[SOLVED] All traffic (including internet) over site to site OpenVPN
-
Hello,
I am trying to set a site to site VPN with all traffic, but till now I was only able to access from remote office, local resourses with IP and local DNS server, in case of using internet, it doesnt go through VPN.
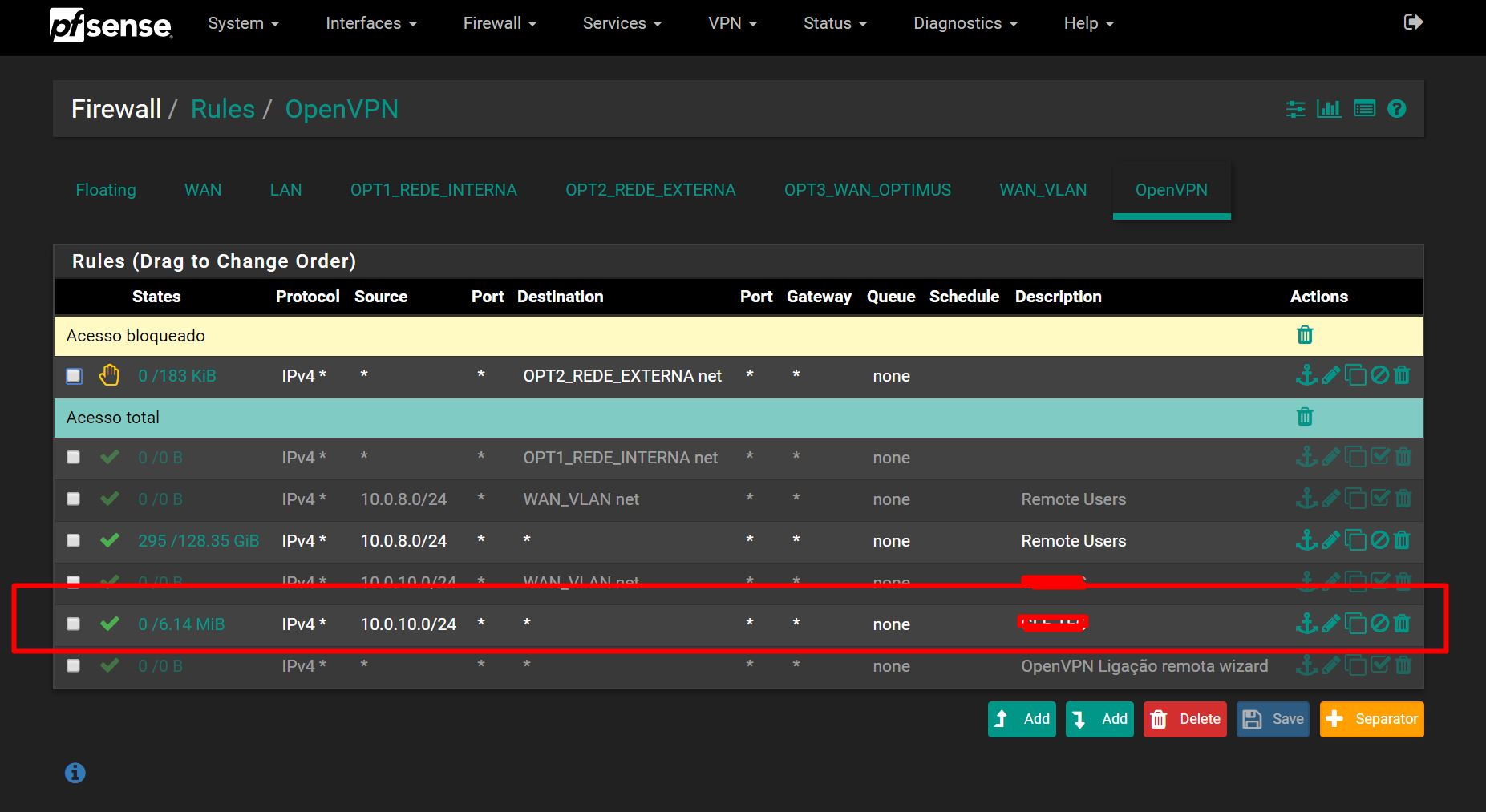
I have already created a NAT rule in Main site:
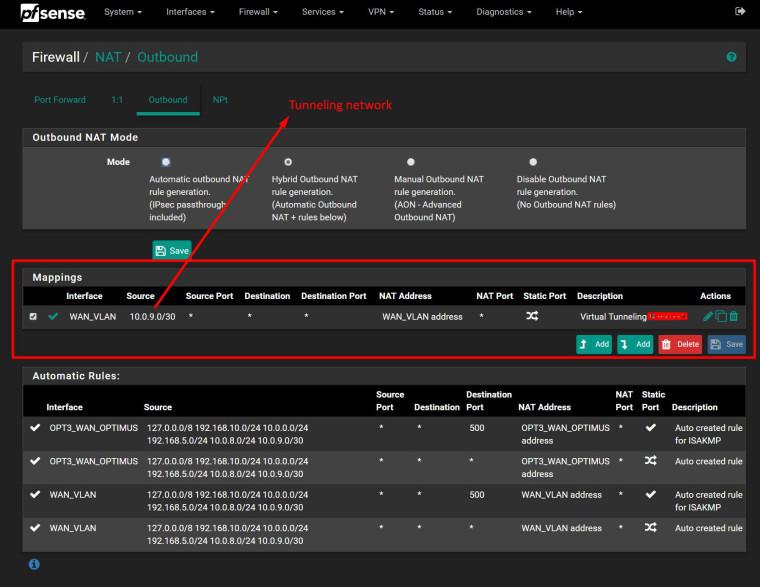
and also a rule for any destination,
Compared with my OpenVPN server for remote users, I have an option with,
Redirect IPv4 Gateway, Force all client-generated IPv4 traffic through the tunnel.
But with a peer to peer OpenVPN server I dont have that option.
I have followed this documentation: https://www.netgate.com/docs/pfsense/vpn/openvpn/routing-internet-traffic-through-a-site-to-site-openvpn-connection-in-pfsense-2-1.html
Anyone knows what do I need to do?
