Explain to me why floating rule is required for my setup
-
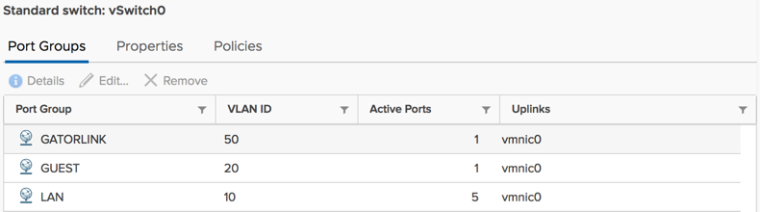
I have two subnets, one 192.168.10.0/24 - LAN and one 10.0.0.0/24 - GatorLink
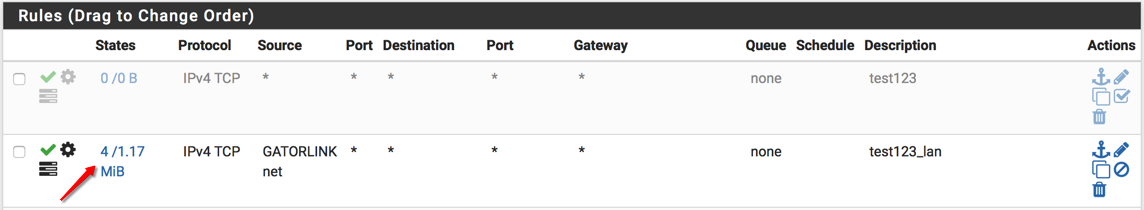
I have a rule on the GatorLink interface to allow access to my NAS (192.168.10.10) on LAN
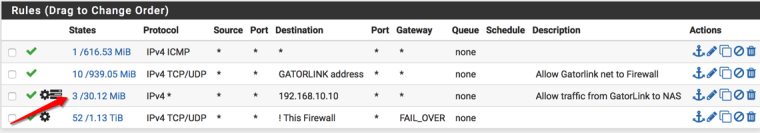
On the LAN side, I've added a rule to allow full access to the GatorLink subnet
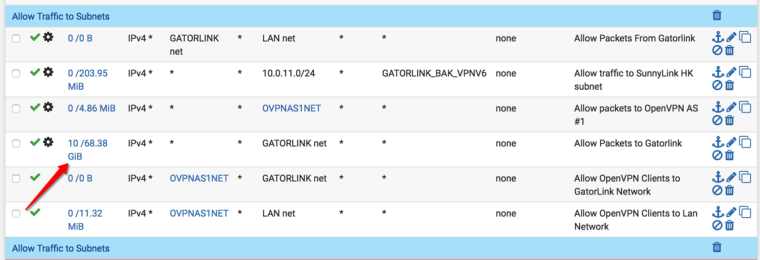
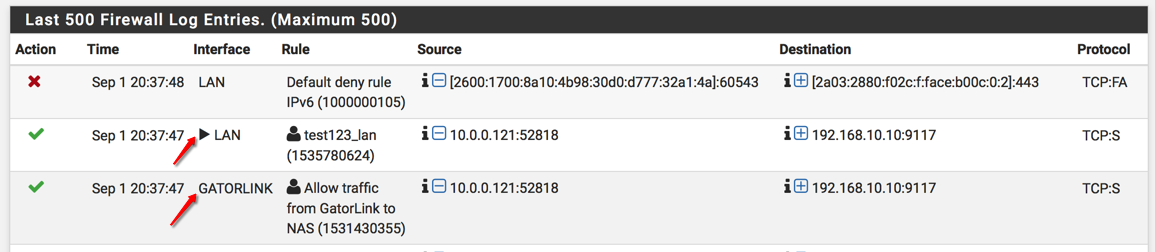
When I look at the firewall logs, why do I have two accesses, one from GatorLink and then one from LAN?
