Redirect DNS traffic for clients connected via OpenVPN (NAT forwarding?)
-
Hello:
We are attempting to create a VPN system which permits users to access certain resources, and all other traffic exits their local workstations normally.To accomplish this we're using routes specified in the OpenVPN configuration for specific IP addresses for these services to carry them over the tunnel. We also wish to use FQDN for the services but not publish public records at our DNS registrar so we're attempting to use the DNS resolver service in pfSense to specify additional records and only permit lookups via VPN.
This obviously creates an issue as we're not forcing all traffic via OpenVPN when clients are connected, so the idea came up to specify routes for the DNS servers in use at the local workstation (ISP, OpenDNS, etc) or what have you, allowing connected clients to not have to change their workstation DNS settings, and attempt to intercept/forward that traffic from VPN users to pfSense's DNS Resolver, thus allowing the specified internal zones to be resolved.
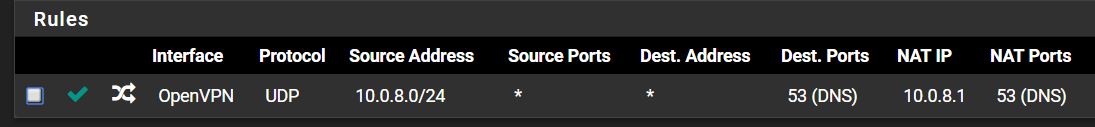
The traffic does indeed route through the VPN tunnel as expected, however, using a NAT forward rule, no matter what it seems I specify, will not forward the traffic to pfSense, it simply continues on through the tunnel to the final destination.
I've tried creating a rule using the OpenVPN interface, as well as the IP range for VPN clients as the source with no success.
Does anyone have suggestions or other ideas on how to accomplish this?
Screenshot of example rule attached
-
Outbound NAT does NOT route traffic. It only determines what NAT occurs when traffic flows that way.
From your description it's pretty difficult to determine exactly what you are showing us there.
What kind of OpenVPN setup is this? (remote access, point-to-point, etc).
-
It's a remote access OVPN setup. Remote employees are connecting to it
-
OK so that's a port forward on the OpenVPN interface.
I would not NAT to the tunnel address there. I am not 100% certain that the DNS resolver even listens on the tunnel address. I would NAT to a LAN address or probably localhost (127.0.0.1)
Forward both TCP and UDP. DNS can use both.
But it looks like what you have should work. Pretty sure you do not need an assigned interface to do that.