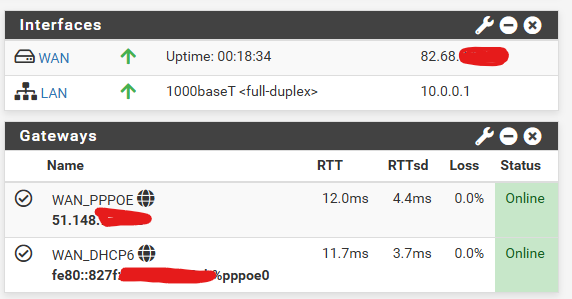
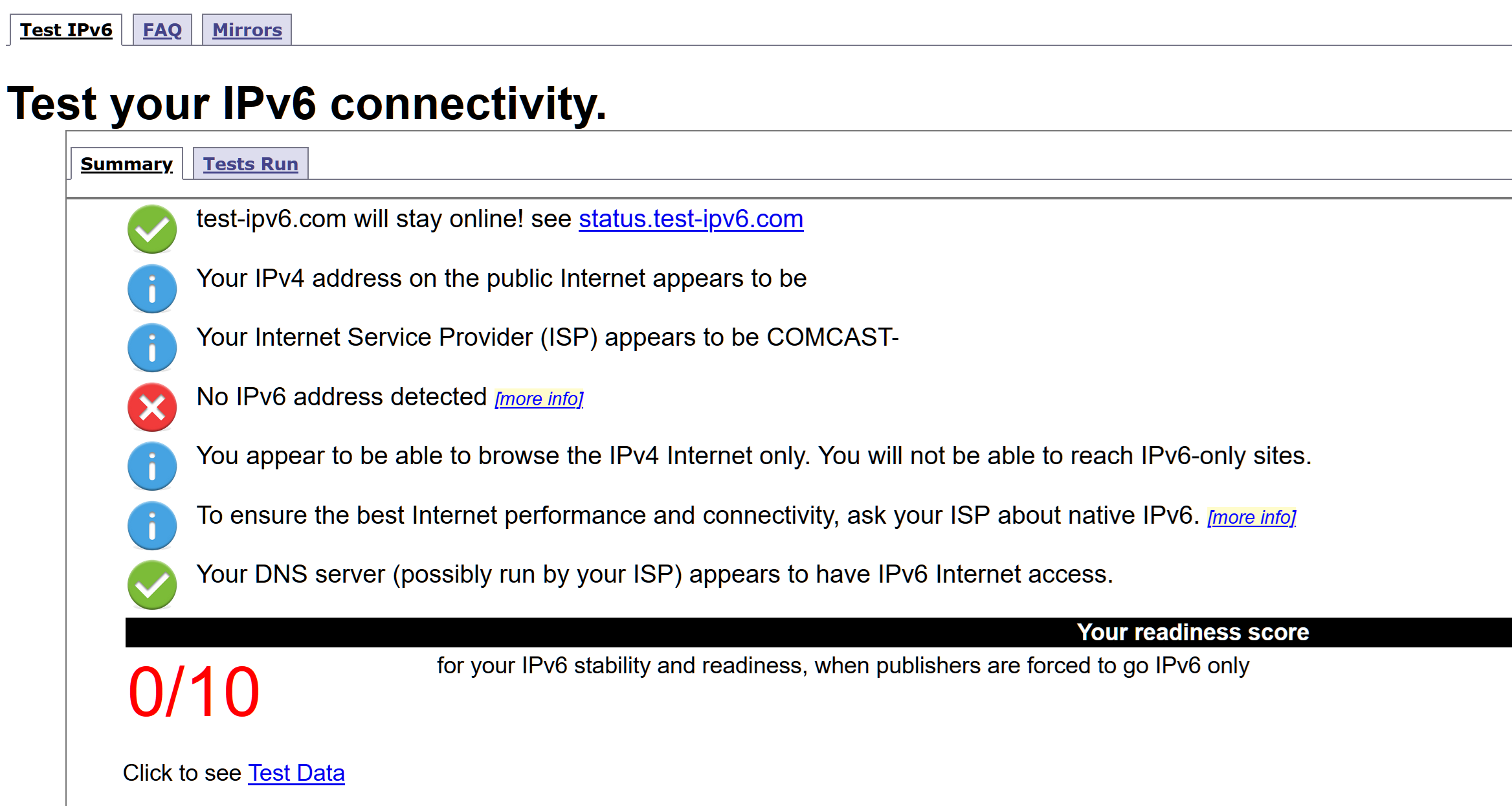
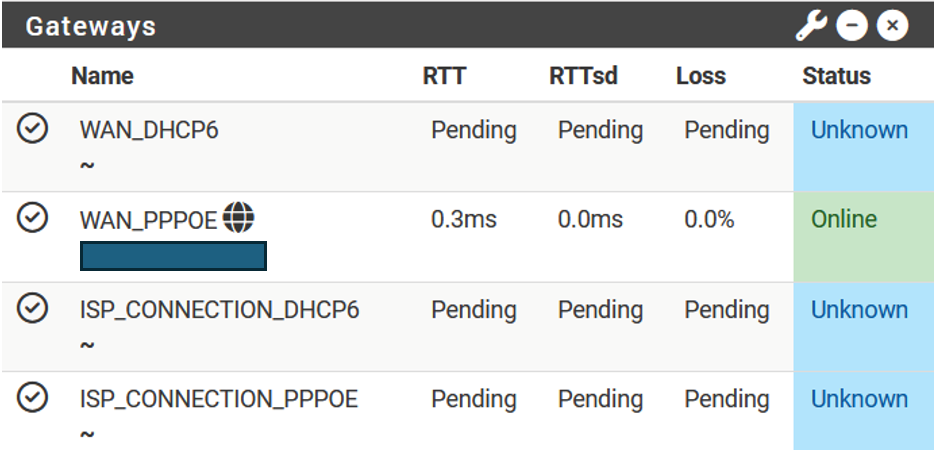
The original settings in this thread worked fine for me a few years ago when Verizon began rolling this out. Then they seemed to roll everything back in late 2023 and I went the whole of 2024 with no ipv6. I noticed this summer that I was seeing ipv6 addresses again and when looking into it, they appeared to have enabled it all again in Jan. of this year. But by the time I noticed over the summer, I had upgraded to the latest pfsense version and also switch over to KeaDHCP server.