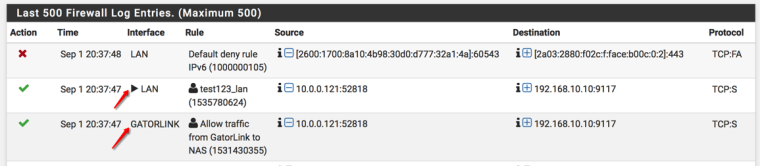
If I don't add a floating rule with interface LAN, direction OUT, source GatorLink net, TCP Flags Any, and State Type Sloppy, some traffic originating from GatorLink to my Synology NAS Dockers does not work.
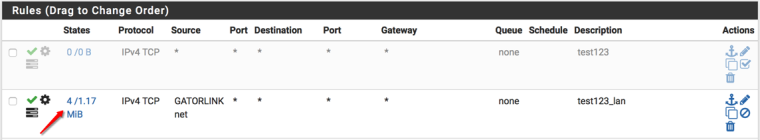
Can anyone explain why I need such a complicated rule set for just allowing all traffic to my NAS?
-
And how do you have this all connected together?
Your 1st rule on your lan is pointless.. When would gatorlink net every be a source into lan?
Looks like your filtering outbound direction. Where exactly are you putting your rules? Are you putting rules on interface and floating?
You have advanced setting on your rules - what are they I see the symbol for something extra being done on the rules
-
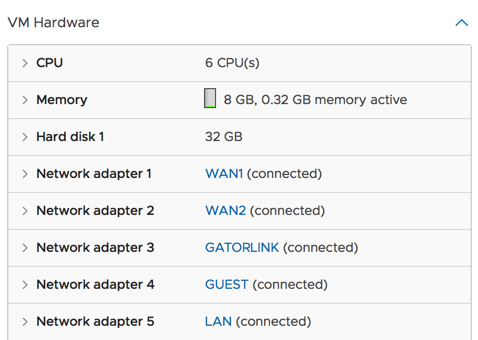
I have two sunsets that are on separate vlans but esxi is handling that and they are presented to pfsense as adapters.
The first rule set is on the gatorlink interface and the second rule set is on the Lan interface. When you look at my firewall logs, you will see the source as gatorlink net appearing on my Lan interface so that’s why I tried to add that rule even though it makes no sense. Also, I tried to add the advance option like all tcp flags and sloppy states as a netgate page had suggested.
The only thing that worked is the floating rule with the advanced option.
-
you got something wrong in your esxi setup.. There would be zero reason to need to do what your doing...
My guess is your just running your layer 3 on the same layer 2.. You setup different port groups for your different vlans and on ths ame vswitch which your different vnic in each port group?
How many physical interfaces do you have on esxi host? Connected how into your physical network? Your problem is your esxi setup.. If setup correctly you would NEVER see your vlan traffic on lan interface - NEVER, its not possible if network is correct.. Only way that could ever happen is if your layer 2 networks are connected together.
-
I believe the VLAN IDs are set up correctly and it has been working for years now.
pfSense VM:
I guess it's one of those things that I say screw it if it works now...
-
Well something changed because its just FACT... You could never see the wrong vlan on pfsense interface unless you have a cross connect.. Its just not possible in networking..
What nics do you have connected to these port groups in pfsense? I not a fan of doing it that way... Set your vswitch to be 4095 so it doesn't strip tags and let pfsense handle the vlans and your actual physical switch..
-
Yes, this looks like asymmetric routing somehow. You are seeing that additional entry on the LAN interface because you have added that floating outbound rule. That traffic would normally be passed by the system rules without logging as it's unnecessary.
I imagine that without the floating rule you see TCP traffic blocked with other TCP flag states, SA, PA etc. It looks like your NAS has a route back to the client without going through pfSense and that's breaking the firewall TCP state awareness.
Steve
-
I think you guys are right. I forgot I created another interface on the NAS that spans the gatorlink subnet so there was another route. Mystery solved!
-
@goldserve said in Explain to me why floating rule is required for my setup:
I say screw it if it works now...
Huh - dude you really should fix that mess.. It will bit you in the ass for sure.. And well its just borked to have it setup like that.. If you need to route to a downstream router or something then use a transit network.. You don't overlap layer 3 networks on the same layer 2.. And multi homing device(s) can be a real pita if don't do it correctly.. And security issue!