Adding 2nd OpenVPN cert causes issues with first cert
-
Hi all, hope this is the right forum.
I've noticed a weird issue on my pfSense config.
I'm using pfsense 2.4.2 community edition.I have 2 linux VPS systems, with two different hosts each running OpenVPNAS.
I have set up the VPS 1 in the cert manager (CA, Cert, set up a tunnel client, and set up an interface for it). The CA is listed as "Self-Signed".
This works fine, it connects and tunnels my traffic through without issue.However, when i do the exact same process on VPS 2, and add it's own CA - VPS 1 lists it's CA as VPS 2.
here is a pic to show you what i mean:

Looks like some sort of weird certificate mismatch - but I can't find out what's causing it. This same setup was working fine on an earlier version of pfsense (2.3.4).
Any idea's what i might be doing wrong?
Thanks!
-
@edgesync I have this same issue, did you ever figure out what was wrong. Initially, both VPN connections will work, but when the 1st connection needs to restart, then the connection will fail and there will be TLS errors in the log.
Can anyone comment on why this is happening. I'm new to pfsense and I don't understand why this is happening.
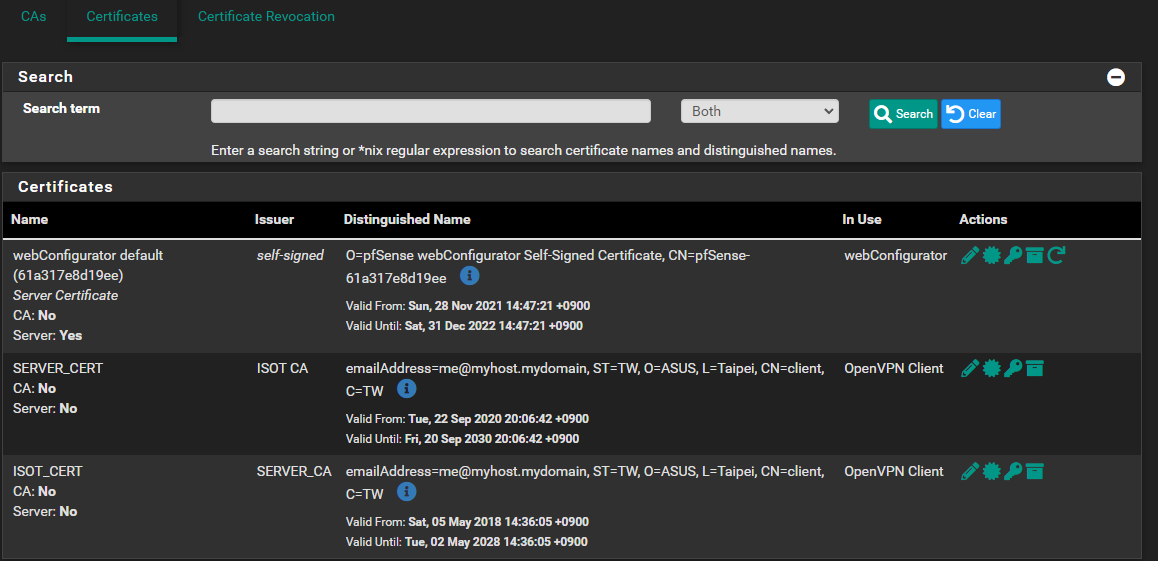
These are my CAs, see how the 1st CA says the issuer is the second CA?

These are my Certs, see how they say each other is the issuer?
These are my VPN client connections.
-
You need to use unique subjects for different CA and certificate entries. You have essentially created duplicates and they can't figure out the issuer because the subjects are identical. At least change the CN for each certificate. You'll have problems with those two certificates as well since they also have identical subjects.
Also, make sure you are setting the certificate properties correctly, you have one labeled "server cert" but it does not have the properties set to be a server certificate.
-
@jimp ok, thanks I see that now. both the VPN servers are Asus AX-11000 routers, so I guess I'll have to install a pfsense box at one of those locations because I don't see any way to change the CN.