Alerts for Remote VPN Access Use / Attempted Unautorized Use
-
I occasionally enable a remote access VPN server for which I am the only user (and rarely at that). AFAIK, It is well secured (TLS/UserAuth with Pass phrase on the device), but there is always the possibility of credentials being compromized .
Can anyone suggest a way that I can send an alert when there is a log in.
(I know how to send an email from a script, I don't know how to get the OpenVPN login info.)I would also be helpful for me to be able to detect unsuccessful attempts.
I'd also be very interested to know how much of a target a well configured VPN server is. It doesn't show in casual scans with a tool like GRC Shields Up. Are there any automated tools that detect and attempt to gain entry to remote VPN servers?
-
Hi,
Put your key on an USB stick, edit the opvn config file so it can find the file on the stick.
Done.I never disable my openvpn access - do not use fail2ban on pfSense, - do not use port knocking , and still feel safe.
I concentrate on one thing : not loosing my access keys (opvn client file).About the script : surely, they exist. As SSH access ports, easy to find. Just nmap the world.
All you need is the client software - and the keys (not user/password, these are disabled most of the time).If security is a real issue, rip out the wires, lock to box in a box, and shut it down. Only then you are approaching the something that could be considered as "safe" without risk.
-
Yeah, credentials compromise is extremely unlikely unless you're sloppy about handling your keys. I keep my OpenVPN server up all the time and there are some occasional knocks on the door but I don't care about it, there is zero chance anyone is going to break in without having actual access to my key files.
-
Hi Thanks for the replies:
Do login attempts (and/or failures) show up in a log? If so where? How can I view/grep from the shell?
Additional comments below:
@gertjan said in Alerts for Remote VPN Access Use / Attempted Unautorized Use:
Hi,
Put your key on an USB stick, edit the opvn config file so it can find the file on the stick.
Done.
Interesting idea..
I never disable my openvpn access - do not use fail2ban on pfSense, - do not use port knocking , and still feel safe.
I concentrate on one thing : not loosing my access keys (opvn client file).About the script : surely, they exist. As SSH access ports, easy to find. Just nmap the world.
All you need is the client software - and the keys (not user/password, these are disabled most of the time).If security is a real issue, rip out the wires, lock to box in a box, and shut it down. Only then you are approaching the something that could be considered as "safe" without risk.
Security is always a tradeoff between convenience and safety. I agree that unless someone has the key it is very unlikely they will gain access unless there is a bad vulnerability or backdoor in OpenVPN,.
@kpa said in Alerts for Remote VPN Access Use / Attempted Unautorized Use:
Yeah, credentials compromise is extremely unlikely unless you're sloppy about handling your keys. I keep my OpenVPN server up all the time and there are some occasional knocks on the door but I don't care about it, there is zero chance anyone is going to break in without having actual access to my key files.
I agree, even a 1024 bit key would be impossible to brute force by a random attacker (would need packet capture and analysis), so I'm not overly worried about anything other than theft of the key without my knowledge.
I use an android phone for access, which I consider to be the weakest link in the security chain-I try to make my configuration as "private" as possible, but it's impossible to know what sort of nonsense is going on with Android.
If my key were stolen and an attempt were made to use it, I would want to know ASAP which is why I want to be able to detect a login and send an alert.
When you say knocks on the door, I'm assuming you are meaning someone just probing your public IP, not specifically examining or attempting to brute force your VPN?
-
The knocks on the door are these:
Jun 5 11:20:28 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.54:37858 Jun 5 01:37:05 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]181.215.195.234:33233 Jun 4 23:08:06 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.58:47797 Jun 4 11:47:42 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.49:43737 Jun 4 00:39:35 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.72:57980 Jun 3 12:31:19 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.50:35658As you can see I'm using a TLS keys for HMAC stamping the UDP packets. I'm not 100% sure but with this set up you should be practically invisible to probing because the server should silently drop any incoming UDP packets that do not have the proper HMAC signatures and the prober shouldn't get any replies to their connection attempts. Brute forcing would be out the question even without HMAC because nobody is going to brute force attack the certificate validation process.
-
@kpa said in Alerts for Remote VPN Access Use / Attempted Unautorized Use:
The knocks on the door are these:
Jun 5 11:20:28 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.54:37858 Jun 5 01:37:05 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]181.215.195.234:33233 Jun 4 23:08:06 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.58:47797 Jun 4 11:47:42 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.49:43737 Jun 4 00:39:35 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.72:57980 Jun 3 12:31:19 openvpn 395 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.50:35658As you can see I'm using a TLS keys for HMAC stamping the UDP packets. I'm not 100% sure but with this set up you should be practically invisible to probing because the server should silently drop any incoming UDP packets that do not have the proper HMAC signatures and the prober shouldn't get any replies to their connection attempts. Brute forcing would be out the question even without HMAC because nobody is going to brute force attack the certificate validation process.
