No IP Alias/Group defined from Feed?
-
Running pfBlockerNG-deve 2.2.1
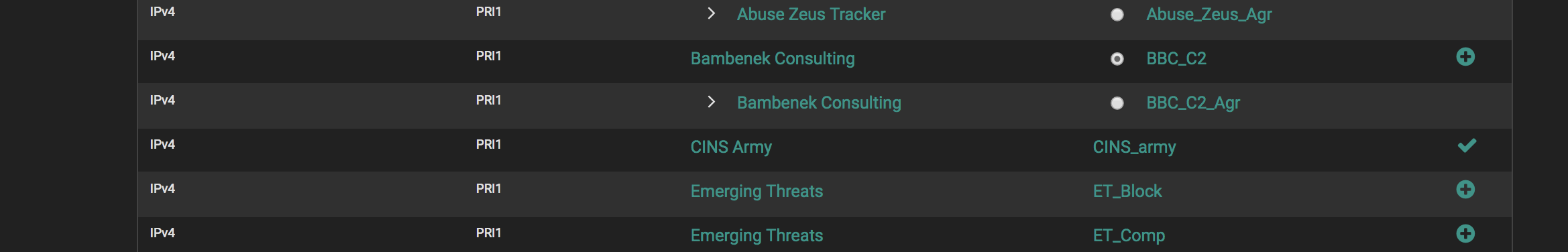
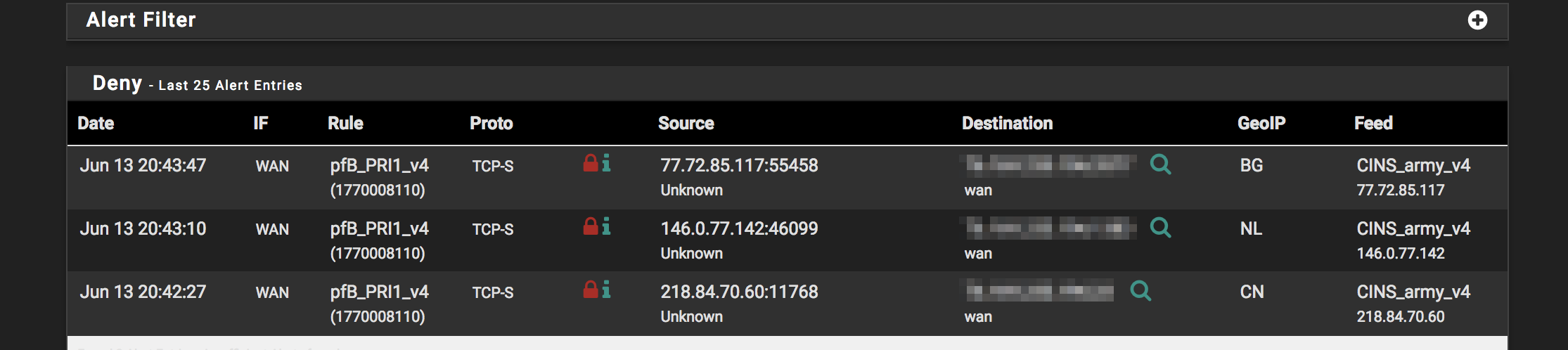
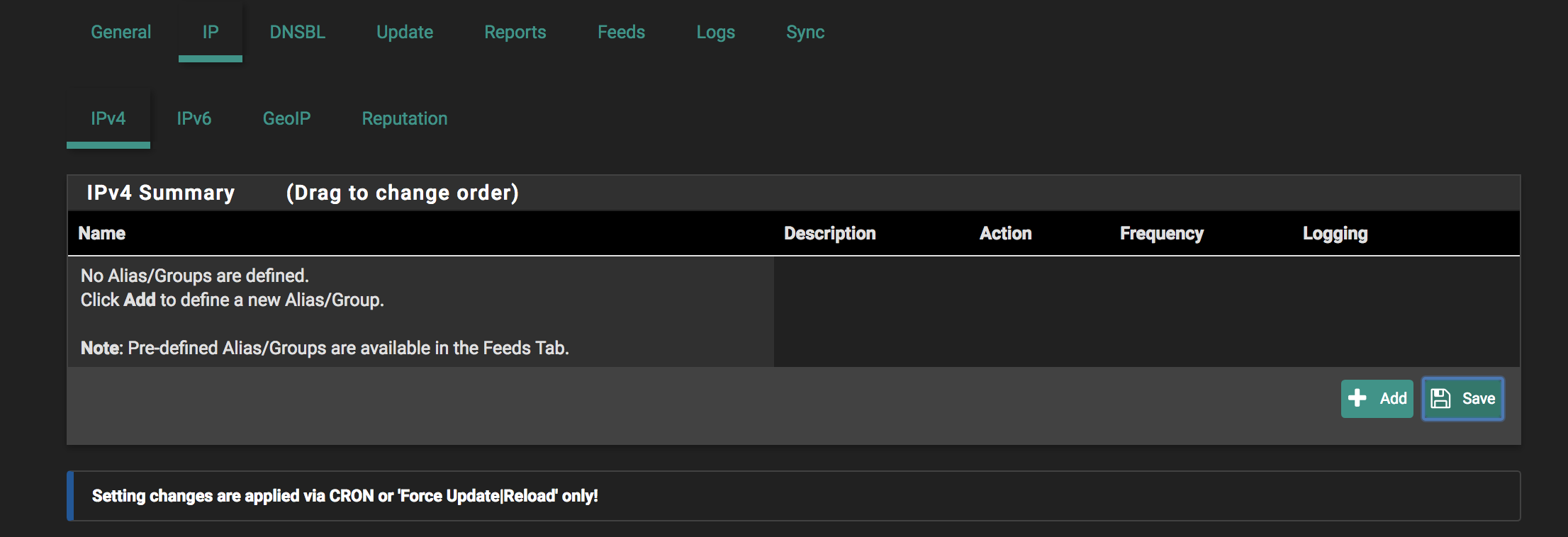
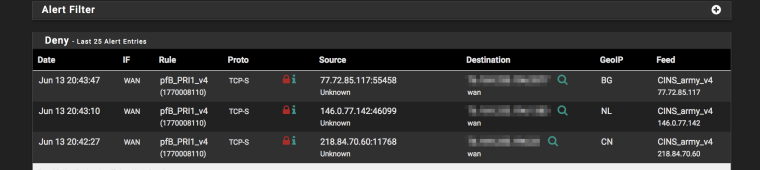
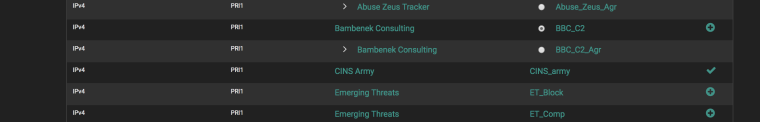
I have created an IP IPv4 block from the Feeds tab (CINS_Army) and it does not show up in the IP/IPv4 list. See pics. I know it is working as I can see blocks from it.
Should it be appearing in the list (IP/IPv4)?
If it is not supposed to appear here, how does it get removed if I want to turn off/remove it?
.
.
-
Bump...
-
Can you force a reload of the IP addreses from the pfBlockerNG update tab.
-
Did that a few times, and just now again. The reload completes fine, but still no Alias/Group entry shows in the IPv4 Summary.
