OpenVPN Site to Site Setup
-
@derelict For some reason it's making me split this into two posts. I'm at my wits end here. Thank you for being so responsive and helpful, but I feel like I'm being an idiot here. This seems like such a simple task to complete.
I've attached copies of the config backup from both PFsense devices. If you could please look them over and let me know if I'm just missing something dumb, that would be amazing. The only thing I did not plug in this time is the IPv4 remote networks. The server side is on 192.168.0.0/24 and the client side is on 192.168.1.0/24.
With this configuration, we're able to ping the client side PFSense from any device on the host network, but nothing else. On the flip side, we cannot ping anything on the host network, not even the PFSense. This happens with an without the IPv4 remote networks mapped. If we have one of the users connect with the Remote Access VPN, they can ping an access everything on the host network as expected, however, they cannot access anything on the client side network. You can't even ping the client side PFSense.
-
I don't see any attachments to your last post... or did you PM them to derelict?
If you post the configs, it's usually pretty easy to spot misconfigured items.
-
@marvosa I'm still attempting to post them. I'm sorry. It's marking it as spam because I'm posting a Google Drive link.
-
Alright, not sure what to do here. Just not having any luck, lol. I'm trying to post the config files, but they're 2.5mb, so they're over the size limit. If I zip them, I get an error. Last resort was using Google Drive, but the post gets marked as spam when I try to submit it.
-
Just post them as coded text... i.e. use the code button and post the raw text within the code tags.
-
There is probably too much information in an unredacted config file.
I don't really want to see the config.
What would be best are the pcaps I already discussed...twice I think.
Diagnostics > Packet Capture
There are four locations you should capture:
- Source interface the host is connecting from
- OpenVPN interface on the near side
- OpenVPN interface on the far side
- Destination interface the ping will go out to reach the target host
Filter the pcap for just ICMP and one of the host addresses.
If you do post anything, be sure to describe exactly where the capture in question was taken.
-
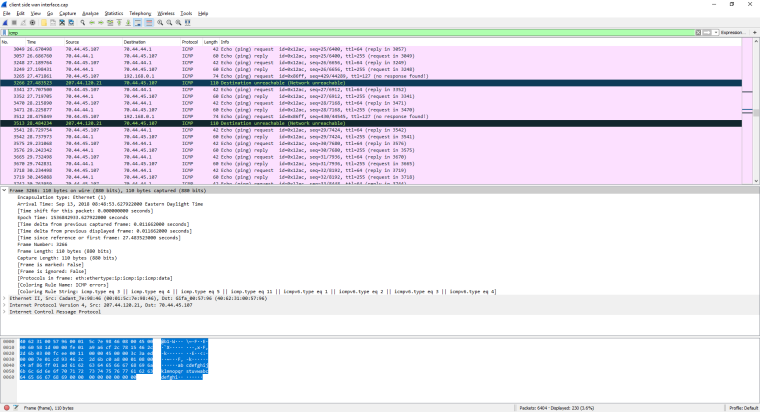
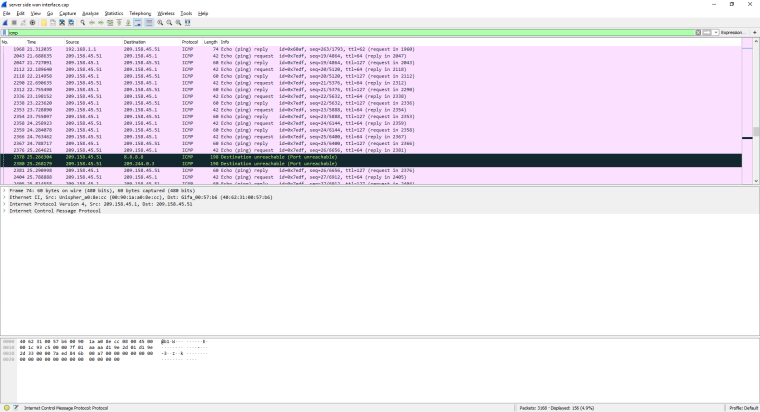
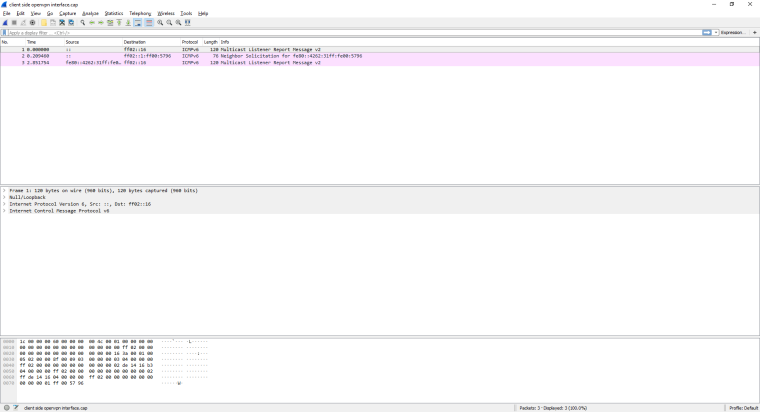
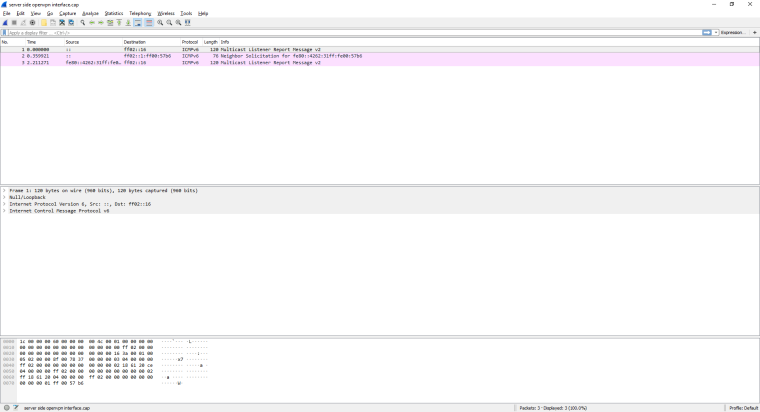
@derelict Alright. So I've ran the packet captures from the PFsense as suggested. I'm getting weird results from the OpenVPN interfaces, however, the WAN interface results look normal.
