[SOLVED] Unable to pass traffic from local network to one of two remote networks under OpenVPN
-
Hello,
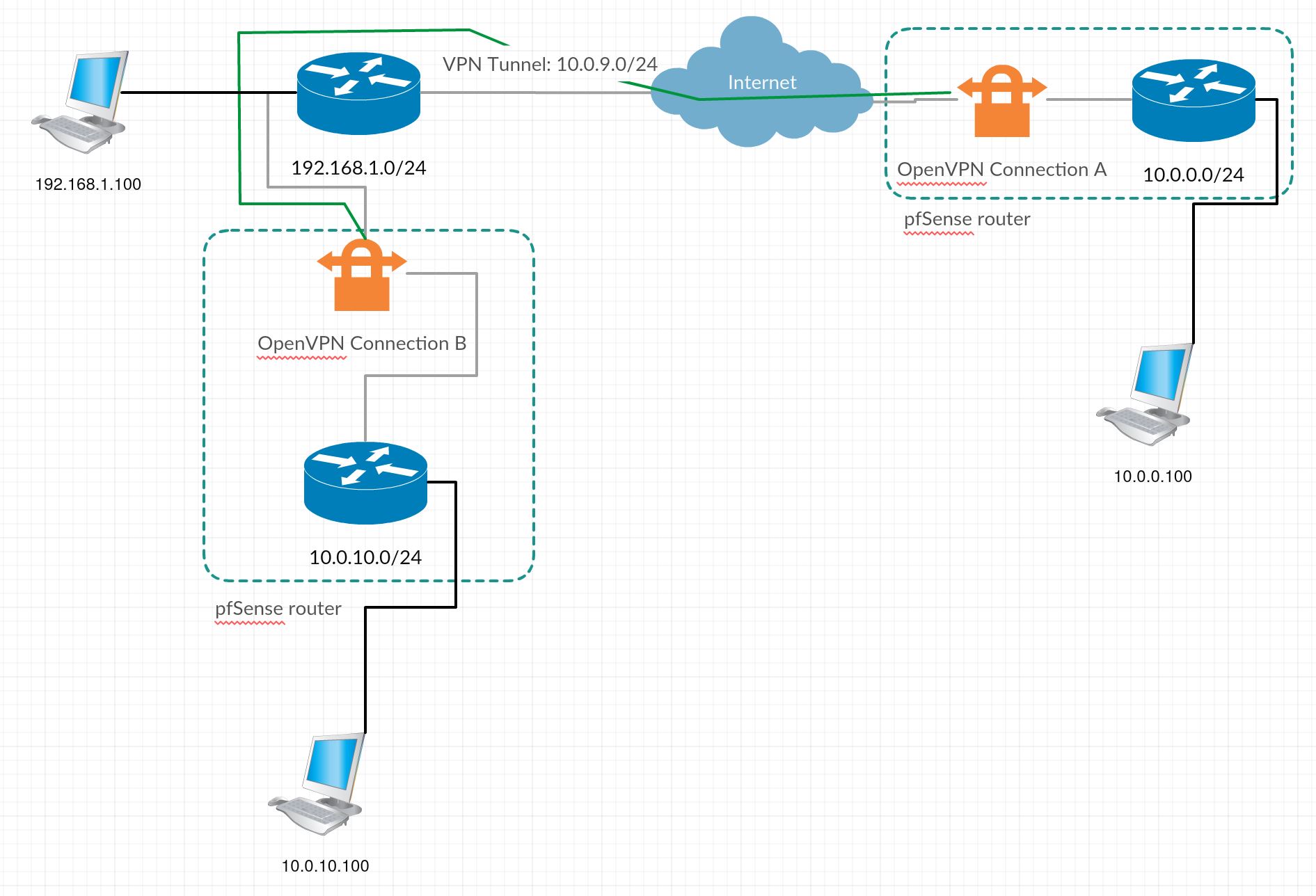
I have an OpenVPN working from site to site, where I can communicate without problem from a local network 10.0.0.0/24 to the remote network 10.0.10.0/24, unless the network who is connected to WAN port (192.168.1.0/24) of the pfSense who is making the VPN.
