IPv6 doubts
-
Greetings from Portugal. Mi ISP here (Vodafone) assigns me a /56 prefix; namely 2001:818:d9d9:ba00::/56. The IPv6 addresses are doled out through SLAAC from the ISP fiber ONT. So far, so good. I think I can set up the WAN interface in my pfSense to receive its IP SLAACly, or set up a static IPv6 within the range of my delegated prefix. I mean, I hhave 256 prefixes to do it, so why not? Here goes, 2001:818:d9d9:ba00::fffe/64, with default gateway set at 2001:818:d9d9:ba00::1. Now that is my WAN interface set up, it works, I can ping6, and everything is smooth as silk. On to the LAN side: Same idea, right? I set an IPv6 address in the same subnet of my assigned prefix, set gateway to none (because it is after all a LAN address), set my DNS servers and all should be fine and dandy, with my clients behind pfsense receiving an Internet-pingable IPv6 address. Right? Wrong. Wrong, because although I get an IPv6, external addresses (google.com, microsoft.com, 1.1.1.1, etc.) get a nice, juicy, "Time out" when pinged. Am I missing something here? Have I done everything "by the book" as they say, or should I look at enabling static routes between the ba00 and ba01 subnets through loopback, or set NAT66 with a ULA, and then use that ULA as my dhcp6 range? Have I missed any firewall black magic? I would appreciate any help available in this matter.
Cheers
-
Your post is a bit confusing. Typically, the ISP uses DHCPv6-PD to assign the prefix to your network. Then the router, such as pfSense can be configured to assign individual /64s to the various interfaces. Do you have IPv6 addresses available on your LAN? And please, Please, PLEASE forget about NAT. It's a hack to get around the IPv4 address shortage.
One you have IPv6 up and running you'll notice you have multiple GUAs on your computers. One will be permanent and the others temporary, typically a new one every day, with a lifetime of 7 days. Point your DNS to the permanent one. On Windows, it will likely by a random number and on Linux, MAC address based. The temporary addresses are always random number based.
-
Dear @JKnott, if my post seems confusing I am sorry, it was unintentional. The fact is, my ISP is not using DHCP-PD to spread IPv6 GUA from its router to my pfSense box. It is using SLAAC to do so, and this information comes straight from the ISP itself. I do have IPv6 GUA in my LAN generated by my pfSense box DHCPv6 server; what I do not have is Internet connectivity from any one of them. I have checked and double checked, time and again. by connecting a client directly to the router, and once it is connected I do get IPv6 addresses with IPv6 connectivity to the Internet, while when the same client is connected behind the pfSense box it fails the ipv6 tests and ping6 reports timeouts to the WAN address. I hope this made the situation more clear, and I do understand twhat you say about NAT, and I agree, but my ISP (by its own admission) has other ideas, it will not do DHCPv6 prefix subdelegation.
-
how are they giving you a /56 with slaac?
I think maybe some sort of communication breakdown here. Do you mean they hand your router an IP on its wan via slaac and then you can get your /56 via delegation?
What is the address you get on your wan - what is the prefix size?
When you state they assigned you this 2001:818:d9d9:ba00::/56, I would take it they routed that to you - if so then your golden you can break that up into /64 and assign to your different networks.
-
@johnpoz: As per your request, the router has in its web interface the following information: The prefix is 2001:818:d9d9.ba00/56, the gateway IP is 2001:818:d9d9:ba00::1. When I called the ISP complaining that I did not get Internet connectivity for any device behind my pfSense and asking how did I have to set up the prefix subdelegation, they told me that IP address distribution from the ISP's router is not made through DHCPv6 but through SLAAC. Using the ISP's own suggestion I assigned the WAN port on the pfSense box a static address, which works. Given that I can't break up the /56 and slice it and dice it to my heart's content -- I have tried, to frustrating failure.
-
If your isp is giving you a /56 via slaac that is utterly borked!!! There are 2 legit prefixes /64 and /128
How about you just let your wan be slaac and setup that /56 broken up behind you and see if that works... How is that isp try and rollout ipv6 and just do not have clue one.. Did nobody at this isp read any of the rfcs?
-
Post the output for your WAN interface from Status > Interfaces.
-
Off topic sorry - tried sending you a chat.. But you have them blocked.. Your link to the use this diagram is not working. Would guess since the change to nodebb vs smf
-
OK yeah chat should be fixed. Waiting for the attachments from the old forum to be sussed out before I hassle that diagram.