Here's the output if it matters:
UPDATE PROCESS START [ 06/15/18 09:06:55 ] ===[ DNSBL Process ]================================================ Loading DNSBL Statistics... completed Loading DNSBL Whitelist... completed [ EasyList ] exists. [ Adaway ] exists. [ D_Me_ADs ] exists. [ D_Me_Tracking ] exists. [ hpHosts_ATS ] exists. [ Cameleon ] exists. [ SBL_ADs ] exists. [ Yoyo ] exists. [ Abuse_DOMBL ] exists. [ Abuse_URLBL ] exists. [ Abuse_urlhaus ] exists. [ Abuse_Zeus_BD ] exists. [ BBC_DC2 ] exists. [ Botvrij_Dom ] exists. [ Ponmocup ] exists. [ CCT_BD ] exists. [ SWC ] exists. [ D_Me_Malv ] exists. [ D_Me_Malw ] exists. [ H3X_1M ] exists. [ ISC_SDL ] exists. [ Malc0de ] exists. [ MDS ] exists. [ MDS_Immortal ] exists. [ MDL ] exists. [ MVPS ] exists. [ Spam404 ] exists. [ SFS_Toxic_BD ] exists. [ VXVault ] exists. [ hpHosts_EMD ] exists. [ hpHosts_EXP ] exists. [ hpHosts_FSA ] exists. [ hpHosts_GRM ] exists. [ hpHosts_HFS ] exists. [ hpHosts_MMT ] exists. [ hpHosts_PHA ] exists. [ hpHosts_PSH ] exists. [ hpHosts_PUP ] exists. [ hpHosts_WRZ ] exists. [ MS_2 ] exists. [ BBC_DGA_Agr ] exists. [ CoinBlocker_All ] exists. [ CoinBlocker_Opt ] exists. [ MoneroMiner ] exists. [ NoCoin ] exists. Saving DNSBL database... completed ===[ GeoIP Process ]============================================ ===[ IPv4 Process ]================================================= [ CINS_army_v4 ] Reload [ 06/15/18 09:06:56 ] . completed .. ===[ IPv6 Process ]================================================= ===[ Aliastables / Rules ]========================================== No changes to Firewall rules, skipping Filter Reload Updating: pfB_PRI1_v4 no changes. ===[ Kill States ]================================================== Firewall state(s) validation for [ 56 ] IPv4 address(es)... No matching states found ====================================================================== ===[ FINAL Processing ]===================================== [ Original IP count ] [ 15000 ] ===[ Deny List IP Counts ]=========================== 15000 /var/db/pfblockerng/deny/CINS_army_v4.txt ===[ DNSBL Domain/IP Counts ] =================================== 1545135 total 812936 /var/db/pfblockerng/dnsbl/BBC_DGA_Agr.txt 191246 /var/db/pfblockerng/dnsbl/hpHosts_FSA.txt 157561 /var/db/pfblockerng/dnsbl/hpHosts_PSH.txt 152030 /var/db/pfblockerng/dnsbl/hpHosts_EMD.txt 43443 /var/db/pfblockerng/dnsbl/hpHosts_ATS.txt 27890 /var/db/pfblockerng/dnsbl/hpHosts_PUP.txt 21529 /var/db/pfblockerng/dnsbl/MDS.txt 14752 /var/db/pfblockerng/dnsbl/EasyList.txt 14716 /var/db/pfblockerng/dnsbl/MS_2.txt 14596 /var/db/pfblockerng/dnsbl/Cameleon.txt 14236 /var/db/pfblockerng/dnsbl/SFS_Toxic_BD.txt 13403 /var/db/pfblockerng/dnsbl/hpHosts_PHA.txt 9681 /var/db/pfblockerng/dnsbl/SWC.txt 8563 /var/db/pfblockerng/dnsbl/CCT_BD.txt 7738 /var/db/pfblockerng/dnsbl/Abuse_URLBL.txt 7002 /var/db/pfblockerng/dnsbl/Spam404.txt 6360 /var/db/pfblockerng/dnsbl/Abuse_urlhaus.txt 5490 /var/db/pfblockerng/dnsbl/CoinBlocker_All.txt 3985 /var/db/pfblockerng/dnsbl/hpHosts_MMT.txt 2596 /var/db/pfblockerng/dnsbl/MDS_Immortal.txt 2255 /var/db/pfblockerng/dnsbl/D_Me_ADs.txt 2047 /var/db/pfblockerng/dnsbl/hpHosts_WRZ.txt 1899 /var/db/pfblockerng/dnsbl/Abuse_DOMBL.txt 1440 /var/db/pfblockerng/dnsbl/ISC_SDL.txt 1144 /var/db/pfblockerng/dnsbl/hpHosts_EXP.txt 1082 /var/db/pfblockerng/dnsbl/MDL.txt 1015 /var/db/pfblockerng/dnsbl/D_Me_Malv.txt 929 /var/db/pfblockerng/dnsbl/MVPS.txt 701 /var/db/pfblockerng/dnsbl/BBC_DC2.txt 552 /var/db/pfblockerng/dnsbl/hpHosts_HFS.txt 527 /var/db/pfblockerng/dnsbl/hpHosts_GRM.txt 496 /var/db/pfblockerng/dnsbl/SBL_ADs.txt 402 /var/db/pfblockerng/dnsbl/Adaway.txt 311 /var/db/pfblockerng/dnsbl/Yoyo.txt 263 /var/db/pfblockerng/dnsbl/CoinBlocker_Opt.txt 139 /var/db/pfblockerng/dnsbl/Ponmocup.txt 49 /var/db/pfblockerng/dnsbl/Botvrij_Dom.txt 43 /var/db/pfblockerng/dnsbl/Abuse_Zeus_BD.txt 28 /var/db/pfblockerng/dnsbl/D_Me_Tracking.txt 20 /var/db/pfblockerng/dnsbl/NoCoin.txt 16 /var/db/pfblockerng/dnsbl/H3X_1M.txt 13 /var/db/pfblockerng/dnsbl/Malc0de.txt 8 /var/db/pfblockerng/dnsbl/VXVault.txt 3 /var/db/pfblockerng/dnsbl/MoneroMiner.txt 0 /var/db/pfblockerng/dnsbl/D_Me_Malw.txt ====================[ IPv4/6 Last Updated List Summary ]============== Jun 15 08:20 CINS_army_v4 ====================[ DNSBL Last Updated List Summary ]============== Jul 31 2015 D_Me_Tracking Mar 9 2016 D_Me_ADs Jan 19 17:42 hpHosts_HFS Jan 20 10:32 Adaway Mar 18 02:51 Cameleon Mar 19 15:51 ISC_SDL Apr 4 23:38 hpHosts_MMT Apr 15 02:34 MVPS May 9 03:18 hpHosts_GRM May 25 01:53 hpHosts_EXP Jun 6 17:10 EasyList Jun 6 17:14 Abuse_Zeus_BD Jun 6 23:58 MDL Jun 7 08:15 Spam404 Jun 7 08:15 CoinBlocker_All Jun 7 08:15 CoinBlocker_Opt Jun 7 08:15 MoneroMiner Jun 8 11:21 UnifiedGamblingPorn Jun 9 01:14 Botvrij_Dom Jun 9 11:56 hpHosts_ATS Jun 9 16:48 hpHosts_WRZ Jun 11 00:03 MS_2 Jun 11 03:17 hpHosts_PUP Jun 12 12:57 Yoyo Jun 12 14:20 MDS_Immortal Jun 13 00:05 NoCoin Jun 13 22:16 SWC Jun 14 06:10 Malc0de Jun 14 06:11 SBL_ADs Jun 14 10:21 hpHosts_PSH Jun 14 14:39 MDS Jun 14 17:06 hpHosts_PHA Jun 14 17:15 BBC_DGA_Agr Jun 14 18:08 hpHosts_EMD Jun 14 18:09 hpHosts_FSA Jun 14 23:14 BBC_DC2 Jun 14 23:21 D_Me_Malw Jun 14 23:21 D_Me_Malv Jun 14 23:55 Abuse_urlhaus Jun 14 23:55 Abuse_URLBL Jun 14 23:55 Abuse_DOMBL Jun 14 23:57 SFS_Toxic_BD Jun 15 00:01 CCT_BD Jun 15 00:01 H3X_1M Jun 15 00:02 VXVault Jun 15 00:33 Ponmocup Alias table IP Counts ----------------------------- 15000 /var/db/aliastables/pfB_PRI1_v4.txt pfSense Table Stats ------------------- table-entries hard limit 2000000 Table Usage Count 18572 UPDATE PROCESS ENDED [ 06/15/18 09:06:59 ] -
rm /var/db/aliastables/pfB_PRI1_v4.txt rm /var/db/pfblockerng/original/CIArmy_v4.orig rm /var/db/pfblockerng/deny/CIArmy_v4.txtThen reload again, that should fully remove all of CIArmy.
