Block IP camera internet traffic?
-
Hi,
I am looking to stop an IP camera on a lan from being able to "phone home". When I reboot the camera it sends 'data' (not sure how much) to upgrade.secu100.net. I am using Pi-Hole as my DNS server & it caught that it was sending a request to that domain.
I would like to use the firewall to allow internal traffic (to allow the NVR & IP camera to connect) as well as being able to view the camera from a desktop within the internal lan.
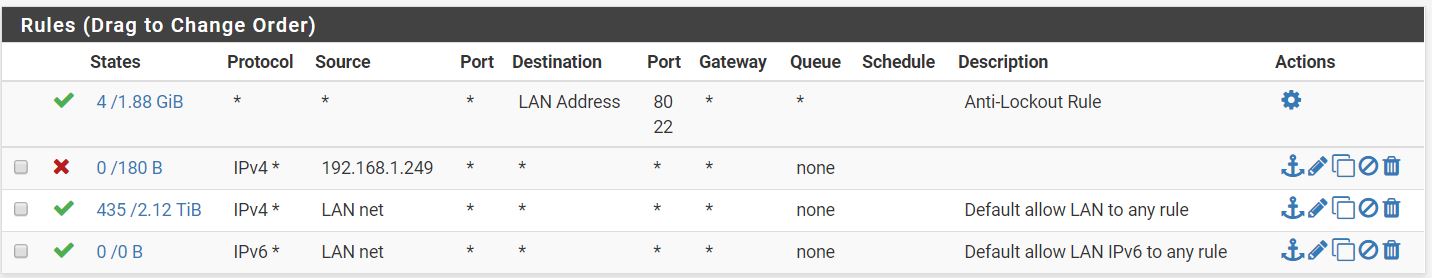
I tried adding a lan rule blocking all traffic to the camera IP (192.168.1.249) but it isnt doing anything but blocking web traffic. I tested this using a desktop IP which allowed RDP, other remote access, pinging external sites, etc - but web browsing didnt work on the firewalled machine.
Any ideas how to make this happen? I would like to do a range - 192.168.1.240-249.
Thanks,
Rich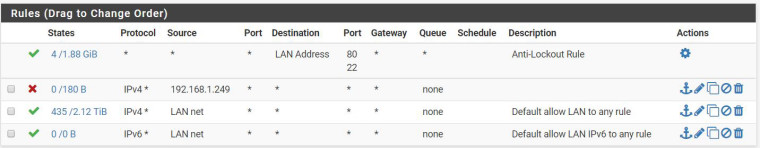
-
The easiest way to do this is to make an alias with your desired IP range to block from going outside your network, and then use that alias to make a deny rule. That's what I did with my IP cameras and it works great at stopping them from phoning home.
-
That sounds great - do you mind sharing how you set that up? I have never used an alias before.
-
So for some reason when I setup the rules, they never actually turn on. I did try the reset state but that doesnt do it either. Should the above rule stop traffic to 192.168.1.249?
The alias is pretty cool too & will do the ticket for me! I just need to get the firewall to block traffic.
-
Aliases are fun, since they can replace swathes of rules and make everything look super clean.
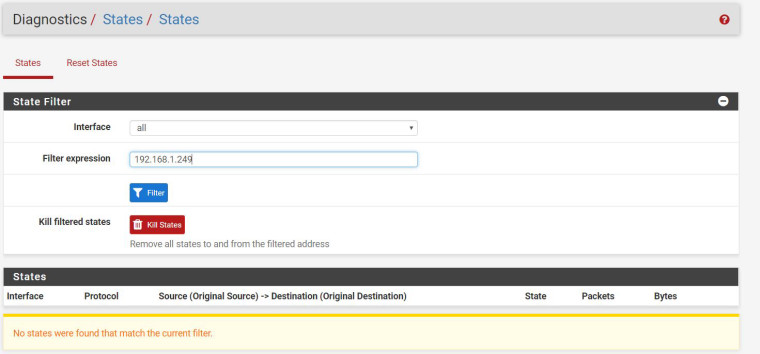
I had the same issue with fresh block rules not going into apparent effect immediately; it does come down to that state table. Filter the state table based on the IP of the camera then kill all of those states, and you should see it start to work. If you see numbers in the left hand column in your rules table, you can see it working. To double verify, turn on logging for that rule and check the Firewall Logs.
-
-
@richtj99 Have you added a static mapping (Services > DHCP Server > DHCP Static Mappings for this Interface) for your camera too? Because without that, just because it's 192.168.1.249 now doesn't mean it always will be. By adding a static mapping, you can be assured that the camera will always have that IP. And then you just need to add a LAN firewall rule blocking all traffic whose source is 192.168.1.249. You could use an alias for that IP too if you'd like (and will need to if you want to block the range as you described). What about your first rule wasn't working? From what I can see, that should have successfully blocked the IP 192.168.1.249 from getting to the WAN, although per cparkervt's comment you might need to clear states first.
-
@richtj99 does the camera itself have a ping utility in its web UI? You can try pinging an outside IP to verify it’s blocked.
-
Hi - I dont have static mapping turned on but did log into the camera web interface and set a static IP.
@cparkervt
I am able to ping the IP from inside the network. I only access the camera from outside the network using Openvpn.I guess I am looking for an internal firewall block, not an external firewall block (as my whole network is blocked with the firewall).
-
@richtj99 If you're using pfSense as a DHCP server for everything else, I'd recommend adding a static mapping. Either that, or make sure that 192.168.1.249 is outside of the IP range the DHCP server is using.
-
@cparkervt
I am able to ping the IP from inside the network. I only access the camera from outside the network using Openvpn.I guess I am looking for an internal firewall block, not an external firewall block (as my whole network is blocked with the firewall).
I am referring to using the ping on the camera itself to test against 8.8.8.8 to make sure that rule is doing what you want.