-
@Derelict : Of course, as soon as I get home I'll post the relevant info.
-
@johnpoz apparently not, I have exactly zero clue as to why they'd give me a whole /56, only to deny it to me by giving me /64 addresses through SLAAC from their router, smh...
-
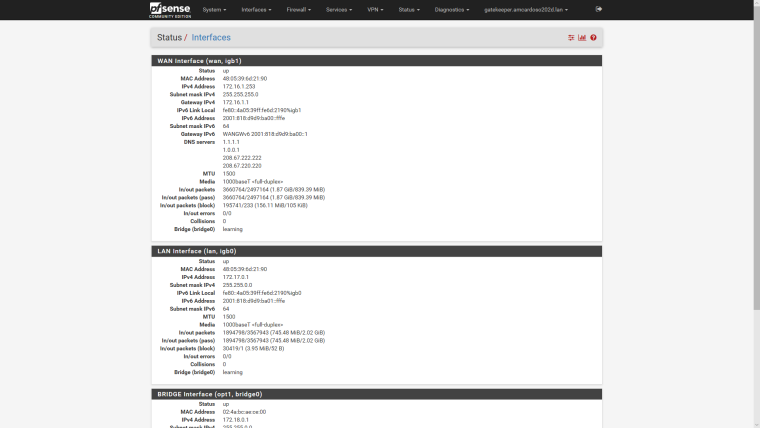
@derelict as per your request here's the requested snapshot
-
OK that's a /64 on WAN so that is what I would expect.
Is that statically-configured or is that what is on the interface when WAN is configured for SLAAC?
LAN looks good as well. I would:
(At least temporarily) Pass ICMPv6 (any) traffic on WAN from source any to destination 2001:818:d9d9:ba00::/56
ping6 2001:818:d9d9:ba01::fffe from the outside someplace.
See if you get a response. If so, you can start looking at why LAN isn't working. If not, verify you can ping6 to 2001:818:d9d9:ba00::fffe. If not your pings are probably not working. if so, packet capture on WAN for IPv6 traffic for 2001:818:d9d9:ba01::fffe and test the ping6 to that again. Stop the capture and see if you can see the echo requests coming in from the ISP. If so, you can proceed to figure out why there is no response. If not, you need to nail down the ISP as to exactly how they are provisioning this /56.
-
You've got a bridge interface set up with IP addresses on each interface and the bridge, thought you should only have IP addresses on the bridge interface.
https://doc.pfsense.org/index.php/Interface_Bridges
-