Another way would be to add back CINS_army feed from the feeds tab, set the update options for the PRI1 IPv4 list. Force an update then go back and delete the PRI1 IPV4 group.
-
Can you create any IPV4 table ? Maybe you config.xml is borked.
-
Interesting, after adding a 'test' Alias/group the CINS_Army entry now shows.
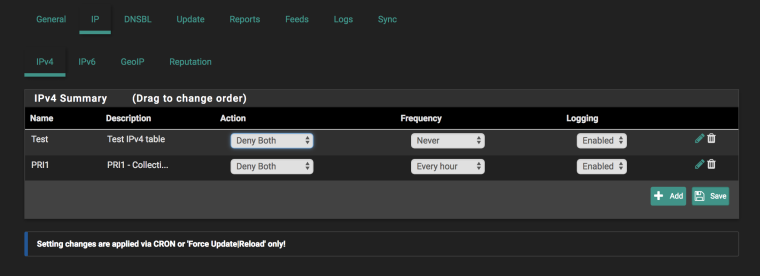
I deleted the 'test' entry and the CINS_Army is maintained in the list it seems. Maybe it was the config.xml being re-written?
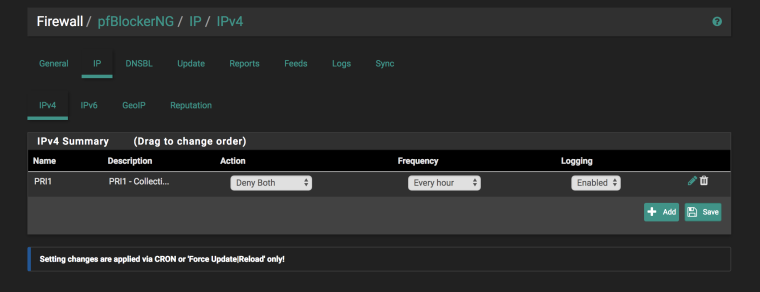
-
@ar15usr said in No IP Alias/Group defined from Feed?:
Interesting, after adding a ‘test’ Alias/group the CINS_Army entry now shows.
 Maybe a specific case of a new installation.
Maybe a specific case of a new installation.Can you keep a copy ( Diagnostics / Backup & Restore / Config History) of the config.xml before installation, after installation and the one after adding the feed from the Feeds Tab and maybe the one before the Test table and the one you have now in case BBcan177 need them to debug the code.
-
Looks like its too late for the installation configs. I'll try and save before/after the feeds setup..
-
What does this command report?
grep -A30 "<pfblockernglistsv4" /conf/config.xmlLooks like there might be an empty <config></config> tag causing issues...
-
<pfblockernglistsv4> <config> <aliasname>PRI1</aliasname> <description><![CDATA[PRI1 - Collection of Feeds from the most reputable blocklist providers. (Primary tier)]]></description> <action>Deny_Outbound</action> <cron>01hour</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> -
@bbcan17 said in No IP Alias/Group defined from Feed?:
grep -A30
Increase the A count in the Grep command until you get to "</pfblockernglistsv4>" which is the end XML tag. Then we can tell if there are any empty tags.
-
I have noticed the same issue, here is my Grep output. Hope it helps.
