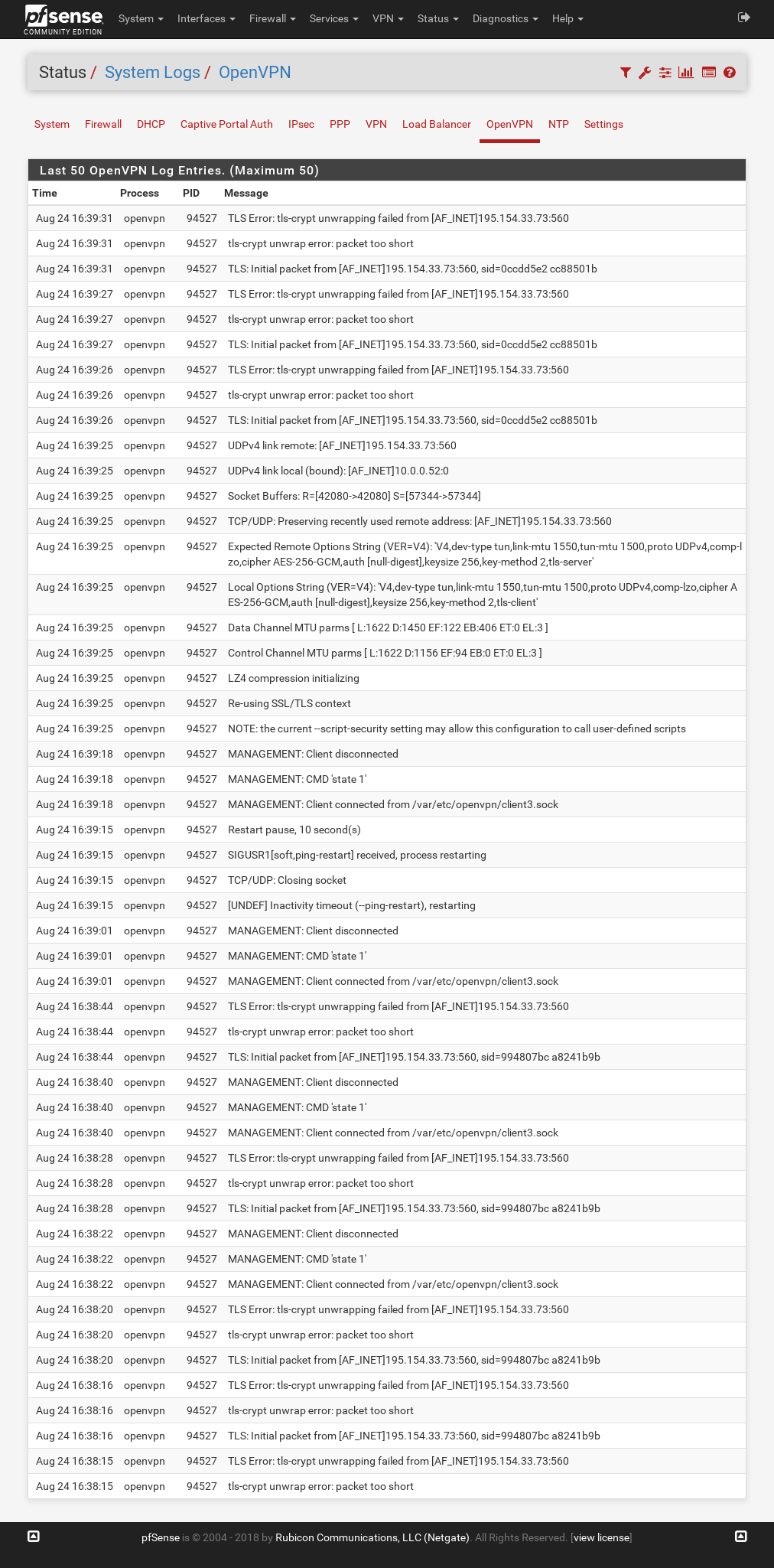
Cryptofree Configuration
-
I am trying to setup an OpenVPN client to connect to Cryptostorm's cryptofree service based on their config file, but I keep getting errors related to TLS. How do I translate their ovpn file to a working configuration in pfSense?