@derelict this is statically configured. I haven't tried using SLAAC, will attempt to do so now.
-
Not at all what I recommended you do but OK.
-
@nogbadthebad Yeah I haven't even started with the bridge yet. First thing is to see if this ISP is even sending the traffic.
@cmpsalvestrini Why are you complicating things that aren't working yet with things like interface bridges? Why do you feel the need to do that?
-
Pings to the WAN interface work.
mac-pro:~ andy$ ping6 2001:818:d9d9:ba00::fffe
PING6(56=40+8+8 bytes) 2a02:8010:XXXX:X::14 --> 2001:818:d9d9:ba00::fffe
16 bytes from 2001:818:d9d9:ba00::fffe, icmp_seq=0 hlim=252 time=50.847 ms
16 bytes from 2001:818:d9d9:ba00::fffe, icmp_seq=1 hlim=252 time=51.265 ms
16 bytes from 2001:818:d9d9:ba00::fffe, icmp_seq=2 hlim=252 time=50.797 ms
16 bytes from 2001:818:d9d9:ba00::fffe, icmp_seq=3 hlim=252 time=50.751 ms
16 bytes from 2001:818:d9d9:ba00::fffe, icmp_seq=4 hlim=252 time=51.085 ms -
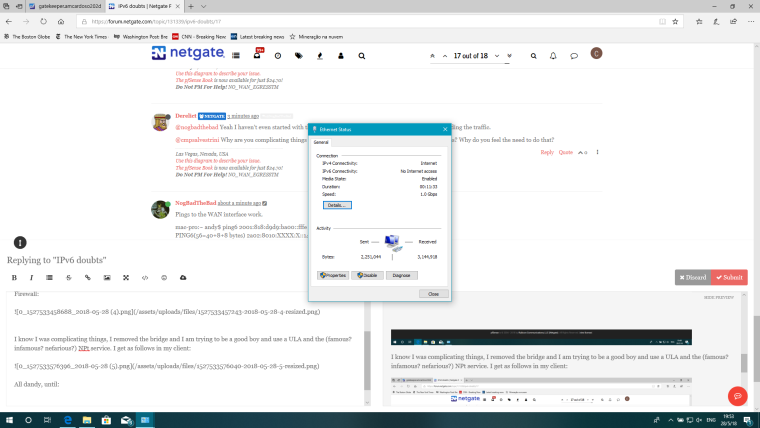
@derelict I-m still on the static, I fiddled with the LAN side a bit and I have as follows:
Interfaces status: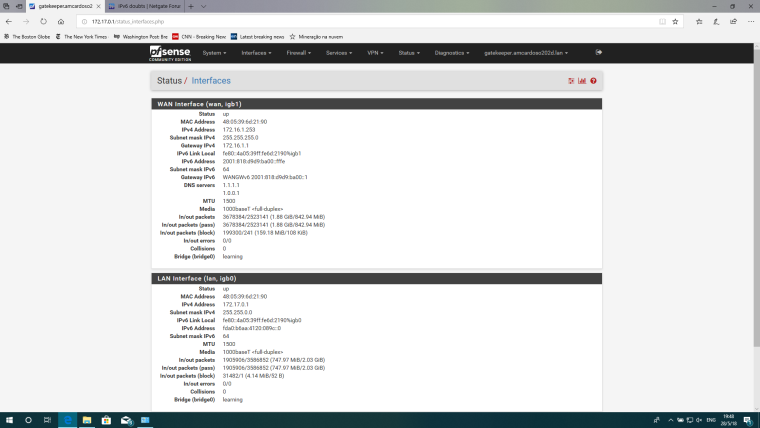
Firewall:
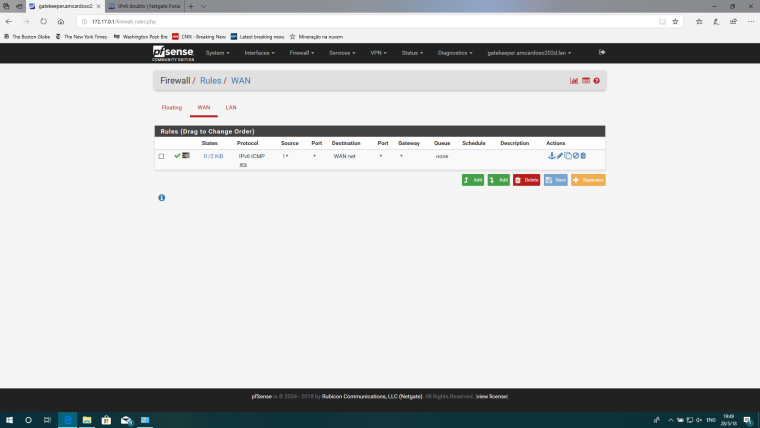
I know I was complicating things, I removed the bridge and I am trying to be a good boy and use a ULA and the (famous? infamous? nefarious?) NPt service. I get as follows in my client:
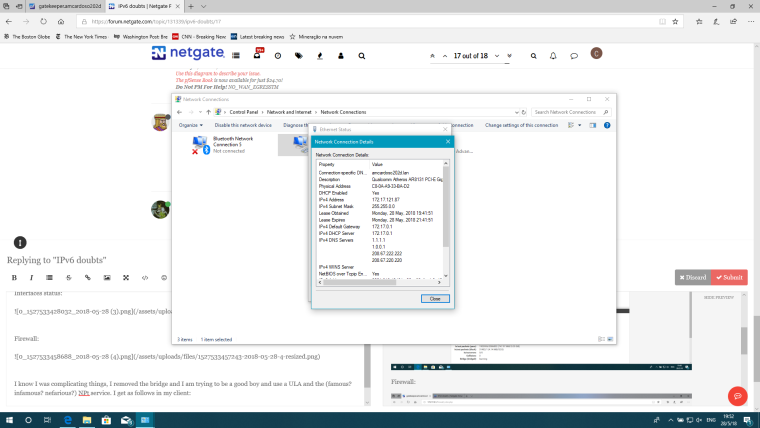
All dandy, until:
-
Right. the other doesn't but that could be rules.