This is the scenario:
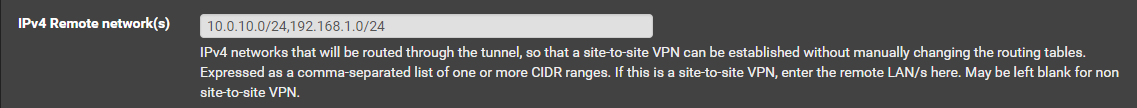
Where I am able to communicate from 10.0.0.100 with 10.0.10.100 and from OpenVPN Connection A interface to 192.168.1.100. If I try to communicate from 10.0.0.100 to 192.168.1.100 I am unable to let traffic pass. I have the server OpenVPN Connection A, configured to route all 10.0.10.0/24 and 192.168.1.0/24 to VPN Tunnel:
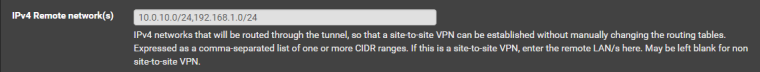
Now, I was expecting that it would route for both 10.0.10.0/24 and 192.168.1.0/24 from 10.0.0.0/24, but it doesnt, and I dont have any rule for the source interface to reject or block traffic to 192.168.1.0/24.
Do you know a way where I could set 10.0.0.0/24 to communicate with 192.168.1.0/24?
Thanks!
-
Since there are two routers at site B, I presume the WAN network 192.168.1.0/24 doesn't use the pfSense which establishes the VPN as default gateway.
So you will have to add a static route to 192.168.1.100 for the remote network 10.0.0.0/24 pointing to pfSense interface IP. -
Thanks for the response viragomann.
Not sure if I have understood but I have already an entrie at remote networks in OpenVPN Connection A server for 192.168.1.0/24, and I can communicate from that server to that network.
"Never add static routes for networks reachable via OpenVPN. Such routes are managed by OpenVPN itself using Remote Network definitions, not static routes."
https://www.netgate.com/docs/pfsense/routing/static-routes.html
And in static route options I am unable to set source network, just destination network is available.
Can you be more specific please?
-
The quoted massage ""Never add static routes ..." refers to pfSense itself.
In your case the static route has to be added to another device.Assumed that the outbound NAT of pfSense on site B is in automatic mode, there will exist a rule for the VPN tunnel subnet on WAN interface translating sources to WAN addresss. Therefor you can access 192.168.1.100 from sites A OpenVPN interface, cause its part of the tunnel network.
If you don't want to add the static route to the device you can also resolve this by adding an additional outbound NAT rule to sites B pfSense WAN interface for the source 10.0.0.0/24.
-
I forgot to say but the primary router of side B, is a Technicolor TG789vac, where the OS is very limited, its a home router. Its just used as an uplink.
On Side B NAT is in Hybrid Outbound NAT, I have a Map there for a device.
I have already did that but I notice now that by mistake I have choosen LAN interface instead of WAN for "matched as it exits the firewall"....
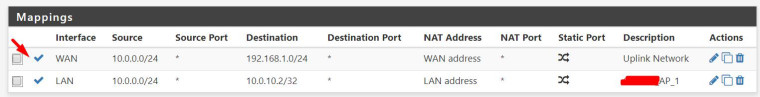
Now its working!
Thanks for the help one more time viragomann!!
PS. If some moderator could move this thread to NAT forum group, would be great, thanks!
-
No, that’s basically a routing issue.
You got no response from the device cause it has no route to the site A LAN. So it sent response packets to its default gateway instead of pfSense.However, this can also be resolved by NAT. The NAT rule tranlates the source addresses in request-packets into pfSense WAN interface address. So responses are sent back to pfSense.
The backdraw of NAT is that you‘re not able to determine where the request comes from on the dest device, cause any requests from site A has the pfSense interface address as source.