Firewall rules stop working.
-
Hi
We've an issue with a firewall rule stopping working, last time this happened we deleted and re added it and it worked fine.
It's happened again, but this time removing and re adding it hasn't worked.
The rule is a simple port redirect for 8081 to 80 and is setup in NAT Port Forward as :
Interface: WAN
Protocol: TCP/UDP
Source: Any
Source port range: any
Destination: Selected VIP
Destination port range: Other 8081 Other 8081
Redirect target IP: the required servers IP Address
Redirect target port: HTTP
NAT Reflection: Use system default
Filter rule association: PassCurrently this isn't working, but it has been.
A pcap captured on the firewall shows the destination IP sending [RST,ACK] back to us.We can access the destination direct on it's IP Port 80, but that is only open for specific IP Addresses
Any ideas why this has stopped and how we allow anyone to access port 80 on the destination via port 8081 ?
Thanks
-
@tomt said in Firewall rules stop working.:
The rule is a simple port redirect for 8081 to 80 and is setup in NAT Port Forward as :
Interface: WAN
Protocol: TCP/UDPOk up untill here. These two are new to me :
Source: Any
Source port range: anyYou clikced "Display advanced" to access them ?
Destination: Selected VIP
Destination is "WAN address" for me
The rest is default :
Destination port range: Other 8081 Other 8081
Redirect target IP: the required servers IP Address
Redirect target port: HTTP
NAT Reflection: Use system default
Filter rule association: Pass -
Thanks for your reply.
I didn't click on 'Display Advanced' and that resulted in the Source being set to ANY and the Source port range being ANY.
We have multiple Virtual IP Addresses configured with in Firewall / Virtual IPs. The destination is one of these Virtual WAN Addresses.
Thanks
-
Anyone any ideas on this ?
It's currently blocking access and causing me issues.Thanks
-
Let me make sure I understand the question.
I have a Synology NAS "diskstation".
It lives on LAB, IP 192.168.1.15
On this disk I have a web server - running on port 80.
I wanted to make this web server accessible from the Internet.I have a known URL that point to my home IP : brit.test-domaine.fr
I want to make this web server visible on port 8081.
So, when you go here : http://brit.test-domaine.fr:8081 you should see this screen :
I added this NAT rule :
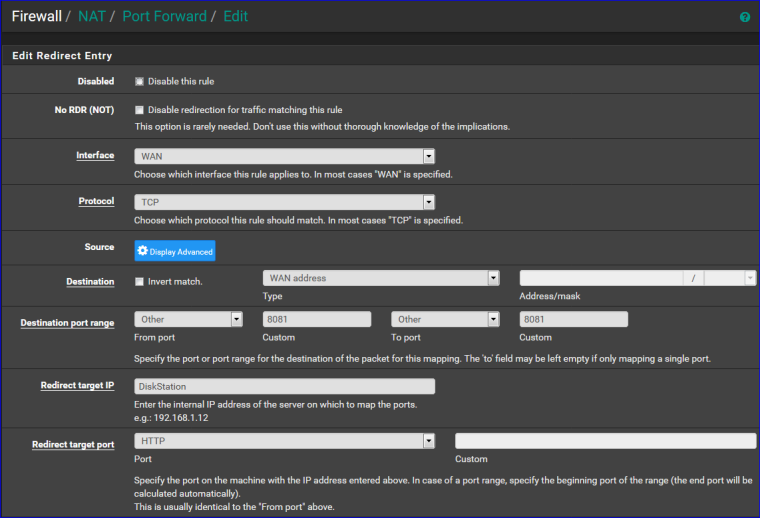
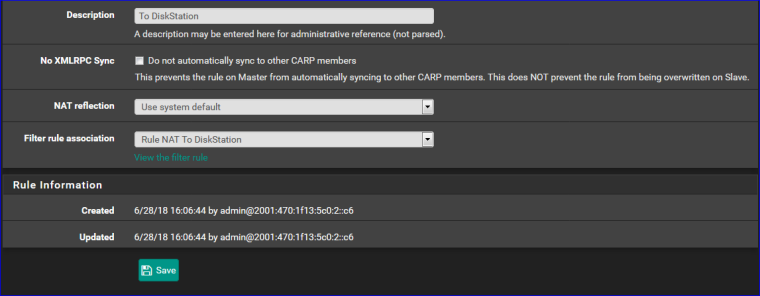
and I worked.
Note the fact that a related firewall is created. Is was added at the bottom, right after my last own explicit "drop all rule", so I had to lift this auto created rule just above it.
Is this scenario identical with yours ?
(Ok, I didn't mention that I needed to NAT also the router in front of my pfSense : all incoming traffic on TCP, port 8081 from WAn to IP-pfSense - but that actually a nearly identical operation)