Lists enabled for all categories
--Has Weighted Lists enabled for all categories
--Has Exception Lists disabled / uncheckedWhen I apply these ACLs to the correct subnet, I can immediately browse to porn sites, and nothing seems to be happening in the real-time logs. If I then modify the ACL to re-enable Site and URL lists & re-apply it, porn sites are blocked, and I can see this happening in the real-time logs. As such, I'm fairly certain I at least have the filter group and IP settings configured correctly.
Am I just mistaken about what the Phrase filtering can do? I thought it was able to read webpage content and block any page with naughty words on it, but maybe I'm wrong?
If it helps, I am not using Squid -- E2G Daemon is set to "Direct Connect," and I also have https interception enabled with a self-signed certificate.
If anyone could be of assistance, I would be extremely grateful. I'm happy to provide any information that might help-- I would even be willing to pay you for help if you were able to fix it for me, after which I would post the findings here so others could use it.
My thanks in advance to any and all who might reply to this!
-
@La6er how are you configuring them? Are you adding them in exactly how you typed?
If so, you need to change the way you've added them. There should be just one IP or subnet per line, but you can't do a 'range' typed in the way you did. So if you wanted those 6 IPs only, the simplest way would be to do one per line, like this:
10.16.0.10
10.16.0.11
10.16.0.12
10.16.0.13
10.16.0.14
10.16.0.15If you already added them this way and it's still not working, you should also check under:
General -> Auth plugins, and ensure that "Ip Address" is selected. -
@amorimpermissus To anyone having this issue as I did, I solved my own problem (yay!). I determined the cause was in the "Groups" settings tab. Even though I had Transparent Proxy and SSL support enabled under the Daemon section, I didn't have MITM properly enabled for the ACL group.
By going to Groups -> <name of the ACL group> -> Group Options, I ensured these were selected:
"Scan clean cache"
"Hex decode content" (this shouldn't be necessary, but I have it enabled anyway)
"Infection/Scan Error Bypass on Scan Errors Only"
"Filter SSL sites forging SSL certificates" (previously not selected)
"Auto-switch to MITM to deliver block page"After this, I needed to simply install the CA cert in the proper locations on my client machines, and all phrase filtering and greylisting worked as designed.
-
Hello. Thanks for this fork.
I want to configure e2guardian with antivirus scanning functionality, but I don't know how to do it without installing squid and enable squid antivirus. If I don't do this, I have not clamav daemon and e2guardian give me error of connection to clamv daemon.
There are the possibility to install clamd service without installing squid?
Thanks a lot -
Does anyone use the bypass feature in E2guardian? It does not seem to work for me. What am I doing wrong?
-
@kenrutt said in Unofficial E2guardian package for pfSense:
Does anyone use the bypass feature in E2guardian? It does not seem to work for me. What am I doing wrong?
I use both source and destination bypass. All work perfectly fine for me. I'm using it through Alias to keep things clean.
-
@pfsensation said in Unofficial E2guardian package for pfSense:
I use both source and destination bypass. All work perfectly fine for me. I'm using it through Alias to keep things clean.
I guess I am not not sure how to use through Alias.
-
@pfsensation said in Unofficial E2guardian package for pfSense:
I use both source and destination bypass. All work perfectly fine for me. I'm using it through Alias to keep things clean.
Do are you talking about the bypass ip's? I was asking about the bypass on the block page when pressing the "Acknowledge".
-
@kenrutt said in Unofficial E2guardian package for pfSense:
@pfsensation said in Unofficial E2guardian package for pfSense:
I use both source and destination bypass. All work perfectly fine for me. I'm using it through Alias to keep things clean.
Do are you talking about the bypass ip's? I was asking about the bypass on the block page when pressing the "Acknowledge".
Ohh, I was referring to the IP's bit. I couldn't get that working either and didn't have time to investigate. Naturally, forgot. :(
I did go as far as to debugging my own code on the block page and making sure that the "Acknowledge" does generate a bypass key. But the key doesn't appear to work when used. Strange. It will need more digging.
Definitely an issue with the back end bypass code.
-
@pfsensation said in Unofficial E2guardian package for pfSense:
Ohh, I was referring to the IP's bit. I couldn't get that working either and didn't have time to investigate. Naturally, forgot. :(
I did go as far as to debugging my own code on the block page and making sure that the "Acknowledge" does generate a bypass key. But the key doesn't appear to work when used. Strange. It will need more digging.
Definitely an issue with the back end bypass code.Ok. Hey if you figure something out keep me posted.
Thanks a bunch. -
How to configure mitm with pfsense please help me
-
@abhijitmore007 Under "Daemon" tab make sure "Check to enable E2guardian SSL interception" is checked and make sure Cert is selected. Then under the groups tab in group options select and highlight "Filter ssl sites forging SSL Certificates (off)".
