DDoS attacks OpenVPN on Pfsense
-
@netblues said in DDoS attacks OpenVPN on Pfsense:
Are you using a static tls key?
Are you using a static TLS key? How is your server configured?
-
@kom said in DDoS attacks OpenVPN on Pfsense:
Does this happen to anyone else?
#Metoo.
Having a static IPv4 your years now, but never saw something like that.
TLS Keys : of course, I use these. -
two different sites got attacked. They are different client and network. They got attacked with the same IP address.
How can i extract OpenVPN log from pfsense
-
Whats the IP address, it's not comming from shodan or shadowserver is it ?
I get these almost every day poking my IPsec VPN, create a blacklist in snort if it is.
shadowserver:- 216.218.206.0/24 shodan:- 198.20.69.72/29 # census1.shodan.io 198.20.69.96/29 # census2.shodan.io 198.20.70.112/29 # census3.shodan.io 198.20.99.128/29 # census4.shodan.io 93.120.27.62 # census5.shodan.io 66.240.236.119 # census6.shodan.io 71.6.135.131 # census7.shodan.io 66.240.192.138 # census8.shodan.io 71.6.167.142 # census9.shodan.io 82.221.105.6 # census10.shodan.io 82.221.105.7 # census11.shodan.io 71.6.165.200 # census12.shodan.io 188.138.9.50 # atlantic.census.shodan.io 85.25.103.50 # pacific.census.shodan.io 85.25.43.94 # rim.census.shodan.io 71.6.146.185 # pirate.census.shodan.io 71.6.146.186 # inspire.census.shodan.io 71.6.158.166 # ninja.census.shodan.io 198.20.87.96/29 # border.census.shodan.io 66.240.219.146 # burger.census.shodan.io 209.126.110.38 # atlantic.dns.shodan.io 104.236.198.48 # blog.shodan.io 104.131.0.69 # hello.data.shodan.io 162.159.244.38 # www.shodan.io 159.203.176.62 # ny.private.shodan.io 188.138.1.119 # atlantic249.serverprofi24.com 80.82.77.33 # sky.census.shodan.io 80.82.77.139 # dojo.census.shodan.io 71.6.146.130 # ubtuntu16146130.aspadmin.com 66.240.205.34 # shodan.io 216.117.2.180 # malware-hunter.census.shodan.io 93.174.95.106 # battery.census.shodan.io 89.248.172.16 # house.census.shodan.io 185.163.109.66 # goldfish.census.shodan.io 93.174.95.106 # battery.census.shodan.io 89.248.167.131 # mason.census.shodan.io 94.102.49.190 # flower.census.shodan.io 94.102.49.193 # cloud.census.shodan.io 185.181.102.18 # turtle.census.shodan.io -