To give details, on each capture ran, I would start the capture, restart the VPN service on the server side first, then client side. I then ran a ping from server side, then from client side, and stopped the capture. I filtered by ICMP as suggested and see the 4 failed pings on the client side. On the server side however, I do not see the ping attempts. At least, I don't see the public IP I would expect.
Since I can't seem to upload any files to the forum, here's some screen caps. You can see the interface and side used in the title bar.
-
You are not understanding at all. We should not be seeing traffic with "public" IP addresses. That looks like a capture on the WAN.
We need a capture on LAN that the piings are coming into, then a capture on OpenVPN where the traffic should be routed out. Capture on the OpenVPN on the other side, then the LAN over there it should be going out of.
Nothing on WAN is interesting to us here.
Or you have to draw your network so we can see what it is we are looking at.
-
@derelict I'm very sorry for the confusion. I'm still new to Pfsense and networking in general. This is a very basic setup, so here is a map. There're two sites about 50 miles from each other. There is only a standard managed switch, but there're no VLAN configurations or anything. Basically just plugged in out of the box, with the password changed, etc.
Host Side:
DSL Modem in Bridged Mode>Host PFSense (192.168.0.1)>16 port switch (192.168.0.11) (Netgear GS116Ev2)>Physical Server (192.168.0.250)Client Side:
DSL Modem in Bridged Mode>Client PFSense (192.168.1.1)>Laptop connected to port 4 (192.168.1.104)Between every packet capture and ping, I would restart the VPN server, then the VPN client, then ping from the listed machine.
The below captures are pinging the Host PFSense (192.168.0.1) from the laptop connected directly to the Client Side PFSense
Server Side LAN Interface:
https://pastebin.com/sJkUi1djClient Side LAN Interface:
https://pastebin.com/UgVfAbuJServer Side OpenVPN Interface:
Filtered by ICMP, I get no results.Client Side OpenVPN Interface:
Filtered by ICMP, I get no results.The below captures are pinging the Client Side PFSense (192.168.1.1) from the Physical Server connected through the switch, on the Host PFSense.
Server Side LAN Interface:
https://pastebin.com/ijXcrx58Client Side LAN Interface:
Filtered by ICMP, I get no results.Server Side OpenVPN Interface:
Filtered by ICMP, I get no results.Client Side OpenVPN Interface:
Filtered by ICMP, I get no results. -
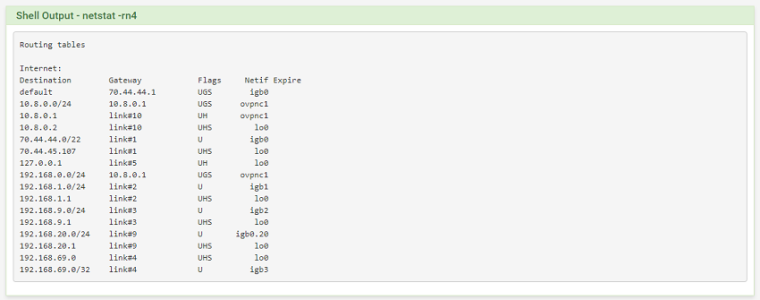
Please post the output from executing
netstat -rn4in Diagnostics > Command Prompt on both nodes.Please post screenshots directly to the forum. pastebin links are hard to follow.
