MFA for pfSense GUI
-
Sure I guess - such a requirement shows lack of understanding of security at a basic level to be sure. Personally would have no desire to do business with such a entity ;)
Since the gui is only available from specific physical connectivity. Have to be connected to the management network to access the gui.. Factor 1, then need password to access said web gui = factor 2. You now have MFA..
If you then say added some form of auth to get on said management network say 802.1x this is factor 3, etc..
But here per JimP last time this came up
https://forum.pfsense.org/index.php?topic=138601.msg758029#msg758029Install FreeRADIUS package. Setup users and Google Authenticator. Setup an entry in the Auth Servers for FreeRADIUS on Localhost. Set GUI to use the local RADIUS server for GUI auth. Done.
-
Sure I guess - such a requirement shows lack of understanding of security at a basic level to be sure. Personally would have no desire to do business with such a entity ;)
First of all, a 'password' is not a security, it's secret and it only works as long it kept secret within a group of people or yourself. It's a very outdated idea considering 'password' as a security measure. If the business thinking otherwise, they are actually doing better. It's the similar argument, if all the internal endpoints should also use SSL/TLS - it's a policy and for a number of good reasons, you like it or not.
Since the gui is only available from specific physical connectivity. Have to be connected to the management network to access the gui.. Factor 1, then need password to access said web gui = factor 2. You now have MFA..
Again, I think we are saying something, which s very outdated according to today's standard. What about internal threats from inside the network? what about a leaked password? What about the case when you need to give access to your management network to a number people from various part of the organization but all of them don't need to login to pfSense GUI? Another simple case, you running your VPN server from pfSense box, something happened out of hrs. and you need to access the pfSense console remotely? And when you say you can only have access to the GUI from VPN, what happens when VPN itself is down and you need to fix that going to web gui. Would you rely on just a password? And some organizations, simply don't just allow any web logins (internal or external) without MFA. I can give you a number of other examples, but that's a start if you really insist you donlt get the point.
Agin I think, you are confusing 'security' with 'secret'. A password CANNOT be the main sentry.
But here per JimP last time this came up
https://forum.pfsense.org/index.php?topic=138601.msg758029#msg758029Install FreeRADIUS package. Setup users and Google Authenticator. Setup an entry in the Auth Servers for FreeRADIUS on Localhost. Set GUI to use the local RADIUS server for GUI auth. Done.
Well that's definitely an option but not a native solution. Why people go through a comparatively harder way when a native solution can be developed and provided. The main reason, people try to bypass security b'cuz we make them so hard and complicated to implement. pfSence should really do the forward thinking rather holding on to some 80's security concepts, IMO.
-
" A password CANNOT be the main sentry. "
It isn't!!! The physical access to the management network is the MAIN security… Password is just one of the many factors involved in access to the web gui.
Physical control is always better than any sort of something you know or even have...
Lets add up the factors that might include. Enter the building. I can not enter my office without a fingerprint.. Something I AM... Just to get in the building.. Now to access the special network that can even access the firewall I have to HAVE my laptop.. This auths to network via 802.1x - so it has to be my laptop.. Something I have.. To login to MY laptop you have to have my tiks card.. So this is something else I have, but also something I know since you have to have the pin to access the certs on that card. Keep in mind that you can not just connect to any port in the building you have to be on the few limited admin ports. Only these ports once proper authed even have access to the management network.
You also need to know the password to my account to login to the laptop.
Now only then could you access the web gui of the firewall. Lets not forget you need to know its IP for management and port. Its not on any user network in the building that can access the web gui.
Then you need to know the gui password.
So how is that not MFA??? You want to add what Google authenticator to it? or some SMS text to your phone..
What I think is happening here is someone needs to check off some box that says MFA.. And doesn't really understand the whole concept of what that actually is.