<pfblockernglistsv4> <config></config> <config> <aliasname>PRI1</aliasname> <description><![CDATA[PRI1 - Collection of Feeds from the most reputable blocklist providers. (Primary tier)]]></description> <action>Deny_Both</action> <cron>01hour</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://sslbl.abuse.ch/blacklist/dyre_sslipblacklist.csv</url> <header>Abuse_DYRE</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://feodotracker.abuse.ch/blocklist/?download=badips</url> <header>Feodo_BadIPs</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://feodotracker.abuse.ch/blocklist/?download=ipblocklist</url> <header>Feodo_Block</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://ransomwaretracker.abuse.ch/downloads/RW_IPBL.txt</url> <header>Abuse_IPBL</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://sslbl.abuse.ch/blacklist/sslipblacklist.csv</url> <header>Abuse_SSLBL</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://zeustracker.abuse.ch/blocklist.php?download=badips</url> <header>Abuse_Zeus</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://osint.bambenekconsulting.com/feeds/c2-ipmasterlist-high.txt</url> <header>BBC_C2</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://cinsarmy.com/list/ci-badguys.txt</url> <header>CINS_army</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt</url> <header>ET_Block</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://rules.emergingthreats.net/blockrules/compromised-ips.txt</url> <header>ET_Comp</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://isc.sans.edu/api/sources/attacks/1000/30?text</url> <header>ISC_1000_30</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://isc.sans.edu/feeds/block.txt</url> <header>ISC_Block</header> </row> <row> <format>auto</format> <state><![CDATA[Disabled]]></state> <url>https://pulsedive.com/premium?key=_API_KEY_&types=ip</url> <header>Pulsedive</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.spamhaus.org/drop/drop.txt</url> <header>Spamhaus_Drop</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.spamhaus.org/drop/edrop.txt</url> <header>Spamhaus_eDrop</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.talosintelligence.com/feeds/ip-filter.blf</url> <header>Talos_BL</header> </row> </config> <config> <aliasname>PRI2</aliasname> <description><![CDATA[PRI2 - Collection of Feeds from Secondary Tier providers.]]></description> <action>Deny_Both</action> <cron>01hour</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://reputation.alienvault.com/reputation.snort.gz</url> <header>Alienvault</header> </row> </config> <config> <aliasname>PRI3</aliasname> <description><![CDATA[PRI3 - Collection of Feeds from Tertiary Tier providers.]]></description> <action>Deny_Both</action> <cron>01hour</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Disabled]]></state> <url>https://www.autoshun.org/download/?api_key=_API_KEY_&format=csv</url> <header>Shunlist</header> </row> <row> <format>auto</format> <state><![CDATA[Disabled]]></state> <url>https://lists.blocklist.de/lists/all.txt</url> <header>BlockListDE_All</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://botscout.com/last_caught_cache.txt</url> <header>BotScout</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://danger.rulez.sk/projects/bruteforceblocker/blist.php</url> <header>DangerRulez</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://blocklist.greensnow.co/greensnow.txt</url> <header>GreenSnow</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.juniper.net/security/auto/spam</url> <header>Juniper</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.malwaredomainlist.com/hostslist/ip.txt</url> <header>MDL</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.maxmind.com/en/high-risk-ip-sample-list</url> <header>MaxMind_BD_Proxy</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://www.nothink.org/blacklist/blacklist_malware_dns.txt</url> <header>NoThink_DNS</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://www.nothink.org/blacklist/blacklist_malware_http.txt</url> <header>NoThink_HTTP</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://www.nothink.org/blacklist/blacklist_malware_irc.txt</url> <header>NoThink_IRC</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://www.nothink.org/blacklist/blacklist_ssh_week.txt</url> <header>NoThink_SSH</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://www.nothink.org/blacklist/blacklist_snmp_week.txt</url> <header>NoThink_SNMP</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://www.nothink.org/blacklist/blacklist_telnet_week.txt</url> <header>NoThink_Telnet</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.stopforumspam.com/downloads/toxic_ip_cidr.txt</url> <header>SFS_Toxic</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://suspect-networks.io/downloads/suspect_networks.txt</url> <header>SuspectNetworks</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://www.reputationauthority.org/toptens.php</url> <header>WatchGuard</header> </row> </config> <config> <aliasname>PRI4</aliasname> <description><![CDATA[PRI4 - Collection of Feeds from Fourth Tier providers.]]