VLAN Assistance
-
Could use some help.
I've setup a vlan specifically for the kids and I'm having a hard time with getting the vlan to route anything. Obviously I'm doing something wrong, in the firewall rules I have a any to any rule which I thought should allow any and all traffic but that's not the case.
Physically I have a NIC interface dedicated to the WiFi AP (by default 10.0.20.0/24) and then the vlan12 (10.0.12.0/24) associated. Anything that connects to the main SSID routes just fine but once I enable vlan12 on the kids wifi network nothing happens. I'm sure I'm doing something very wrong or missing a step. Any help would greatly appreciated.
Thank you
-
Is it an actual AP ?
Is it connected to a switch where your trunking the native vlan and VLAN 12 to the AP ?
-
@nogbadthebad said in VLAN Assistance:
Is it an actual AP ?
Is it connected to a switch where your trunking the native vlan and VLAN 12 to the AP ?
Actual AP, an Unifi AC-Pro. It's connected directly to the pfsense box. The clients do connect and get the correct IP. Just no traffic moves, not even to the management page of the pfsense.
-
What rules did you put on the vlan 12 interface in pfsense? Had you messed with the outbound nat and taken it off automatic. If so when you add a network/vlan you would have to make sure you adjust the outbound nat, etc.
-
This may be a dumb question, but did you set up a VLAN interface in pfSense? Do the kids get an IP address? If they get one, can they ping the VLAN interface on pfSense?
-
Ah same AP that I have then, I use a POE switch as well :)
Should work, what do your firewall rules on VLAN 12 look like ?
-
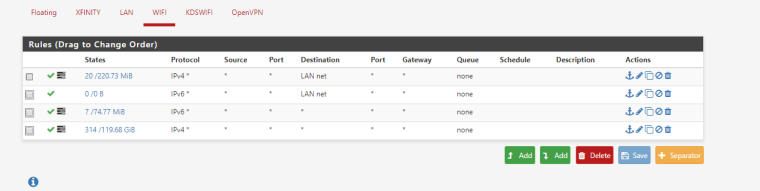
Here are the rules I have setup for the WiFi interface. - https://gyazo.com/952b4386388881cf71458ea1e1fdb219
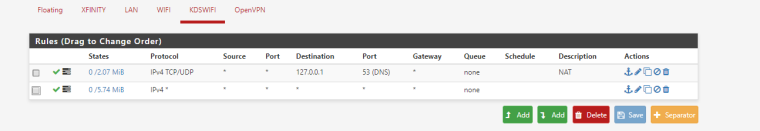
Here are the rules I have setup for the Kids Wifi Interface. - https://gyazo.com/06da96f5d8d992af67b087833301cca1
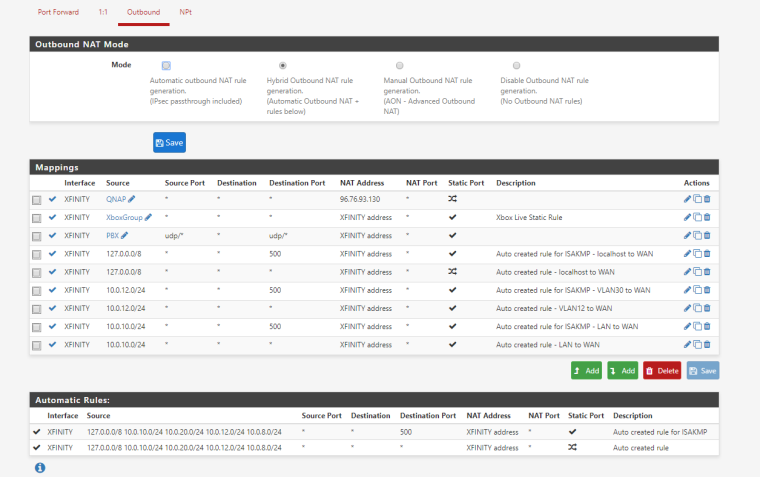
Here are my current NAT rules - https://gyazo.com/e6cd81fa145743bead73f8a6a963ac03
I'm definitely not the brightest bulb in the pack, I'm sure it's something dumb stupid that I'm overlooking. All help is greatly appreciated.
-
you can remove the 127.0.0.1 firewall rule, as 127.0.0.1 is the device itself.
You can just drop screenshots into the compose window btw :)
-
Yes pleas just attach.. Some of us are at work, and work proxy blocks access to such image hosting sites most of the time. I can not access those without bypass the proxy.. Which isn't all that hard - just a bit of a PITA ;)
-
@johnpoz said in VLAN Assistance:
Yes pleas just attach.. Some of us are at work, and work proxy blocks access to such image hosting sites most of the time. I can not access those without bypass the proxy.. Which isn't all that hard - just a bit of a PITA ;)
I had to do a shift reload to see it the second time :)
-
-
It seems like it's a rule problem but I'm really not sure. DHCP for the vlan works, the clients get an IP but nothing else besides that work, can't hit the admin page for pfsense and no internet access. Looking at my rules I'm sure I need to clean them up but getting this vlan thing figured out would be so great right now. I'm about to start locking down the network.
-
Why do you have all those manual mappings in your outbound nat that duplicate your automatic?
What is your vlan 12 interface settings.. Can your wireless clients on this vlan even ping your pfsense IP on this interface? You have a any any rule so they should be able to get to pfsense.
