-
I am unable to get ACME certificate renewal with DNS validation to work with Dyn.
There is no custom API for Dyn - so I configured it to use the nsupdate command and obtained a key from Dyn.
This always fails with a time-out.
If I run nsupdate from the command line in the same manner as the Acme script does…that also fails with time out.
However, if I add the Zone parameter as shown below it works.
nsupdate
server update.dyndns.com
key keyname keyvalue
update add myfqdn 60 in txt "blah blah"
zone myzone
sendAccording to the nsupdate man page - if zone is not explicitly provided it attempts to figure it out from other input. That doesn't seem to be working in my situation for some reason.
Am I out of luck?
-
FWIW - an update on this. The pfsense nsupdate renewal script is subtly incompatible with Dyn's implementation. Dyn requires an explicit zone parameter and uses an arbitrary TSIG key name that is not derived from the zone/host name. RFC 2845 strongly recommends that the Key Name reflect the name of the host(s). Dyn's TSIG account key does not.
It is possible to hack the pfsense script at /usr/local/pkg/acme/dnsapi/dns_nsupdate.sh so that certificate renewal works.
Just add your zone and your TSIG keyname and keyvalue from Dyn as nsupdate parameters and certificate renewal will then work. In the short run this gets the job done.
In the long run I will probably choose another vendor (Cloudflare?) for DNS management since Netgate support expresses no enthusiasm for enhancing Acme to work properly with Dyn.
-
The latest ACME package has support for Dyn.
It was added to acme.sh and we recently went through and added all the new providers supported by acme.sh now.
We don't have any Dyn accounts to test against, but the code is all there.
-
Hi, I do have a domain and the DNS service, both from Dyndns.
But I can't make it to work.Using the DNS dyn method.
I can see that through the Dyndns reports page, that an entry is added and deleted by _acme-challenge.mydomain.net during the certification generation.
But in the ends, it fails with this message:mydomain.net:Verify error:Correct value not found for DNS challenge
I ran the dnssec-keygen, and ran bind using the key command in the global settings:
key Kmydomain.net {
algorithm hmac-md5;
secret "HcszMU0bDghj/Jx+8NIcNMHae13OlRE9gKnfghtywGwJ6X3e/Zw4A6DA4wWcJa13NgX5RSNRveXCdgh+2Lg==";
};Any one got this to work?
-
Hi,
I'm also having problems with this. I can't even get the domain updated. The error shown in the logs is (I have replaced my domain name with <mydomain>in this listing):
[Mon Dec 18 19:38:44 CST 2017] Start Dyn API Session
[Mon Dec 18 19:38:45 CST 2017] get token failed
[Mon Dec 18 19:38:45 CST 2017] Error add txt for domain:_acme-challenge. <mydomain>[Mon Dec 18 19:38:45 CST 2017] Please check log file for more details: /tmp/acme/<mydomain>/acme_issuecert.logNot sure what to do. I'm using the correct username and password (verified several times). @mcury, what type of DYN account do you have?
Brian</mydomain></mydomain></mydomain>
-
I had the dns managed express with a domain there in Dyndns.
But gave up dyndns, not using it anymore.As my objective was just to get a SSL certificate for my GUI, I created a duckdns.org account and it`s working just fine so far.
The example below is just valid for your FQDN duckdns account.
It’s useful if you don’t have a domain in the Internet, and if you just want a certificate for a FQDN. (off course not valid for the domain)!!By doing this way, you won’t need to disable any security feature, won’t need to buy a domain anywhere, and will need only one entry into your DNS server (which can be local).
It’s perfect for setting your Pfsense management to HTTPS without having certificate warnings.
You can also export those certificates and use in another server, but there are other methods that you can use that are better for this purpose.How it’s working here
My local domain: local.lan
My certificate is valid for myhost.duckdns.orgFor that to work without disabling any security feature as DNS rebind check when you connect to PFsense management using that new ACME duckdns certificate, you can do the following:
Configure it to be your GUI SSL certificate and set in that same page
System > advanced settings > admin access > Alternate Hostname:
Set the same FQDN configured into your certificate.Go into your DNS resolver (or the DNS server you use), and point the FQDN of the ACME certificate pointing to your Pfsense LAN IP.
If you don’t have a WAN static IP or just want that to be reachable from outside, you can also set Pfsense Dynamic DNS feature to update your IP to the same FQDN configured into the certificate.
EDIT: Use VPN to reach your PFsense from outside, don`t leave the managament port open on WAN!
-
Hi,
has there been any further developments on the acme dyndns?
-
I know, I know... replying to an ancient thread. But this was the ONLY information that got up and working.
For those of you trying to issue ACME certs through Let's Encrypt on pfSense this should help. I too considered moving to another dynamic DNS provider but got lazy just thinking about updating all the DDNS clients I have out there...
