HAProxy 0.59_7 not working with SSL. :(
-
Pfsense 2.4.3-Release-p1
HAProxy 0.59_7 updated from 0.54_2Firewall has been restarted.
Issue:
port 443 sites don't work at all, only port 80 sites work.
Frontend-HTTPS type is ssl/https
For my exchange server backend it shows, server list; active, exch443, address+port, 192.168.75.60, 443, no Encrypt SSL, no SSL checks, no weight.Frontend shows WAN address (IPv4) as the listen address, port 443, no ssl offloading.
the ACL has;
exchange443 "sever name indication TLS extension matches" no cs no not owa.smoothrunnings.caActions, shows use backend, exchange443.. backend: backend-exch443
When I try to access the site from inside my network it is accessible. The SSL 2048bit cert is valid until 2020. The issuer is AlphaSSL CA - SHA256 - G2. It was working previously on HAProxy 0.54_2 but since the update it no longer passes the traffic over. :(
Thanks,
-
@smoothrunnings
Can you check the server configuration? The server should probably not have encrypt ssl checked, but should have ssl checks checked?If thats not it, can you share your haproxy.cfg from bottom of settings tab?
-
Hi PiBa,
There has been no changes on my servers and I can access the sites OWA and WWW for instance which run on separate Windows 2016 Servers using https: locally without any issues. And OWA worked perfectly before upgrading to O.59_7
Automaticaly generated, dont edit manually.
Generated on: 2018-08-10 10:22
global
maxconn 500
stats socket /tmp/haproxy.socket level admin
uid 80
gid 80
nbproc 1
hard-stop-after 15m
chroot /tmp/haproxy_chroot
daemon
tune.ssl.default-dh-param 2048
server-state-file /tmp/haproxy_server_statelisten HAProxyLocalStats
bind 127.0.0.1:2200 name localstats
mode http
stats enable
stats refresh 10
stats admin if TRUE
stats show-legends
stats uri /haproxy/haproxy_stats.php?haproxystats=1
timeout client 5000
timeout connect 5000
timeout server 5000frontend Frontend-HTTP
bind 24.212.203.198:80 name 24.212.203.198:80
mode http
log global
option http-keep-alive
timeout client 30000
acl website80 var(txn.txnhost) -m str -i www.smoothrunnings.ca
acl exchange80 var(txn.txnhost) -m beg -i owa.smoothrunnings.ca
acl autodiscover80 var(txn.txnhost) -m beg -i autodiscover.smoothrunnings.ca
http-request set-var(txn.txnhost) hdr(host)
use_backend backend-www80_ipvANY if website80
use_backend backend-exch80_ipvANY if exchange80
use_backend backend-autodiscover80_ipvANY if autodiscover80frontend Frontend-HTTPS
bind 24.212.203.198:443 name 24.212.203.198:443
mode tcp
log global
timeout client 30000
tcp-request inspect-delay 5s
acl website443 req.ssl_sni -i www.smoothrunnings.ca
acl exchange443 req.ssl_sni -i owa.smoothrunnings.ca
acl autodiscover443 req.ssl_sni -i autodiscover.smoothrunnings.ca
tcp-request content accept if { req.ssl_hello_type 1 }
use_backend backend-www443_ipvANY if website443
use_backend backend-exch443_ipvANY if exchange443
use_backend backend-autodiscover443_ipvANY if autodiscover443backend backend-www80_ipvANY
mode http
id 109
log global
timeout connect 30000
timeout server 30000
retries 3
option httpchk OPTIONS /
server website80 192.168.75.40:80 id 110 check inter 1000backend backend-exch80_ipvANY
mode http
id 105
log global
timeout connect 30000
timeout server 30000
retries 3
option httpchk OPTIONS /
server exch80 192.168.75.60:80 id 106 check inter 1000backend backend-autodiscover80_ipvANY
mode http
id 111
log global
timeout connect 30000
timeout server 30000
retries 3
option httpchk OPTIONS /
server autodiscover80 192.168.75.60:80 id 112 check inter 1000backend backend-www443_ipvANY
mode tcp
id 107
log global
timeout connect 30000
timeout server 30000
retries 3
option httpchk OPTIONS /
server website443 192.168.75.40:443 id 108 check inter 1000backend backend-exch443_ipvANY
mode tcp
id 103
log global
timeout connect 30000
timeout server 30000
retries 3
option httpchk OPTIONS /
server exch443 192.168.75.60:443 id 104 check inter 1000backend backend-autodiscover443_ipvANY
mode tcp
id 101
log global
timeout connect 30000
timeout server 30000
retries 3
option httpchk OPTIONS /
server autodiscover443 192.168.75.60:443 id 102 check inter 1000 -
@smoothrunnings
can you check the 'ssl check' option? (For the SSL :443 servers that is..)
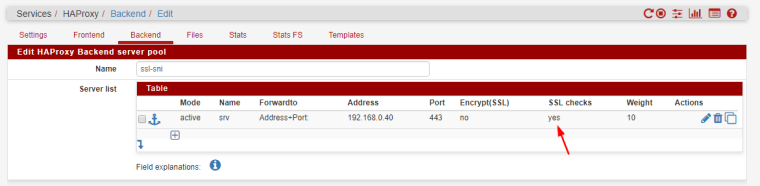
For the :80 servers i wonder what does the stats page LastChk say about them?
-
@piba OK. that seems to have fixed. Not sure if the update removed this option or if the previous version option didn't work correctly as I have don't fiddle with things once they are working. Thanks for your help again!
-
@smoothrunnings
Previous haproxy package version (before 0.56.x iirc) did some 'automagic' configuration guessing if ssl checks and ssl encryption should be needed from 1 configured checkbox, combined with the frontend it was used by. This is now split up, to allow full control over both options. But with the 'config upgrade' it didn't know the exact desired situation, this is what went wrong for people using sni, and right for people using https-'offloading' on the frontend. I'm sorry for the trouble. So the upgrade did not remove the SSL-Check checkbox as that is a new checkbox added in this update.. But it did change behavior for some people.. -
@smoothrunnings
Just to be sure.. it does seem that backend-exch80_ipvANY isnt 'up' yet.. Have you checked what the stats page says in LastChk column? -
@piba said in HAProxy 0.59_7 not working with SSL. :(:
it does seem that backend-exch80_ipvANY isnt 'up' yet.. Have you checked what the stats page says in LastChk column
That's the next thing I have to fix on the server side it seems. The server reports a 503 server when I do HTTP to it. I think in the past I had it setup to redirect to HTTPs but after CU10 it might have broke. So no worries right now. 443 works, so does the webserver on 443 and 80. autodiscover is on the same server as OWA so it too is broke on 80.