Are you running unifi controller? I was not aware that they allow for their phone app to set ssid with vlan IDs on them? Thought that had to be done in the controller?
Been running unifi and pfsense for years. Run multiple vlans on mine and also even got their MAB working on their psk networks with freerad, etc. This is clickity clickity stuff so missing something stupid for sure.
-
Do you have any sort of device you can connect to the pfSense port that supports VLANS so you could rule out the AP?
You can with a MAC:-
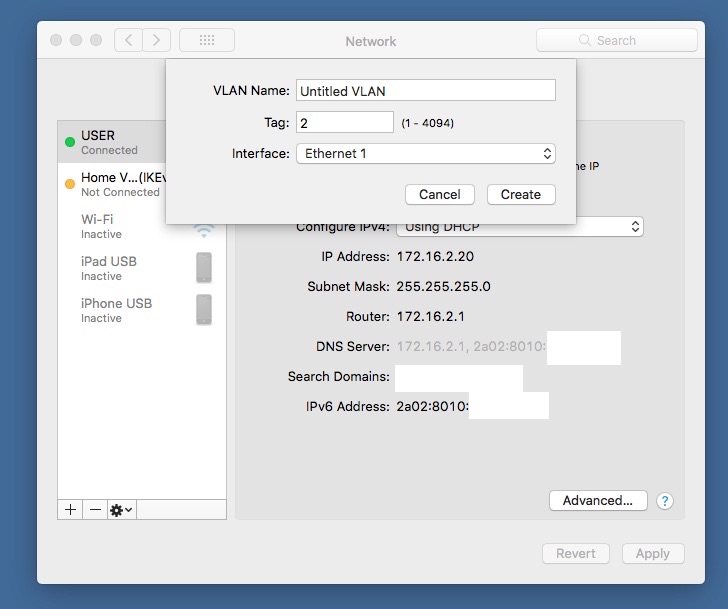
Choose Apple menu > System Preferences, then click Network. Click the Action pop-up menu at the bottom of the list on the left, then choose Manage Virtual Interfaces. Click the Add button , then choose New VLAN. Give the service a name, then enter a value in the Tag field.
Also I'd not open my NAS up to the internet unless I had a very good reason.
-
I removed the additional rules. May have been left overs of some other crazy idea I had.
Here is the configuration for interface vlan 12 aka KdsWiFi
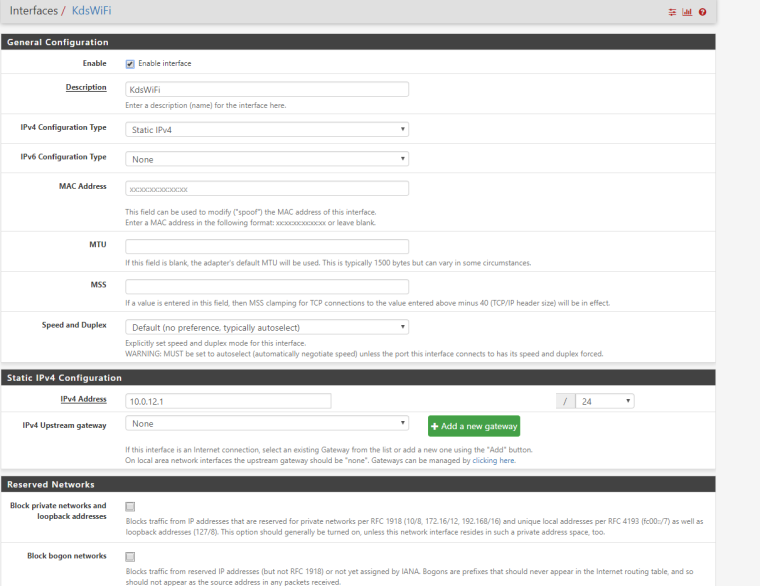
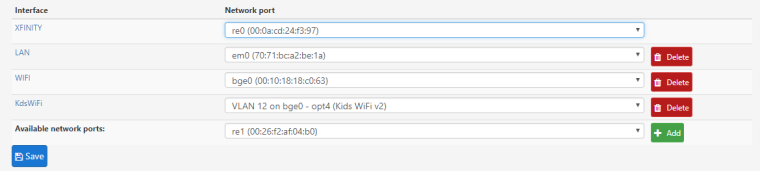
Yes, I am using a unifi controller. Since that's wired, thats on another IP range but I've opened the rules to allow bi-directional talks between the two.
Appreciate your feedback.
-
Originally this worked perfectly. I had two lan ports bridged and attached a vlan to the mix + a PoE managed switch. All was well with the world, then my PoE switch died. I saw online where someone has there AP setup on a dedicated LAN port and attached some vlans. I'm either an idiot or missing something in my setup.
Crazy thing is the clients get an IP, just no internet and I can't hit the admin page or pin the pfsense.
-
Getting DHCP and nothing else is the behaviour you see when there are no firewall rules on the interface.
Though you have added rules to pass that the behaviour indicates they may not be loading correctly.
Do you see any alerts shown in the GUI at the top of the page? None of your screenshots quite showed that.You might be hitting this:
https://forum.netgate.com/topic/129001/solved-2-4-3-rc-filter_configure_sync-cannot-define-table-bogonsv6Steve
-
@easysimpleit Stupid question but I remember it being of use previously: did you reboot pfSense?
-
@stephenw10 I’ve made the adjustment but haven’t tested it. I’ll get back to you
-
@jahonix I did not but I can. Let me try that.