@piperspace Thank you so much for pointing me in the right direction. I was going nuts trying to get this to work.
I had to make the following edits in /usr/local/pkg/acme/dnsapi/dns_nsupdate.sh:
nsupdate -k "${THISNSUPDATE_KEY}" <<EOFbecomes
nsupdate <<EOFthen added:
zone <your domain in DynDNS> key <DynDNS TSIG Key Name> <DynDNS TSIG Key HMAC>(THE SPACE IN BETWEEN THE KEY VALUE IS IMPORTANT!!!)
I also added a "quit" after the "send" statement, dunno if it is needed, but it's working for me.
Make sure you update the dns_nsupdate_add() and dns_nsupdate_rm() functions as well.
Be patient when you renew/issue, the script sleeps for 120 seconds to allow DNS updates to show.
Hope this helps someone.
-
@taius You are welcome. I am glad my research helped you.
FWIW - I noticed in August that the then current version of Acme no longer required my hack. But now I am on Acme 0.3.2_4 and the hack is again necessary. Are we having fun yet?
-
@piperspace, @taius ... Thank you both.
Background: I was unfortunately not able to use the webserver/port 80 method, as I need to forward the port to an internal webserver, on which I can't/won't use the FTP method. Also, the Dyn.com built-in provider does not work with a Standard DNS account at Dyn.com, which meant using the nsupdate method was the only one left available to me. Without this helpful post, I would have given up in despair!
Because I prefer to have my setup configurable through the webGUI, I decided to attack the dns_nsupdate.sh file to allow configuration through the existing webGUI fields. For this I have explicitly checked for "update.dyndns.com" as the target, and therefore used the "KEY" textarea to provide the necessary ZONE and KEY lines required.
First, replace the dns_nsupdate.sh file with the one attached.
Then configure your domains in the webGUI as usual, with the server specified as "update.dyndns.com", and the Key as:zone example.com key [Key Name] [Key HMAC]This way you can use multiple domains/keys/etc. all from the webGUI.
The changes/additions I made to the file are as follows:
_info "adding ${fulldomain}. 60 in txt \"${txtvalue}\"" if [ "${THISNSUPDATE_SERVER}"="update.dyndns.com" ]; then THISNSUPDATE_DATA=`awk -F '"' 'BEGIN{RS=";"}NR>1{print $2}' "${THISNSUPDATE_KEY}"` nsupdate <<EOF ${THISNSUPDATE_DATA} server ${THISNSUPDATE_SERVER} ${NSUPDATE_SERVER_PORT} update add ${fulldomain}. 60 in txt "${txtvalue}" send quit EOF else nsupdate -k "${THISNSUPDATE_KEY}" <<EOF server ${THISNSUPDATE_SERVER} ${NSUPDATE_SERVER_PORT} update add ${fulldomain}. 60 in txt "${txtvalue}" send EOF fiand
_info "removing ${fulldomain}. txt" if [ "${THISNSUPDATE_SERVER}"="update.dyndns.com" ]; then THISNSUPDATE_DATA=`awk -F '"' 'BEGIN{RS=";"}NR>1{print $2}' "${THISNSUPDATE_KEY}"` nsupdate <<EOF ${THISNSUPDATE_DATA} server ${THISNSUPDATE_SERVER} ${NSUPDATE_SERVER_PORT} update delete ${fulldomain}. txt send quit EOF else nsupdate -k "${THISNSUPDATE_KEY}" <<EOF server ${THISNSUPDATE_SERVER} ${NSUPDATE_SERVER_PORT} update delete ${fulldomain}. txt send EOF fiOther than the "cryptic" awk command to extract the text out of the generated key file - everything else is very self explanatory.
Thanks again ... very helpful, and very timely info!
Cheers.
-
I still have issues with this.
It fails on adding _acme-challenge.....
error updating domainThe TSIG is correct.
Perhaps a couple of screenshots?This is so convoluted for a major dyndns provider.
-
I am now having some Acme success with DynDNS on Pfsense 2.4.4-p2 with Acme package 0.5.4_1. I no longer need to engage in script hacking.
Below is a screenshot of my Amce config.
