How do I allow OpenVPN clients to connect to my LAN devices?
-
Hi all,
My network setup is below:
Main network 192.168.16.0 /24
OpenVPN Tunnel network: 10.0.8.0/24pfSense IP: 192.168.16.254
secondary router: 192.168.16.1
Windows Terminal Server (RDP): 192.168.16.5For example:
if the terminal servers default gateway is set to: 192.168.16.254, the openvpn clients can connect fine, but if it was set to: 192.168.16.1, they can no longer ping or connect to it.Why is this? I need this to work as not all devices on my network will use the pfSense as there default gateway but I need the openvpn clients to connect to them.
I've tried
push "route 192.168.16.0 255.255.255.0"
with no luck unfortunatelyAny help would be appreciated thanks,
Gary -
@gary-crawford said in How do I allow OpenVPN clients to connect to my LAN devices?:
Why is this?
Because your server would talk to its gateway 192.168.16.1 which how would that get back to the tunnel network the openvpn client is on.
You would have to put route on server telling it how to get to your 10.0.8 network which your openvpn client would get an IP on.. Sounds like you have asymmetrical mess if you have clients on what would normally be a transit network if you have a downstream router.
-
@johnpoz said in How do I allow OpenVPN clients to connect to my LAN devices?:
@gary-crawford said in How do I allow OpenVPN clients to connect to my LAN devices?:
Why is this?
Because your server would talk to its gateway 192.168.16.1 which how would that get back to the tunnel network the openvpn client is on.
You would have to put route on server telling it how to get to your 10.0.8 network which your openvpn client would get an IP on.. Sounds like you have asymmetrical mess if you have clients on what would normally be a transit network if you have a downstream router.
Hi John, thanks for the fast response. I'm currently in the process of replacing our Draytek router which is the (192.168.16.1) with the pfSense one. But what I don't understand is how the Draytek VPN clients can access the terminal server no matter what default gateway it has e.g (192.168.16.254). I would like the OpenVPN clients to access the whole network regardless of what the gateway settings on the servers would be just like the Draytek VPN seems to be setup. Is that not possible?
-
Then you would have to source NAT your vpn clients connection into the 192.168.16 network so it looks like its coming from pfsense 16.254 address.
Or as I already stated create a route on this vpn server telling it how to get to the 10.0.8 network.
-
@johnpoz
Thanks John adding the NAT Outbound rule has made it work
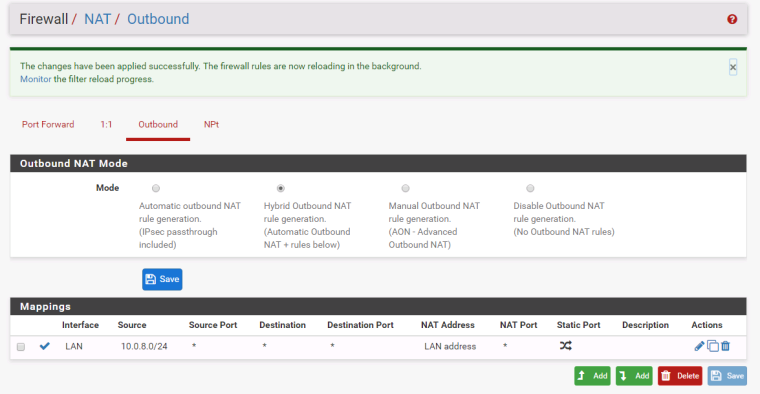
Do you know of any disadvantages to this? Or is it fine to use it this way
-
It overly complex - And you can not create any unsolicited traffic to clients with such a setup.
I would not do it this way no - why would your dest have a different gateway then pfsense in the final setup?
-
@johnpoz I suppose in the final setup it wont be needed as this will be the only gateway, but at the moment I need it as it is not our primary gateway just yet. Thanks for your help on this anyway John.