No Internet access if the last rule is deactivated
-
Hi,
I am not the best at firewall rules as you will see but I can't see why I am wrong. The last rule allows everything which is bad but when it is disabled, it locks up and there is no access.
I'm trying to setup a DMZ.0_1532141471518_Basic firewall rules not working.pdf.zip
Cheers,
-
Why don't you insert a screenshot here. It's easy.
Assuming the showed rules are from the DMZ tab, the allowed services in the rules like DNS, HTTP, HTTPS have to be set as destination ports. The source ports have to be any in all rules.
-
How is it in this day and age of snapchat and instagram people do not get how to post up a simple screen shot?
Here for the next guy, doesn't have to unzip and view a PDF?
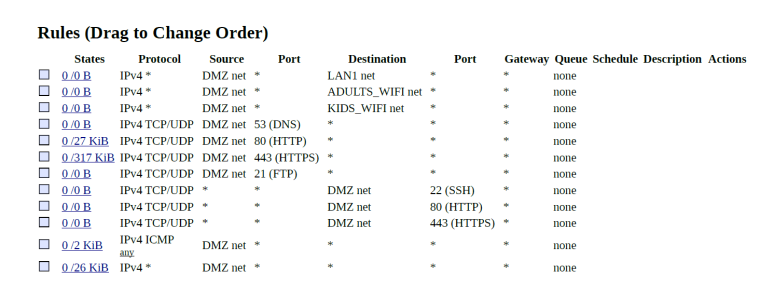
For starters all those rules with dmz net as dest on what has to be your dmz interface I assume are just pointless. Also shince when would ssh be UDP?
Also as mentioned already those rules with source ports make no sense with dest of any... but odd showing hits on the 80/443 rules.
But yeah killing your last rule will for sure kill internet access..
What blows me away is how is it someone wants to setup a secondary segment, dmz if you will and doesn't understand the basics of source and dest ports?
Firewall rules are evaluated as traffic enters an interface from the network its connected too.. When would pfsense ever see traffic from ANY to dmz net on the dmz interface?
Rules are evaluated top down, first rule to trigger wins no other rules evaluated..
-
Sorry guys.
I wasn't up to speed on screenshots on Linux. So now I have Kazam ...
Those firewall rules I posted have already been changed a bit but worse is that I feel pretty dumb. They are probably really shocking to some of you.
I don't get the difference between 'DMZ net' and 'DMZ address' and was thinking you had to setup a rule from the net to the address ...

I have a purpose built N13 box with an i3 and 6 ethernet ports from IWill in China ( https://www.alibaba.com/product-detail/mini-pc-6-lan-port-and_60776223770.html?spm=a2700.7724838.2017115.73.3c9e3dc7MMaD32 ) and am running pfSense 2.4.2-RELEASE-p1 (amd64) on it.
The various interfaces are: WAN, LAN1, LAN2, Adults_Wifi, Kids_Wifi and DMZ.
All I need at this stage is to have access to the Internet on all interfaces and for the DMZ to work. I do have Internet access on all I think (I haven't tested LAN2 and don't care about it at this stage).
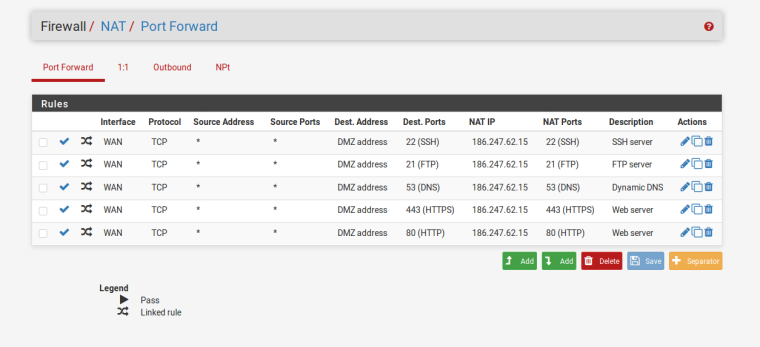
I've been trying some NAT rules ... am I on the right track ? (here goes a screenshot ...)
