Double OpenVPN config on single network WAN>LAN>WAN2>LAN2
-
Greetings,
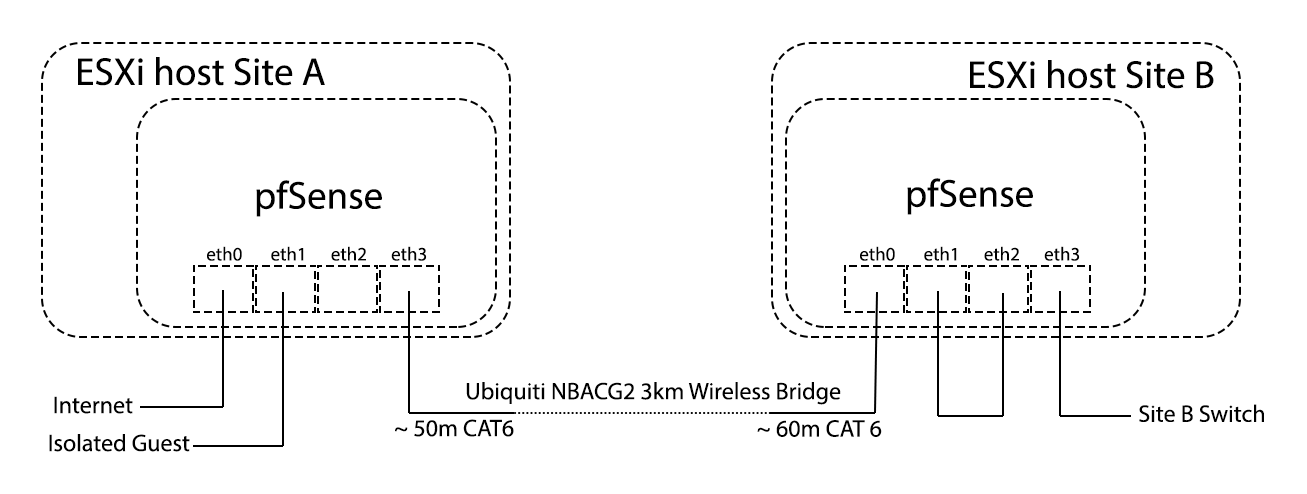
I have my network setup as follows:
The two CAT6 cables between Site A eth3 and Site B eth 0 are a security issue for me as they are openly available for anyone to splice and gain access to my network. To remedy this, I intend to encrypt everything in between Site A eth3 and Site B eth 0 using OpenVPN.
I intend to have a local VPN tunnel between Site A eth 3 and Site B eth 0. And to make things complicated, this has to be in addition to a VPN tunnel I already have between Site B and a remote server in Germany. This tunnel has a few exempted ports and thats what the VPN tunnel between Site A eth 3 and Site B eth 0 is for.
To further try to explain, lets say the traffic generated at Site B goes through LAN (eth3) to WAN (eth2) where it is encrypted (with a few ports excempted). This (semi) encrypted traffic goes to LAN (eth1) and then to WAN (eth0) where it is fully encrytpted before going to Site A LAN (eth3) where it is decrypted (I can therefore access the ports for SMB, Plex etc here). Then the remaining (semi) encrypted traffic goes on to the remote server in Germany.
Can anyone please advice how to set this up in pfSense?
-
Honestly, in that case I would probably use IPsec.
There really isn't enough information provided to make any recommendations. Need to know how the subnets are defined, etc.
Zero idea what you are doing with that eth1 - eth2 loop at Site B, for instance.