Proxy Detected Error
-
Hi Guys,
Am having trouble with our Squid Proxy. Yes it is enabled, but the thing is I didn't configured any thing to point our computers to proxy. They are all set in "Automatically detect proxy" but the thing is I did not configured WPAD. How is this even possible. And the proxy server that was returned in proxy check is the IP of our ISP. It's the public IP.
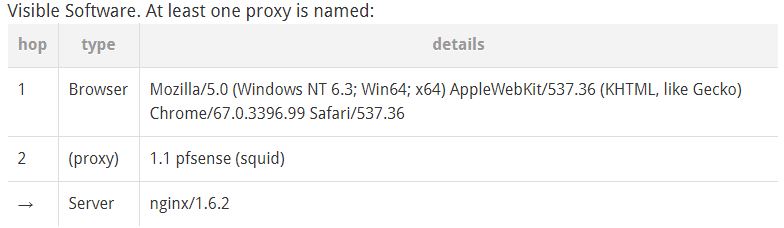
Take a look at my screenshot:
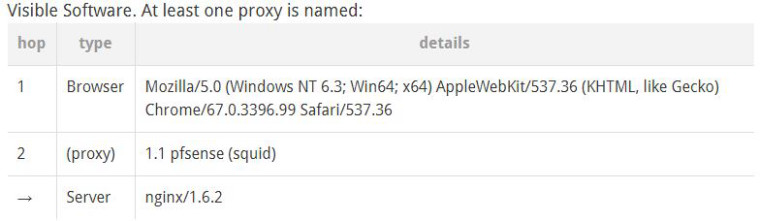
It says there that server that is holding the WPAD (since our setting is set to automatically detect) is Nginx. I checked nginx.conf but I didn't see any codes in there that point out or host WPAD.
Do you guys have any idea? And btw, when I blocked something in squidguard, it is not working.
-
The automatic detect settings will look for wpad configuration on your dns and dhcp. To see if any traffic is hitting squid, take a look on realtime tab.
-
@marcelloc Yup. I am aware of that. I can confirmed that I removed the settings in DNS and DHCP for WPAD. I can't even resolve wpad when I try it in cmd using NSLOOKUP utility. That's why it is kind of weird.
I already checked the real time tab and it is logging the connection. So it means that it is passing thru our proxy.
-
ok. Check with tcpdump on console/ssh if the traffic is hitting the proxy with a direct proxy connection or via transparent proxy.
If pfsense is the dns server you will able to see all dns request from the machine too.
-
@marcelloc Do you have any guide on using this tcpdump? How do I know if it's hitting a direct or a transparent proxy?
-
If the destination ip/port is the pfSense ip with proxy port, then it's a direct connect.
If the destination ip/por is an valip ip address with port 80 or 443 then it's a transparent connection if transparent mode is configured.The basic usage for tcpdump is:
tcpdump -ni YOUR_LAN_OR_WAN_INTERFACE host YOUR_CLIENT_IP