I tried using it for an online game and was noticing that I was getting dropouts for 15 minutes about every hour, so I just went back to using ipv4. This weekend I started looking at it more closely and found that every 1 hour 15 minutes, I would lose the ability to use ipv6. These are the entries I would see in my logs. The period from 9:52-10:04, I would have no ipv6 connectivity. IPv4 would renew the leases fine and connectivity there was unaffected.
Oct 12 10:04:40 dhcp6c 55217 dhcp6c Received INFO
Oct 12 10:04:39 dhcp6c 55217 Sending Renew
Oct 12 10:04:36 dhclient 40170 bound to <redacted ip> -- renewal in 3600 seconds.
Oct 12 10:04:36 dhclient 18404 Creating resolv.conf
Oct 12 10:04:36 dhclient 17251 RENEW
Oct 12 10:04:36 dhclient 40170 DHCPACK from <redacted ip>
Oct 12 10:04:36 dhclient 40170 DHCPREQUEST on igb0 to <redacted ip> port 67
Oct 12 09:52:27 kea-dhcp6 21138 WARN [kea-dhcp6.alloc-engine.0x1c3afd017400] ALLOC_ENGINE_V6_ALLOC_FAIL_CLASSES duid=[<redacted>], [no hwaddr info], tid=0x6b0e2c: Failed to allocate an IPv6 address for client with classes: ALL, pool_lan_0, UNKNOWN
Oct 12 09:52:27 kea-dhcp6 21138 WARN [kea-dhcp6.alloc-engine.0x1c3afd017400] ALLOC_ENGINE_V6_ALLOC_FAIL_NO_POOLS duid=[<redacted>], [no hwaddr info], tid=0x6b0e2c: no pools were available for the lease allocation
Oct 12 09:52:27 kea-dhcp6 21138 WARN [kea-dhcp6.alloc-engine.0x1c3afd017400] ALLOC_ENGINE_V6_ALLOC_FAIL_SUBNET duid=[<redacted>], [no hwaddr info], tid=0x6b0e2c: failed to allocate an IPv6 lease in the subnet <redacted ip>::/64, subnet-id 1, shared network (none)
Oct 12 09:52:27 kea-dhcp6 21138 WARN [kea-dhcp6.alloc-engine.0x1c3afd016d00] ALLOC_ENGINE_V6_ALLOC_FAIL_CLASSES duid=[<redacted>], [no hwaddr info], tid=0x6b0e2c: Failed to allocate an IPv6 address for client with classes: ALL, pool_lan_0, UNKNOWN
Oct 12 09:52:27 kea-dhcp6 21138 WARN [kea-dhcp6.alloc-engine.0x1c3afd016d00] ALLOC_ENGINE_V6_ALLOC_FAIL_NO_POOLS duid=[<redacted>], [no hwaddr info], tid=0x6b0e2c: no pools were available for the lease allocation
Oct 12 09:52:27 kea-dhcp6 21138 WARN [kea-dhcp6.alloc-engine.0x1c3afd016d00] ALLOC_ENGINE_V6_ALLOC_FAIL_SUBNET duid=[<redacted>], [no hwaddr info], tid=0x6b0e2c: failed to allocate an IPv6 lease in the subnet <redacted ip>::/64, subnet-id 1, shared network (none)
After fooling around with various settings and searching online, I came to the conclusion that pfsense's implementation of KeaDHCP did not appear to handle renewals of the prefix delegation. I don't know if that is the right conclusion, but the config that was being generated looked to have hard coded subnet ranges and never used Kea's pd-pools config block.
Ultimately, all I did to "fix" this was to disable the KeaDHCP service on my LAN interface and change the Router Advertisment-->Router Mode from Managed to Assisted and let my clients sort ipv6 themselves instead of having the router do DHCP. I could set it to Stateless but if someone can tell me what I was doing wrong I'll try and set up DHCP6 again.
As I could not find others online having this problem, I assume I did not have the DHCP server configured correctly, but at least for my use case, I don't actually need DHCP6.
[image: 1760369517889-beb9b838-c78b-496e-813b-653f044d6232-image.png]
Since making that change, my ipv6 dropouts ceased. Also, an unexpected 1.5-2ms reduction in ping time to the target I was using.
[image: 1760369744926-42176401-a3c8-4d22-b829-a9b5c0b4516a-image.png]
Hopefully this helps others who might end up in a similar boat. This and the now lost thread on dslreports.com were tremendous resources for getting this working originally.