></description> <action>Deny_Both</action> <cron>01hour</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.badips.com/get/list/any/2?age=30d</url> <header>BadIPs_30d</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.binarydefense.com/banlist.txt</url> <header>BDS_Ban</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.botvrij.eu/data/ioclist.ip-dst.raw</url> <header>Botvrij_IP</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://cybercrime-tracker.net/fuckerz.php</url> <header>CCT_IP</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.darklist.de/raw.php</url> <header>Darklist</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://isc.sans.edu/api/threatlist/miner</url> <header>ISC_Miner</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://malc0de.com/bl/IP_Blacklist.txt</url> <header>Malc0de</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://malwaredb.malekal.com/export.php?type=url</url> <header>Malekal_BL</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.myip.ms/files/blacklist/csf/latest_blacklist.txt</url> <header>Myip_BL</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://www.ipspamlist.com/public_feeds.csv</url> <header>NVT_BL</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://zerodot1.gitlab.io/CoinBlockerLists/MiningServerIPList.txt</url> <header>CoinBlocker</header> </row> </config> <config> <aliasname>PRI5</aliasname> <description><![CDATA[PRI5 - Collection of Feeds from Fifth Tier providers.]]></description> <action>Deny_Both</action> <cron>EveryDay</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://gist.githubusercontent.com/BBcan177/bf29d47ea04391cb3eb0/raw</url> <header>MS_1</header> </row> </config> <config> <aliasname>SFS</aliasname> <description><![CDATA[SFS - Stop Forum Spam]]></description> <action>Deny_Both</action> <cron>08hours</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Disabled]]></state> <url>https://www.stopforumspam.com/downloads/bannedips.zip</url> <header>SFS_IPs</header> </row> </config> <config> <aliasname>TOR</aliasname> <description><![CDATA[TOR - Collection of Feeds for the TOR network.]]></description> <action>Deny_Both</action> <cron>01hour</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.binarydefense.com/tor.txt</url> <header>BDS_TOR</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://rules.emergingthreats.net/blockrules/emerging-tor.rules</url> <header>ET_TOR_All</header> </row> </config> <config> <aliasname>MAIL</aliasname> <description><![CDATA[MAIL - Collection of Feeds for Mail Server specific blocklists.]]></description> <action>Deny_Both</action> <cron>01hour</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://antispam.imp.ch/spamlist</url> <header>Improware</header> </row> <row> <format>auto</format> <state><![CDATA[Disabled]]></state> <url>https://www.unsubscore.com/blacklist.txt</url> <header>LB_BL</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://www.dnsbl.manitu.net/download/nixspam-ip.dump.gz</url> <header>Nix_Spam</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.spamcop.net/w3m?action=map;net=cmaxratio;mask=65535;sort=spamcnt;format=text</url> <header>SpamCop_SC</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>http://toastedspam.com/deny</url> <header>Toastedspam</header> </row> </config> <config> <aliasname>Internic_4</aliasname> <description><![CDATA[Internic - List of the 13 IPv4 Root DNS servers via Internic Domain Registration service.]]></description> <action>Permit_Outbound</action> <cron>Weekly</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.internic.net/domain/named.root</url> <header>Resolver4</header> </row> </config> <config> <aliasname>BlockListDE</aliasname> <description><![CDATA[Collection of specific fail2ban reporting service Feeds.]]