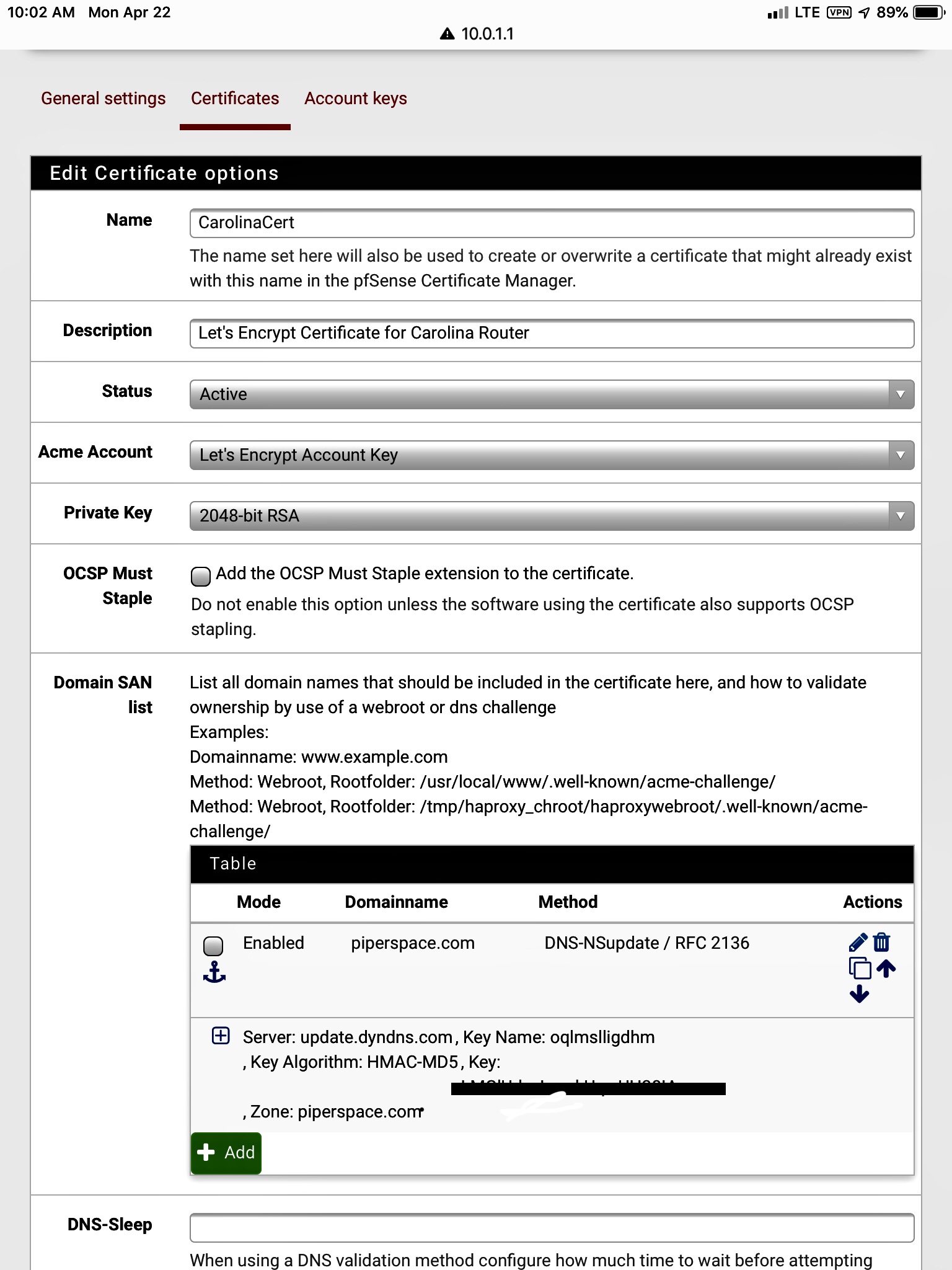
-
I reset the script back to the original.
