unsupported certificate purpose
-
Im getting this error unsupported certificate purpose no matter what i do.
If i create a Server Certificate for a user i see this error on the server side (/var/log/openvpn.log). If i create a User Certificate for the same user i get this error on the Client side. Both OpenVPN configs are made with the build-in wizard which apply the firewall rules.
I have another pFSense (2.3.3-RELEASE) appliance which works perfectly with OpenVPN and was easy to setup.
I reinstalled this pFSense and compared the OpenVPN setup with the other pFSense server, but still this error comes up.pFSense version: 2.4.3-RELEASE-p1
OpenVPN version: 2.4.4Client Certificate config;
dev tun
persist-tun
persist-key
cipher AES-256-CBC
auth SHA1
tls-client
client
resolv-retry infinite
remote 149.210.XXX.XXX 4494 udp
verify-x509-name "rbs_cert_client" name
auth-user-pass
pkcs12 rbsfw01-UDP4-4494.p12
tls-auth rbsfw01-UDP4-4494-tls.key 1Client log;
Thu Jun 14 08:58:27 2018 VERIFY ERROR: depth=0, error=unsupported certificate purpose: C=NL, ST=Noord-Holland, L=Haarlem, O=RBS, emailAddress=info@test.nl, CN=rbs_cert_client, OU=ICT
Thu Jun 14 08:58:27 2018 OpenSSL: error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed
Thu Jun 14 08:58:27 2018 TLS_ERROR: BIO read tls_read_plaintext error
Thu Jun 14 08:58:27 2018 TLS Error: TLS object -> incoming plaintext read error
Thu Jun 14 08:58:27 2018 TLS Error: TLS handshake failedServer Certificate config;
dev tun
persist-tun
persist-key
cipher AES-256-CBC
auth SHA1
tls-client
client
resolv-retry infinite
remote 149.210.XXX.XXX 5594 udp
verify-x509-name "rbs_cert_server" name
auth-user-pass
pkcs12 rbsfw01-UDP4-5594.p12
tls-auth rbsfw01-UDP4-5594-tls.key 1
remote-cert-tls server/var/log/openvpn.log
Jun 13 21:34:39 rbsfw01 openvpn[15613]: 5.132.XXX.XXX:34986 VERIFY ERROR: depth=0, error=unsupported certificate purpose: C=NL, ST=Noord-Holland, L=Haarlem, O=RBS, emailAddress=info@test.nl, CN=CERT, subjectAltName=
Jun 13 21:34:39 rbsfw01 openvpn[15613]: 5.132.XXX.XXX:34986 OpenSSL: error:14089086:SSL routines:ssl3_get_client_certificate:certificate verify failed
Jun 13 21:34:39 rbsfw01 openvpn[15613]: 5.132.XXX.XXX:34986 TLS_ERROR: BIO read tls_read_plaintext error
Jun 13 21:34:39 rbsfw01 openvpn[15613]: 5.132.XXX.XXX:34986 TLS Error: TLS object -> incoming plaintext read error
Jun 13 21:34:39 rbsfw01 openvpn[15613]: 5.132.XXX.XXX:34986 TLS Error: TLS handshake failed
Jun 13 21:36:14 rbsfw01 openvpn[15613]: 5.132.XXX.XXX34986 VERIFY ERROR: depth=0, error=unsupported certificate purpose: C=NL, ST=Noord-Holland, L=Haarlem, O=RBS, emailAddress=info@test.nl, CN=RBS CERT, subjectAltName=
Jun 13 21:36:14 rbsfw01 openvpn[15613]: 5.132.XXX.XXX:34986 OpenSSL: error:14089086:SSL routines:ssl3_get_client_certificate:certificate verify failed
Jun 13 21:36:14 rbsfw01 openvpn[15613]: 5.132.XXX.XXX:34986 TLS_ERROR: BIO read tls_read_plaintext error
Jun 13 21:36:14 rbsfw01 openvpn[15613]: 5.132.XXX.XXX:34986 TLS Error: TLS object -> incoming plaintext read error
Jun 13 21:36:14 rbsfw01 openvpn[15613]: 5.132.XXX.XXX:34986 TLS Error: TLS handshake failed
Jun 13 21:36:44 rbsfw01 openvpn[43354]: 5.132.XXX.XXX:34986 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Jun 13 21:36:44 rbsfw01 openvpn[43354]: 5.132.XXX.XXX:34986 TLS Error: TLS handshake failedAny help is appreciated.