Could you tell me how to create a blacklist in snort?
-
Create the blacklist file:-
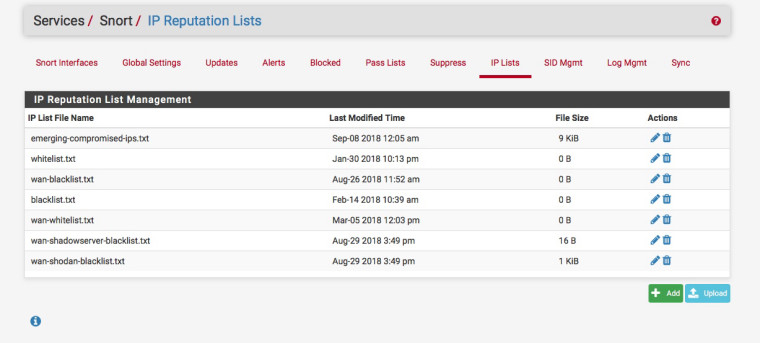
Apply it to the interface:-
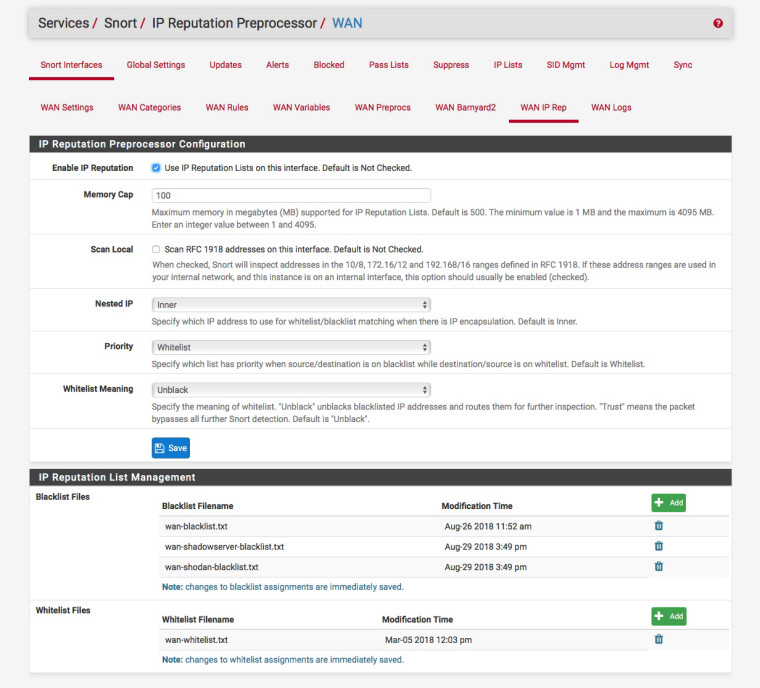
You then should see (spp_reputation) packets blacklisted in the blocked list:-
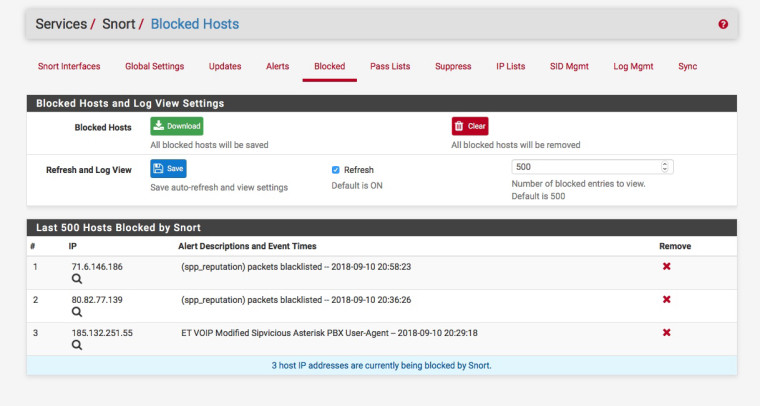
-
Love it. Thanks for your help
-
@netblues said in DDoS attacks OpenVPN on Pfsense:
Are you using a static tls key?
You have been asked this twice now. It's hard to help you when you don't answer questions.
-
You have ZERO need of snort to stop traffic from hitting your wan IP on your openvpn port - ZERO!!!
Im with kom - you going to answer the simple TLS key question??
-
I checked. I didn't use TLS key on OpenVPN setting. Might be you can help me to set this up for extra layer.
My OpenVPN set up look like this
SSL/TLS + user auth -> DUO -> AD for people to sign in. I am not using local database for user auth
Do you sugguest any online guide that I can read of TLS?
-
I think you just have to check the Use a TLS key box and then generate new user config that has the TLS key embedded in the .ovpn file, for instance.
-
The guide on openvpn hardening has lots of info
https://community.openvpn.net/openvpn/wiki/Hardening
tls key is described in section Use of --tls-auth
As for pfsense, its rather straight forward to implement what it suggests.
It also means that you need to send the tls.key to all your clients somehow.
Now if you are running clients by the thousands, this is definitely an issue on its own.
Imagine this as an initial passphrase. If the client connecting knows it, thserver will deal with him further, spending computing resources to do all the needed security handshakes
Obviously it won;t help if you are experiencing a network level attack, ie ping flood saturating your line. -
I got the TLS in place at one site. I will keep my eyes on it for the next few days. Also, set up a blocklist on Snort is also a good idea.
This guide is quite useful too. Thanks
https://community.openvpn.net/openvpn/wiki/Hardening