></description> <action>Deny_Both</action> <cron>01hour</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://lists.blocklist.de/lists/apache.txt</url> <header>BlockListDE_Apache</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.blocklist.de/lists/asterisk.txt</url> <header>BlockListDE_Asterisk</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://lists.blocklist.de/lists/bots.txt</url> <header>BlockListDE_Bots</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://lists.blocklist.de/lists/bruteforcelogin.txt</url> <header>BlockListDE_Brute</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.blocklist.de/lists/email.txt</url> <header>BlockListDE_Email</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://lists.blocklist.de/lists/ftp.txt</url> <header>BlockListDE_FTP</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.blocklist.de/lists/proftpd.txt</url> <header>BlockListDE_FTPD</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.blocklist.de/lists/ircbot.txt</url> <header>BlockListDE_IRC</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://lists.blocklist.de/lists/imap.txt</url> <header>BlockListDE_IMAP</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://lists.blocklist.de/lists/mail.txt</url> <header>BlockListDE_Mail</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.blocklist.de/lists/pop3.txt</url> <header>BlockListDE_POP3</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://www.blocklist.de/lists/postfix.txt</url> <header>BlockListDE_Postfix</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://lists.blocklist.de/lists/sip.txt</url> <header>BlockListDE_SIP</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://lists.blocklist.de/lists/ssh.txt</url> <header>BlockListDE_SSH</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://lists.blocklist.de/lists/strongips.txt</url> <header>BlockListDE_Strong</header> </row> </config> <config> <aliasname>Abuse_PS</aliasname> <description><![CDATA[Abuse Ransomware Tracker - Payment Sites]]></description> <action>Deny_Both</action> <cron>01hour</cron> <dow>1</dow> <aliaslog>enabled</aliaslog> <stateremoval><![CDATA[enabled]]></stateremoval> <autoaddrnot_in></autoaddrnot_in> <autoports_in></autoports_in> <aliasports_in></aliasports_in> <autoaddr_in></autoaddr_in> <autonot_in></autonot_in> <aliasaddr_in></aliasaddr_in> <autoproto_in></autoproto_in> <agateway_in>default</agateway_in> <autoaddrnot_out></autoaddrnot_out> <autoports_out></autoports_out> <aliasports_out></aliasports_out> <autoaddr_out></autoaddr_out> <autonot_out></autonot_out> <aliasaddr_out></aliasaddr_out> <autoproto_out></autoproto_out> <agateway_out>default</agateway_out> <suppression_cidr>Disabled</suppression_cidr> <whois_convert></whois_convert> <custom></custom> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://ransomwaretracker.abuse.ch/downloads/CW_PS_IPBL.txt</url> <header>Abuse_CW_PS</header> </row> <row> <format>auto</format> <state><![CDATA[Enabled]]></state> <url>https://ransomwaretracker.abuse.ch/downloads/LY_PS_IPBL.txt</url> <header>Abuse_LY_PS</header> </row> </config> </pfblockernglistsv4> -
@morgion said in No IP Alias/Group defined from Feed?:
<pfblockernglistsv4>
<config></config>To fix that:
- Make a pfSense Backup of the config.xml
- Goto pfSense > Diagnostics > Edit File
- Enter "/conf/config/xml"
- Scroll down and find "<pfBlockernglistsv4>"
- Remove the line "<config></config>"
- Save
-
@bbcan177 said in No IP Alias/Group defined from Feed?:
/conf/config/xml
Worked both IPv4 & IPv6 List are now present, Thank you again for your help.
-
@bbcan177
Sorry, been away for the weekend...I'm seeing 11 of these empty configs. Should I change them all?
<pfblockernglistsv6> <config></config><pfblockerngafrica> <config></config> </pfblockerngafrica> <pfblockerngantarctica> <config></config> </pfblockerngantarctica> <pfblockerngasia> <config></config> </pfblockerngasia> <pfblockerngeurope> <config></config> </pfblockerngeurope> <pfblockerngnorthamerica> <config></config> </pfblockerngnorthamerica> <pfblockerngoceania> <config></config> </pfblockerngoceania> <pfblockerngsouthamerica> <config></config> </pfblockerngsouthamerica> <pfblockerngtopspammers> <config></config> </pfblockerngtopspammers> <pfblockerngproxyandsatellite> <config></config><pfblockerngreputation> <config></config> -
This post is deleted! -
@ar15usr said in No IP Alias/Group defined from Feed?:
Should I change them all?
No, those are normal when nothing is defined / configured for these entries.