Their config:
client dev tun # "If hostname resolve fails for --remote, retry resolve for 16 seconds # before failing." resolv-retry 16 # "send server an exit notification if tunnel is restarted or OpenVPN # process is exited". This informs our server that the session has # ended, which is necessary to decrease the session counter. explicit-exit-notify 3 # "Require that peer certificate was signed with an explicit key usage # and extended key usage based on RFC3280 TLS rules. This is a useful # security option for clients, to ensure that the host they connect to # is a designated server. This is an important security precaution to # protect against a man-in-the-middle attack where an authorized client # attempts to connect to another client by impersonating the server. # The attack is easily prevented by having clients verify the server # certificate using any one of --remote-cert-tls, --verify-x509-name, # or --tls-verify." remote-cert-tls server # Even though the hostname below says "windows", the configuration for # these ECC instances are actually cross-platform. It was just easier # to reuse the DNS used by the Windows instances since the ECC instances # are on port 5060 of all of the Windows instance IPs. remote windows-cryptofree.cryptostorm.nu 5060 udp # "LZ4 generally offers the best performance with least CPU usage" compress lz4 # "Call --down cmd/script before, rather than after, TUN/TAP close." # No down cmd/script is used in this configuration, but most Debian # users will be adding the /etc/openvpn/update-resolv-conf up/down # script so OpenVPN can properly update the DNS. down-pre # Increase --verb for more verbosity, 0 to disable. verb 4 # "Log at most 3 consecutive messages in the same category" # Helps prevent the logs or STDOUT from getting flooded with the same # messages. mute 3 # Not doing "auth SHA512" for ECC instances, because: # "If an AEAD cipher mode (e.g. GCM) is chosen, the specified --auth # algorithm is ignored for the data channel, and the authentication # method of the AEAD cipher is used instead." # These instances use --cipher AES-256-GCM, so even if --auth is # specified, it would be ignored. # # Uncomment the below line to enable --auth-nocache #auth-nocache # "If specified, this directive will cause OpenVPN to immediately # forget username/password inputs after they are used". # We're not enabling it by default because, for users that are inputting # their token using standard input, it can be annoying because OpenVPN # will constantly ask them for their token on every TLS renegotiation. # For those providing a file to --auth-user-pass (to skip the user/pass # prompt), --auth-nocache doesn't prompt the user since the user/pass # is loaded from a file. auth-user-pass # "256 bit key, 128 bit block". The best available at the moment. # GCM chosen instead of CBC because in our tests it shows better # performance. cipher AES-256-GCM # TLS version 1.2 is the only version allowed, to prevent downgrade # attacks. tls-version-min 1.2 tls-version-max 1.2 # Elliptic curve Diffie-Hellman + Elliptic Curve Digital Signature Algorithm # with AES-256-GCM-SHA384, used to encrypt the control channel. # The most secure available at the moment. Again, GCM chosen instead of # CBC because in our tests it outperformed CBC. tls-cipher TLS-ECDHE-ECDSA-WITH-AES-256-GCM-SHA384 tls-client # CA certificate, using the signature algorithm ecdsa-with-SHA512, # and prime256v1 to provide a 256 bit EC public key. # "a 256-bit elliptic curve public key should provide comparable # security to a 3072-bit RSA public key". <ca> -----BEGIN CERTIFICATE----- MIIBszCCAVigAwIBAgIJALumkoBwGuApMAoGCCqGSM49BAMEMBkxFzAVBgNVBAMM DmNyeXB0b3N0b3JtIENBMB4XDTE4MDIyMjE5Mjc1NloXDTM4MDIyMjE5Mjc1Nlow GTEXMBUGA1UEAwwOY3J5cHRvc3Rvcm0gQ0EwWTATBgcqhkjOPQIBBggqhkjOPQMB BwNCAATAkRZNfbXjbs6LE1zkFlmnvamGgFNuuTUMidN1qrB1Uho39qxuRzzWYKAC 7flSU9vdIF9Wu0SoXxbx68ZStl/Uo4GIMIGFMB0GA1UdDgQWBBQ+CMOnCKZq7SzJ qpc1o2atGx9RUjBJBgNVHSMEQjBAgBQ+CMOnCKZq7SzJqpc1o2atGx9RUqEdpBsw GTEXMBUGA1UEAwwOY3J5cHRvc3Rvcm0gQ0GCCQC7ppKAcBrgKTAMBgNVHRMEBTAD AQH/MAsGA1UdDwQEAwIBBjAKBggqhkjOPQQDBANJADBGAiEApPF2CAqMD4bHdOkG vg3HMUwmcAfWoEnMMT8lm6n8JeoCIQCv9GORxdibasrHSZnSjlbOtLOWhbOlmz46 dVugiAfKSA== -----END CERTIFICATE----- </ca> # "Encrypt and authenticate all control channel packets with the key". # "Encrypting (and authenticating) control channel packets: # provides more privacy by hiding the certificate used for the TLS connection, # makes it harder to identify OpenVPN traffic as such, # provides "poor-man's" post-quantum security" <tls-crypt> -----BEGIN OpenVPN Static key V1----- 4875d729589689955012a2ee77f180ec b815c4a336c719c11241a058dafaae00 806bbc21d5f1abad085341a3fca4b4f9 3949151c2979b4ee4390e8d9443acb00 61d537f1e9157e45f542c3648f563305 05f3eaff97ef82ee063b9d88bb9d5aa0 060428455b51a2a4fd929d9af4b94adc b0a4acaa14ff62a9b0f4f9f0b3f01e71 fc98a6c60e8584f4deb3de793a5a7bc2 7014c9369f9724bc810ef0d191b30204 78eead725b3ae6aaef2e1030a197e417 421f159ed54eb2629afcfb337cf9a002 5bf1d5c0d820fffb219d0b4214043d2d f27ed367b522945a5dadc748e2ca379e 3971789dbdf609b3d9bfe866361b28e3 c90589baa925157ad833093a5a7bede5 -----END OpenVPN Static key V1----- </tls-crypt> # uncomment the line below to enable TrackerSmacker, # our DNS-based intrusive ad/tracker blocking service #dhcp-option DNS 10.31.33.7My config:
My errors:
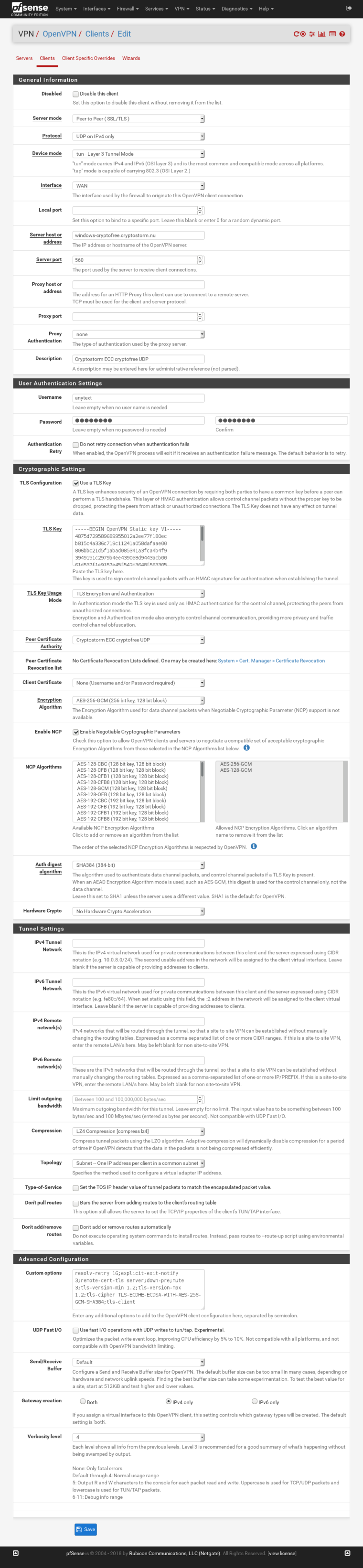
-
first, it's port 5060 not 560.
