transparent bridge firewall with seperate management-port
-
Hello everybody,
I'm currently trying to secure some servers in a small server room from the rest of the LAN with pfSense via a transparent firewall. The firewall itself should have an extra MGMT port, which is connected to the switch "behind" the firewall and is secured by itself:
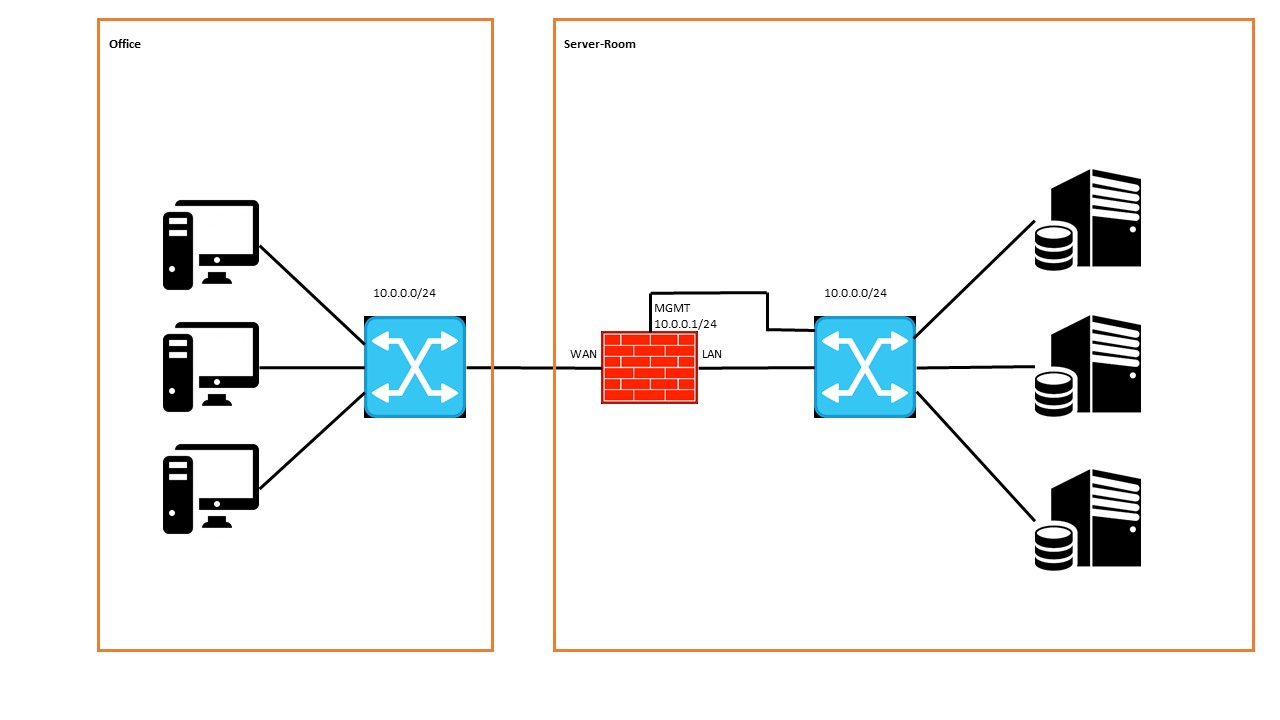
The IP network in front of and behind the firewall is the same. The firewall WAN and LAN ports have been configured as a bridge, both have no IP assigned.
The MGMT port of the firewall has an IP of the local LAN.First question is if this configuration is possible at all?
I think the switch behind the firewall does not like the constellation. Unfortunately, I have no access to the management of the switch and can not control anything, but I would currently suspect that there is a loop between the bridge-LAN-port and the MGMT port.Thank you very much for your help!
-
What device are you running pfsense on?
"The firewall itself should have an extra MGMT port, which is connected to the switch "behind" the firewall and is secured by itself" - I don't understand this part. How is it connected?
-
Unless you can get management rights to the switch and the switch is VLAN capable I don't see how you could achieve what you want.
I would just dedicate a NIC (what you now have as default LAN would be a good choice, move your bridge to be between WAN and OPT1) to the MGMT network and leave it unconnected anywhere in your systems, plug in a laptop or whatever when you need to administer your pfSense.
-
The best solution is for your management address to be on a different network than anything touching the bridge (different L2, different subnet).
If you must have it the way you describe, then your LAN, WAN, and MGMT interfaces would all be part of the bridge and MGMT should actually be the
bridge0interface and not a separate physical port. There is no need for a separate port if it's on the same network as the bridge, and you'd actually be making an L2 loop of sorts by doing so. -
Hi,
thx for your replies so far!
@gboone the Firewall will probably run on an one U server with a Xeon E5-2637 and 16 GB of RAM;@kpa a special VLAN or similar for the MGMT interface is unfortunately not possible; furthermore should the MGMT be accessible all the time from the Offie-LAN;
@jimp sadly I think I did produce the L2 loop which caused a lot of trouble with my network admin :/
the goal should be a complete transparent firewall between the Office- and the Server-Room-LAN with filtering rules;
furthermore should the firewall be manageable from the Office-LAN all the time;
I don`t need the MGMT-Interface necessarily wether I anyway can manage the firewall from the Office-LAN
I think the main problem is that on both sides of the firewall I have the same VLAN and IP-Network which I'm not able to change... -
pfSense might be able to do what you're asking... but IMHO, the real solution is to buy a managed switch and apply ACL to each port connected to the server closet. I don't think it's possible to do what you're asking unless you can manage the server closet switch.
If you're willing to put all the server room machines into a different IP subnet, a large number of options will open up to solving your problem.