Also that is built in.. Just install the package and set it up for whatever auth you want to use. its all just clickity clickity to set up.. If your checkoff sheet says oh you need to be able to do XYZ as your MFA then the sheet is pointless and doesn't understand the basic concept that makes up MFA...
If your web gui is accessible to even the normal internal network of your org then your doing it wrong in the first place..
-
Well that's definitely an option but not a native solution. Why people go through a comparatively harder way when a native solution can be developed and provided. The main reason, people try to bypass security b'cuz we make them so hard and complicated to implement. pfSence should really do the forward thinking rather holding on to some 80's security concepts, IMO.
What do you consider a native solution? Can you give an example?
-
Exactly… Like to hear this as well, since if you want to setup any sort of MFA on say cisco you need to point to a remote auth server and in this remote auth server you can setup different forms of MFA other than just a user name and password. Say some sort of fob like google auth, I personally use Authy myself where this sort of MFA make sense.
Ie services that have no access controls other than username/password - ie say your bank website, or your email site.. Ie the interface is open to the public..
Maybe the user would be happy with a walk through of how easy it is to say setup OTP to the gui? Even though I personally think its a waste of time - since the web gui to your firewall should always only be accessible via a controlled network.
Another way to accomplish MFA when remote to the firewall would be VPN as only way to access it. Where you now have multiple factors to access the vpn, even if remote.. Cert for example, even could setup OTP needed as well along with this, etc.
I have sneaky feeling only thing they might consider built in, is if you had a check box to click and it post up a QR code you could scan on your phone to setup your OTP.
-
I have sneaky feeling only thing they might consider built in, is if you had a check box to click and it post up a QR code you could scan on your phone to setup your OTP.
For Google Auth in the FreeRADIUS 3 package, it has exactly that. A QR code you can scan into the GA app.
Most other MFA setups require involving an external/central auth server or RADIUS specifically. It may be possible to bake in something like that without RADIUS but why reinvent the wheel when doing so offers no advantage?
It may happen eventually, but for the moment there isn't any compelling reason to spend manpower on reimplementing something that works fine as-is.
-
Yeah Jim but they have to do a bit of reading and click a few buttons ;)
And OMG they have to actually click the install for the freerad package.. So clearly its not built in… I think everyone should drop everything else they are working on and work on this. Because you know someone needs to check off a checklist that pfsense supports MFA without actually knowing what that actually means. But if there is a check box that gives them a QR code for their OTP then they can give it a checkmark ;)
Must be loosing 1000's of customers a day because of this...
Love to know what the OP thinks about the fact that google auth is just really another password.. But oh wait they call it a "shared secret key" ;) Be it a bit longer that is used for a math formula to generate a code based on time of day ;) So anyone with that "password" could generate the same code as well.. Not all that secure now is it when you think about it ;)
So when it comes down to it your talking about really just having 2 passwords vs 1.. So their MFA is just 2 things you know vs an actual other factor like something you have or are, or physical access, etc.
If I know the users password and whatever the super secret "shared secret key" is I have access.. Vs say having to have a physical access to a specific network that has multiple "passwords" you have to auth with. And something longer than than just a shared key..
Now I guess a cert could be seen as the same thing... But then your taking about a REALLY LONG password ;)
But hey have to check off that MFA check box now don't we... The 30 seconds you spend answering this thread you could of been working on setting up that check box ;)
-
Hi @ivor
Sorry for my silence. by 'native' I meant something like AWS Management Console, which you can enable/disable in the user settings area and once it enabled the only after MFA entry you get access to the console. Or something like ability to integrate some 3rd part application like DUO.I know you guys may not like the idea of having MFA but really like to see it's not just relying on a silly password only.
-San
-
This post is deleted! -
TOTP has become commonplace. sad this is still a reality in 2022...
RIP cybersecurity attestation forms as pfsense is natively uninsurable
-
You know you can do this via Freeradius using Google Auth or mOTP?