-
Can you provide step by step configuration
-
@kenrutt I am using pfsens 2.4.4 and squid with e2d for filtering but squid not integrated with e2d for ssl cert. there is no need of squid for ssl filtering
-
I've updated the install code to use version 3.5.1 and ssl interception.
Motivational Quotes in Hindi -
@kenrutt thank you problem resloved
now https filter is working -
@kenrutt some site get error
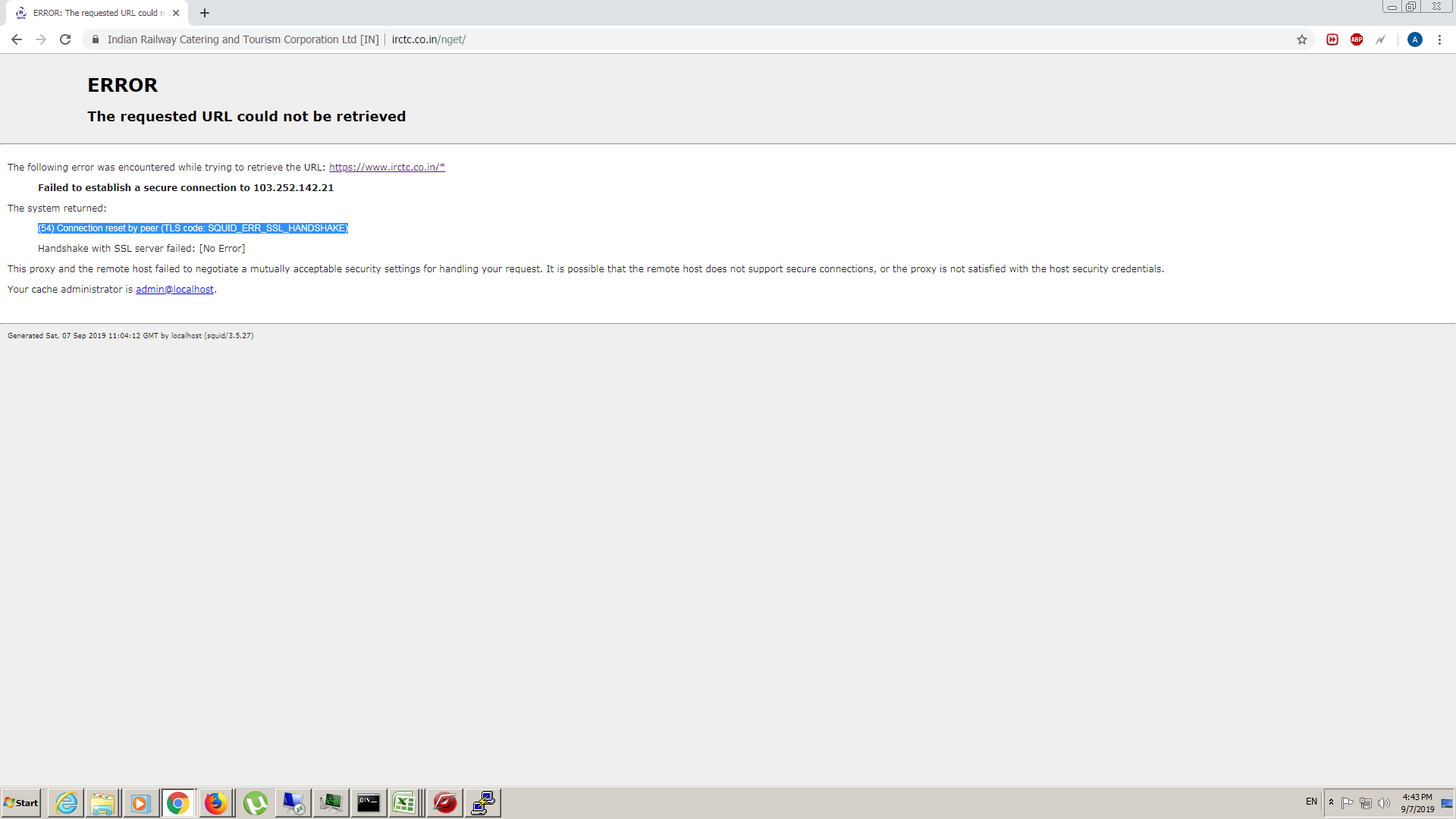
-
@abhijitmore007
The error maybe this site requires a secure connection. mitm is a man in the middle attack and will fail with such sites. Yo may need to create an exception rule with a list for those sites to not use mitm. You still can filter the sites but not filter/read the content. -
@abhijitmore007 said in Unofficial E2guardian package for pfSense:
@kenrutt some site get error

I stopped using squid due to problems, try with direct mode without squid. I pretty much have no problems with any site via the browser. The apps I have issues with I have made exceptions for.
-
@pfsensation My experience has been the same. With e2guardian in direct mode things work fairly well. Only a few things I needed to bypass.