-
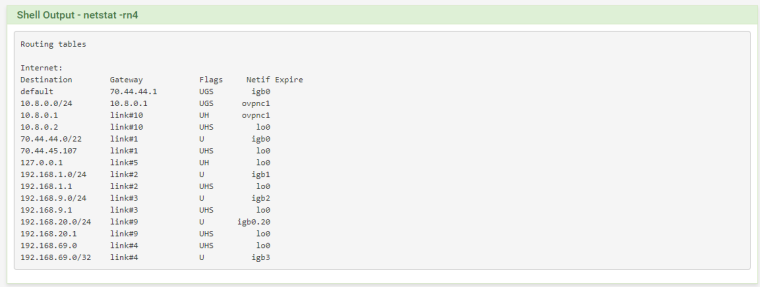
@derelict Client Side:
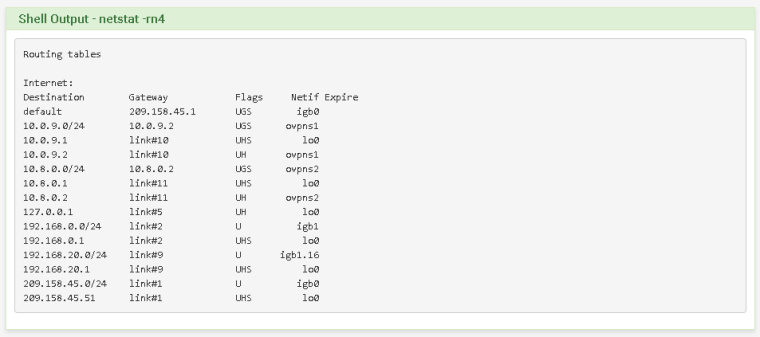
Server Side:
-
Notice you do not have 192.168.0.0/24 routes into the tunnel on the 192.168.1.0/24 side and you do not have routes to 192.168.1.0/24 into the tunnel on the 192.168.0.0/24 side.
Add the CIDR/route for the other side on each side's OpenVPN Remote Networks settings.
On the server side you should end up with a route for 192.168.1.0/24 gateway 10.8.0.1 Netif ovpns2
On the client side you should end up with a route for 192.168.0.0/24 gateway 10.8.0.2 Netif ovpnc1
-
Which would have been readily apparent had the configs been posted a week ago.
-
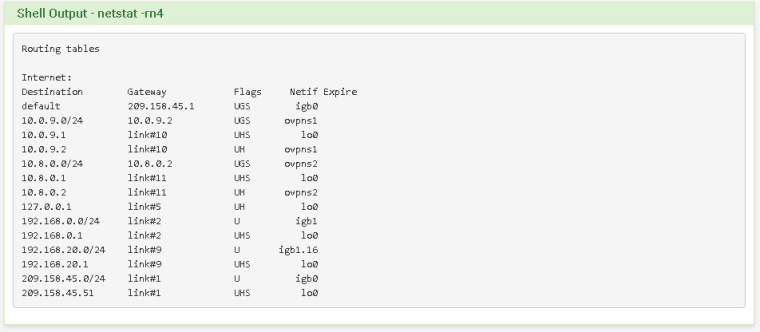
@derelict I had those settings set exactly as you stated before. I did not have them set when I posted the initial netstat, I apologize. However, I'm still experiencing the exact same issue. Can ping the client side PF from the server, but not the other way around.
@marvosa I'm not sure how to get those config files. If you could let me know how to get those, I'd be more than happy to.
Server Side:
Client Side:
-
@sage-badolato said in OpenVPN Site to Site Setup:
Can ping the client side PF from the server, but not the other way around.
Then it is either the firewall rules on the server side's OpenVPN tab or the firewall on the device you are pinging itself.
-
@sage-badolato said in OpenVPN Site to Site Setup:
@marvosa I'm not sure how to get those config files. If you could let me know how to get those, I'd be more than happy to.
The OpenVPN config files are located here:
/var/etc/openvpnYou can view the contents via the shell or Diagnostics -> Edit File
-
Ended up finding that Client Override needed to be enabled on the Server Side PFsense. Once we enabled this, everything started working.