My settings:
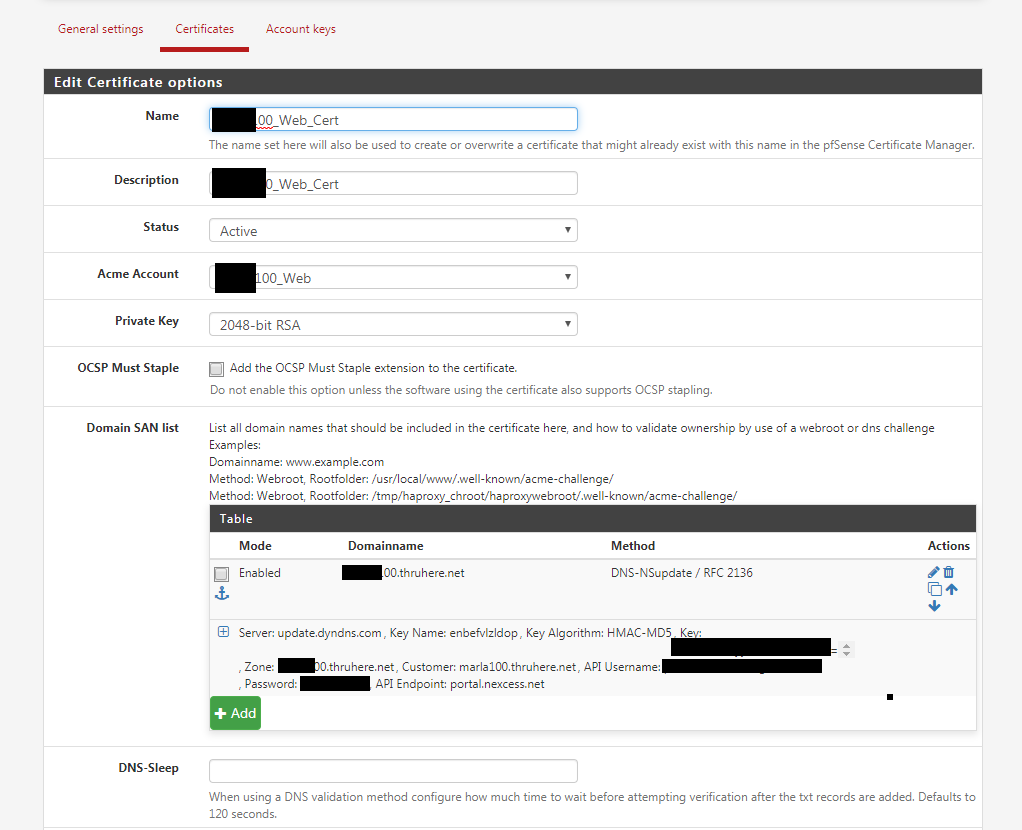
Error message:
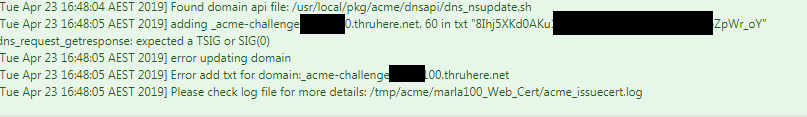
I probably need to get a better understanding of how this process works, can i use a DynDNS as the Zone?
-
No. DynDns.net is not your zone. The parameter you are using for that looks ok. But you are using additional parameters I don’t know about.
I have DynDns Standard DNS which lacks a proper API thus requiring nsupdate. There is also DynDns Pro which may have an API. It’s confusing. Which service do you have? If you have DynDns Pro you are probably barking up wrong tree here.
Also, you can test parameters by connecting to your router and running nsupdate from the command line.
-
The additional parameters auto-filled, so I don't know where they came from and I can't seem to edit them. Perhaps, as you point out, I have a dyndns pro service.
-
You might want to delete your config and start over using the DNS-Manual method.
-
So I upgraded Acme to version 0.5.7_1 and this is busted again.
In /tmp/acme/[mycertname] there is a .key file where my parameters have been stored. Except there is a period mysteriously appends to my key name.
When I edit this key file, remove the period and then feed it to nsupdate it works.I am vexed that Dyn compatibility seems to come and go. Would be willing to beta test new versions if that would be well taken.
-
Just wanted to update things. This is still broken in 0.58!
I suspect this is because the team thinks the dyn support is in the dyn section. Well, I know I for one, cannot get a dynid. So I'm stuck with the nsupdate method. Why can't I get a dynid? NO CLUE! I put in my "old" credentials, which I had just logged in with, and it says invalid. I suspect many of us are in the same boat, so PLEASE people, just because you support the new DynID, doesn't mean you've left a bunch of us high and dry!So, I basically used the script posted above, but for somereason it didn't pull out the keyname. So I added this right below his awk magic
THISNSUPDATE_KEYNAME=awk '{if (NR == 1){ key=substr($2,2,length($2)-3); print key}}' "${THISNSUPDATE_KEY}"
Then, it also didn't include the zone. I'm not sure of the "right way" to get the zone, so here's what I did: ZONE=echo ${fulldomain} | sed 's/_acme-challenge\.//g'
Then I changed the dnsupdate command to dnsupdate -d and added key $THISNSUPDATE_KEYNAME $THISNSUPDATE_KEY
zone $ZONE
This allowed everything to work.Posting this to help others and provide "cloud" backup of my work :)
-
Recently I got a notice from Oracle. The DYN Standard service I have is being phased out next spring. My option at that time is to migrate to an alternate Oracle product.
My plan is to use up the remaining time on my DYN Standard subscription and then migrate to CloudFlare.
-
I got the notice as well, but I have paid domain registrations as well as dyn pro (though I’m not sure I use it anymore...I had originally obtained it so I could do things like device.mysubdomain.dyndns.org...maybe I should audit that.
Regardless, they said it would be “migrated” to an oracle product line. Do they do dns? Or do they mean “rebranded”. Either way, I expect little to change other than eventually...maybe....they’ll fix their dynid bugs :)
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.