-
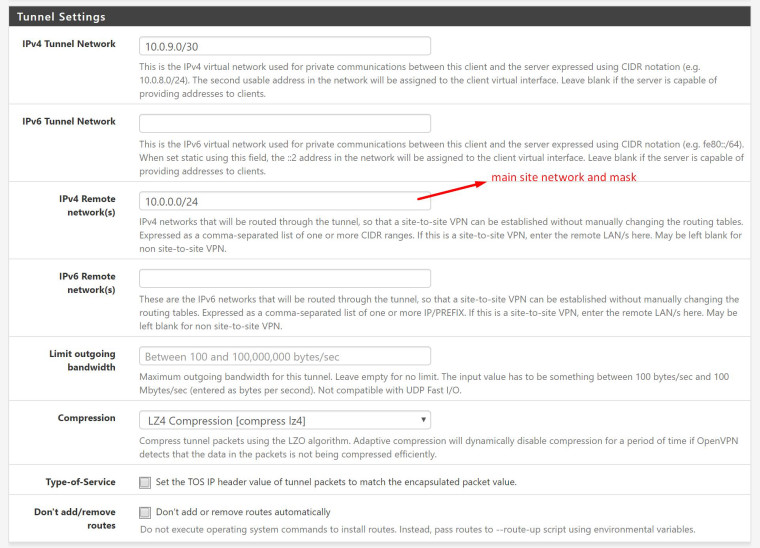
In the clients settings at "IPv4 Remote network(s)" enter "0.0.0.0/0" to set the default route.
If you also want to route IPv6 over the vpn enter "::/0" at "IPv6 Remote network(s)".
It will also be a good advice for your setup to assign interfaces to both vpn servers on the main site.
-
@viragomann said in All traffic (including internet) over site to site OpenVPN:
In the clients settings at “IPv4 Remote network(s)” enter “0.0.0.0/0” to set the default route.
If you also want to route IPv6 over the vpn enter “::/0” at “IPv6 Remote network(s)”.
It will also be a good advice for your setup to assign interfaces to both vpn servers on the main site.I have set IPv4 Remote network to 0.0.0.0/0 and without anything but I lose contact with main site. =/
Also I am not using IPv6.
Assign an interface per vpn server?