-
Post a screenshot of both WAN and DMZ firewall rules. the picture that johnpoz posted for you doesn't show what interfaces those are actually on..
-
Thanks for the reply chpalmer.
The WAN rules I haven't touched but they have some added by the NATting ones I posted earlier.
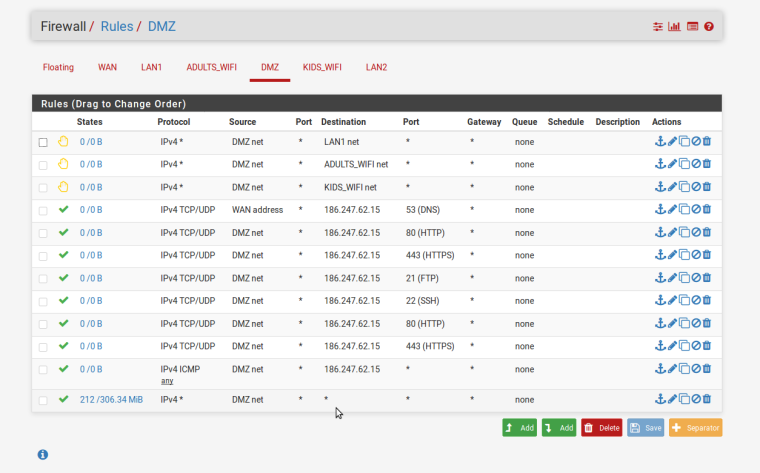
The DMZ rules are shocking but I'm being honest and posting them anyway. The first 4 might work but anything else other than the default one are needing to be deleted or changed...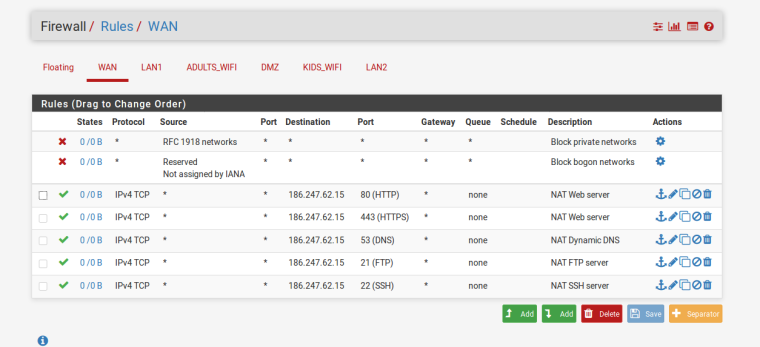
Cheers,
-
Are you using the 186.247.62.x addresses as your DMZ subnet?
Are you the owner of that subnet as it is a public subnet.
Telemar Norte Leste S.A.??
-
Dude you should really step back and understand how rules are evaluated before you attempt to edit them..
So on your DMZ... How is your wan address ever going to be a source???
So you want your dmz net to only go to that 185.x.x.x address? Or is that your wan IP? And you think if you allow that it can talk to the internet??
The internet is not wan net, its not your wan IP... The internet is ANY!!! Your last rule there allows to internet.. All of those rules above that allow to that 185.x.x.x are pointless since your last rules allows everything. So uness you were going to log those rules.. What are they suppose to accomplish.
Why don't you state WHAT your wanting to do and we can walk through how to do that.
Also as already mentioned you can not just grab public IPs and use them on your network without issues. If you did own those IPs - why would you be natting to them?? So just at a complete loss to what your wanting to do exactly here. From your wan rules that looks like your port forwarding to that IP.. But then your dmz rules are allowing access to it? On udp for protocols that do not support UDP..
So again - why don't you draw up your network, what networks your using on your different vlans (rfc1918 I would assume) you don't have any public space routed to you - do you? And then what you would like to accomplish with firewall between your segments and any port forwards and we can walk through how to do that.