-
The server side must use a server certificate. The client side needs a user certificate. The client certificate can't be the same as the server certificate.
-
I tried both.
- Created a CA certificate
- Created a USER certificate
- Created a USER
- Added USER Certificate to USER
- Used OpenVPN Wizard to create openvpn files
This gives me a error on the CLIENT side: VERIFY ERROR: depth=0, error=unsupported certificate purpose
Removed all configs and certificates except CA
- Created a SERVER certificate
- Created a USER
- Added SERVER Certificate to USER
- Used OpenVPN Wizard to create openvpn files
This gives me the same error but on the SERVER side: VERIFY ERROR: depth=0, error=unsupported certificate purpose
Am i doing something wrong? I tried so much i dunno anymore.
-
You never said what you did on the server.
You need to create a server certificate and then select it in the OpenVPN server settings.
-
I used the server cert in the OpenVPN server setting;
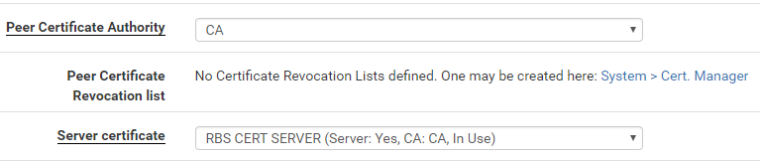
With this setting i get the unsupported certificate purpose on the server side (openvpn.log)
-
The server side should be OK then, provided you also have a user (NON-server) certificate on the client at the time.
If you try to use a server certificate on both it would fail, same as if you used a client certificate on the server. Both of those are unsupported purposes so it fails.
-
Ah ok.. i understand now..
I did the following now;
Removed the Server Cert from the User and added a User Certificate.
Then used openvpn wizard to create a new config. When im done the new config pops up in the server configs(?);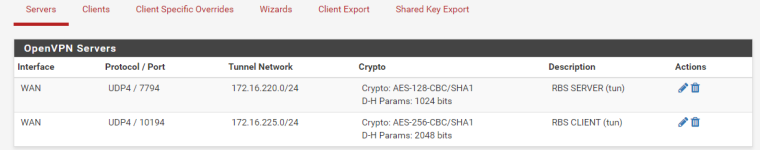
When i download the files and put them in the OpenVPN config folder and connect i still get this on the client side;
Thu Jun 14 17:09:12 2018 TLS Error: Unroutable control packet received from [AF_INET]149.210.180.XXX:10194 (si=3 op=P_CONTROL_V1)
Thu Jun 14 17:09:12 2018 VERIFY ERROR: depth=0, error=unsupported certificate purpose: C=NL, ST=Noord-Holland, L=Haarlem, O=RBS, emailAddress=info@test, CN=rbs_client, OU=ICT
Thu Jun 14 17:09:12 2018 OpenSSL: error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed
Thu Jun 14 17:09:12 2018 TLS_ERROR: BIO read tls_read_plaintext error
Thu Jun 14 17:09:12 2018 TLS Error: TLS object -> incoming plaintext read error
Thu Jun 14 17:09:12 2018 TLS Error: TLS handshake failedMaybe in version 2.3.3 everything worked different then in 2.4.4 or something because when i do exactly the same on the other pFSense box it works flawless...
-
Same here with 2.44 (it also works with the same certs in 2.3x).
Any hints?
-
Make and use the correct certificates for their role.
Certificates for the server must be server certificates. Certificates for users must be user certificates.
If you see this error, the configuration was always wrong, but OpenVPN was less strict about enforcing proper usage in the past.
-
@jimp said in unsupported certificate purpose:
Make and use the correct certificates for their role.
Certificates for the server must be server certificates. Certificates for users must be user certificates.
Ah, I see, this had been the problem to me also. No my VPN works (again). Thanks.
If you see this error, the configuration was always wrong, but OpenVPN was less strict about enforcing proper usage in the past.
When did that change? Although I usually try to read the changelogs completely, I do not remember having read about that.
-
@peter808 said in unsupported certificate purpose:
When did that change? Although I usually try to read the changelogs completely, I do not remember having read about that.
That would be a change in OpenVPN itself, not pfSense. Most likely when that changed to OpenVPN 2.4 (which by coincidence was new in pfSense 2.4.0 and later)