-
If I wanted to realize a transparent firewall with pfSense, what is the "regular" way to do this? Without the MGMT-Port in the example above.
I "merge" the WAN- and LAN-Port without any IP-Adresses into a bridge-port and set up the firewall-rules for this bridge.
So the two networks with the same IP-Subnets should be separated and access should be filtered by the firewall-rules.
But how do I connect to the management section of the firewall in this szenario? -
Hi, I tryed the whole thing again in an other way.
I installed pfsense on a pc with two network-cards.The LAN-Port has the static IPv4 10.0.0.150/24
The WAN-Port doesn`t have an IP
Both ports are configured to a bridge-interface an the settings "net.link.bridge.pfil_member=0" and "net.link.bridge.pfil_bridge=1" are set.
NAT is disabled.Each port of the firewall is connected to a seperate networkswitch.
LAN-Port --> Switch --> Test-Client with IP 10.0.0.100/24
WAN-Port --> Switch --> Test-Client with IP 10.0.0.101/24following firewall-rules are active:
LAN-Interface:
allow IPv4 from any to anyWAN-Interface:
allow IPv4 from any to anyBridge-Interface:
allow IPv4 from any to anyIn this scenario I can reach the firewall from both of the clients and the clients can reach each other.
When I delete the LAN and the WAN firewall-rule, no more traffice is possible.
But why? The bridge firewall-rule with "allow IPv4 any any" is still active!
For my understanding the filtering should exclusively happen on the bridge interface with the set "net.link.bridge.pfil" settings.
Or am I understanding this in a wrong way? -
-
@menace you are definitely following the write-up but it doesn't say which interface should have the ip address. It just says only one.
It does say that the bridge should be exclusively filtering. I was unaware of this setting.
Did you set up MGMT on bridge0?
-
as mentioned above I´m trying to separate the server-room from the rest of the network via a transparent firewall with pfsense
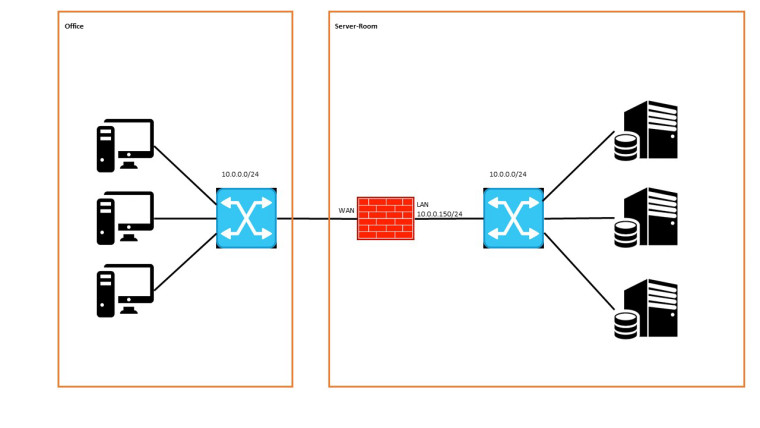
Because of having problems with a separate MGMT interface on pfsense, now I tryed to resign this one and use the LAN interface for managing the firewall.
Sadly I´m not able the change anything about the given IP situation in the network. -
There may be reasons for you to do that. But if we talk about a /24 including Clients and Servers, just make a clean design where in a first step Servers and Clients live in a separate LAN. Later there will be more to add, maybe a Printer LAN, Wireless, Guests and so on. THEN you can still follow the transparent setup, but it will be always be limited in terms of managing. And in terms of security there is also no benefit, except segregation of duties..
-
Finally we´re making some progress. I installed the firewall-pc completely new from scratch.
I configured the LAN and WAN port into a BRIDGE and set net.link.bridge.pfil_member to 0 and net.link.bridge.pfil_bridge to 1
After this, I set the management IP of the firewall to the BRIDGE interface and deleted it from the LAN interface. I think this did the trick for me.
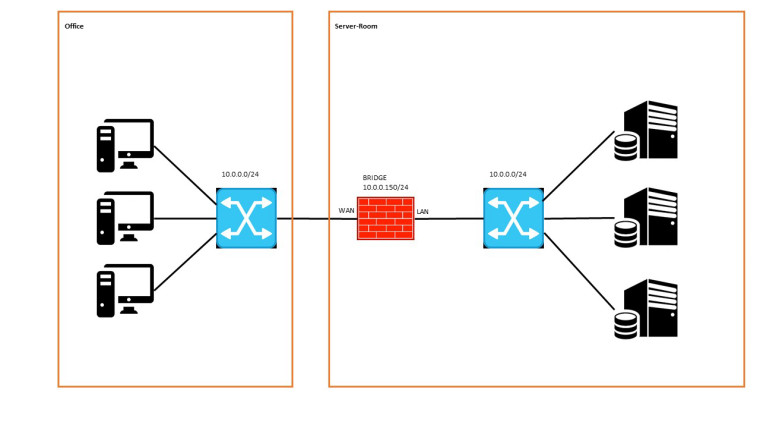
now following firewall rules are aktive:
LAN interface:
allow IPv4 from LAN net to anyWAN interface:
allow IPv4 from WAN net to anyBRIDGE interface:
allow IPv4 from LAN-test-pc-IP to firewall-ip port 443
allow IPv4 from WAN-test-pc-IP to firewall-ip port 443With this settings/rules I can access the firewall-webinterface from test-pcs on both sides of the bridge.
Apparently this constellation works for me in my desired constellation. More tests are in the pipeline.
Crossing fingers, the firewall still works, when I connect it to the "live" network, without making trouble and causing L2 loops!
amendment:
apparently the two "allow any any" rules on the LAN and WAN interface aren´t necessary for the function of the bridge. I deleted them and the traffic is still filtered through the bridge as desired.