-
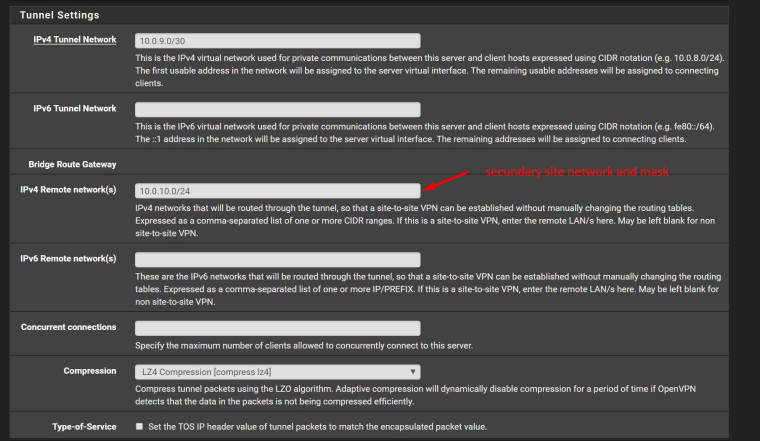
In main site I have this setup at Tunnel Settings:
-
On secundary site, in OpenVPN server:
-
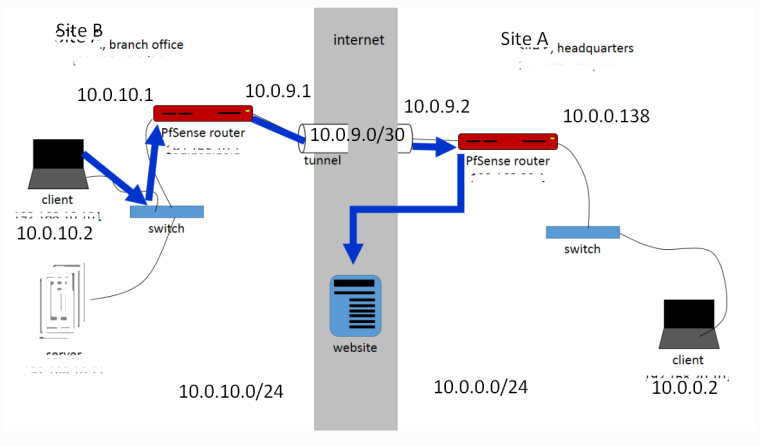
This is the scenario thata I am trying to accomplish:
-
Maybe the 0.0.0.0/0 route was a bad idea. When "Redirect gateway" is checked in the OpenVPN server settings, pfSense splits the default and sets two routing entries:
0.0.0.0/1
128.0.0.0/1
So you can try it with these two subnets. -
This post is deleted! -
@viragomann said in All traffic (including internet) over site to site OpenVPN:
Maybe the 0.0.0.0/0 route was a bad idea. When "Redirect gateway" is checked in the OpenVPN server settings, pfSense splits the default and sets two routing entries:
0.0.0.0/1
128.0.0.0/1
So you can try it with these two subnets.|-You are my Hero(!) Viragomann!!!-|
I have made lots of testing and read lots of documentation in past 3 days, using ping and traceroute with local and external IPs and FQDN, and I was ONLY able to achieve this doing in secundary OpenVPN side, IPv4 Remote network,
0.0.0.0/1,128.0.0.0/1
I notice that I was not able to pass all traffic with just 0.0.0.0/1 or 128.0.0.0/1, but only certain parts of traffic. With both I was able to pass all traffic.
Also in NAT Outbound at primary site, I have change the source to 10.0.10.0/24 for WAN address, who in this case was my WAN_VLAN address.
Thank you one more time!
Hope that this could help others trying to achieve the same.
-
0.0.0.0/0 = 0.0.0.0/1 + 128.0.0.0/1
Both are the whole IPv4 range. I don't know, why OpenVPN splits the range into two parts. Maybe this way it is applied with lower prio or cause the default route for 0.0.0.0/0 already points to the WAN gateway in most cases and FreeBSD has no metric option. -
@viragomann The reason for the split is that the two routes can be simply added to the routing table without touching the existing 0.0.0.0/0 route and removed to restore the old default route.
-
After setting this up, and installed this router in the remote side, after several days of testing I notice that there was a 50% decrease on internet speed, so I had to route just the traffic for my primary side, and leaving the remote side with his own uplink for internet.
From primary side to secundary, there is a distance of 30kms, and both have uplinks of 100/100 Mbps.
Here is the issue described:
https://forum.netgate.com/topic/133011/solved-loss-of-internet-speed-while-on-vpn-from-site-to-site