Create ACME cert for an existing website SSL?
-
Hi,
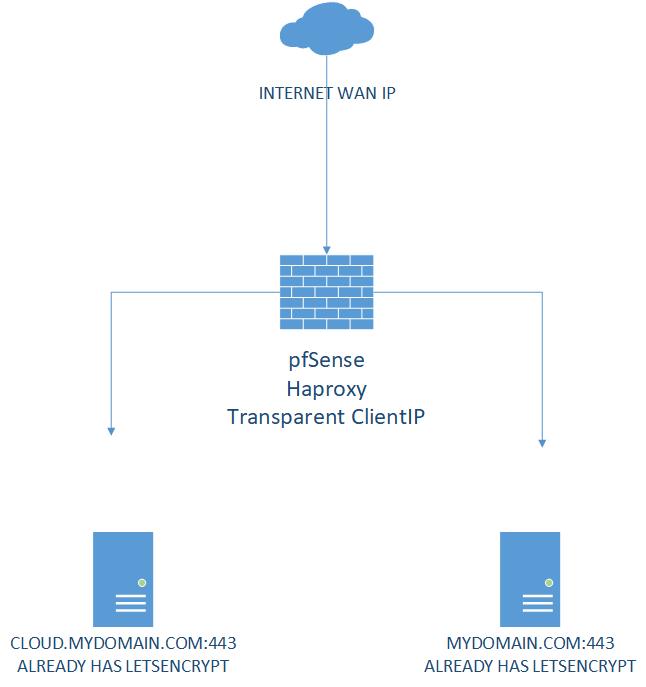
I was wondering if someone could shed some light on what im trying to do, just want to know if its possible. Currently Have HAproxy which tunnels 2 of my sites, cloud.mydomain.com and mydomain.com both sites are running Lets-encrypt on port 443 on the same WAN IP. Now i want to change that the Lets-encrypt would run on pfSense instead on the vms, then route that to HAproxy would that possible? As reading few sites and forums i saw that Lets-encrypt has to run on port 80? or how would i create my certificates on pfSense on which mydomain.com already has SSL which also has Lets-encrypt.Thank you
-
One of the dynamic DNS methods such as RFC2136/nsupdate or one of many others is probably what you want here.
Flow
- Start the certificate issuance/renewal process
- Let's Encrypt sends you a blob to put in a DNS TXT record at _acme-challenge.host.domain.com
- pfSense uses the information at-hand to update the proper DNS record dynamically
- Let's Encrypt queries the record and, if it matches, issues the new certificate.
- pfSense deletes the TXT record and installs the new certificate.
You don't need to worry about making the .well-known location visible on a web server any more.
-
@derelict said in Create ACME cert for an existing website SSL?:
RFC2136/nsupdate or one of many others is probabl
Thanks for the reply, so if i understood correctly would it in my case standalone HTTP server on the domain SAN list? This is what i have now currently setup (see picture)
This is the error im getting
[path] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [PATH] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ ) [Mon Aug 13 21:45:41 COT 2018] Renew: 'mydomain.com' [Mon Aug 13 21:45:42 COT 2018] Standalone mode. [Mon Aug 13 21:45:43 COT 2018] Single domain='mydomain.com' [Mon Aug 13 21:45:43 COT 2018] Getting domain auth token for each domain [Mon Aug 13 21:45:43 COT 2018] Getting webroot for domain='mydomain.com' [Mon Aug 13 21:45:43 COT 2018] Getting new-authz for domain='mydomain.com' [Mon Aug 13 21:45:44 COT 2018] The new-authz request is ok. [Mon Aug 13 21:45:44 COT 2018] Verifying:mydomain.com [Mon Aug 13 21:45:44 COT 2018] Standalone mode server [Mon Aug 13 21:45:48 COT 2018] mydomain.com:Verify error:Invalid response from http://mydomain.com/.well-known/acme-challengeThank you
-
I'm sorry I don't understand what you are asking.
-
Thanks for the reply, and sorry for confusing you. What i want is pfSense to handle the SSL Letsencrypt rather then the 2 vms (cloud, website)
Before i can do that i would need to create the SSL certificates on pfSense the issue is that when i try to get the certificate keeps telling meadding _acme-challenge.mydomain.com. 60 in txt "mEFL11-5FdtnGmZMXeUxLeEms4bEPNB0RJuNEsAXGbA" key option must specify [hmac:]keyname:secret [Mon Aug 13 21:51:52 COT 2018] error updating domainThe idea is to use the Certificates of Letsencrypt on pfSense to then redirect it to HAproxy for the backend of my 2vms which are running the cloud.mydomain.com and mydomain.com
Thank you
-
If you want to offload SSL to HAProxy on pfSense and let ACME handle the validation, you can. You do not need to import anything from your other servers, let the ACME package create and request the certificates for you. Even though they already exist, as long as the validation passes it will be OK.
From the look of that last error you do not have the proper settings for DNS validation.
You could instead follow the example at https://forum.netgate.com/topic/90643/let-s-encypt-support/31 and configure it so HAProxy can assist in handling the validation instead of using DNS.