Splice and Bump based on source IPs and destination domains
-
First and foremost, I have setup squid with HTTPS splice-all on pfSense at home and it is working better than I ever thought possible.
Being able to see basic HTTPS usage data and logs is great!Now I want to bump a few hosts at home (Mostly because I have NFI how to install certs on devices at home (Chromecasts, Roku, Kindles, etc)
Can I have a whitelist for internal IP addresses (my laptop and mobile) that will be bumped (for Blacklist/AV inspection), while all others continue to be spliced (so I can see a summary of who is accessing certain domains).In addition to this, I'd also like to exclude certain domains from being bumped (such as when I browse my banking site). Can I also whitelist destination domains
Finally, I'm not reading many good things about squidguard or [dans/e2]guardian.
Has anyone used https://www.diladele.com/licensing.html before as the web filter and http://www.squidblacklist.org/ for the blacklist?Thanks
-
Hello BluBoy, if you have questions about web safety ask me.
-
This is my running "SSL/MITM Mode: Custom" config:
# some banking sites that should not be MITM-ed acl no_ssl_bump ssl::server_name .mybank.com acl no_ssl_bump ssl::server_name .whatsapp.com acl no_ssl_bump ssl::server_name .whatsapp.net # some source IPs that should not be MITM-ed acl splice_only src 10.0.1.7 acl splice_only src 10.0.1.8 acl splice_only src 10.0.1.19 # get SNI obtained by parsing TLS Client Hello during step2 # (which is instructed by ssl_bump peek step1) acl step1 at_step SslBump1 # no_ssl_bump and splice_only ssl_bump peek step1 ssl_bump splice no_ssl_bump ssl_bump splice splice_only # bump the rest ssl_bump bump all -
Hello BluBoy, if you have questions about web safety ask me.
You may have already had an email from me.
The personal usage limit of 7 devices is insanely low. Most households have multiple people, each with multiple devices which would exceed this quite easily.
I've been very eager to try it, but that limit has prevented me for so long (your support was great, responding extremely quickly with a possible solution. But how many people would go to the effort of querying your license restriction over email?)This is my running "SSL/MITM Mode: Custom" config:
# some banking sites that should not be MITM-ed acl no_ssl_bump ssl::server_name .mybank.com acl no_ssl_bump ssl::server_name .whatsapp.com acl no_ssl_bump ssl::server_name .whatsapp.net # some source IPs that should not be MITM-ed acl splice_only src 10.0.1.7 acl splice_only src 10.0.1.8 acl splice_only src 10.0.1.19 # get SNI obtained by parsing TLS Client Hello during step2 # (which is instructed by ssl_bump peek step1) acl step1 at_step SslBump1 # no_ssl_bump and splice_only ssl_bump peek step1 ssl_bump splice no_ssl_bump ssl_bump splice splice_only # bump the rest ssl_bump bump allThis looks like it is exactly what I am after.
Rather than using URLs, I take it I can feed it a list instead?Also, what settings have you used on the configuration page?
If you are able to, would you mind sharing a screenshot please?Thanks!
-
Also, what settings have you used on the configuration page?
If you are able to, would you mind sharing a screenshot please?Thanks!
Nothing special, just the default settings, screenshot attached. And yes you can extend that list of domains and IPs as you like.
Maybe good to know:
https://wiki.squid-cache.org/SquidFaq/WindowsUpdate#Squid_with_SSL-Bump_and_Windows_Updates
https://docs.diladele.com/faq/squid/index.html
If you do AV scanning, feed clamav with extra signatures:
Info: http://sanesecurity.com/usage/signatures/
Script: https://github.com/extremeshok/clamav-unofficial-sigs
Cheers!

-
Thanks, this is worked fine for me
This is my running "SSL/MITM Mode: Custom" config:
# some banking sites that should not be MITM-ed acl no_ssl_bump ssl::server_name .mybank.com acl no_ssl_bump ssl::server_name .whatsapp.com acl no_ssl_bump ssl::server_name .whatsapp.net # some source IPs that should not be MITM-ed acl splice_only src 10.0.1.7 acl splice_only src 10.0.1.8 acl splice_only src 10.0.1.19 # get SNI obtained by parsing TLS Client Hello during step2 # (which is instructed by ssl_bump peek step1) acl step1 at_step SslBump1 # no_ssl_bump and splice_only ssl_bump peek step1 ssl_bump splice no_ssl_bump ssl_bump splice splice_only # bump the rest ssl_bump bump all -
Hi All,
I'm trying to use your hints on my configuration.
I need to put a subnet (e.g. 192.168.0.0/24) with Splice All and all the other traffic with Splice Whitelist, Bump Otherwise.Thank you!
-
Hi All,
I'm trying to use your hints on my configuration.
I need to put a subnet (e.g. 192.168.0.0/24) with Splice All and all the other traffic with Splice Whitelist, Bump Otherwise.Thank you!
Did you try this
some banking sites that should not be MITM-ed
acl no_ssl_bump ssl::server_name .mybank.com
some source IPs that should not be MITM-ed
acl splice_only src 192.168.0.0/24
get SNI obtained by parsing TLS Client Hello during step2
(which is instructed by ssl_bump peek step1)
acl step1 at_step SslBump1
no_ssl_bump and splice_only
ssl_bump peek step1
ssl_bump splice no_ssl_bump
ssl_bump splice splice_onlybump the rest
ssl_bump bump all
-
@bluboy Thank you I used the ACL for a XBOX to splice only so I could still SSL check other devices with certificates
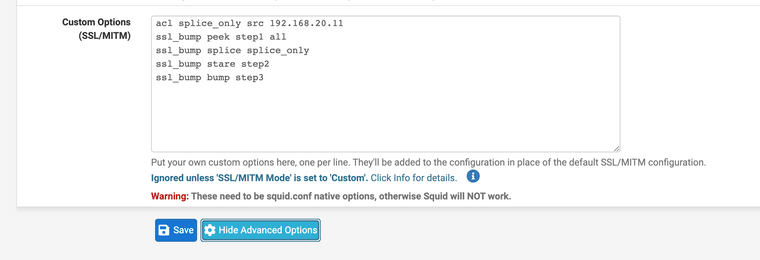
This way I can cache and check for viruses on my laptop and my son can watch xbox and play games.