Cannot connect to a 2nd pfsense firewall
-
I have two static Internet connections from my ISP; one at 216.146.215.8 and the other at ...13. I have current, up-to-date, pfSense firewires running on both.
From behind each, I can access the internet, ping the firewall, the isp, etc.
However, I can not access services from one to the other.
I created an open ICMP rule on both, and they can now ping each other - so the network is fine (and its unlikely my ISP is doing anything strange).
However only ICMP is now working, all other services are generating "No route to host" errors.
For example, from a node on the .8 network:
rackserv ~ # ping 216.146.251.13 PING 216.146.251.13 (216.146.251.13) 56(84) bytes of data. 64 bytes from 216.146.251.13: icmp_seq=1 ttl=62 time=2.09 ms 64 bytes from 216.146.251.13: icmp_seq=2 ttl=62 time=1.01 ms 64 bytes from 216.146.251.13: icmp_seq=3 ttl=62 time=1.42 ms ^C --- 216.146.251.13 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 1999ms rtt min/avg/max/mdev = 1.016/1.511/2.090/0.442 ms rackserv ~ # man telnet rackserv ~ # telnet 216.146.251.13 15858 Trying 216.146.251.13... telnet: Unable to connect to remote host: No route to host rackserv ~ # netstat -nr Kernel IP routing table Destination Gateway Genmask Flags MSS Window irtt Iface 0.0.0.0 172.16.4.1 0.0.0.0 UG 0 0 0 eth1 172.16.4.0 0.0.0.0 255.255.252.0 U 0 0 0 eth1 rackserv ~ # telnet 216.146.251.1 Trying 216.146.251.1... telnet: Unable to connect to remote host: Connection refused(I included an attempt to telnet into my ISPs firewall just to show what I would expect to see if the service was not responding.)
Any suggestions?
-
Update: this appears to be tied to Advanced -> Firewall & NAT settings. Either "Enabled NAT Reflection for 1:1 NAT" or "Enable automoatic outbound NAT for Reflection", both of which I had switched on from a previous exploration of PURE NAT mode. Untoggling those two cleared up the situation... for about 30 seconds. That or it was just the firewall going through the "save".
rackserv ~ # telnet 216.146.251.13 15858 Trying 216.146.251.13... ^C rackserv ~ # telnet 216.146.251.13 15858 Trying 216.146.251.13... telnet: Unable to connect to remote host: No route to host -
I assume your public IPs are within the same subnet. So have you set the correct subnet mask for the WAN IPs, propably /29?
-
@ccgllc said in Cannot connect to a 2nd pfsense firewall:
215.8 and the other at ...13. I have current, up-to-date, pfSense firewires running on both.
What is the mask on this? The mentioned /29 would not be right because .8 would be the wire not a host.
Are these in the same network... What is the mask setting on these 2 pfsense wan interfaces?
How exactly are they connected to your isp? ISP device to a switch? 2 different ISP devices? Are the 2 wan interfaces connected to the same L2 on your side?
-
My ISP uses a full Class C for their static customers, so /24, which things are set at.
216.146.251.1 is my upstream gateway for both.


Both are indendant fibre channel glass cables connecting into the ISP equipment at their facility.
-
@ccgllc said in Cannot connect to a 2nd pfsense firewall:
My ISP uses a full Class C for their static customers, so /24, which things are set at.
Address classes are obsolete since the introduction of CIDR. You just have a /24.
-
@jknott said in Cannot connect to a 2nd pfsense firewall:
@ccgllc said in Cannot connect to a 2nd pfsense firewall:
My ISP uses a full Class C for their static customers, so /24, which things are set at.
Address classes are obsolete since the introduction of CIDR. You just have a /24.
OK. I'm old. I'm obsolete. I remember when Gopher was cool new tech. You still got the point.
-
-
So you have a /24 and there is no local L2 network.. And run to your isp that still should be the same L2.. If you can not talk to either then that is on your ISP..
-
@johnpoz Expect that both work fine independantly, and now that I've opened up ICMP, pings work between then. TCP/IP does not.
Still, I'll ask. But not expecting much from them. Given that the pings work, they are going to point back to my firewalls.
-
Here is the thing.. So you have this at a logical level..
You have this
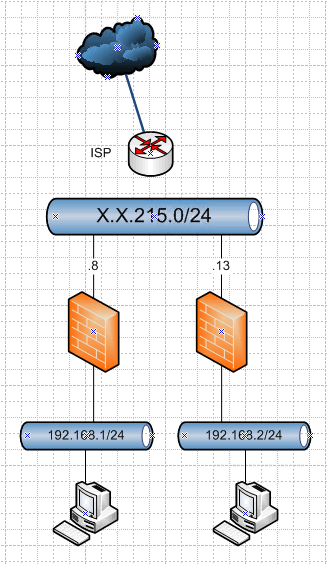
Your trying to talk to .13 from .8 that are in the same network.. So sniff on .13, do you see the traffic from .8? If you see it then problem in your forward, if you do not see it then problem at the ISP.