Thanks for the info - That's the configuration set up like this correct?
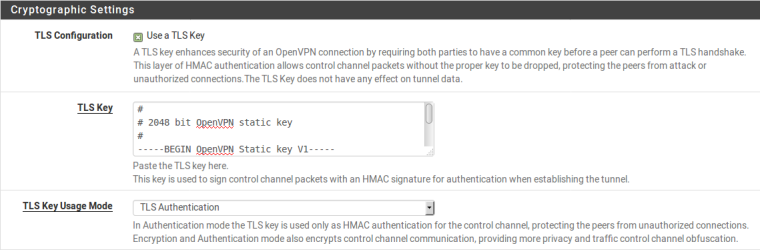
What file did you get those log entries from?
(and how can I do it from the shell? I assume I need to use clog?)I would assume that there is also a log entry for successful authentication?
I wouldn't think it should be too difficult to search for the login string and fire off an email on successful login. If my key does get used improperly, I'll hopefully be able to get it revoked before too much damage is done. (I severely limit access to anything sensitive, and most files are readonly access).
-
You are better off shipping the logs off to a log server that is designed to evaluate and alert based on criteria you set.
-
@derelict said in Alerts for Remote VPN Access Use / Attempted Unautorized Use:
You are better off shipping the logs off to a log server that is designed to evaluate and alert based on criteria you set.
Any practical (free or almost free) solution for this?
I run a small network with a FreeNAS server and a handful of PCs. pfSense IS my log server since it is the only system guaranteed to be up (if it isn't I don't have a network, and if I'm on vacation, I may have only IoT devices + pfSense running).
-
Graylog is free.
Awesome, but pfSense is not a log server. It is a firewall.
-
When I inspected my "pfSense" logs - I'm using a remote (but local) log server, I do see lines like :
06-06-2018 12:00:12 Daemon.Notice 192.168.1.1 Jun 6 12:00:14 openvpn[32669]: 80.12.41.173:55353 [GertjaniPhone] Peer Connection Initiated with [AF_INET]80.12.41.173:55353when I loggin with a VPN client on my VPN server (== pfSense).
Scripting against the log file with tools like fail2ban (or whatever hand written shell script) and you have your notification mail.
As @Derelict : I'm not keeping the logs (+100 Kbytes every day) on pfSense.
You have a FreeNAS system, so I guess you're close to a good solution. -
@derelict said in Alerts for Remote VPN Access Use / Attempted Unautorized Use:
Graylog is free.
Awesome, but pfSense is not a log server. It is a firewall.
Thanks for passing this along - Do you use it? I'm wondering what you do (if your use case is similar - Home/Home Office-A few PCs, a couple of "Smart Devices/Media Players/IoT or similar)
or are you running a large network.I would absolutely agree that it's not ideal as a log server and wouldn't work for a large setup.
@gertjan said in Alerts for Remote VPN Access Use / Attempted Unautorized Use:
When I inspected my "pfSense" logs - I'm using a remote (but local) log server, I do see lines like :
06-06-2018 12:00:12 Daemon.Notice 192.168.1.1 Jun 6 12:00:14 openvpn[32669]: 80.12.41.173:55353 [GertjaniPhone] Peer Connection Initiated with [AF_INET]80.12.41.173:55353when I loggin with a VPN client on my VPN server (== pfSense).
Scripting against the log file with tools like fail2ban (or whatever hand written shell script) and you have your notification mail.
That's what I had in mind!
As @Derelict : I'm not keeping the logs (+100 Kbytes every day) on pfSense.
You have a FreeNAS system, so I guess you're close to a good solution.
If you have a similar use case to me, what software are you using?This discussion has caused me to consider creating a log server on my FreeNAS.
Certainly I have the capacity to do it, just worried the learning curve for these other
tools may be too steep given my time constraints. Unless I have hardware issues
FreeNAS is always running when the other PCs are running and analysis/monitoring
is badly needed.I think for OpenVPN I will stick with a simple script on /var/log/openvpn.log - maybe
a bit of python. OpenVPN might be running when FreeNAS is down, so I'd rather
have this simple bit of monitoring locally.