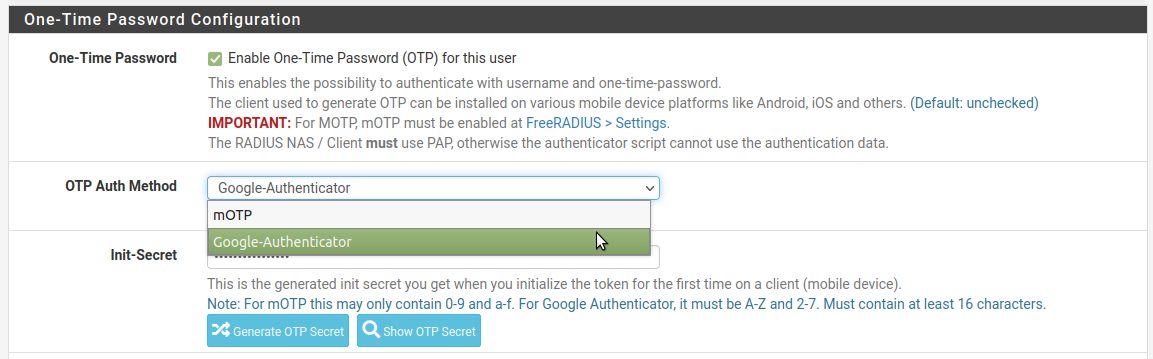
-
@stephenw10 I get that it's possible. It just feels unnecessary to have a dependency on the freerad package for this functionality.
-
@condescending_dev said in MFA for pfSense GUI:
@stephenw10 I get that it's possible. It just feels unnecessary to have a dependency on the freerad package for this functionality.
I don’t mean to stir up the discussion again, but it is a fact that cybersecurity insurance and company policies can become a pfSense showstopper because of MFA.
Yes, I know, install freeradius and do it that way, but you - like me - also know that there are several cases where that package stops running, doesn’t reinstall on upgrades and so on, and that just becomes a major problem if you are in uptime trouble as it is.
It would be nice if it was a backed in feature you could depend on in a standalone/isolated/no running packages situation as well.
-
@keyser said in MFA for pfSense GUI:
It would be nice if it was a backed in feature
I agree. I'll poke it further up the list if I can.
Steve
-
and just last week, we were stopped from using
pfSensebecause we failed to demonstrate a meaningful MFA to login to the webConfigurator.
We also failed to get Cyber Essential certificate (in UK) because of lack of MFA on the GUI.
We really need something sooner than later.
-San
-
If it were to be something considered in the future. Then please consider adding support for such things as FIDO/2. So that we could use hardware keys e.g. Yubikeys as well.
Please and thank you.

-
@macusers but why didnt you implement the suggestion asd outlined by @jimp
Use FreeRadius and Google Auth?I get where everyone is coming from - basically a standlone feature to do this but again....the feature technically exists now with the freeradius package. Im really not understanding the issue here. Use it or dont.
-
@michmoor said in MFA for pfSense GUI:
@macusers but why didnt you implement the suggestion asd outlined by @jimp
Use FreeRadius and Google Auth?I get where everyone is coming from - basically a standlone feature to do this but again....the feature technically exists now with the freeradius package. Im really not understanding the issue here. Use it or dont.
Because we have all tried doing upgrades :-)
Packages are supposed to install in the background, but that can occasionally fail - or cause issues, and then you are in big trouble if your physical console is a 1000 miles away.
Relying on a local installed 3rd party freeradius package for the second factor is a hen and the egg problem waiting to happen if you have any issues. -
@keyser if Radius fails isnt there a fallback to local auth then?
-
@michmoor said in MFA for pfSense GUI:
@keyser if Radius fails isnt there a fallback to local auth then?
and you back with no MFA again.
The thing, which is very hard for me understand: why it's so hard to acknwledge the issue and work towards a proper solution, rather than spending time convincinging people for a not-so-convenient work around.-San