Second, I could not get that server to respond. It came right up using this:
# Cryptostorm.is config optimized for Tunnelblick/Viscosity OSX and OpenVPN iOS client dev tun resolv-retry 16 nobind float #txqueuelen 686 remote-random remote linux-cryptofree.cryptostorm.net 443 udp remote linux-cryptofree.cryptostorm.org 443 udp remote linux-cryptofree.cryptokens.ca 443 udp remote linux-cryptofree.cstorm.pw 443 udp remote linux-cryptofree.cryptostorm.nu 443 udp comp-lzo down-pre allow-pull-fqdn explicit-exit-notify 3 hand-window 37 mssfix 1400 auth-user-pass <ca> -----BEGIN CERTIFICATE----- MIIFIDCCBAigAwIBAgIJAKekpGXxXvhbMA0GCSqGSIb3DQEBCwUAMIG6MQswCQYD VQQGEwJDQTELMAkGA1UECBMCUUMxETAPBgNVBAcTCE1vbnRyZWFsMTYwNAYDVQQK FC1LYXRhbmEgSG9sZGluZ3MgTGltaXRlIC8gIGNyeXB0b3N0b3JtX2RhcmtuZXQx ETAPBgNVBAsTCFRlY2ggT3BzMRcwFQYDVQQDFA5jcnlwdG9zdG9ybV9pczEnMCUG CSqGSIb3DQEJARYYY2VydGFkbWluQGNyeXB0b3N0b3JtLmlzMCAXDTE3MTIxNjA3 NTk0MloYDzIwNjcxMjE2MDc1OTQyWjCBujELMAkGA1UEBhMCQ0ExCzAJBgNVBAgT AlFDMREwDwYDVQQHEwhNb250cmVhbDE2MDQGA1UEChQtS2F0YW5hIEhvbGRpbmdz IExpbWl0ZSAvICBjcnlwdG9zdG9ybV9kYXJrbmV0MREwDwYDVQQLEwhUZWNoIE9w czEXMBUGA1UEAxQOY3J5cHRvc3Rvcm1faXMxJzAlBgkqhkiG9w0BCQEWGGNlcnRh ZG1pbkBjcnlwdG9zdG9ybS5pczCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC ggEBAMlo5Jghf+yb7j86QKDIA9gH9U+MOj1gFz7POcobF3UXx8CR6py4+kY0LEwE s66YuwF3Et1Haymkrxy72RjHqD58FRC1KGg6PzhDr6foXgOpuOweUvBTLS6WR5Ba TW+8oqSkFWIZUWxnk4N1npxonZRjYLjU4AJNB1uUKpp5uwtC+n9UYpNZ2H1SwZDc tpJNzG3Q+ySqkaJYRR44YbeYoTQpbK/G3o7H2Kz1BsNck5h2SVBo9f3JS4gjTcaP fGb6+Lqra/MPlXKY55MzKTLsZ5q1t3ZTjn0vDO7+D7xXoRCXyq9atcRJf9ldm80b xABw5dTiS00E6hm3CzpPOSelAXcCAwEAAaOCASMwggEfMAwGA1UdEwQFMAMBAf8w HQYDVR0OBBYEFDhY4fdfMy+L0fMdat75Kep6cFElMIHvBgNVHSMEgecwgeSAFDhY 4fdfMy+L0fMdat75Kep6cFEloYHApIG9MIG6MQswCQYDVQQGEwJDQTELMAkGA1UE CBMCUUMxETAPBgNVBAcTCE1vbnRyZWFsMTYwNAYDVQQKFC1LYXRhbmEgSG9sZGlu Z3MgTGltaXRlIC8gIGNyeXB0b3N0b3JtX2RhcmtuZXQxETAPBgNVBAsTCFRlY2gg T3BzMRcwFQYDVQQDFA5jcnlwdG9zdG9ybV9pczEnMCUGCSqGSIb3DQEJARYYY2Vy dGFkbWluQGNyeXB0b3N0b3JtLmlzggkAp6SkZfFe+FswDQYJKoZIhvcNAQELBQAD ggEBABrPLmFpugICgUKyJ+6q5h8ZKfoV3S0RtTfrwtobNSFf7H4ZQvCXF2bOuhyc g00ffreEGZN2uwtiLh38ncB/BFhHfgkITfTe88m08pJ45PkrpeBfrFbZ+ckXVhV/ aCnUKkIZgmCNKnn1RIbUt4mzTzggwtN3GamoTzSWqSwCEO9Ig1AJKi5Ms/5Awtdz nr95qaqI0ih0NGnfC/yIGYvt1Yay0hCil3jIUT9Ogdw6DW6RqUdJaPrwm58fTwIR U33KzBqGs8r3UEIMWXuIGc6eXOm2Br08iFgOsUPGqp1ulvD52pFH1o1vT21v3aXl D9Ier/83JLMnBGctT1Kzs9OP/U0= -----END CERTIFICATE----- </ca> ns-cert-type server auth SHA512 cipher AES-256-CBC replay-window 128 30 tls-cipher TLS-DHE-RSA-WITH-AES-256-CBC-SHA tls-client key-method 2 # uncomment the line below to enable TrackerSmacker, # our DNS-based intrusive ad/tracker blocking service #dhcp-option DNS 10.31.33.7
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.